Cyber Security News
Semiengineering
256
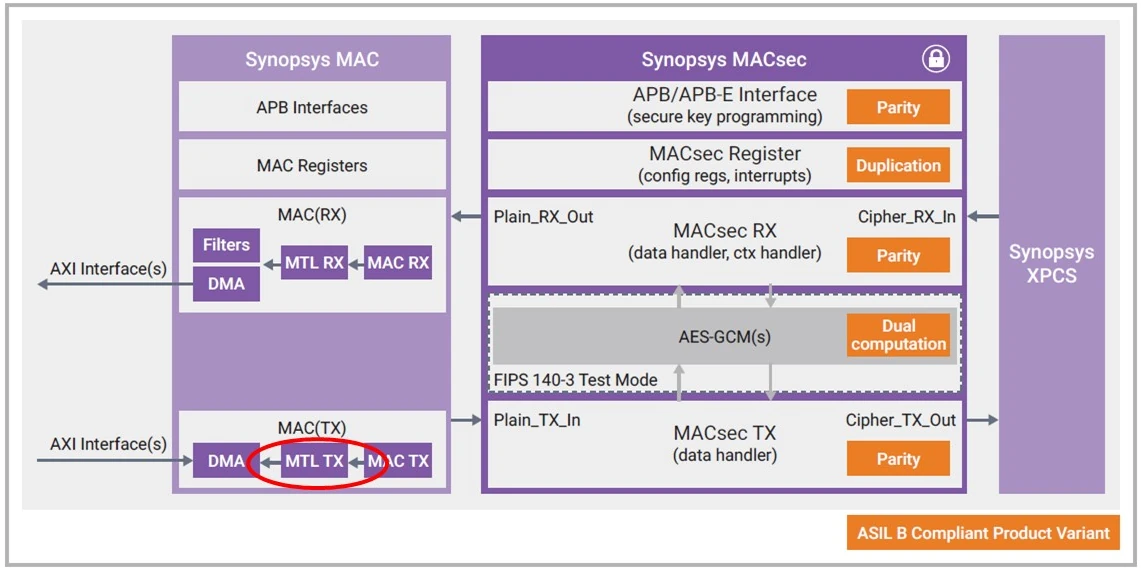
Image Credit: Semiengineering
Securing The Road Ahead: MACsec Compliant For Automotive Use
- The automotive industry has seen significant transformation with the rise of connected and autonomous vehicles, leading to increased security risks due to heightened connectivity.
- Synopsys expands its MACsec IP portfolio with an Automotive MACsec variant compliant with safety and cybersecurity requirements in the automotive market.
- Ethernet adoption in vehicles is increasing due to high bandwidth capabilities supporting sensors, cameras, and infotainment systems, reducing complexity in wiring and facilitating data transfer.
- Securing Ethernet connections in vehicles is crucial to prevent unauthorized access, manipulation of vehicle functions, and data breaches.
- Encrypting data over Ethernet is essential as a proactive measure against potential security threats and ensuring ongoing protection of sensitive information.
- Media Access Control security (MACsec) provides data confidentiality, integrity, and authenticity over Ethernet networks, essential for safeguarding automotive communications.
- Compliance with standards like ISO 26262 and ISO/SAE 21434 is crucial for automotive systems to meet safety and security requirements, ensuring the protection of sensitive data.
- Synopsys introduces Automotive MACsec aligning with IEEE standards, offering encryption, authentication, and end-to-end security for Ethernet traffic in vehicles.
- Automotive MACsec ensures safety and security functionality, meeting ASIL B compliance and incorporating advanced safety mechanisms to protect against faults.
- By adhering to ISO/SAE 21434 cybersecurity requirements, Automotive MACsec provides robust cybersecurity measures for modern vehicles, addressing key threats and enhancing resilience.
Read Full Article
15 Likes
Semiengineering
35

Image Credit: Semiengineering
How Secure Are Analog Circuits?
- Security concerns in analog circuits are gaining attention with the move towards multi-die assemblies and the importance of sensor data at the edge.
- Analog circuits traditionally had limited space on-chip, pushing security concerns towards digital circuits.
- Shift towards multi-dimensional SiPs has eased area restrictions for analog circuits, allowing for more freedom in development and potential for increased reuse.
- The integration of analog circuits in multi-die assemblies poses new security challenges and vulnerabilities to cyber attacks.
- Chiplet I/Os facilitate potentially vulnerable subsystem-to-subsystem communications in complex assemblies.
- Ensuring security in multi-die assemblies, particularly in the context of AI, is crucial for safeguarding against counterfeits and side-channel attacks.
- Securing analog circuits at the edge, where AI/ML expansion is sensor-driven, involves implementing cryptographic operations in sensors and ML models.
- Analog data security at the edge mirrors digital data security concerns and involves verifying source authenticity and monitoring sensors for degradation or attacks.
- The disparity between digital and analog engineering domains poses unique security challenges, especially in evolving multi-die assembly environments.
- Ensuring analog security is as robust as digital security is imperative as chiplets become more prevalent in heterogeneous systems.
Read Full Article
2 Likes
Pymnts
1k

Image Credit: Pymnts
Google Warns of Social Engineering Scheme Targeting Salesforce Users
- Google's Threat Intelligence Group has warned about an organization targeting Salesforce users through voice phishing schemes.
- The attackers, known as UNC6040, manipulate employees through social engineering, gaining access to steal Salesforce data.
- UNC6040 uses social engineering tactics rather than exploiting vulnerabilities in Salesforce to compromise networks.
- Google advises companies to implement security measures like least privilege, rigorous access management, IP-based restrictions, and multifactor authentication to guard against such threats.
Read Full Article
12 Likes
Dev
44

Image Credit: Dev
What Is a DDoS Attack and How Can We Defend Against It?
- DDoS attacks aim to disrupt online services by overwhelming them with massive traffic from compromised devices.
- Types of DDoS attacks include volumetric, protocol, and application layer attacks, with application layer attacks being the hardest to detect.
- The impact of DDoS attacks includes service downtime, increased infrastructure costs, reputation damage, and heightened security risks.
- Defenses against DDoS attacks include CDNs, rate limiting, traffic filtering, WAFs, behavioral analysis, and challenges like CAPTCHA.
Read Full Article
2 Likes
Analyticsindiamag
71
Image Credit: Analyticsindiamag
The Hidden Dangers Lurking in Cloud AI Infrastructure
- A recent report from Tenable highlights that about 70% of cloud AI workloads have at least one unremediated vulnerability, with potential risks lurking in the rest.
- The reliance on default service accounts in Google Vertex AI poses a significant threat, leading to security vulnerabilities that cascade through AI services.
- The article emphasizes the need for a risk-based model like Vulnerability Priority Rating (VPR) over Common Vulnerability Scoring System (CVSS) for prioritizing security vulnerabilities in cloud AI environments.
- Addressing identity sprawl and implementing AI-powered analytics on the network are crucial steps to enhance security in cloud AI infrastructures.
- Narang suggests merging human and machine identities into a single directory and enforcing least-privilege access to mitigate security risks effectively.
- Cloud AI security requires a platform approach to tackle growing risks efficiently, emphasizing the importance of zero-trust policies and real-time monitoring of entitlements and configurations.
- A case study involving an oversight in a Redis library by OpenAI in March 2023 highlighted how simple misconfigurations can lead to privacy incidents in cloud AI setups.
- Narang stresses the need for a comprehensive approach to securing training and testing data, including asset classification, encryption, and privacy-preserving techniques.
- Securing the pipeline, including monitoring data assets and implementing encryption, is crucial to prevent large-scale privacy breaches in cloud AI environments.
- Organizations that integrate visibility, automation, and risk-based prioritization in their cloud AI strategies will be better equipped to safeguard their systems against evolving threats, as per Narang's insights.
Read Full Article
4 Likes
Securityaffairs
103

Image Credit: Securityaffairs
Law enforcement seized the carding marketplace BidenCash
- U.S. and Dutch authorities collaborated to dismantle the BidenCash cybercrime marketplace by seizing 145 associated domains.
- The U.S. Department of Justice announced the seizure of 145 darknet and clear web domains, along with cryptocurrency funds linked to BidenCash.
- BidenCash, operational since March 2022, charged a fee for transactions and distributed millions of stolen payment cards, generating around $17 million in revenue.
- Authorities shut down 145 domains related to BidenCash, redirecting them to law enforcement servers to prevent further criminal activities.
Read Full Article
6 Likes
Dev
98

Image Credit: Dev
Arbitrary File Read Vulnerability in Vite (CVE-2025-31125)
- Chaitin Tech discovered an arbitrary file read vulnerability (CVE-2025-31125) in Vite, a popular frontend build tool used in JavaScript and TypeScript web development.
- The vulnerability allows attackers to read sensitive files on the server by crafting special URLs, impacting Vite versions 4.5.10 to 6.2.3.
- The Vite team has released patches (6.2.4, 6.1.3, 6.0.13, 5.4.16, 4.5.11) to address the issue and users are advised to update through npm update vite.
- Mitigation steps include restricting network access and enforcing file permissions until the update can be applied to prevent exploitation of this high-risk vulnerability.
Read Full Article
5 Likes
Medium
303

Image Credit: Medium
The $450 Million Mirage: How AI Hype Fueled Builder.ai’s Collapse
- Builder.ai, a startup marketed as an AI-powered app development platform, raised $450 million but was revealed to be powered by human developers, not AI.
- This case of AI washing exposes a systemic issue of misrepresenting AI capabilities, from inflated financials to deceptive branding, across industries.
- Investor excitement in AI's promise for automated efficiency and scalability highlights the gravity of the situation when reality falls short of expectations.
- The collapse of Builder.ai raises critical questions about accountability and transparency in the tech industry's AI hype, emphasizing the need for genuine innovation over mere illusions.
Read Full Article
17 Likes
Dev
8

Image Credit: Dev
0day RCE Vulnerability in Apusic Application Server via IIOP Deserialization
- Chaitin Security Emergency Response Center disclosed a critical remote code execution (RCE) vulnerability in Apusic Application Server (AAS). The vulnerability arises from unsafe Java deserialization in the IIOP protocol, enabling unauthenticated attackers to execute arbitrary code remotely.
- The vulnerability in AAS is triggered by unsafe Java deserialization in processing IIOP requests, allowing attackers to send crafted payloads to achieve remote code execution, potentially leading to full server compromise.
- The risk summary categorizes the vulnerability as high priority, high severity, with potential for remote network access without authentication, and exploit availability through public PoC/exploit. The official patch is available with low fix complexity.
- Affected versions range from Apusic Application Server v10.0 Enterprise Edition SP1 to SP8. Mitigation steps include restricting IIOP port access or disabling the IIOP protocol if not needed. Users are advised to download and install the patched version from the official Apusic site.
Read Full Article
Like
Mcafee
377

Image Credit: Mcafee
What to Do If You Book a Hotel or Airbnb and It Turns Out to Be a Scam
- Accommodation scams are increasing in sophistication, targeting travelers during vacation season.
- Scammers create fake listings on popular platforms, mimic real properties, and exploit emotional vulnerability.
- Warning signs include unusually low prices, requests for off-platform payments, and lack of property details.
- Immediate actions if scammed: document everything, contact financial institution, report to the platform, file official reports, and monitor accounts.
- Long-term protection strategies involve using comprehensive digital protection services like McAfee's family protection plans.
- McAfee's services offer real-time scam protection, secure VPN for travel research, financial transaction monitoring, and identity monitoring.
- Protection plans cover up to six family members, provide identity theft coverage, and offer 24/7 restoration assistance.
- Investing in prevention measures like research, protection software, and education on scam tactics is crucial for financial security.
- Legitimate accommodation providers prioritize trust and verification; be cautious of pressure to skip verification steps or use unusual payment methods.
- Ensuring family safety and financial security is paramount during travel; staying vigilant and prepared can prevent vacation nightmares.
- Remember, the best vacation is where pleasant surprises await and scams are averted.
Read Full Article
22 Likes
Siliconangle
305

Image Credit: Siliconangle
CrowdStrike faces federal scrutiny following global Windows outage
- CrowdStrike Holdings Inc. cooperating with U.S. federal investigations into 2024 global Windows outage.
- Justice Department and SEC seeking information on incident, revenue-recognition practices, and annual recurring revenue.
- CrowdStrike received inquiries from multiple government agencies and parties related to the outage.
- Outage caused by faulty update to CrowdStrike's Falcon Sensor software, impacting millions of computers.
Read Full Article
18 Likes
Wired
436

Image Credit: Wired
ICE Quietly Scales Back Rules for Courthouse Raids
- Immigration and Customs Enforcement has quietly rescinded guidance on courthouse raids, potentially leading to escalated enforcement tactics and legal disputes.
- The revised ICE policy aims to enhance agents' autonomy, removing the requirement to respect local laws during arrests in and around courthouses.
- Under the new policy, the responsibility to navigate complex legal questions regarding courthouse arrests falls on individual officers.
- ICE's updated approach raises concerns about eroding local autonomy and blurring the distinction between civil and criminal enforcement.
- The Biden administration had previously limited ICE enforcement actions in courthouses to prevent chilling effects on individuals' willingness to engage with the legal system.
- ICE's shift in policy could have implications for states like Colorado with similar protections against civil arrests in sensitive locations.
- Recent high-profile arrests at courthouses have drawn criticism, with ICE agents facing backlash for their tactics and interactions with citizens.
- Legal challenges are expected against the federal government's encroachment on state sovereignty due to the revised ICE policy.
- The Trump administration's move to expand ICE enforcement operations without regard to state laws has raised concerns about justice in local and state courts.
- DHS published a list of sanctuary jurisdictions but removed it after protests, highlighting tensions between federal and local authorities on immigration enforcement.
Read Full Article
26 Likes
Pymnts
89

Image Credit: Pymnts
Worldpay Partners With Early Warning Services to Offer Paze Checkout Option
- Worldpay and Early Warning Services have partnered to integrate the Paze online checkout solution into Worldpay's offerings for merchants.
- Paze, developed by Early Warning Services, allows consumers to pay online using credit and debit cards through tokenization for increased security and potentially higher authorization rates for merchants.
- The collaboration aims to enhance security and convenience in online transactions for Worldpay merchants by offering a seamless checkout experience that can increase conversion rates.
- The partnership makes Paze available to thousands of U.S. merchants, reaching an estimated 150 million consumers through their financial institutions, and will be integrated into Worldpay's U.S. hosted payment pages soon.
Read Full Article
5 Likes
Tech Radar
35

Image Credit: Tech Radar
Malware affiliate pyramid scheme is shuttered by US feds: here's how to keep safe
- FBI's crackdown on Qakbot malware led to the seizure of servers and confiscation of $8.6 million, but it re-emerged stronger with new spam bomb attacks.
- Qakbot's alleged mastermind, Rustam Rafailevich Gallyamov, adapted to law enforcement actions by using more deceptive tactics like spam bomb attacks tricking employees.
- The attackers posed as IT staff in subscription emails to gain access to company systems, leading to data theft, encryption, and ransom demands.
- Despite seizing funds from Gallyamov, he remains in Russia beyond the reach of US law enforcement, leaving organizations vulnerable to similar cyber threats.
Read Full Article
2 Likes
TechDigest
916

Image Credit: TechDigest
H&M stores hit by major IT outage, cyber attack speculation mounts
- H&M stores in the UK experienced a significant IT outage, preventing customers from making payments.
- Speculation of a possible cyberattack arose due to a recent trend of such incidents targeting major British retailers.
- Sales were disrupted for about two hours in a London store, and the issue is being investigated with no confirmation of a cyberattack.
- Other retailers like Marks & Spencer and Co-op have recently faced cyberattacks, emphasizing the importance of cybersecurity measures.
Read Full Article
26 Likes
For uninterrupted reading, download the app