Cyber Security News
Osxdaily
247

Image Credit: Osxdaily
How to Enable iCloud Private Relay on Mac
- iCloud Private Relay is a privacy feature part of iCloud+ subscription that hides IP address & encrypts DNS lookups to enhance online privacy.
- To enable iCloud Private Relay on Mac, go to System Preferences, click on your Apple ID, select iCloud, and toggle Private Relay switch to ON.
- Ensure you have a modern MacOS version (Monterrey or later) and a paid iCloud subscription for access to this feature.
- With Private Relay enabled, your IP address is hidden, providing more privacy, but custom DNS settings are disabled for security reasons.
- To disable iCloud Private Relay, follow the same steps and toggle the setting to OFF position in System Preferences.
- iCloud Private Relay encrypts internet traffic in Safari through two separate relays, enhancing privacy without being a VPN.
- It ensures websites and third parties can't track your online activities effectively, enhancing online privacy for Safari users.
- Enabling iCloud Private Relay on all your devices is recommended for consistent privacy protection across platforms.
- Paid iCloud subscription is required for this feature, and using other browsers like Chrome will not activate Private Relay.
- It's a seamless integration for privacy-conscious users, but may require disabling for specific website compatibility.
Read Full Article
14 Likes
Medium
99

A software engineer’s data security and privacy insights for Mac users
- FileVault only encrypts data when the Mac is powered off or locked, leaving data vulnerable when the system is in use.
- HDDs and SSDs require different data destruction methods, with macOS lacking a proper secure deletion feature in recent versions.
- An app called VaultSort addresses these gaps by providing proper DOD-standard secure deletion and individual file encryption.
- The app allows for selective encryption of files or directories with strong encryption, catering to non-technical users' needs.
Read Full Article
5 Likes
Tech Radar
351

Image Credit: Tech Radar
Misspelled a site's name? Cybercriminals are exploiting this to infect your computer with malware - here's how to stay safe
- Hackers are exploiting typos in popular package names to inject malware into developers' systems.
- A supply chain attack revealed attackers are targeting Colorama and Colorizr users with fake packages.
- By using typosquatting techniques, attackers upload fake packages to repositories to gain control over systems.
- Developers are advised to be cautious, double-check package sources, and proactively audit deployable packages to avoid falling victim to these malicious tactics.
Read Full Article
21 Likes
VentureBeat
328

Image Credit: VentureBeat
Phonely’s new AI agents hit 99% accuracy—and customers can’t tell they’re not human
- Phonely, Maitai, and Groq collaboration achieves breakthrough in conversational AI by reducing response times, increasing accuracy, and eliminating awkward delays that reveal machine nature of interactions.
- The partnership enables Phonely to surpass GPT-4o's benchmark with 99.2% accuracy and improve performance across four model iterations.
- Groq's zero-latency LoRA hotswapping and Maitai's optimization platform play key roles in enhancing AI model performance and reducing latency in phone interactions.
- The solution addresses the 'uncanny valley' of voice AI, making automated conversations more human-like and transformative for call centers and customer service operations.
- The improvements in response times and accuracy make AI phone agents indistinguishable from humans, leading to significant business outcomes like increased qualified leads and cost savings for call centers.
- Phonely excels in appointment scheduling and lead qualification, showing substantial performance improvements compared to legacy providers in industries like insurance, legal, and automotive.
- Groq's Language Processing Units (LPUs) provide specialized AI inference chips optimized for language processing, offering scalability and efficiency for AI deployment.
- The partnership's rapid deployment capability allows same-day transitions for companies already using general-purpose models, addressing concerns about lengthy implementation timelines.
- The shift towards specialized, task-specific AI systems signals a change in enterprise AI architecture, emphasizing purpose-built solutions over monolithic models for improved performance and scalability.
- The collaboration's success showcases the potential of AI infrastructure companies working together to overcome complex deployment challenges and set new standards for automated customer interactions.
- The advancements in conversation AI technology indicate a future where artificial phone conversations may soon be indistinguishable from human interactions, driving innovation and competitiveness in the AI sector.
Read Full Article
19 Likes
Securityaffairs
31

Image Credit: Securityaffairs
U.S. CISA adds ASUS RT-AX55 devices, Craft CMS, and ConnectWise ScreenConnect flaws to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added ASUS RT-AX55 devices, Craft CMS, and ConnectWise ScreenConnect flaws to its Known Exploited Vulnerabilities catalog.
- ConnectWise detected suspicious activity from an advanced nation-state actor impacting a small number of its ScreenConnect customers due to CVE-2025-3935, a vulnerability that may have led to a breach.
- A new AyySSHush botnet with over 9,000 compromised ASUS routers exploits an authenticated command injection flaw (CVE-2023-39780) to establish a persistent SSH backdoor.
- Federal agencies have until June 23, 2025, to address the identified vulnerabilities in the catalog as per the Binding Operational Directive (BOD) 22-01 issued by CISA.
Read Full Article
1 Like
Tech Radar
176

Image Credit: Tech Radar
Billions of Chrome users at risk from new data-stealing browser vulnerability - here's how to stay safe
- A zero-day vulnerability, CVE-2025-4664, affecting both Windows and Linux systems has been discovered in Google Chrome and Chromium browsers, putting billions of users at risk of data theft.
- The vulnerability allows the leakage of sensitive cross-origin data like OAuth tokens and session identifiers, without user interaction, through the handling of the Link HTTP header for sub-resource requests.
- Google has issued an emergency patch for Windows and Gentoo Linux systems, urging users to update their browsers immediately. Chromium users on Debian 11 remain vulnerable with no updated package available yet, advised to uninstall until patched.
- Experts recommend using endpoint protection platforms, malware protection, and antivirus solutions in addition to applying browser patches to combat browser-based zero-day exploits.
Read Full Article
10 Likes
TechBullion
40

Image Credit: TechBullion
Zircuit Joins Binance Alpha: ZRC Airdrop and Trading Competition Go Live
- Zircuit has been featured on Binance Alpha, an exclusive platform for early-stage Web3 projects.
- An airdrop of 80 million ZRC tokens through Binance Alpha and a ZRC trading competition with a 27.5 million ZRC prize pool are being launched by Zircuit in celebration.
- Starting from June 3 at 8:30 UTC, eligible Binance users with at least 211 Alpha points can claim their ZRC allocation directly from the Alpha Events page.
- Following the airdrop, a ZRC trading competition with 27,500,000 ZRC in rewards will be initiated by Zircuit, with more details to be announced.
Read Full Article
2 Likes
Medium
207
Image Credit: Medium
Part 12 — How I Run My Entire Digital Life on a Raspberry Pi: Unify and Elevate your…
- The article discusses setting up a Keycloak stack using a docker-compose file.
- Keycloak concepts such as realms, applications (clients), and users are explained.
- The process of creating realms, users, and setting up login credentials in Keycloak is detailed.
- Instructions on creating an admin user, assigning roles, and ensuring security are provided.
- Steps to register an application (Grafana) for Single Sign-On (SSO) with Keycloak are outlined.
- Configuring Keycloak client for Grafana SSO with necessary settings like Client Authentication and Valid redirect URIs.
- Obtaining the Client secret from Keycloak for Grafana setup and configuring necessary environment variables.
- The process of disabling the standard login form on Grafana for Keycloak-based authentication.
- After deployment and configuration, users can log in to Grafana using Keycloak credentials successfully.
Read Full Article
12 Likes
Medium
288

Day 17 of #60DaysofGRC: What’s the Difference Between a PIA and a DPIA (and When Do You Need One)?
- PIA and DPIA share similar structures but differ in regulatory roots and triggers.
- In the U.S., DHS requires PIAs for privacy compliance in public agencies, financial institutions, health organizations, and any business handling PII.
- DPIA helps protect data subjects' rights and ensures GDPR compliance under Article 35.
- Engage in cybersecurity discussions and learning with the author through their blog and LinkedIn for insights on GRC, Red/Blue teaming, and building cyber skills.
Read Full Article
17 Likes
TechBullion
410

Image Credit: TechBullion
RELIANOID: The Challenger in Load Balancing and Application Security
- RELIANOID is a fast-growing player in load balancing and application security, offering reliable, high-performance, and security-focused solutions tailored for modern IT infrastructures.
- RELIANOID's flagship offering is a comprehensive, Linux-based load balancing platform that supports Layer 4 and Layer 7 load balancing, focusing on high availability with features like hot restart capabilities and real-time health checks.
- The platform integrates application security features and supports real-time logging and integration with SIEM systems for faster threat detection and response.
- RELIANOID provides transparency, extensibility, and flexibility by running on standard Debian-based Linux systems and supporting automation and deployment through tools like Ansible, Terraform, or Kubernetes.
Read Full Article
24 Likes
Tech Radar
328

Image Credit: Tech Radar
Chat Control – Poland's EU Presidency gives up on the voluntary scan of your encrypted chats
- Poland's EU Presidency has given up on making the scanning of encrypted chats voluntary, failing to find a majority agreement.
- The disputed child sexual abuse (CSAM) scanning bill couldn't secure necessary majority support among EU members.
- The EU Commission introduced the Chat Control proposal in May 2022 to require scanning of users' chats, including encrypted ones.
- Denmark, set to take over EU Presidency in July, may continue pushing the controversial Chat Control proposal.
Read Full Article
19 Likes
Tech Radar
225
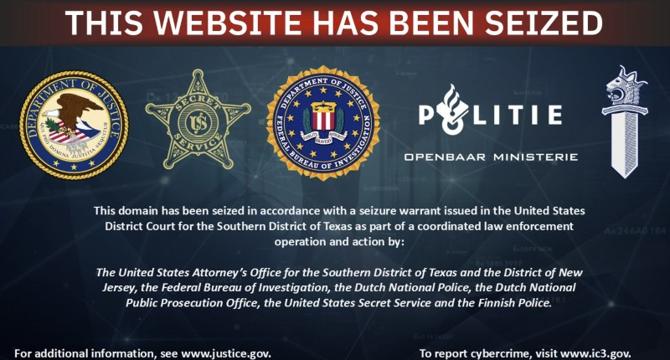
Image Credit: Tech Radar
FBI, Secret Service operation takes down AVCheck site used to test malware
- The FBI, along with Dutch and Finnish police, has shut down AVCheck.net, a website offering analysis services for cybercriminals.
- AVCheck was a Counter Antivirus (CAV) service that allowed cybercriminals to test malware against multiple antivirus engines without detection.
- The takedown operation also dismantled two crypting services, Cryptor.biz and Crypt.guru, used by criminals to hide malware and evade detection.
- The operation, known as Operation Endgame, aimed to disrupt cybercriminal activities early on and prevent victimization.
Read Full Article
13 Likes
Wired
238

Image Credit: Wired
How the Farm Industry Spied on Animal Rights Activists and Pushed the FBI to Treat Them as Bioterrorists
- Top lobbyists and representatives of the agricultural industry collaborated with the FBI to surveil and target animal rights organizations over nearly a decade.
- The FBI's Weapons of Mass Destruction Directorate and the Animal Agriculture Alliance worked together to monitor activists like Direct Action Everywhere (DxE) and labeled them as a 'bioterrorism' threat.
- The AAA supplied federal agents with intelligence on animal rights groups and used undercover operatives to gather strategic information.
- The alliance aimed to shield industry actors from public scrutiny, press for investigations against critics, and portray animal rights activists as a national security menace.
- State authorities cited protests as reasons to withhold information about disease outbreaks at factory farms from the public.
- Animal cruelty investigator Zoe Rosenberg from DxE faced charges for rescuing chickens, highlighting the conflict between private-sector surveillance and law enforcement priorities.
- The AAA surveilled DxE for years, infiltrating meetings and events to monitor activities and gather information.
- The FBI sought records of activist incidents on farms through interactions with the AAA, aiming to use 'terrorism' charges against activists instead of legal violations.
- The AAA sought closer ties with the FBI to share information about groups like DxE, emphasizing concerns about 'extremist campaigns.'
- The alliance's tactics and collaboration with law enforcement agencies have raised concerns about civil liberties, health, and transparency within the animal agriculture industry.
Read Full Article
14 Likes
TechCrunch
207

Image Credit: TechCrunch
Indian grocery startup KiranaPro was hacked and its servers deleted, CEO confirms
- Indian grocery startup KiranaPro was hacked, and all its data was wiped, including app code and servers with customer information.
- KiranaPro, with 55,000 customers and 30,000-35,000 active buyers, operates as a buyer app on the Indian government’s Open Network for Digital Commerce.
- Hackers gained access to KiranaPro’s root accounts on AWS and GitHub, leading to the deletion of Electric Compute Cloud services and a halt on processing orders.
- KiranaPro is filing cases against former employees and seeking help from GitHub's support team to identify the hacker's IP addresses and traces of the incident.
Read Full Article
12 Likes
Tech Radar
292

Image Credit: Tech Radar
Qualcomm finally patches Adreno GPU zero-day flaws used in Android attacks
- Qualcomm has patched three Adreno GPU zero-day vulnerabilities (CVE-2025-21479, CVE-2025-21480, CVE-2025-27038) that were being exploited in the wild since January 2025.
- Google Threat Analysis Group hints at limited, targeted exploitation of the vulnerabilities.
- Qualcomm has provided the patches to OEMs with a strong recommendation to deploy them on affected devices as soon as possible.
- No specific details on the attackers using the vulnerabilities have been disclosed, but similar flaws have been utilized in spyware campaigns in the past.
Read Full Article
16 Likes
For uninterrupted reading, download the app