Cyber Security News
TechJuice
206

Image Credit: TechJuice
“Operation Grey” Revvs Up Against Major Scam Call Centers in Pakistan
- Authorities in Pakistan launch Operation Grey to crack down on scam call centers involved in fraudulent activities.
- Operation Grey, led by the Federal Investigation Agency (FIA) and Pakistan Telecommunication Authority (PTA), aims to dismantle large-scale networks engaged in scam operations targeting individuals inside and outside Pakistan.
- The FIA has already conducted raids and shut down several scam centers in Lahore, Islamabad, and Karachi. They have arrested individuals linked to the scams and are working on tracking down their associates.
- PTA has played a crucial role in blocking illegal numbers used by fraudsters to impersonate government officials and others. International cooperation with Interpol and foreign cybercrime units is underway to trace cross-border networks. Public awareness campaigns and enhanced cyber laws are part of the government's efforts to combat such scams.
Read Full Article
12 Likes
Tech Radar
143

Image Credit: Tech Radar
More than 3 million records, 12TB of data exposed in major app builder breach
- Passion.io, a major no-code app-building app, operated a non-password-protected database.
- The exposed archive contained 3,637,107 records totaling 12.2TB, but has since been locked down.
- Sensitive information like names, email addresses, and payment details of users and app creators was found in the database.
- Passion.io confirmed taking swift action to enhance security measures and prevent such incidents in the future.
Read Full Article
8 Likes
TechCrunch
13

Image Credit: TechCrunch
Anthropic unveils custom AI models for U.S. national security customers
- Anthropic has unveiled a new set of AI models specifically designed for U.S. national security customers, called the 'Claude Gov' models.
- These custom models cater to government operations like strategic planning, operational support, and intelligence analysis, and are currently deployed at the highest levels of U.S. national security.
- Anthropic's Claude Gov models have undergone rigorous safety testing and offer enhanced capabilities in handling classified information, languages critical to national security, and interpreting complex cybersecurity data.
- Other AI labs, such as OpenAI, Meta, and Google, are also actively pursuing defense contracts by offering specialized AI models for government and defense applications.
Read Full Article
Like
Hitconsultant
350

Image Credit: Hitconsultant
Lessons Learned from The Change Healthcare Cyberattack, One Year Later
- Change Healthcare experienced the largest medical data breach in U.S. history, affecting over 190 million individuals and causing significant system outages.
- The cyberattack on Change Healthcare highlighted the vulnerability of healthcare organizations to third-party vendor attacks.
- UnitedHealth Group, Change Healthcare's parent company, paid a $22 million ransom to resolve the cyberattack aftermath.
- Healthcare providers must assess and audit third-party vendors to mitigate cybersecurity risks and ensure adherence to regulations.
- Establishing robust business continuity plans is crucial for healthcare organizations to minimize downtime during cyber crises.
- Continuous preparation and testing of disaster response protocols are essential for healthcare providers to maintain critical operations.
- Healthcare organizations must acknowledge that cyber risk is persistent and implement tailored cybersecurity solutions and staff training.
- Collaboration among healthcare providers is key to sharing best practices, addressing challenges, and enhancing cybersecurity measures.
- Seeking insights from cybersecurity experts can benefit healthcare providers in fortifying their security posture against evolving threats.
- Proactively addressing cybersecurity threats is crucial for healthcare organizations to safeguard sensitive data and maintain high security standards.
Read Full Article
21 Likes
Siliconangle
134

Image Credit: Siliconangle
Tuskira integrates with ServiceNow to bring AI-driven threat validation to SecOps workflows
- Tuskira Inc. integrates with ServiceNow Inc. to enhance exploitability validation, simulation-backed scoring and posture-aware mitigation.
- The collaboration embeds Tuskira’s Agentic AI Analysts into ServiceNow’s Vulnerability Response and Security Operations modules for faster and smarter threat response.
- Tuskira's AI Analysts simulate attackers' movements in enterprise environments, validate existing controls, and transform vulnerabilities into resolved risks.
- The integration with ServiceNow provides exploitability and defense validation in a single platform, accelerating decision-making and enhancing threat response without workflow rewrites.
Read Full Article
8 Likes
Pv-Magazine
179

Danish energy sector probes removes concerns about solar involvement
- Danish trade group rules out any link between suspicious components in energy equipment and compromised solar inverters in the US.
- Green Power Denmark confirms unknown components found are unrelated to solar inverters, distancing from recent US concerns regarding Chinese-made PV equipment.
- The investigation continues, focusing on broader energy supply technology rather than the solar sector.
- Discovery of components prompts ongoing investigation to determine their nature and intent, raising concerns about cybersecurity risks in Europe's energy infrastructure.
Read Full Article
10 Likes
VentureBeat
233
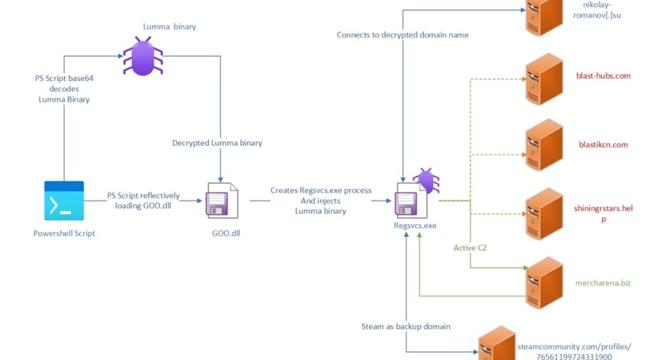
Image Credit: VentureBeat
Demystifying Myth Stealer: An ‘InfoStealer’ that targeted video games | Trellix
- Trellix's Advanced Research Center discovered a fully undetected infostealer malware called Myth Stealer targeting games, written in Rust code and marketed on Telegram.
- Infostealers infiltrate systems to collect passwords, cookies, credit card info, and more from browsers, setting apart Myth Stealer with its Rust code written in a less common language.
- Using Rust gives Myth Stealer wider platform support for the malware's execution, potentially increasing the exposure for victim organizations.
- Myth Stealer was promoted on Telegram with advanced features appealing to cybercriminals, initially offered for free trial and later shifted to a subscription model.
- The malware is distributed through fraudulent gaming websites, targeting browsers like Gecko and Chromium, extracting sensitive data and utilizing anti-analysis techniques.
- Myth Stealer's authors update the code frequently to avoid antivirus detection, adding features like screen capture and clipboard hijacking.
- The malware is now offered on a subscription basis through cryptocurrency and Razer Gold, with a separate channel for testimonials and compromised account sales being shut down by Telegram.
- Myth Stealer was distributed disguised as game-related software on fraudulent gaming websites, and as a crack for game cheating software in online forums.
- The malware evolved from stealing data in free versions to subscription-based with additional functionalities like fake windows, screenshots, and clipboard hijacking.
- Myth Stealer's consistent updates and enhancements, like string obfuscation and fake windows, challenge endpoint security solutions to detect it, posing a persistent risk to users.
Read Full Article
14 Likes
Ubuntu
40

Image Credit: Ubuntu
What if your container images were security-maintained at the source?
- Software supply chain security is a growing concern due to open source vulnerabilities in applications.
- Canonical has introduced the Container Build Service to address these challenges.
- Organizations are adopting OSS to reduce costs, accelerate development, and increase reliability.
- 84% of codebases contain at least one known open source vulnerability, with 50% categorized as high-severity.
- Supply chain attacks are on the rise, leading to an increased focus on container image integrity.
- Canonical's Container Build Service offers reproducible, security-maintained container images with up to 12 years of support.
- The service guarantees security updates for the entire container, covering all dependencies, not just OS components.
- Canonical's chiseled Ubuntu container images reduce image size and attack surface, enhancing performance and security.
- Chiseled images include only essential components, leading to faster start-up times and lower memory usage.
- The Container Build Service builds on Ubuntu Pro's long-term support policies, providing comprehensive security maintenance for containers.
Read Full Article
2 Likes
Dev
283

Image Credit: Dev
How to Generate an AI SBOM, and What Tools to Use
- AI systems rely on various third-party components, making them vulnerable to security risks without proper tracking.
- While SBOMs enhance transparency, security, and governance, their adoption in AI projects is limited.
- Challenges in SBOM adoption for AI projects include complexity, lack of standardization, integration difficulties, and dynamic components.
- Slow SBOM adoption exposes organizations to security vulnerabilities, compliance challenges, reduced accountability, and supply chain risks.
- SBOMs in AI projects offer enhanced security, traceability, transparency, collaboration, maintenance, and auditability.
- Tools for creating AI SBOMs include container-based SBOM tools, model-oriented SBOM frameworks, and registry-based SBOM management.
- New tools extend SBOM capabilities to address the needs of AI projects, including tracking model lineage, dataset information, and provenance.
- Effective integration of SBOMs into AI development workflows is essential for AI governance and compliance requirements.
- Adoption of AI-specific SBOM tools can help safeguard models, ensure compliance, and maintain transparency in AI projects.
- AI SBOMs play a crucial role in maintaining security, compliance, and transparency in modern AI projects.
- Tools like KitOps and Jozu Hub offer solutions for generating and managing AI SBOMs to protect models against security threats and ensure project integrity.
Read Full Article
17 Likes
Kraken
436

Image Credit: Kraken
Crypto complacency: The hidden security threats at industry conferences
- Crypto conferences are growing larger globally, signaling mainstream adoption of crypto.
- Personal security measures at these conferences have been overlooked, posing security risks.
- Precautions like securing devices, avoiding broadcasting wealth publicly, and being cautious with QR codes are advised.
- Maintaining basic situational awareness, limiting sensitive conversations, and staying vigilant at events are highlighted for personal safety.
Read Full Article
26 Likes
TechJuice
260

Image Credit: TechJuice
EddieStealer Malware Exploits Fake CAPTCHAs to Steal Credentials
- Elastic Security Labs discovered a new Rust-based infostealer called EddieStealer, which tricks users with fake CAPTCHA pages to steal credentials.
- EddieStealer spreads through deceptive CAPTCHA interfaces on adversary-controlled domains, appearing authentic to fool users.
- The malware uses a complex infection mechanism involving obfuscated JavaScript payloads and PowerShell commands to download and execute malicious scripts.
- To combat analysis and detection, EddieStealer utilizes obfuscation techniques, sandbox evasion, and data exfiltration capabilities targeting sensitive information.
Read Full Article
15 Likes
Medium
418

Image Credit: Medium
Signal Under the Hood — What Activists & Journalists Need to Know About the Risks Beyond Encryption
- Signal is a widely trusted messaging app, but understanding its vulnerabilities beyond encryption is crucial for activists and journalists.
- Signal's centralized servers in the US make it subject to US laws, potentially exposing data to legal demands like National Security Letters.
- The closed-source spam filter in Signal introduces a trust element, deviating from the open-source security principle.
- Signal Desktop poses security risks with unencrypted attachments, database key vulnerabilities, and potential exposure of data on the hard drive.
- Metadata like delivery receipts and jurisdictional issues raise concerns for activists and journalists using Signal.
- The funding origins of Signal and governance connections raise questions about independence and susceptibility to influence.
- Security threats like device compromise and adversaries using spyware like Pegasus highlight the limitations of encrypted communication tools.
- For high-risk users, minimizing desktop use, protecting data at rest, verifying safety numbers, and utilizing secure devices are essential practices.
- Signal's encryption protects message content in transit, but considerations like metadata, jurisdiction, and spyware risks must be part of the security analysis.
- Balancing Signal's strengths with its vulnerabilities, especially in high-risk scenarios, requires a comprehensive security strategy beyond relying solely on the app.
Read Full Article
25 Likes
TechBullion
62

Image Credit: TechBullion
Top 10 Cybersecurity Companies in UAE [2025]
- Leading cybersecurity companies in the UAE focus on protecting industries like banking, healthcare, and government from digital threats.
- CPX is a prominent cybersecurity company in the UAE, offering comprehensive solutions and proactive security measures.
- CPX's integrated framework enables organizations to identify vulnerabilities, strengthen defenses, monitor threats, and respond quickly to incidents.
- Other notable cybersecurity firms in the UAE include CyberGate Defense, Wattlecorp, Help AG, Resolution IT, Mindfire, ITSEC, VRS Technologies, ValueMentor, and EDCS.
- These companies provide various cybersecurity services, including threat monitoring, incident response, risk assessments, and compliance measures.
- Firms like ITSEC have received accolades for their excellence in cybersecurity and serve a diverse clientele, including leading organizations like Netflix and DHL.
- Cybersecurity companies in the UAE use advanced technologies like AI-driven tools, XDR, SIEM, and Zero Trust frameworks to enhance security measures.
- Choosing a cybersecurity partner in the UAE involves considering factors like industry experience, certifications, end-to-end protection, local presence, and use of modern tools.
- Continuous monitoring, real-time alerts, and personalized solutions are essential offerings from cybersecurity firms to ensure businesses are well-protected 24/7.
- Overall, cybersecurity companies in the UAE play a critical role in safeguarding digital assets, maintaining compliance, and supporting the nation's digital infrastructure.
Read Full Article
3 Likes
Tech Radar
215

Image Credit: Tech Radar
Microsoft launches free cybersecurity protection for European governments against AI threats and more
- Microsoft is launching a new European Security Program to offer free cybersecurity protection to European governments against AI threats and state-sponsored attacks from countries like Russia, China, Iran, and North Korea.
- The program includes additional threat intelligence sharing, increased cybersecurity investment, and partnerships - all provided at no cost to European governments.
- Microsoft aims to improve response times against AI threats by providing cutting-edge AI insights, enhancing intelligence sharing and collaboration, advising on vulnerabilities, and focusing on foreign-influence and disinformation campaigns.
- The program will cover all EU member states, EU accession countries, EFTA members, as well as the UK, Monaco, and the Vatican, reflecting Microsoft's commitment to safeguarding Europe's digital infrastructure.
Read Full Article
12 Likes
Analyticsindiamag
85

Image Credit: Analyticsindiamag
Synology ActiveProtect: Closing the Cyber Resilience Gap in Indian Enterprises
- India has faced a surge in cyberattacks, with 95 organizations experiencing data breaches in 2024.
- Cyber breaches cost the Indian economy an average of ₹19.5 crore, impacting various industries.
- The complexity of IT environments and cloud reliance have made enterprises vulnerable to sophisticated threats.
- The Digital Personal Data Protection Act in India has emphasized data protection measures for organisations.
- Indian organizations need a strategic data protection approach to prevent and recover from cyber incidents.
- Implementing 3-2-1-1-0 backup strategy with verifiable restoration is crucial for cyber resilience.
- ActiveProtect by Synology enhances backup protection against ransomware with air-gapped storage and integrity checks.
- It simplifies data protection management across multiple sites and vendors for sectors like BFSI and healthcare.
- ActiveProtect offers fast performance, advanced deduplication, and cross-platform recovery capabilities.
- The appliance supports role-based access controls, bare-metal restoration, and versatile recovery options.
Read Full Article
5 Likes
For uninterrupted reading, download the app