Cyber Security News
TechCrunch
92

Image Credit: TechCrunch
FBI says hackers are sending fraudulent police data requests to tech giants to steal people’s private information
- Hackers are using fraudulent emergency data requests to steal private information from tech giants.
- The FBI warns about an increase in criminal posts advertising access to or conducting fraudulent data requests.
- Cybercriminals gain access to compromised government email addresses to masquerade as law enforcement.
- Companies are urged to apply critical thinking and strengthen cybersecurity measures to prevent such intrusions.
Read Full Article
5 Likes
Dev
78

Image Credit: Dev
BSides Orlando 2024: Insights, Innovations, and Security Adventures
- BSides Orlando 2024 was a security event that brought together professionals and students with a wide range of backgrounds.
- This year marked the most prominent BSides Orlando yet, with over 500 attendees attending two days of workshops and talks from industry experts.
- Partnering with the host venue, Full Sail University, BSides Orlando was able to grant multiple $5,000 scholarships to students who participated in the event.
- Former CIO of UbiSoft and CEO/Founder of Arcanum Security, Jason Haddix, took us through a history of AI use and laid out a path for all security professionals to better leverage this rapidly evolving technology.
- Alexander Cote, Lead Engineer at Abbot Laboratories, in his session "Cheaply and efficiently manage security events using datalake architectures," walked us through the problems of trying to manage all our logged events directly in SIEM tooling.
- "One Arrow, One Breach: The Medieval Mindset in Cyber Defense," Kevin Johnson, CEO at Secure Ideas talked about the need to spend time building traps and early warning systems when something or someone does not seem right.
- Michael Brown, Security Compliance Director at Financial Recovery Group, walked us through what it means to conduct assessments.
- This year's event theme was "Choose your own security adventure."
- With over 200 chapters worldwide, there is likely a BSides event near you soon.
- It is important to attend security events as well as conferences like DevOpsDays, Developer Days, and programming language-specific meetups to be part of the larger world of computer science conversations.
Read Full Article
4 Likes
Tech Radar
285

Image Credit: Tech Radar
Scammers are using fake copyright infringement claims to hack businesses
- Scammers are using fake copyright infringement claims to distribute the Rhadamanthys infostealer malware.
- The campaign targets various industries, with a focus on entertainment, media, and tech.
- The attackers use dedicated Gmail accounts and AI capabilities to automate the phishing attacks.
- Rhadamanthys infostealer is designed to steal sensitive information from infected systems.
Read Full Article
17 Likes
Cybersecurity-Insiders
234

Image Credit: Cybersecurity-Insiders
American Oilfield supplier Newpark Resources hit by ransomware attack
- Newpark Resources, a Texas-based company providing essential tools and services to the oil and gas industry, as well as the construction sector, was recently targeted in a ransomware attack that disrupted its financial and operational analytics systems.
- The attack, which occurred on October 29, 2024, partially crippled the company’s internal systems for a period, affecting its ability to function at full capacity.
- Newpark Resources acted swiftly to mitigate the impact. The company immediately notified the U.S. Securities and Exchange Commission (SEC) of the incident and activated its incident response team, which took prompt action to neutralize the threat and contain the damage.
- Newpark Resources reassured its stakeholders that the ransomware incident had been contained and that recovery efforts were ongoing.
- The timing of the attack especially raised concerns among cybersecurity experts as it occurred just one week before the 2024 U.S. elections, a period when many companies, including Newpark Resources, experience reduced staff levels due to the approaching holiday season, making businesses more vulnerable to cyber threats.
- Many high-profile ransomware attacks have impacted major players in recent years, endorsing the increasing sophistication of cybercriminals and evolving tactics they employ to infiltrate businesses.
- While no specific ransomware group has yet claimed responsibility for the Newpark Resources attack, cybersecurity experts are speculating that the Rhysida ransomware gang may be behind it.
- Investigators are continuing to gather evidence, and the full scope of the attack, as well as the identity of the perpetrators, remains unclear.
- The attack on Newpark Resources is a stark reminder of the ever-present threat of ransomware and the vulnerabilities that can exist in even the most well-established companies.
- Businesses must remain vigilant and ensure they have robust security measures in place to protect against such threats. Proactive cybersecurity measures are essential in mitigating the risks posed by modern cyber threats.
Read Full Article
14 Likes
Siliconangle
427

Image Credit: Siliconangle
Is generative AI hitting a ceiling? Maybe, but investors don’t care
- Venture capitalists Marc Andreessen and Ben Horowitz, who believe we will now be entering a wonderland of building under a Trump administration, wonder if generative AI models are hitting their limits.
- Nonetheless, investors keep pouring the money into AI companies such as Anthropic, Perplexity and Physical Intelligence.
- Plans by Amazon, Meta and Google to jumpstart nuclear plants to power all that AI could take a while.
- An open letter to Amazon calls for stock buybacks, more explanation of AI spending, and better management of its original-content ambitions.
- Supermicro's books present unsavoury signs as its stock tanks this week alongside weak earnings reports from Cloudflare and Akamai.
- Broadcom is expanding its VMware private-cloud options, which could prove good timing for the special edge needs of AI.
- Perplexity has finalised a new $500m funding round and will see its AI value soar to $9bn.
- Nvidia announces new robot AI learning and simulation tools.
- AMD overtook Intel for the first data center revenue in the third quarter, according to SemiAnalysis.
- Broadcom broadens private cloud options and Permiso launches three open-source tools to enhance cloud security detection.
Read Full Article
25 Likes
Tech Radar
32

Image Credit: Tech Radar
HPE reveals critical security bug affecting networking access points
- Hewlett Packard Enterprise (HPE) has released a patch for six serious security vulnerabilities affecting Aruba Networking Access Points.
- The vulnerabilities could allow for authenticated remote command execution attacks, arbitrary file creation, unauthenticated command injection, and more. Two of the vulnerabilities (CVE-2024-42509 and CVE-2024-47460) were particularly dangerous.
- The affected products include AOS-10.4.x.x, Instant AOS-8.12.x.x, and Instant AOS-8.10.x.x. Users are advised to update their access points to the recommended versions.
- Workarounds include blocking access to UDP port 8211, restricting access to management interfaces, and implementing firewall policies.
Read Full Article
1 Like
Mcafee
64

Image Credit: Mcafee
Every Step You Take, Every Call You Make: Is Your Phone Tracking You?
- Your smartphone stores and shares a lot of data with third parties, including data brokers who sell that info to anyone who’ll pay.
- Your phone can track you in several ways with varying degrees of accuracy, including GPS, cell towers, public Wi-Fi and Bluetooth.
- Certain apps pair location info with other info they collect while you use that app and share that precise combination of info with third parties.
- Your phone might know a lot about your health, including step counts, vital signs, and menstrual cycles.
- Companies make constant improvements to their devices and services, which might include the review of commands from users to make sure they are interpreted correctly.
- To lower the amount of tracking on your smartphone, you can turn off your phone or switch to Airplane Mode, turn off location services, provide permissions on an app-by-app basis, turn off app tracking, opt yourself out of cell phone carrier ad programs, delete old apps and remove your info from data broker sites.
Read Full Article
3 Likes
Tech Radar
441

Image Credit: Tech Radar
A critical Palo Alto Networks bug is being hit by cyberattacks, so patch now
- A critical bug found in Palo Alto Networks' Expedition program is being abused in the wild
- The bug allows threat actors to take over admin accounts and steal sensitive data
- CISA added the vulnerability to its KEV catalog, giving federal agencies a deadline to patch
- A workaround is available for those unable to install the patch immediately
Read Full Article
26 Likes
Tech Radar
133

Image Credit: Tech Radar
Nokia confirms data breach leaked third-party code, but its data is safe
- Nokia has confirmed a data breach involving a third party, but its own data is safe.
- The investigation found no evidence of impact on Nokia's systems or data.
- The breach occurred through a customized software application from a third-party vendor.
- The leaked archive contained source code and credentials, but did not endanger critical Nokia systems or customer data.
Read Full Article
8 Likes
Medium
377
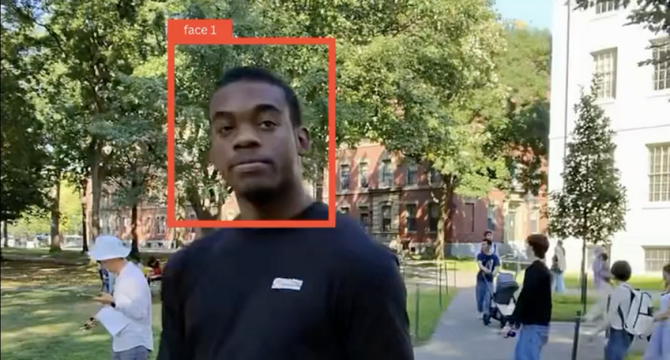
Image Credit: Medium
Ray-Ban Meta Smart Glasses Can Be Used to Dox Strangers — and Why This Matters
- Two Harvard students created a facial recognition app connected to Meta's smart glasses, which can dox complete strangers.
- The app pulls up names, contacts, addresses, and more just by looking at a person.
- This experiment highlights the privacy and security concerns associated with advanced AI technology.
- There is currently no clear solution to address these issues.
Read Full Article
22 Likes
Securityaffairs
294

Image Credit: Securityaffairs
iPhones in a law enforcement forensics lab mysteriously rebooted losing their After First Unlock (AFU) state
- Law enforcement warns that securely stored iPhones awaiting forensic examination are mysteriously rebooting, making them harder to unlock.
- The reboot causes the iPhones to lose their "After First Unlock" (AFU) state, making unlocking more difficult for law enforcement.
- The issue was documented by law enforcement officials in Detroit, who suspect it is due to a new security feature in iOS 18, causing iPhones to reboot when disconnected from cellular networks.
- Forensics labs are advised to isolate AFU devices from iOS 18 devices and check if any AFU devices have already rebooted.
Read Full Article
17 Likes
Tech Radar
225

Image Credit: Tech Radar
Rising AI threats are making firms turn back to human intelligence
- Almost half of security leaders consider AI as a significant threat to their organization.
- 10% of security researchers specialize in AI due to increasing demand for AI expertise.
- 55% of reported vulnerabilities are related to AI safety issues.
- 77% of security researchers are driven by potential income, while 67% believe unbiased human reviews are effective in uncovering AI security issues.
Read Full Article
13 Likes
Tech Radar
124

Image Credit: Tech Radar
Thousands of employees could be falling victim to obvious phishing scams every month
- A recent report claims that three in 1,000 banking employees click on a phishing link every month.
- Hackers often mimic the target bank's website to steal bank account information and login credentials.
- Russian criminal groups are found to be the primary perpetrators of phishing attacks on banks.
- Despite the threat, banks are more hesitant in adopting new technologies compared to other industries.
Read Full Article
7 Likes
Minis
1.5k
Image Credit: Minis
995 Crore Passwords Stolen In Biggest Data Breach Ever: Report
- In what's being called the largest data breach ever, 995 crore passwords were leaked by a hacker known as "ObamaCare".
- The dataset, named Rockyou2024, combines passwords from various breaches, posing a significant risk of credential stuffing and unauthorized access. This compilation, alongside other leaked databases, could lead to widespread data breaches, financial fraud, and identity thefts.
- Cybernews researchers urge enhanced cyber hygiene practices to mitigate risks. The breach underscores the critical need for robust cybersecurity measures globally, emphasizing the ongoing threat posed by large-scale data breaches.
Read Full Article
28 Likes
Minis
2.6k

Image Credit: Minis
Shadowy hacker claims he has data of 375 million Airtel users, Airtel says no breach in its systems
- A hacker claims to possess data of 375 million Airtel users, including sensitive information like phone numbers, Aadhaar numbers, and more.
- Airtel denies any breach, attributing the claim to misinformation aimed at damaging its reputation. The alleged data sale surfaced on forums frequented by cybercriminals, sparking concerns despite Airtel's assurances.
- Security experts debate the validity of the claim, urging vigilance in cyber hygiene practices like password updates, monitoring accounts, enabling 2FA, and avoiding phishing. Airtel emphasizes its systems' security while acknowledging past data breaches in Indian companies.
Read Full Article
24 Likes
For uninterrupted reading, download the app