Info. Security News News
Pymnts
206

Image Credit: Pymnts
23andMe Reportedly Paying $30 Million to Settle Data Breach Suit
- 23andMe will pay $30 million to settle a lawsuit related to a data breach.
- The settlement requires 23andMe to provide three years of security monitoring for affected customers.
- The lawsuit accused 23andMe of failing to protect the private information of nearly 7 million customers exposed in the breach.
- The settlement also addresses allegations that 23andMe did not inform customers targeted by a hacker selling their information on the dark web.
Read Full Article
12 Likes
Securityaffairs
454

Image Credit: Securityaffairs
Port of Seattle confirmed that Rhysida ransomware gang was behind the August attack
- Port of Seattle confirmed that Rhysida ransomware gang was behind the August attack.
- The cyber attack disrupted travel plans at the Port of Seattle, impacting websites, email, and phone services.
- The Rhysida ransomware group has been active since May 2023, targeting organizations in various sectors.
- The Port of Seattle has refused to pay the ransom and is working on restoring systems and enhancing security measures.
Read Full Article
27 Likes
Securityaffairs
27

Image Credit: Securityaffairs
Security Affairs newsletter Round 489 by Pierluigi Paganini – INTERNATIONAL EDITION
- U.S. CISA adds Ivanti Cloud Services Appliance Vulnerability to its Known Exploited Vulnerabilities catalog
- GitLab fixed a critical flaw in GitLab CE and GitLab EE
- New Linux malware called Hadooken targets Oracle WebLogic servers
- Lehigh Valley Health Network hospital network has agreed to a $65 million settlement after data breach
Read Full Article
1 Like
Hackersking
105

Image Credit: Hackersking
GTFOBins To Bypass Local Security Restrictions In Linux/Unix
- This article discusses privilege escalation in Linux by using binaries like GTFOBins or GTFOBinaries.
- GTFOBins provides a list of binaries and commands that can be exploited for privilege escalation.
- GTFOBins also provides detailed information about each binary and the required user privileges for execution.
- Privilege escalation involves exploiting vulnerabilities in a system to obtain higher levels of access.
- There are two types of privilege escalation- horizontal and vertical.
- Misconfigurations like improper SUID/SGID settings or over-privileged sudo rights can lead to security vulnerabilities.
- GTFOBins is an open-source initiative and is constantly evolving to include the latest binaries and techniques.
- Some possible ways to exploit SUID binaries include shared object injection and environment variable exploitation.
- Improperly configured Sudo can also lead to privilege escalation.
- Path injection and Linux capabilities misconfigurations can also be exploited for privilege escalation.
Read Full Article
6 Likes
Inkbotdesign
110

How to Minimise Google Data Collection to Protect Privacy
- Every search you make, every location you visit, and every email you send or receive on Gmail leaves a digital footprint.
- You can limit Google data collection by being selective of what you share and declining invitations to share more.
- You can use Google's tools against Google, such as using Incognito Mode when you want to keep those searches under wraps.
- Audit third-party apps and remove permissions for anything you are no longer using or don't find trustworthy.
- Google provides different utilities to control your privacy such as My Activity, Privacy Checkup, and Google Takeout.
- Google's data collection leads to potential risks of data breaches, profiling, and loss of control over one's digital identity.
- Regularly going through your privacy settings and changing them according to what makes you comfortable can protect your privacy.
- Being private is not about returning to a pre-digital world but about owning our choices and drawing the line in the sand.
- Whenever you hesitate between clicking “accept” and going over which data you have shared, you do something more than protect your privacy: You take control.
- Google might be watching but you should let it see only some things, and step by step, you can secure your data.
Read Full Article
6 Likes
Securityaffairs
87

Image Credit: Securityaffairs
U.S. CISA adds Ivanti Cloud Services Appliance Vulnerability to its Known Exploited Vulnerabilities catalog
- The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added Ivanti Cloud Services Appliance Vulnerability to its Known Exploited Vulnerabilities catalog.
- Ivanti warned that the recently patched flaw in Cloud Service Appliance (CSA) is being actively exploited in the wild.
- An attacker can trigger this high-severity vulnerability to achieve remote code execution.
- CISA orders federal agencies to fix this vulnerability by October 4, 2024.
Read Full Article
5 Likes
Hackingblogs
156
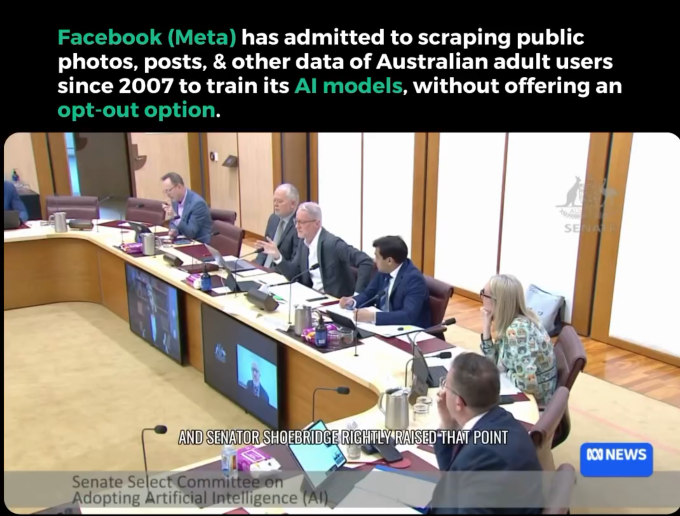
Image Credit: Hackingblogs
Meta Admits to Using All Public Data for AI Training Since 2007—No Opt-Out Available
- Meta Facebook admits to using all public data since 2007 for AI training without offering opt-out choice to Australian users.
- The company scrapes public images, posts, and other data of adult Australian users without their consent.
- European users have the opt-out option, but Australian users do not.
- Meta is exploring partnerships with news publishers to obtain more training data.
Read Full Article
9 Likes
Securityaffairs
270

Image Credit: Securityaffairs
Ivanti Cloud Service Appliance flaw is being actively exploited in the wild
- Ivanti Cloud Service Appliance flaw CVE-2024-8190 is being actively exploited in the wild.
- The vulnerability allows remote code execution under specific conditions.
- Ivanti released a security update for CSA 4.6 to address the vulnerability.
- Customers should upgrade to Ivanti CSA 5.0 for continued support and protection.
Read Full Article
16 Likes
Securityaffairs
68

Image Credit: Securityaffairs
GitLab fixed a critical flaw in GitLab CE and GitLab EE
- GitLab addressed multiple vulnerabilities impacting GitLab CE/EE, including a critical pipeline execution issue.
- GitLab released security patches for 17 vulnerabilities in GitLab CE and EE.
- One of the vulnerabilities, tracked as CVE-2024-6678, is a critical pipeline execution flaw.
- GitLab also fixed other high, medium, and low-severity vulnerabilities.
Read Full Article
4 Likes
Amazon
64

Image Credit: Amazon
Podcast: Empowering organizations to address their digital sovereignty requirements with AWS
- Developing strategies to navigate the evolving digital sovereignty landscape is a top priority for organizations operating across industries and in the public sector.
- Customers are meeting their unique digital sovereignty needs with AWS, which offers control, choice, security, and resilience in the cloud.
- AWS innovations like the Nitro System, Dedicated Local Zones, Key Management Service External Key Store, and the upcoming European Sovereign Cloud are discussed.
- Visit Digital Sovereignty at AWS to learn more and effectively navigate the digital sovereignty landscape while unlocking the full potential of cloud computing.
Read Full Article
3 Likes
Securityaffairs
101
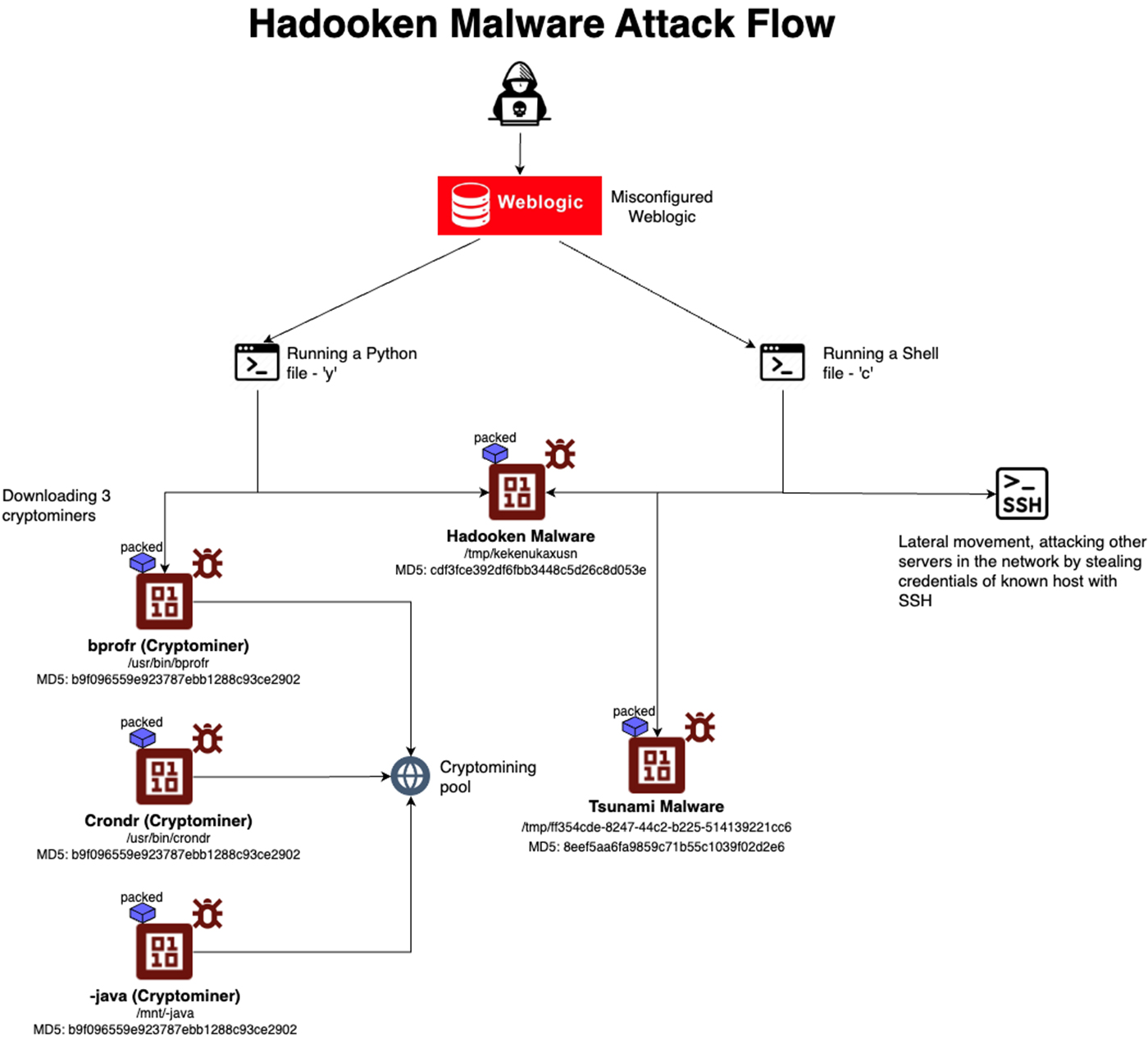
Image Credit: Securityaffairs
New Linux malware called Hadooken targets Oracle WebLogic servers
- A new Linux malware called Hadooken targets Oracle WebLogic servers.
- The malware drops a Tsunami malware and deploys a cryptominer.
- Threat actors exploit weak passwords to gain access.
- Hadooken malware is linked to ransomware families.
Read Full Article
6 Likes
Securityaffairs
381

Image Credit: Securityaffairs
Lehigh Valley Health Network hospital network has agreed to a $65 million settlement after data breach
- Lehigh Valley Health Network (LVHN) hospital network has agreed to a $65 million settlement in a class action lawsuit related to a data breach.
- The data breach occurred as a result of a BlackCat ransomware attack and resulted in the publication of nude images of 600 cancer patients.
- The breach exposed personal information of at least 134,000 individuals, including names, addresses, phone numbers, medical records, and health insurance information.
- Under the settlement, affected individuals will receive compensation ranging from $50 to $70,000, with the highest amounts going to those whose hacked nude photos were published online.
Read Full Article
22 Likes
Amazon
50

Image Credit: Amazon
Reduce risks of user sign-up fraud and SMS pumping with Amazon Cognito user pools
- Amazon Cognito is a managed OpenID Connect (OIDC) identity provider (IdP) that you can use to add self-service sign-up, sign-in, and control access features to your web and mobile applications.
- SMS pumping is when bad actors purchase a block of high-rate phone numbers from a telecom provider and then coerces unsuspecting services into sending SMS messages to those numbers.
- In this blog post, we explore how SMS pumping may be perpetrated and options to reduce risks, including blocking unexpected user registration, detecting anomalies, and responding to risk events with your Cognito user pool.
- Implementing bot mitigation techniques, such as CAPTCHA, can be very effective in preventing simple bots from pumping user creation flows.
- You can validate the user provided phone number in the backend to catch incorrectly formatted phone numbers and add logic to help filter out unwanted phone numbers prior to sending text messages.
- Another layer of mitigation is to identify the actor’s phone number early in your application’s sign-up process.
- You can also choose to deliver an OTP using other methods, such as email, especially if your application doesn’t require the user’s phone number.
- By implementing these strategies, you can enhance the security of your web and mobile applications and help to safeguard your services from potential abuse and financial loss.
- We suggest that you apply a combination of these prevention, detection, and mitigation approaches to protect your Cognito user pools.
- It’s essential to continually review the effectiveness of these rules to minimize the risk of blocking legitimate sources and make dynamic adjustments to the rules when you detect new bad actors and patterns.
Read Full Article
3 Likes
Sentinelone
335

Image Credit: Sentinelone
The Good, the Bad and the Ugly in Cybersecurity – Week 37
- Singaporean authorities conducted an island-wide raid on various suspects that were being monitored for their links to a global cybercrime syndicate.
- Two individuals have been indicted in the U.S. for their alleged involvement in managing a dark web marketplace known as WWH Club.
- Crypto took a major hit last year with losses exceeding $5.6 billion.
- The report laid out several fraud and scam trends, ranging from fake investment sites, pig butchering schemes linked to dating apps and professional networking platforms, and liquidity mining scams that offer high returns for staking assets.
- Iraqi government entities have been targeted in a sophisticated campaign led by OilRig (aka APT34), an Iranian state-sponsored threat group.
- OilRig introduced two new malware strains, Veaty and Spearal, designed to execute PowerShell commands and extract sensitive files.
- Spearal, a .NET backdoor, uses DNS tunneling for communication, while Veaty relies on compromised email accounts for its command-and-control (C2) operations.
- The campaign targeting Iraqi government infrastructure also involved the discovery of additional backdoors, such as CacheHttp.dll, that targets Microsoft’s Internet Information Services (IIS) servers.
- Advanced persistent threats (APTs) like OilRig continue to develop specialized techniques in maintaining C2 channels to further develop elaborate cyber-espionage campaigns against high-value adversarial targets.
- Latest findings published by the FBI’s Internet Crime Complaint Center (IC3), the product of almost 70,000 reports, marks this 45% rise as a new record high for the industry.
Read Full Article
20 Likes
Securityintelligence
381

Image Credit: Securityintelligence
What can businesses learn from the rise of cyber espionage?
- Rival nation-states and the organizations loyal to them are increasingly turning to cyber espionage to gain a strategic advantage.
- Long gone are the days when standalone criminals are the greatest threat. Now the greater threat comes from nation-states and large enterprises that have capitalized on the opportunities of digital espionage.
- The combination of AI and increasingly massive amounts of data means business strategy can be decided in hours and days rather than months, making AI a necessity even in the world of cyber crime and espionage.
- State-sponsored attackers are already using tools like large language models (LLMs) to scale, inform, and enhance their attacks, making AI a force multiplier in the broader threat landscape.
- Organizations must proactively protect against cyber espionage by layering on a zero trust architecture, conducting regular security audits, and ensuring all sensitive information is encrypted regardless of where it resides.
- Businesses need to continuously monitor, review and update their security systems, and layering on AI has become necessary thanks to its ability to augment real-time threat detection and response capabilities.
- No business will ever be immune to cyberattacks, but the greatest risk comes with a failure to innovate. Businesses need to strike the right balance by incorporating AI strategically as a tool to protect against the next generation of state-sponsored cyber threats.
Read Full Article
22 Likes
For uninterrupted reading, download the app