Programming News
Dev
2M
179

Image Credit: Dev
Understanding Browser Storage: Local Storage, Session Storage, and IndexedDB
- Browsers offer various storage mechanisms for client-side data management: Local Storage, Session Storage, and IndexedDB.
- Local Storage is persistent, suitable for small data, stores strings, and is synchronous in operations.
- Session Storage has a shorter lifespan, ideal for temporary per-tab data needs, also stores strings, and is synchronous.
- IndexedDB is for storing large structured data, supports complex types, has larger capacity, asynchronous API, and is suitable for offline-first applications.
Read Full Article
10 Likes
Medium
2M
215

Unlocking AI and Machine Learning with Java
- Java is evolving to support AI needs such as processing big data efficiently and running fast on modern hardware.
- Java's platform features have broad applicability beyond AI, benefiting areas like big data and scientific computing.
- The strong ecosystem of open source communities and ongoing updates position Java as a primary language for AI development.
- Project Panama's Foreign Function & Memory API enhances Java's interoperability with native code for faster data transfer.
- The Vector API in Java enables hardware-accelerated data parallelism using SIMD programming for faster math operations.
- Valhalla's Value Classes support new numerical types for efficient memory usage, beneficial for AI tasks that can tolerate lower precision.
- Code Reflection and Babylon in Java enable flexible hardware and model interoperability, aiding in auto differentiation for neural network training.
- Oracle's use of Java's GPU acceleration toolkit simplifies GPU integration for deep learning and data processing tasks.
- Leveraging high-speed native libraries like Bliss, Java facilitates high-performance matrix operations, essential for training AI models efficiently.
- Java's features enhance data analysis, anomaly detection, and model deployment in real-world systems, offering faster and more reliable AI solutions.
Read Full Article
12 Likes
Dev
2M
303

Image Credit: Dev
Building Your AI Side Hustle: A Developer's Guide to Extra Income in 2025
- Developers have significant opportunities in the AI side hustle space to create additional income streams alongside their primary careers.
- The AI market is booming, with developers earning $1,000 to $10,000 monthly through side AI projects due to a talent shortage in AI expertise.
- Accessible AI side hustles for developers include AI Integration Services, Custom AI Tool Development, AI-Powered Content Creation, Chatbot Development, and Predictive Analytics Tools.
- An example features Robert, earning over $13,000 monthly by building custom AI workflows for accounting firms using no-code platforms alongside his full-time job.
- A step-by-step guide is provided for building a customizable AI chatbot service using NextJS, OpenAI, and Firebase for enhancing customer engagement.
- Monetization strategies include implementing a Stripe subscription model with pricing plans and features, allowing developers to earn recurring revenue.
- Potential income calculation shows that with 18 clients across different tiers, developers can generate over $1,500 monthly in recurring revenue.
- Strategies for scaling the AI side hustle include automating client onboarding, creating industry-specific templates, building additional features, and outsourcing customer support.
- The article emphasizes the opportunity for developers to build valuable side incomes by solving real business problems with customized AI solutions.
- Success in AI side hustles lies in identifying business problems, delivering tangible value through AI, and leveraging existing development skills to create sustainable income streams.
Read Full Article
18 Likes
Medium
2M
250
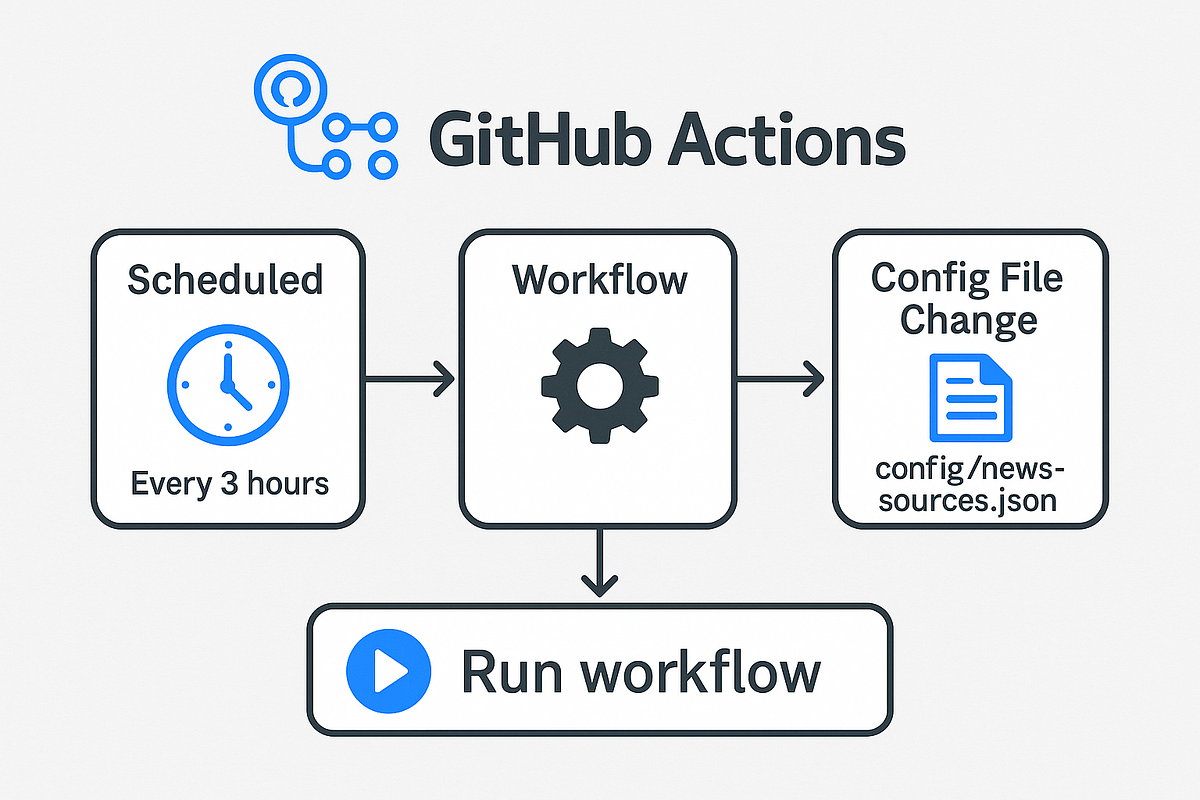
Image Credit: Medium
My Cybersecurity News Aggregator: Built with GitHub Actions
- GitHub Actions is being utilized for automating the Cybersecurity News Aggregator, making it efficient and self-updating.
- The news aggregator is a clean, responsive website that gathers the latest cybersecurity stories from top sources in one repository.
- This automation setup not only saves time but also allows for deeper exploration of cybersecurity trends without the hassle of managing multiple tabs.
- To explore the code for this Cybersecurity News Aggregator built with GitHub Actions and share your own innovations, visit https://github.com/ricomanifesto/SentryDigest
Read Full Article
14 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
2M
41

Image Credit: Dev
How to Build a Simple Python Video Stream Server with aiortc?
- Setting up a simple video stream server using Python and the aiortc library involves integrating Python and HTML/JavaScript components for a local network setup.
- One common issue faced by developers when working with WebRTC is the ValueError related to Session Description Protocol (SDP) errors, particularly when SDPs lack valid track information causing connection failures.
- To build a Python video streaming server with aiortc, you need to install dependencies and utilize Python code to stream video, while the corresponding JavaScript code connects to the server to receive the video stream.
- Troubleshooting SDP issues requires ensuring valid track information in SDPs, correct setup for handling offers and answers, and checking network configurations for ICE candidate exchange.
Read Full Article
2 Likes
Medium
2M
298

SaaS Best Practices: 15 Essentials for Building Scalable, Secure, and Successful Platforms
- Enforce tenant isolation and security measures at all layers of your SaaS platform by using middleware or policies to inject tenant context automatically.
- Implement a clean architecture that decouples concerns using different layers such as Domain, Application, Infrastructure, and API to ensure business rules are pure and easily testable.
- Utilize standards like OAuth2/OpenID Connect for authentication and authorization, and implement tenant-aware Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC) for security.
- Focus on observability by tagging logging, metrics, and tracing with tenant information and leverage tools like Serilog, OpenTelemetry, and Application Insights for better insights into platform performance.
Read Full Article
17 Likes
Dev
2M
59

Image Credit: Dev
The Quest Continues: Porting the Word Game With AsyncSSH
- The article discusses the process of porting a word game to be served over SSH using the AsyncSSH library in Python.
- Initially, the author explored using Paramiko but found AsyncSSH with its developer-friendly documentation to be more suitable for the project.
- The article delves into creating an SSH server and defining the application logic using classes like MySSHServer and MyREPLSession.
- The author covers implementing the connection, shell, data received, and other key methods for handling user interaction in the SSH session.
- The article also details the process of creating the server, managing tasks with AsyncIO, and setting up SSH keys for the application.
- Two different approaches to handling user input/output through SSHServerProcess and SSHLineEditorChannel objects are explored.
- The author highlights the differences and similarities between the CLI and SSH versions of the word game.
- The article concludes with the realization that hosting applications over SSH required a shift in handling I/O, showcasing the ease of development with AsyncSSH.
- Overall, the journey of porting the word game to SSH was filled with discoveries and learnings facilitated by the AsyncSSH library and collaboration with Gemini.
- The article aims to inspire more developers to explore hosting applications over SSH and showcases how AsyncSSH can make the development experience intuitive.
Read Full Article
3 Likes
Dev
2M
4

Image Credit: Dev
Get the Weather: A Clean and Practical Python Script
- Learning Python with practical projects like building a weather-fetching script using the OpenWeatherMap API can enhance your skills.
- This project teaches you how to work with APIs, process JSON data, structure code clearly, and handle errors gracefully.
- The script provided fetches real-time weather data for a specified city, showcasing logic and data handling in Python.
- By starting with such utility projects, you can potentially expand into more complex tools like weather dashboards or automation systems.
Read Full Article
Like
Johndcook
2M
41

An island of stability in a sea of chaos
- The island of stability is located within the chaotic region, starting at r = 3.8284.
- Despite the presence of three stable cycle points in this region, chaos still technically persists.
- The existence of points with period 4 in the system is affirmed through calculations involving the logistic map with r = 3.83.
- While the visible region may only show three stable cycle points, there are infinitely more cyclic points present but not observable, emphasizing the intricate nature of chaos.
Read Full Article
2 Likes
Dev
2M
147

Image Credit: Dev
🤪 7 JavaScript Tricks They Don’t Teach You in Bootcamp
- The article introduces 7 JavaScript tricks that are not typically taught in bootcamps.
- 1. Use short-circuit guards to avoid over-nesting and make logic flow clear and direct.
- 2. Object.fromEntries() simplifies creating objects from arrays and allows powerful object transforms.
- 3. Enforce sanity with assertion functions for faster debugging and catching assumptions early.
- 4. Destructuring with defaults avoids crashing or logging undefined values.
- 5. Named function expressions in callbacks improve stack traces, debugging, and documentation.
- 6. Freeze configs to prevent inadvertent changes and errors in team or large codebase settings.
- 7. Utilize Function .name and .toString() to debug unknown functions and monitor behaviors in callback-heavy apps.
- These tricks focus on writing code with more intent and efficiency rather than reducing code length.
- Readers are encouraged to share their own under-the-radar JavaScript tricks in the comments section.
- Additionally, the article highlights GitHub bundles for developers, offering curated repositories for faster project building.
Read Full Article
8 Likes
Dev
2M
431

Image Credit: Dev
Utility Containers in Docker: A Powerful Tool for Local Development Without Polluting Your Machine
- Utility containers in Docker are a powerful tool for local development without cluttering your machine.
- They allow running tasks using Docker containers without needing to install dependencies locally.
- By creating utility containers for different tasks like Node.js, Python, Go, or Terraform, you can streamline development workflows.
- Using Docker Compose with utility containers simplifies setup and offers a consistent development environment for team projects.
Read Full Article
25 Likes
Medium
2M
101
Image Credit: Medium
Dynamic Recursive Entropy Model (DREM) with math and PyTorch
- Dynamic Recursive Entropy Model (DREM) redefines entropy as a recursive input-output function within adaptive systems, supporting structural evolution and complexity generation.
- DREM extends the Fractal Flux framework by integrating entropy as a driver of recursive systemic evolution, emphasizing self-similarity and adaptivity across dimensions.
- Entropy in DREM is modeled recursively, with entropy feedback contributing to useful variance, order emergence, and controlled system adaptation.
- Applications of DREM include utilizing entropy noise in machine learning, AI creativity engines, physics simulations, and multiversal models as an active system component.
- A mathematical signature of DREM introduces a momentum-like formulation for recursive entropy injection in response to system structure and feedback dynamics.
- A PyTorch implementation prototype of DREM demonstrates recursive entropy injection in a module, emphasizing dynamic learnable scaling and recursive feedback mechanisms.
- Future research in DREM includes exploring DRE Autoencoders, entropy-based curriculum learning, dimensional perturbation models, and fractal memory architectures for enhanced recursive learning.
- Dynamic Recursive Entropy complements the Dynamic Entropy Model (DEM) by incorporating recursive feedback mechanisms, enabling long-range systemic learning and evolution within systems.
- Practical implications of integrating DEM and DREM span adaptive learning systems in machine learning, complex system modeling in biology, and the developmental needs of Artificial General Intelligence (AGI) systems.
Read Full Article
6 Likes
Medium
2M
36
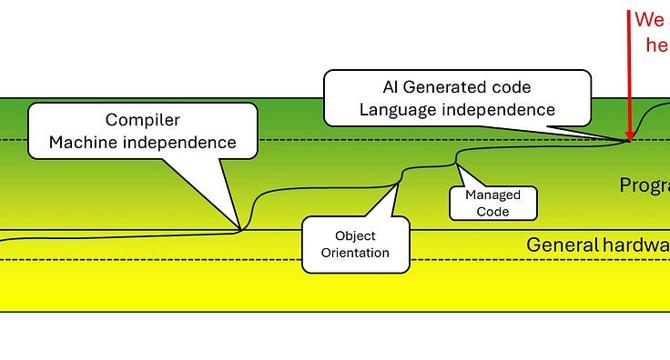
Image Credit: Medium
Programming languages in the age of AI
- The author argues that programming languages are becoming obsolete in the age of AI.
- They draw parallels between historical advancements and the current rapid evolution of technology.
- Assemblers became outdated with the introduction of compilers and personal computers in the 1980s.
- AI has now mastered interpreting complex human languages, eliminating the language barrier.
- Programming languages are seen as less complex and formal, making them easily translatable for AI.
- The extensive libraries and documentation available to programmers can be comprehended by AI language models.
- While developers may not become obsolete, their roles will shift towards problem analysis and system architecture.
- Important skills for future developers include problem analysis, system architecture decisions, and software design.
- The ability to structure requirements, minimize dependencies, and create a suitable design are crucial for efficient software development.
- AI may not yet replace developers due to challenges in system architecture and articulating problems clearly.
Read Full Article
2 Likes
Dev
2M
284

Image Credit: Dev
This Python Script Found 1,237 Leaked Passwords in 3 Minutes
- A Python script discovered 1,237 leaked passwords in under three minutes, highlighting the prevalence of data leaks and breaches in today's ecosystem.
- The article provides an in-depth guide with explanations, code samples, real-world statistics, resources, and tips to enhance one's toolkit for identifying exposed credentials.
- Data breaches surged in 2024, with 5.5 billion compromised accounts, emphasizing the critical importance of automated leak-scanning to mitigate risks.
- The architecture overview involves fetching sources from platforms like Pastebin and GitHub Gists, skipping duplicates, extracting secrets using regex patterns, and storing findings for analysis.
- Parallel processing techniques are employed for speed, enabling the script to efficiently scan URLs for credentials using ThreadPoolExecutor.
- The process includes alerting mechanisms through SMTP Email and Slack Webhook, ensuring timely notifications for identified credentials.
- Metrics and dashboard capabilities can track pastebin scanning, credentials found, and alerts triggered, offering insights into the scanning performance and outcomes.
- The article concludes with a real-world example of uncovering 1,237 credentials in just 3 minutes, prompting readers to replicate the script, customize it, and integrate it into their security operations.
- It emphasizes the significance of fast leak detection tools for proactive security measures and directs readers to python.0x3d.site for additional Python-powered security tools and support.
- In addition to the security-focused content, the article features tailored learning kits and courses related to hacking evolution, secret operating systems, programming languages, and tech history for curious minds to explore.
- The article offers a blend of practical Python scripting insights and educational resources, encouraging readers to delve deeper into cybersecurity practices and expand their technical knowledge.
Read Full Article
17 Likes
Dev
2M
9

Image Credit: Dev
Mastering Git Commit Messages with Conventional Commits
- In any software project, the structure of commit messages is crucial for understanding changes, generating changelogs, and leveraging CI/CD tools effectively.
- Conventional Commits provide a standardized convention for writing structured, meaningful, and machine-parsable commit messages in Git.
- The structure of a Conventional Commit includes type, scope, description, body, and footer(s), with common types like feat, fix, docs, style, refactor, test, and chore.
- Examples of Conventional Commits include adding a new feature, fixing a bug, updating documentation, making styling changes, refactoring code, and handling breaking changes.
Read Full Article
Like
For uninterrupted reading, download the app