Cyber Security News
Analyticsindiamag
85

Image Credit: Analyticsindiamag
Synology ActiveProtect: Closing the Cyber Resilience Gap in Indian Enterprises
- India has faced a surge in cyberattacks, with 95 organizations experiencing data breaches in 2024.
- Cyber breaches cost the Indian economy an average of ₹19.5 crore, impacting various industries.
- The complexity of IT environments and cloud reliance have made enterprises vulnerable to sophisticated threats.
- The Digital Personal Data Protection Act in India has emphasized data protection measures for organisations.
- Indian organizations need a strategic data protection approach to prevent and recover from cyber incidents.
- Implementing 3-2-1-1-0 backup strategy with verifiable restoration is crucial for cyber resilience.
- ActiveProtect by Synology enhances backup protection against ransomware with air-gapped storage and integrity checks.
- It simplifies data protection management across multiple sites and vendors for sectors like BFSI and healthcare.
- ActiveProtect offers fast performance, advanced deduplication, and cross-platform recovery capabilities.
- The appliance supports role-based access controls, bare-metal restoration, and versatile recovery options.
Read Full Article
5 Likes
Hackernoon
161

Image Credit: Hackernoon
"Vibe Hacking" and the Rise of the AI-Augmented Attacker
- Artificial intelligence was expected to give cybersecurity defenders a competitive advantage, but attackers are now using AI to enhance their capabilities, leading to a faster evolution of cyber threats referred to as 'vibe hacking.'
- Attackers leverage AI to craft sophisticated phishing attempts that mimic legitimate communications, making it harder to detect fraudulent messages, while AI-powered polymorphic phishing generates unique variations to evade traditional security measures.
- Training to combat phishing needs to focus on recognizing subtle inconsistencies and using trusted communication methods to verify suspicious messages, as attackers now have AI support for refining attacks.
- AI tools, like LLM co-conspirators, assist novice attackers in correcting errors and refining exploits, streamlining the process of launching successful attacks with minimal expertise.
- Automated reconnaissance powered by AI tools provides attackers with detailed attack plans and actionable intelligence based on partial data, drastically reducing the effort and cost of planning attacks.
- The rise of AI-driven attacks results in more credible phishing campaigns, precisely targeted payloads, and persistent probing of defenses, challenging security teams that can no longer rely on traditional warning signs.
- Effective defense against AI-driven threats requires realistic penetration testing that mirrors modern attacker behaviors, emphasizing the need for security assessments to evolve with the advancing landscape of cyber threats.
- Regular, realistic penetration testing remains crucial in staying ahead of evolving cyber threats facilitated by AI, ensuring that defensive strategies align with the tactics employed by modern attackers.
Read Full Article
9 Likes
Embedded
400

PSA Certified: A Security Framework for All Digital Devices – Not Just Internet-Connected Ones
- In today’s digital world, all digital devices, not just internet-connected ones, are vulnerable to cybersecurity risks.
- Recent incidents in automotive and government infrastructure emphasize the need for robust security measures.
- The Platform Security Architecture (PSA) Certified framework by Arm helps ensure secure digital products.
- Global legislation like the EU's Cyber Resilience Act and UK's PSTI are increasing pressure for security standards.
- PSA Certified offers a multi-level certification framework focusing on core security goals.
- Levels 1 to 4 of PSA Certified cover various security aspects from foundational requirements to high-security use cases.
- A layered trust model in PSA Certified includes Immutable Root of Trust, Updateable Root of Trust, and Application RoT.
- Secure-by-design approach is essential for security, especially for devices in regulated markets.
- PSA Certified ensures that devices are secure from the silicon level up, addressing long-term security concerns.
- Trust in digital devices starts with secure chips, and PSA Certified offers a structured approach for compliance.
Read Full Article
24 Likes
Tech Radar
44

Image Credit: Tech Radar
Fake IT support voice calls lead to cyber extortion and stolen company data
- Google experts warn about an ongoing vishing campaign where threat actors impersonate IT support to trick individuals into downloading malware and steal data.
- Around 20 companies lost their data due to cybercriminals impersonating Salesforce and tricking employees into installing a tainted version of Salesforce Data Loader.
- The threat actor UNC6040 targeted organizations in various sectors like hospitality, retail, and education by calling them and gaining access to sensitive information from compromised Salesforce environments.
- Google advises educating employees on phishing dangers to defend against such campaigns, as no vulnerabilities specific to Salesforce were exploited in this cyber extortion scheme.
Read Full Article
2 Likes
Cybersafe
319

Image Credit: Cybersafe
U.S. Offers $10M Reward for Intel on RedLine Malware Hackers
- The U.S. Department of State is offering a reward of up to $10 million for information on state-sponsored hackers linked to the RedLine infostealer malware and its alleged creator, Maxim Alexandrovich Rudometov.
- The bounty is part of the Rewards for Justice program, aiming to identify foreign government threat actors involved in cyberattacks against U.S. entities, particularly critical infrastructure.
- Maxim Alexandrovich Rudometov, indicted in the U.S. as part of Operation Magnus, is believed to be associated with RedLine malware, maintaining its infrastructure and managing cryptocurrency accounts.
- International law enforcement efforts have disrupted RedLine and META malware platforms, leading to arrests in Belgium and seizures of servers and web domains, but it's uncertain if Rudometov has been apprehended.
Read Full Article
19 Likes
Pymnts
134

Image Credit: Pymnts
Banks Bet on Virtual Cards as the New Credit Battleground
- Virtual cards are emerging as the next frontier in consumer finance, with 42% of US consumers using them in the last six months primarily for online purchases and subscriptions.
- Digital wallets have paved the way for the rise of virtual cards, which are entirely digital and offer greater security and control with features like one-time numbers for each transaction to limit fraud exposure.
- Virtual cards provide real-time spending controls, immediate issuance post-approval, and seamless integration with merchant apps, positioning them as a competitive tool in the credit market.
- The challenge lies in bridging the gap between digital-first consumers and those seeking traditional rewards, with financial institutions needing to educate users about the security, convenience, and integration benefits of virtual cards.
Read Full Article
8 Likes
VoIP
125

Image Credit: VoIP
Nokia to Lead EU Project Advancing Drone and Robotics Tech
- Nokia is set to lead a significant EU project named Proactif, focused on utilizing drones and robotics for monitoring critical infrastructure in Europe.
- The project involves 43 organizations from 13 countries and aims to enhance infrastructure surveillance and automation using cutting-edge technologies.
- Nokia's consortium includes tech giants like Nvidia and defense companies such as Leonardo and Saab to revolutionize infrastructure monitoring and provide real-time insights.
- The Proactif initiative targets economic growth, aiming to generate revenue, introduce new products, secure patents, and create specialized jobs by 2035, aligning with the EU's strategic goals for technological self-reliance and enhanced security.
Read Full Article
7 Likes
Medium
170

Image Credit: Medium
Quantum-Safe Security Protocols for Critical Infrastructure Communication
- The quantum era is approaching rapidly, posing a threat to traditional cryptography used in critical infrastructure systems worldwide.
- Adversaries are utilizing the 'Harvest Now, Decrypt Later' strategy to eavesdrop on sensitive communications, jeopardizing national security.
- Post-Quantum Cryptography (PQC) algorithms like CRYSTALS-Kyber and CRYSTALS-Dilithium are being developed to counter quantum attacks and secure critical systems.
- Organizations are urged to transition to quantum-resistant cryptographic components to prepare for the impending quantum age and safeguard against catastrophic breaches.
Read Full Article
10 Likes
Semiengineering
4

Image Credit: Semiengineering
Creating A Modular And Versatile State-of-the-Art Cryptographic Subsystem
- Chipmakers are developing cryptographic subsystems to meet the increasing demand for secure and high-performance silicon.
- Customers seek versatile solutions that offer robust security capabilities for defense electronics, automotive systems, and industrial IoT.
- Key features customers value include comprehensive cryptographic support, efficient architecture, secure key management, customizability, side-channel protection, and certification readiness.
- Rambus has introduced the CryptoManager Hub, a configurable cryptographic engine that provides flexibility, compliance with standards, and high performance for tailored security subsystems.
Read Full Article
Like
Semiengineering
256
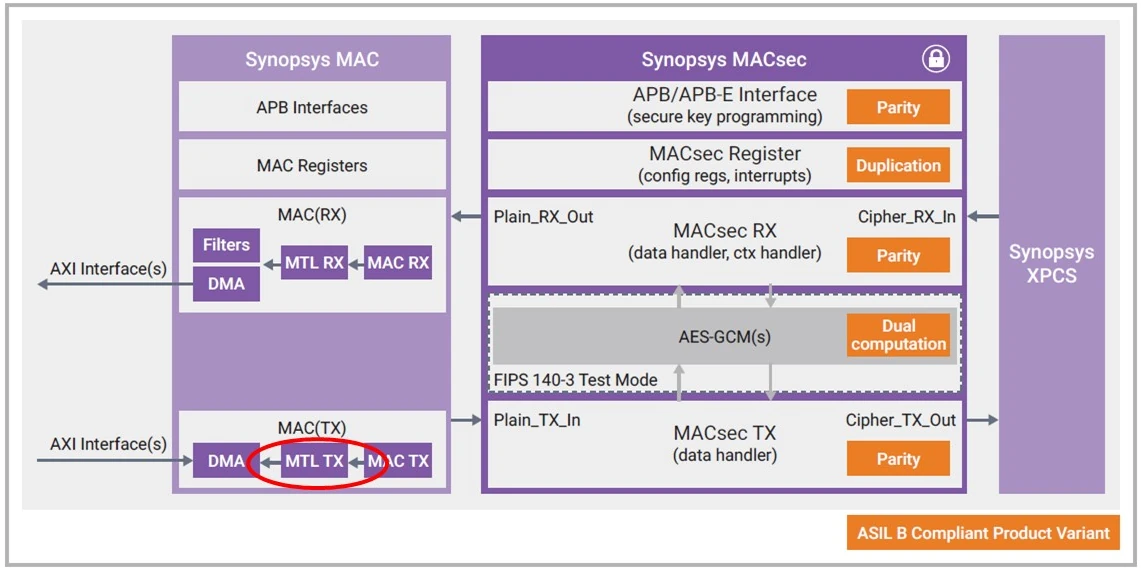
Image Credit: Semiengineering
Securing The Road Ahead: MACsec Compliant For Automotive Use
- The automotive industry has seen significant transformation with the rise of connected and autonomous vehicles, leading to increased security risks due to heightened connectivity.
- Synopsys expands its MACsec IP portfolio with an Automotive MACsec variant compliant with safety and cybersecurity requirements in the automotive market.
- Ethernet adoption in vehicles is increasing due to high bandwidth capabilities supporting sensors, cameras, and infotainment systems, reducing complexity in wiring and facilitating data transfer.
- Securing Ethernet connections in vehicles is crucial to prevent unauthorized access, manipulation of vehicle functions, and data breaches.
- Encrypting data over Ethernet is essential as a proactive measure against potential security threats and ensuring ongoing protection of sensitive information.
- Media Access Control security (MACsec) provides data confidentiality, integrity, and authenticity over Ethernet networks, essential for safeguarding automotive communications.
- Compliance with standards like ISO 26262 and ISO/SAE 21434 is crucial for automotive systems to meet safety and security requirements, ensuring the protection of sensitive data.
- Synopsys introduces Automotive MACsec aligning with IEEE standards, offering encryption, authentication, and end-to-end security for Ethernet traffic in vehicles.
- Automotive MACsec ensures safety and security functionality, meeting ASIL B compliance and incorporating advanced safety mechanisms to protect against faults.
- By adhering to ISO/SAE 21434 cybersecurity requirements, Automotive MACsec provides robust cybersecurity measures for modern vehicles, addressing key threats and enhancing resilience.
Read Full Article
15 Likes
Semiengineering
35

Image Credit: Semiengineering
How Secure Are Analog Circuits?
- Security concerns in analog circuits are gaining attention with the move towards multi-die assemblies and the importance of sensor data at the edge.
- Analog circuits traditionally had limited space on-chip, pushing security concerns towards digital circuits.
- Shift towards multi-dimensional SiPs has eased area restrictions for analog circuits, allowing for more freedom in development and potential for increased reuse.
- The integration of analog circuits in multi-die assemblies poses new security challenges and vulnerabilities to cyber attacks.
- Chiplet I/Os facilitate potentially vulnerable subsystem-to-subsystem communications in complex assemblies.
- Ensuring security in multi-die assemblies, particularly in the context of AI, is crucial for safeguarding against counterfeits and side-channel attacks.
- Securing analog circuits at the edge, where AI/ML expansion is sensor-driven, involves implementing cryptographic operations in sensors and ML models.
- Analog data security at the edge mirrors digital data security concerns and involves verifying source authenticity and monitoring sensors for degradation or attacks.
- The disparity between digital and analog engineering domains poses unique security challenges, especially in evolving multi-die assembly environments.
- Ensuring analog security is as robust as digital security is imperative as chiplets become more prevalent in heterogeneous systems.
Read Full Article
2 Likes
Pymnts
1k

Image Credit: Pymnts
Google Warns of Social Engineering Scheme Targeting Salesforce Users
- Google's Threat Intelligence Group has warned about an organization targeting Salesforce users through voice phishing schemes.
- The attackers, known as UNC6040, manipulate employees through social engineering, gaining access to steal Salesforce data.
- UNC6040 uses social engineering tactics rather than exploiting vulnerabilities in Salesforce to compromise networks.
- Google advises companies to implement security measures like least privilege, rigorous access management, IP-based restrictions, and multifactor authentication to guard against such threats.
Read Full Article
12 Likes
Dev
44

Image Credit: Dev
What Is a DDoS Attack and How Can We Defend Against It?
- DDoS attacks aim to disrupt online services by overwhelming them with massive traffic from compromised devices.
- Types of DDoS attacks include volumetric, protocol, and application layer attacks, with application layer attacks being the hardest to detect.
- The impact of DDoS attacks includes service downtime, increased infrastructure costs, reputation damage, and heightened security risks.
- Defenses against DDoS attacks include CDNs, rate limiting, traffic filtering, WAFs, behavioral analysis, and challenges like CAPTCHA.
Read Full Article
2 Likes
Analyticsindiamag
71
Image Credit: Analyticsindiamag
The Hidden Dangers Lurking in Cloud AI Infrastructure
- A recent report from Tenable highlights that about 70% of cloud AI workloads have at least one unremediated vulnerability, with potential risks lurking in the rest.
- The reliance on default service accounts in Google Vertex AI poses a significant threat, leading to security vulnerabilities that cascade through AI services.
- The article emphasizes the need for a risk-based model like Vulnerability Priority Rating (VPR) over Common Vulnerability Scoring System (CVSS) for prioritizing security vulnerabilities in cloud AI environments.
- Addressing identity sprawl and implementing AI-powered analytics on the network are crucial steps to enhance security in cloud AI infrastructures.
- Narang suggests merging human and machine identities into a single directory and enforcing least-privilege access to mitigate security risks effectively.
- Cloud AI security requires a platform approach to tackle growing risks efficiently, emphasizing the importance of zero-trust policies and real-time monitoring of entitlements and configurations.
- A case study involving an oversight in a Redis library by OpenAI in March 2023 highlighted how simple misconfigurations can lead to privacy incidents in cloud AI setups.
- Narang stresses the need for a comprehensive approach to securing training and testing data, including asset classification, encryption, and privacy-preserving techniques.
- Securing the pipeline, including monitoring data assets and implementing encryption, is crucial to prevent large-scale privacy breaches in cloud AI environments.
- Organizations that integrate visibility, automation, and risk-based prioritization in their cloud AI strategies will be better equipped to safeguard their systems against evolving threats, as per Narang's insights.
Read Full Article
4 Likes
Securityaffairs
103

Image Credit: Securityaffairs
Law enforcement seized the carding marketplace BidenCash
- U.S. and Dutch authorities collaborated to dismantle the BidenCash cybercrime marketplace by seizing 145 associated domains.
- The U.S. Department of Justice announced the seizure of 145 darknet and clear web domains, along with cryptocurrency funds linked to BidenCash.
- BidenCash, operational since March 2022, charged a fee for transactions and distributed millions of stolen payment cards, generating around $17 million in revenue.
- Authorities shut down 145 domains related to BidenCash, redirecting them to law enforcement servers to prevent further criminal activities.
Read Full Article
6 Likes
For uninterrupted reading, download the app