Cyber Security News
Cybersecurity-Insiders
197

Image Credit: Cybersecurity-Insiders
Three trending Cybersecurity news headlines on Google
- Elon Musk’s satellite-based internet communication service, Starlink, has become involved in a growing controversy linked to the 2024 US Presidential Election, accused of potentially influencing the outcome on behalf of Republican candidate, former President Donald Trump.
- Reports suggest that Starlink’s broadband services were used to keep critical voting infrastructure online during the election period, raising concerns over the company's role in maintaining electoral system integrity.
- US government and international observers will likely be monitoring the effects of Starlink's recent agreement with the Indian government over data sovereignty and overseas influence.
- After reports of Chinese cyberattacks on critical US telecoms infrastructure, Consumer Financial Protection Bureau has urged federal employees to limit their mobile phone use due to risks of foreign surveillance, with government-approved platforms recommended instead.
- There has been little public discussion regarding efforts to address the underlying causes of the Chinese State-linked attacks, with the government's response focusing much more on limiting the exposure of sensitive information through employee devices.
- A Distributed Denial of Service (DDoS) cyberattack was carried out on a major payment gateway service, Hyp, in Israel, which significantly disrupted the operations of various high-profile online services, including ride-hailing service Gett, online food delivery platform Wolt, and health insurance provider Maccabi Health Fund.
- Experts have suggested that the latest attack may have been carried out by pro-Iranian hacking groups who often target Israeli infrastructure.
- This incident underscores the role that cyber operations play in modern geopolitical conflicts and highlights the increasingly precarious nature of global cybersecurity.
- The intersection between global business, cybersecurity, and politics is becoming a defining feature of international relations.
- The battle for control of cyberspace is set to escalate in the coming years, with far-reaching consequences for national security and international diplomacy.
Read Full Article
11 Likes
TechJuice
78

Image Credit: TechJuice
PTA Issues Urgent Cybersecurity Alert on Critical Oracle WebLogic Server Vulnerability
- The Pakistan Telecommunication Authority (PTA) has issued a critical cybersecurity advisory regarding a vulnerability in Oracle WebLogic Server.
- The vulnerability, CVE-2017-3506, allows attackers to execute arbitrary code using specially crafted HTTP queries.
- PTA advises organizations to upgrade to the most recent versions of WebLogic Server to protect against the vulnerability.
- The advisory emphasizes the importance of implementing multi-factor authentication and network segmentation for enhanced security.
Read Full Article
4 Likes
Dev
36

Image Credit: Dev
How to use GitHub Personal Access Tokens Securely
- GitHub personal access tokens are a better option than passwords, especially for working with GitHub through APIs and command-line operations.
- Fine-grained personal access tokens are recommended as they provide detailed permission and access control to only the specific resources required, reducing security risks.
- Classic tokens provide wider access and lack granularity, but are still necessary for many established workflows.
- Tokens should be deleted when no longer needed to avoid exposing programs to any risks.
- Token caching increases efficiency by remembering the token, and these credentials can be cached for a set duration.
- Best practices include only creating tokens with necessary privileges, using fine-grained tokens wherever possible, and embracing other authentication methods to secure workflows.
- Developers can minimize risks with mismanaged tokens by regularly cleaning up and revoking old or unused tokens.
- Monitoring tools like CICube provide detailed insights to optimize CI/CD pipelines.
- Overall, GitHub personal access tokens are powerful and following secure management practices can ensure a safe development environment.
Read Full Article
2 Likes
Dev
417

Image Credit: Dev
How to Use Kubernetes CronJob
- Kubernetes CronJob is a powerful way to schedule jobs.
- CronJob maintains the right relationship between the Job and actual execution.
- Creating, managing, and troubleshooting CronJobs are covered in this article.
- Syntax and configurations for CronJobs are explained, along with practical implementations.
- A manifest is created to show how to print the current date and a greeting message.
- CronJob schedule syntax is explained using the same syntax one would see in standard Unix/Linux cron jobs.
- Troubleshooting CronJobs is addressed, including missed schedules and failed ones.
- The concept of concurrency, and its three major categories: Allow, Forbid, and Replace, is covered.
- This article is useful for DevOps practitioners looking to create automated workflows and manage applications within a cluster.
Read Full Article
25 Likes
Dev
358

Image Credit: Dev
Node.js Authentication: Best Practices and Key Strategies
- This article showcases secure login strategies for Node.js, implementing multiple security techniques to safeguard user credentials, sessions, and account access.
- Passwords are hashed using a strong hashing algorithm (e.g., bcrypt) along with a random salt for each password. This ensures that even if the hashed password is compromised, it cannot easily be reversed into the original password.
- JWT (JSON Web Token) is used for token-based authentication, allowing stateless authentication between the client and server. Users receive a JWT upon login, which is then sent with every subsequent request in the Authorization header.
- A refresh token is used to obtain new access tokens without requiring the user to log in again. This ensures a smooth experience for users without compromising security.
- Store sensitive tokens such as refresh tokens in HTTP-only cookies. This prevents JavaScript from accessing the tokens, protecting them from XSS (Cross-Site Scripting) attacks.
- JWT tokens do not have built-in revocation. To invalidate tokens (e.g., on logout), JWT blacklisting is used. A database or Redis is used to store invalidated tokens until they expire.
- Ensure that only one session is active for a user at any given time. When a new session is created, invalidate previous tokens or sessions.
- Sessions expire after a period of inactivity. Implement a session expiration timer to automatically log out users who are inactive for a predefined time.
- Prevent brute force attacks by locking out accounts after several failed login attempts. Implement time-based lockout, where accounts are temporarily locked after repeated failures.
- Users can reset their passwords through a secure process. Use a time-limited, one-time token (OTP) sent to the user's email for the reset process. Ensure the reset token expires after a short period.
- Strong password policies help prevent unauthorized access and minimize the risk of brute-force attacks, dictionary attacks, and credential stuffing.
- User-specific token revocation is the process of invalidating a single user’s tokens without affecting others.
- Configure CORS to restrict which origins are allowed to access the API. Only trusted domains should be allowed to send requests to your server.
Read Full Article
21 Likes
Securityaffairs
238
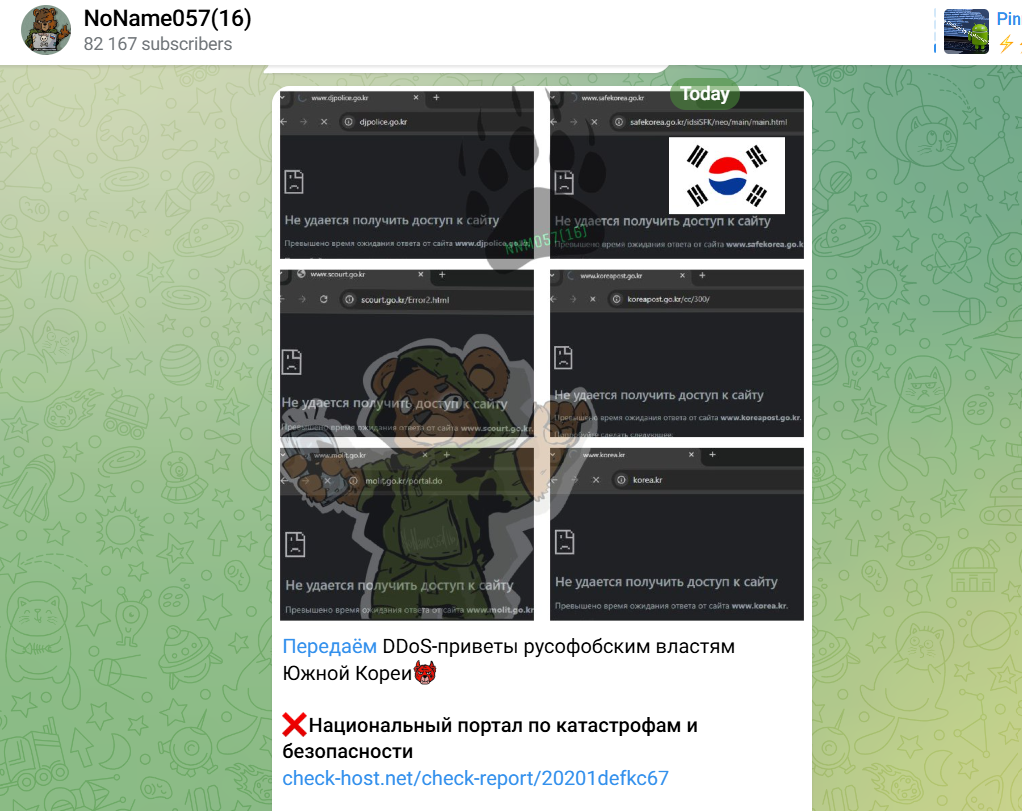
Image Credit: Securityaffairs
A surge in Pro-Russia cyberattacks after decision to monitor North Korean Troops in Ukraine
- South Korea claims Pro-Russia actors intensified cyberattacks on national sites after it decided to monitor North Korean troops in Ukraine.
- South Korea reports over 10,000 North Korean troops deployed in Russia to support the war in Ukraine, raising concerns of escalating conflict.
- South Korean government actively countering DDoS attacks from pro-Russian hacktivist groups targeting public and private websites.
- South Korea plans to enhance cyber threat preparedness through monitoring and collaboration among relevant agencies.
Read Full Article
14 Likes
Lastwatchdog
82

MY TAKE: Technology breakthroughs, emerging standards are coalescing to assure IoT integrity
- The Internet of Things (IoT) is growing at a compounded rate of 12%, and by 2030 an estimate suggested we will be relying on some 41 billion IoT devices worldwide. Ensuring that hyper-connected IoT devices are resilient against cyber threats requires technical innovation that infuses with supporting security standards and emerging government regulations much quicker and smoother than the speed of the Internet era.
- Infineon, for instance, is known for supplying secured, energy-efficient semiconductors and microcontrollers critical for IoT security. The Munich, Germany-based company has stepped forward to take a leading role in making security breakthroughs at the hardware level.
- Microcontrollers have emerged as a main ingredient for securing IoT services. Infineon designs microcontrollers to be much more capable and secured in IoT applications to help establish a trusted foundation at the outermost edges of modern IoT systems by safeguarding device integrity inside each IoT sensor and IoT controller.
- The EU and the US are pushing for stricter data security compliance rules. The EU's Cyber Resilience Act requires connected devices sold in Europe to meet cybersecurity benchmarks. Meanwhile, the U.S. Cyber Trust Mark will serve as a certification for secure consumer IoT devices. Infineon's innovations come as regulatory bodies are preparing for the strategic growth of the IoT market with compliance requirements acting as a global catalyst for consistent device security.
- Infineon is among the companies preparing for the future by developing post-quantum encryption to replace today's vulnerable asymmetric algorithms, posing a significant risk to connected systems.
- Proactivity is necessary towards taking a proactive stance on IoT security has become de rigueur, and every stakeholder must be vigilant in creating a safer hyperconnected digital ecosystem.
- Infineon's microcontrollers are optimized to prevent unauthorized access and preserve data integrity in everything from cars to smart home devices. Infineon has integrated a Hardware Security Module directly into their microcontrollers to enhance security in critical IoT applications like automotive systems.
- The EU's decision to enforce security requirements through the CE mark is powerful because it extends to non-European manufacturers who want access to the market.
- The securing of our increasingly hyper-connected digital world is unfolding in real-time, and it requires proactive measures to maintain the security between internet users and devices.
- Emerging standards, technologies are coalescing to ensure IoT integrity, and security must be embedded in each IoT device from the start.
Read Full Article
4 Likes
Dev
417

Image Credit: Dev
HardenEKS: The Easy Way to keep your AWS EKS clusters secure and compliant
- HardenEKS is an open source Python CLI that helps you programmatically validate if your EKS clusters follow best practices defined in the AWS EKS Best Practices Guide EBPG.
- HardenEKS is easy to use. Simply install it, run it against your EKS cluster, and it will generate a report of any violations.
- HardenEKS is a valuable tool for any EKS administrator who wants to keep their clusters secure and compliant.
- Before and after making significant changes to your cluster, HardenEKS captures a snapshot of your cluster's configuration status. This baseline serves as a reference point.
- Comparing these baselines allows you to detect drift—any unintended variations between configurations.
- HardenEKS facilitates this ongoing validation process and supports JSON output, which is highly beneficial.
- HardenEKS offers several additional options to tailor the checks to your specific needs.
- If you're interested in contributing to HardenEKS, we invite you to review our contribution guidelines.
- HardenEKS maintains a publicly accessible roadmap outlining the planned features for upcoming versions.
- HardenEKS is a potent Python-based Command Line Interface (CLI), capable of systematically assessing whether Amazon Elastic Kubernetes Service (Amazon EKS) clusters comply with the strict guidelines laid out in the AWS EKS Best Practices Guide (EBPG).
Read Full Article
25 Likes
Cybersecurity-Insiders
335

Image Credit: Cybersecurity-Insiders
Detect and Destroy APTs with Crystal Eye TDIR
- Red Piranha's Crystal Eye TDIR provides an advanced threat detection and response solution to protect against sophisticated attacks that can evade traditional defences.
- The solution adheres to global security standards and offers complete visibility across both network and endpoints.
- The rise of EDR evasion tools and LOTL attacks are major threats today, allowing attackers to bypass traditional endpoint security.
- Crystal Eye TDIR aligns with global guidelines by utilizing AI and machine learning, generating real-time alerts with incident response automation, providing complete network visibility with NDR, implementing efficient event logging with centralised log management, and supporting proactive threat hunting with extended log retention.
- Crystal Eye TDIR is scalable and compliant enough to detect, investigate and respond to advanced attacks across IT, cloud, and OT environments.
Read Full Article
20 Likes
Fintechnews
146

Image Credit: Fintechnews
Proposed Bill Could Allow Police to Restrict Bank Accounts of Potential Scam Victims
- The Protection from Scams Bill empowers the Singapore police to temporarily restrict banking transactions of potential scam victims.
- The measure is used as a last resort when persuading the potential victim has failed.
- The restrictions primarily target online and telecommunication scams.
- Individuals under restriction can apply to access their funds for essential needs.
Read Full Article
8 Likes
Global Fintech Series
335

Image Credit: Global Fintech Series
Sekady and Liquid Logics Forge Partnership to Enhance Workflow Automation and Security for Private Lenders
- Sekady and Liquid Logics have formed a partnership to enhance workflow automation and security for private lenders.
- Sekady's draw management and payment platform will be integrated with Liquid Logics' loan origination software.
- This collaboration aims to reduce manual errors and inefficiencies, streamline loan management operations, and enhance security.
- The partnership enables lenders to stay focused on growth while being supported against fraud and operational bottlenecks.
Read Full Article
20 Likes
Amazic
381

Image Credit: Amazic
9 Ways to Handle Secrets Management for Multi-Cloud Setups: Rotation, Auditing, and Access Control
- Gartner suggests that new security threats are among the biggest pain points for CIOs across businesses.
- Secrets management is an essential part of cybersecurity strategy for multi-cloud infrastructure.
- Managing secrets requires ways to protect them from breaches and unauthorized access and monitor their usage.
- Three main methods—rotation, auditing, and access control—can ascertain such proactiveness and vigilance in secrets management.
- Nine ways to implement these techniques are discussed with their contrast for different cloud vendors, namely AWS, Azure Cloud, and GCP Cloud.
- Secret rotation is the first line of defense where the secrets are consistently rotated or updated to minimize, if not eliminate, any breaches.
- Secret auditing allows security teams and cloud management experts to track when API tokens, encryption keys, and other such secrets were accessed and used for any services.
- Access control is critical for multi-cloud-based secrets management as it helps implement the principle of least privilege on the secrets.
- Multi-cloud infrastructure is one of the most sensible choices for businesses when dealing with cloud computing.
- Secrets management is necessary to maximize multi-cloud's potential while ensuring top-notch security and compliance.
Read Full Article
22 Likes
Fintechnews
307

Image Credit: Fintechnews
The Top Payment Fraud Trends in 2024
- The top payment fraud trends in 2024 have been highlighted in a report by Visa Payment Fraud Disruption (PFD). The report states that cybercriminals are increasingly leveraging AI to perpetuate fraud. Threat actors are also increasingly using AI to conduct reconnaissance on individual victims or victim organizations by scraping available information. The report highlights the surge of PRA attacks and the sharp rise in physical theft, where criminals would exploit the delay between theft and victim awareness. Ransomware and data breaches decreased in H1 2024. However, the overall number of individual ransomware and data breach incidents tracked by Visa PFD decreased by 12.3% in H1 2024 compared to H2 2023.
- PRA attacks result in potential losses of nearly US$184,000 for Visa's issuing partners, reflecting an increase in the average cost of 58% compared to H2 2023.
- Another trend highlighted in the report is a resurgence of physical theft. A new form of fraud, known as "digital pickpocketing", has emerged.
- In H1 2024, Visa PFD's Global Risk Investigations (GRI) team recorded a 6% decrease in digital skimming incidents targeting either e-commerce merchants or third-party providers, compared with H2 2023.
- The team observed a shift in focus, with the number of digital skimming attacks targeting third-party providers declining by a staggering 83% compared with H2 2023.
- Ransomware and data breaches are still a significant challenge, particularly as attackers are increasingly targeting third-party service providers to access more customer accounts at once.
- Digital skimming continues to be a prominent threat this year.
- Threat actors create a fraudulent merchant using merchant ecosystems, and register a mobile device as mPOS terminal to initiate a card-present-transaction on the mPOS.
- Visa PFD opened a record number of PRA investigations, accounting to 81% increase from H2 2023.
- Threat actors have been observed discussing the release of new AI technology, including malicious versions of AI chatbot programs in cybercrime underground marketplaces.
Read Full Article
18 Likes
Medium
211

Role of Artificial Intelligence
- Artificial intelligence (AI) has become indispensable in cybersecurity.
- AI-powered threat detection helps identify and mitigate evolving cyber threats.
- User and entity behavior analytics (UEBA) enhances the AI's ability to detect threats.
- Attackers are also using AI in cyber-attacks, including deepfake attacks, DoS attacks, and advanced persistent threats (APTs).
Read Full Article
12 Likes
Siliconangle
1.3k

Image Credit: Siliconangle
Israeli cybersecurity firm Upwind reportedly in talks to raise $100M on up to $900M valuation
- Israeli cybersecurity firm Upwind Security is reportedly in talks to raise $100 million in funding.
- The funding round is expected to value the company between $850 million and $900 million.
- Upwind Security offers a cloud-native application protection platform that secures cloud infrastructure and mitigates risks.
- The platform combines runtime data with build-time insights, providing efficient and unified cloud protection.
Read Full Article
23 Likes
For uninterrupted reading, download the app