Cyber Security News
Dev
432
Image Credit: Dev
The Most Potent Security Control on AWS
- Encryption is only as good as the security of the key.
- Amazon S3 encryption may not protect against a compromised Root account.
- Implementing least privilege with AWS IAM is crucial for effective security.
- IAM provides precise access control and temporary credentials for enhanced security.
Read Full Article
25 Likes
TechCrunch
239

Image Credit: TechCrunch
iPhones might be harder for police to unlock, thanks to new reboot feature
- New code introduced in the latest version of Apple’s mobile operating system could make it more difficult for both police and thieves to unlock iPhones.
- Law enforcement officials have reported that iPhones being stored for forensic examination are rebooting themselves, making it harder to unlock them using password-cracking tools.
- This reboot seems to occur after iPhones with iOS 18.1 have been in a locked state for four days.
- Security experts view this as a significant security improvement that doesn't inconvenience users but may inconvenience law enforcement.
Read Full Article
14 Likes
Securityaffairs
202
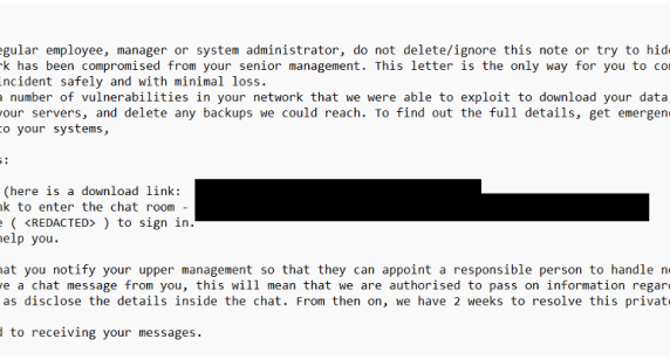
Image Credit: Securityaffairs
Veeam Backup & Replication exploit reused in new Frag ransomware attack
- A critical flaw, CVE-2024-40711, in Veeam Backup & Replication has been exploited to deploy Frag ransomware.
- Sophos researchers warned about the exploitation of the vulnerability, which allowed the creation of rogue accounts and malware deployment.
- Veeam released security updates in September 2024, fixing 18 high and critical severity flaws. The most severe one was the CVE-2024-40711 impacting Veeam Backup & Replication.
- Threat actors exploited the Veeam vulnerability to spawn net.exe and create a local account named 'point' to deploy ransomware such as Fog and Akira. Sophos recently found instances of Frag ransomware being deployed through the same exploit.
Read Full Article
12 Likes
TechJuice
266

Image Credit: TechJuice
Effective Ways to Detect and Eliminate Malware from Your Android Device
- Detecting and removing malware promptly is essential to maintaining the health and security of your device.
- Identifying and eliminating malware while providing preventive measures can keep your Android device safe.
- Methods to detect malware on Android include checking for software updates, identifying sideloaded apps, looking for suspicious apps, and monitoring your phone’s temperature and data usage.
- You need to beware of pop-ups and ads, as frequent pop-ups or redirects typically indicate the presence of malware.
- Monitoring battery usage and checking for administrative privileges can also help you detect malware.
- Scanning with antivirus apps such as Google Play Protect and removing malware manually by booting into safe mode, disabling administrative privileges and uninstalling infected apps can help eliminate malware.
- Preventive measures to avoid malware infections include downloading apps only from trusted sources, avoiding clicking suspicious ads, installing a trusted antivirus app, and using a VPN for Android.
- Consistently monitoring the behavior of your phone and adhering to sound security practices, you can guarantee the security of your device and achieve a sense of tranquility.
Read Full Article
16 Likes
Secureerpinc
78

Image Credit: Secureerpinc
Guarding Against the Growing Threat of Data Poisoning
- Data poisoning attacks the very heart of artificial intelligence systems by corrupting the dataset used to train machine learning or AI models.
- Spotting data poisoning attacks requires carefully monitoring the model's accuracy and performance, looking for sudden changes, biased results, or unexpected outcomes.
- Protecting against data poisoning involves implementing adversarial training, advanced data validation, and continuous monitoring of ML outputs.
- Addressing the threat of data poisoning also requires educating teams about ML security and encouraging reporting of suspicious outcomes.
Read Full Article
4 Likes
Tech Story
114

FBI Issues Urgent Warning on Rise of Fraudulent Emergency Data Requests
- The FBI has issued an urgent warning about cybercriminals exploiting compromised law enforcement and government email accounts.
- These criminals use fraudulent 'emergency' data requests to obtain private user data from U.S.-based technology companies.
- The misuse of emergency data requests has seen a sharp increase, with hackers using stolen credentials to access personal information.
- The FBI advises law enforcement agencies to strengthen their cybersecurity defenses and for tech companies to assess the legitimacy of emergency data requests.
Read Full Article
6 Likes
TechJuice
4

Image Credit: TechJuice
PTA Declares No Responsibility for Security of Electronic Devices
- The Pakistan Telecommunication Authority (PTA) has clarified that it is not responsible for the security of electronic devices such as pagers.
- The PTA's primary responsibility is to regulate telecommunication systems and terminal equipment and doesn't extend to identifying explosive materials.
- The PTA is responsible for regulating terminal devices, ensuring compliance with established standards and providing type certifications for telecommunication devices.
- The identification of explosive materials is not within the PTA's jurisdiction, and it referenced other agencies and regulations that handle these matters.
Read Full Article
Like
Medium
197
Image Credit: Medium
NordVPN subscription benefits review
- NordVPN offers a VPN service and effective online security features at an exceptional value during its Black Friday promotion, which includes a 74% discount and three extra months for free.
- The VPN service provides encryption technology designed to keep users' online presence secure and anonymous and boasts fast connection speeds and a comprehensive suite of features for safer online activities.
- Threat Protection scans downloads for malware, blocks obnoxious ads, and sends alerts if your credentials are compromised, while the platform's strict no-log policy assures users that their online actions aren't being recorded nor monitored.
- Moreover, users who subscribe to NordVPN can secure up to 10 gadgets simultaneously with a single subscription and can benefit from NordPass and NordLocker as part of the service.
- NordVPN's Black Friday offer enables users to start their subscription for as low as $2.99/month with a 30-day money-back guarantee.
- The VPN's user-friendly interface is highly intuitive, and customer support is available 24/7 through live chat and email.
- NordVPN holds industry accolades such as PCMag Editors’ Choice 2024 and Forbes Advisor Best of 2023.
- With millions of satisfied users trusting NordVPN for a safer browsing experience, users can rest assured that their online journey is in good hands and benefit from this exceptional Black Friday deal.
- Enhancing online security through NordVPN comes highly recommended for individuals prioritizing online privacy, speed, and robust security features.
- Signing up is a straightforward process, and users can browse confidently. With NordVPN, it is easy to join the world of secure browsing without any hassle.
Read Full Article
11 Likes
Medium
372

Image Credit: Medium
Compare Desktop VPN Services
- Desktop VPN services encrypt your connection, making it secure and safe from prying eyes, and NordVPN is a popular option.
- NordVPN’s advanced technology ensures that your devices remain malware-free, while its encryption is virtually unbreakable, keeping your online activities well-protected.
- One of NordVPN’s standout features is its ability to block malicious websites and web trackers that monitor your online activity.
- NordVPN offers a vast network of servers, providing impressive speeds suitable for everyday browsing, streaming, and downloading.
- NordVPN allows you to use the service on up to ten devices simultaneously, ensuring that every device is well-protected from prying eyes.
- The service actively scans and blocks potentially harmful websites, making your browsing experience even more secure.
- The premium password manager helps you generate strong passwords, auto-fill fields, and securely store your passwords for better protection.
- If you deal with sensitive data, NordVPN’s encryption feature is an excellent tool for encrypting your files before sending them over the internet.
- Some notable alternatives to NordVPN include ExpressVPN, CyberGhost, and Surfshark, which offer their unique features strengths and weaknesses.
- When choosing a VPN service, consider various factors that matter to you, such as features, pricing, and usability.
Read Full Article
22 Likes
Tech Radar
381

Image Credit: Tech Radar
This new phishing strategy utilizes GitHub comments to distribute malware
- GitHub repositories are being infected with malware
- Trusted repositories can bypass secure web gateways
- GitHub comments are also being used to hide malicious files
- Phishing campaign leverages trusted GitHub repositories to distribute malware
Read Full Article
22 Likes
Dev
294

Image Credit: Dev
Using SSH to Connect Local Git to Remote Repositories
- This blog post explains how to use SSH to connect local git to remote repositories.
- SSH is a protocol that allows secure communication between a local machine and a remote host, while Git is a distributed version control system.
- Different methods to connect to a remote repository are HTTPS and SSH, but SSH offers a greater level of security.
- Using a password-based authentication, HTTPS may be vulnerable if someone intercepts the network, compares to SSH, which uses a private-public key pair.
- SSH is more convenient than HTTPS which eliminates the need to enter passwords by using an SSH-Agent which stores a passphrase securely in memory and automate the authentication process.
- To use SSH, the first step is to generate SSH keys. The most commonly used algorithm is Ed25519.
- After generating a private-public key pair, you can check whether you have an SSH key or generate a new key if required.
- Next, add the public key to the remote repository by copying the key from your local machine and pasting it into the remote repository.
- To connect your private SSH key to the website of the remote repository, add it to ssh-agent.
- Finally, testing the SSH connection will let you concludes if everything goes smoothly. You're now ready to use SSH to connect local git to remote repositories and make changes in a secure way.
Read Full Article
17 Likes
Pymnts
1.5k

Image Credit: Pymnts
Visa and Tencent to Launch Pay-by-Palm Solution in Singapore
- Visa and Tencent partnered to launch a pay-by-palm solution in Singapore.
- The collaboration combines Tencent's palm recognition technology and Visa's payment token.
- The pay-by-palm service will begin with a pilot program in Singapore involving Visa cardholders from participating banks and a café called Alchemist.
- Participants will enroll by tapping their Visa card, scanning their palm, and completing a one-time authentication.
Read Full Article
9 Likes
Medium
401

Image Credit: Medium
Choosing the Best DNS Server: Speed, Privacy, and Customization Compared
- DNS servers play a crucial role in the functioning of the internet, as they help translate human-readable website addresses into IP addresses.
- Choosing the best DNS server is important for factors such as security, privacy, and speed.
- DNS servers allow devices to locate the IP addresses of websites they want to communicate with.
- Remembering IP addresses is difficult for humans, which is why DNS servers are necessary.
Read Full Article
24 Likes
Tech Radar
198

Image Credit: Tech Radar
This new malware utilizes a rare programming language to evade traditional detection methods
- A new form of malware called Pronsis Loader has been discovered by Trustwave SpiderLabs.
- Pronsis Loader utilizes JPHP, a rarely used programming language, to evade traditional detection methods.
- The malware employs advanced installation techniques and obfuscation to avoid triggering security tools.
- Once installed, Pronsis Loader can download and execute additional malware, making it highly flexible for attackers.
Read Full Article
11 Likes
Medium
134

Image Credit: Medium
AI and Cybersecurity: Mastering the Digital Battleground in 2024
- The integration of Artificial Intelligence (AI) in cybersecurity is transforming the security landscape.
- AI's ability to analyze data rapidly helps in real-time threat detection and automated responses.
- However, cybercriminals are also utilizing AI to optimize attack processes and complicate detection efforts.
- The future of AI in cybersecurity will require continuous advancements to keep pace with AI-driven threats.
Read Full Article
8 Likes
For uninterrupted reading, download the app