Software News
Medium
427

Image Credit: Medium
Ancient Purity Laws and Software Development Team Health
- Ancient laws about ritual purity, as described in the Torah portions Tazria and Metzora, focus on identifying, isolating, and reintegrating individuals in a state of impurity back into the community through purification.
- The laws entail living in isolation outside the camp, followed by purification rituals to address spiritual impurity and seek reintegration, not as a punitive measure but as a process of restoration.
- In the context of software development, the principles from these ancient laws can be applied to address interpersonal issues like gossip, arrogance, and lack of collaboration within development teams, emphasizing the importance of reflection, responsibility, and team healing.
- Modern purification rituals in software development may include temporary isolation and reintegration processes like mentoring on best practices, assigning unfamiliar code tasks, and collaborative decision-making workshops to strengthen team communication and trust.
Read Full Article
25 Likes
Towards Data Science
195

How AI Is Rewriting the Day-to-Day of Data Scientists
- The article discusses various AI tools used in data science, such as OpenAI API, ChatGPT, Gemini, Glean AI, Cursor, Copilot, Hex Magic, and Snowflake Cortex.
- It focuses on two main aspects: eliminating low-value tasks and accelerating high-value work in data science.
- In terms of eliminating low-value tasks, AI plays a role in empowering stakeholders for self-serve analytics and reducing time spent on repetitive reporting.
- AI tools are aimed at enhancing query data with natural language, implementing chat-based BI assistants, and improving data catalog tools for better documentation.
- To accelerate high-value work, AI assists in coding and debugging, automating EDA and analysis processes, and enhancing NLP capabilities for data analysis.
- AI tools like Google Data Science Agent, ChatGPT's Data Analyst tool, and OpenAI API are mentioned for their contributions in streamlining data analysis workflows.
- The article emphasizes the importance of using AI to eliminate barriers to productivity and to focus on driving impactful data projects efficiently.
- It advises data scientists to be pragmatic in adopting AI tools that work, staying updated on emerging technologies, and prioritizing the core purpose of data science.
Read Full Article
11 Likes
Fb
317

Image Credit: Fb
Taking the plunge: Why Meta is laying the world’s longest subsea cable
- Meta is laying the world’s longest subsea cable to develop infrastructure for transporting information worldwide.
- Subsea cables are crucial for Meta to serve people globally, with over 95% of intercontinental traffic passing through them.
- Meta's engineering team focuses on innovation and quality in designing and deploying subsea cables, as discussed in the Meta Tech Podcast.
- The podcast episode delves into the engineering details of large-scale subsea cable projects like Project Waterworth.
Read Full Article
16 Likes
Fb
207
Image Credit: Fb
Taking the plunge: The engineering journey of building a subsea cable
- Meta's engineering team is focused on developing infrastructure globally, including subsea cables that are essential for intercontinental internet traffic.
- In the Meta Tech Podcast, subsea cable systems engineers discuss the latest in subsea engineering technology, emphasizing innovation and quality in designing these cables.
- The podcast delves into the engineering aspects of large-scale subsea cable projects like Project Waterworth, showcasing Meta's commitment to excellence in this field.
- For more insights on Meta's engineering endeavors, listeners can access the Meta Tech Podcast to learn about the company's innovations and career opportunities.
Read Full Article
11 Likes
Discover more
- Programming News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Engadget
202
Image Credit: Engadget
Epic Games takes aim at Apple and Steam with zero-commission policy for developers
- Epic Games has announced a zero-commission policy for developers on its store for the first $1,000,000 in revenue per year, starting in June.
- This move provides a significant advantage to smaller developers compared to platforms like Steam (30% commission) and Apple App Store (15% commission).
- Epic also introduced webshops for out-of-app purchases to bypass Apple's high fees, following its legal victory against Apple.
- The victory allows Fortnite to return to Apple devices in the US, with Epic CEO Tim Sweeney offering a 'peace plan' to drop all pending litigations on the matter.
Read Full Article
12 Likes
Medium
423

Image Credit: Medium
How to Create Interactive Stories with Character.ai
- Character.ai is a user-friendly platform for creating interactive stories, allowing readers to actively participate in the narrative.
- The platform uses AI models to generate responsive dialogue, enabling characters to adapt and maintain consistent personalities.
- Creating detailed character backgrounds enhances engagement and consistency in interactive storytelling.
- Test dialogues help ensure character coherence and quality interaction before sharing with others.
- Character.ai allows for branching narratives based on user choices, enhancing interactivity and engagement.
- Managing memory and context length is a challenge, but episodic storytelling and external resources can help overcome limitations.
- External resources like Wikipedia integration can enhance character knowledge, enabling accurate discussions on specific topics.
- Character.ai empowers creators to share their interactive stories easily and benefit from the platform's community feedback.
- The platform has applications in entertainment, education, and experimental storytelling, offering a wide range of creative possibilities.
- Character.ai bridges traditional fiction with interactive AI storytelling, presenting exciting opportunities for creators to explore new formats.
Read Full Article
25 Likes
Dev
310

Image Credit: Dev
Why Your Product Won’t Be Saved by AI or Web3 — and What Will?
- Many companies fail to achieve success with technology implementations like AI, blockchain, and Web3 because they focus on technology first instead of understanding and addressing the underlying business problems.
- Successful projects start with deep diagnostics to identify real business challenges and opportunities, not by simply implementing the latest technologies.
- Technology like AI can be beneficial for forecasting demand, automating internal processes, and enhancing personalization, but only if applied strategically to address specific business needs.
- Starting with a prototype, proof of concept, or focus group test can reduce risks, reveal weaknesses, and ensure that technology solutions align with business objectives.
Read Full Article
18 Likes
Medium
171

Image Credit: Medium
How Learning to Code Changed My Life (And Why I Almost Gave Up Before It Even Started)
- The individual's job involved monotonous tasks with spreadsheets, prompting a need for change.
- After considering various hobbies that didn't resonate, a friend suggested learning to code.
- The journey of learning to code was challenging and filled with moments of doubt and difficulty.
- Despite the initial struggles, the experience of learning to code brought a transformative change to the individual's life.
Read Full Article
10 Likes
Medium
216

Image Credit: Medium
What Actually Happens When You Use “new” in JavaScript
- The new keyword in JavaScript triggers a series of steps to create a new object, set up internal connections, and run the constructor function.
- JavaScript first creates an empty object when the new keyword is used, which is intended to become an instance of the function being called.
- After creating the object, JavaScript links it to the constructor function's prototype, enabling method and property sharing efficiently.
- By setting up this link, JavaScript avoids copying methods onto each object individually, ensuring a lightweight and efficient object model.
- When the constructor function runs, this inside the function points to the new object created by new, allowing properties to be attached to it.
- JavaScript checks the return value of the constructor - if an object is returned, it replaces the initially created object; otherwise, the original object is used.
- Automatic object creation and prototype linking by new simplify object creation, making constructors act as recipes for objects.
- Using prototypes for method sharing reduces memory usage by having all instances point to the same methods, improving memory efficiency.
- Constructors can return different objects, providing flexibility for special cases and enabling the creation of factory-like constructors.
- Each step in the new process in JavaScript ensures smooth object creation without manual setup, enhancing developer productivity and code clarity.
Read Full Article
13 Likes
Medium
427

Image Credit: Medium
Where the JVM Spends Time During Class Loading and Initialization
- Class loading in the JVM is done dynamically as classes are needed during program execution to conserve memory and avoid unnecessary preparation.
- The JVM utilizes class loaders in a hierarchical structure including Bootstrap, Platform, and Application ClassLoaders to locate and load classes.
- Parent delegation is a pattern where the JVM asks parent class loaders first before child loaders when loading classes to prevent duplication.
- Class loading can be delayed until a class is used, enabling the JVM to optimize startup times and memory consumption.
- Loading involves finding and reading the .class file into memory, but it does not yet initialize the class or set up static fields.
- Linking is the phase where the JVM checks the class structure, verifies bytecode safety, prepares static fields, and resolves symbolic references.
- Verification ensures the bytecode follows JVM rules for safety and type correctness, detecting errors like improper type conversions.
- Preparation allocates memory for static fields with default values without executing static initialization code.
- Resolution converts symbolic references to direct pointers during linking, enhancing runtime performance by replacing name lookups with quick memory access.
- Initialization runs static initializers, assigns values to static fields, and ensures class readiness for program execution.
Read Full Article
25 Likes
Hackaday
279

Image Credit: Hackaday
libogc Allegations Rock Wii Homebrew Community
- The Wii homebrew community is facing allegations of impropriety against the developers of libogc, a C library used by homebrew software for the Wii and GameCube.
- Developers must uphold a high standard to keep the line between homebrew and piracy clear and avoid legal repercussions from console manufacturers like Nintendo or Sony.
- Allegations include license violations and concerns about code origins, potentially rendering the distribution of community-developed software for the consoles illegal.
- The lead developer of the Homebrew Channel (HBC) raised concerns about libogc containing code obtained through improper means and copied from RTEMS, a real-time operating system.
- Efforts to hide the source of the code allegedly copied from RTEMS and lack of proper attribution raised doubts about the integrity of the libogc developers.
- While some developers involved in libogc have responded to the allegations, there is no official statement addressing the issues raised by the community.
- Debates continue regarding the origins of libogc, with some acknowledging the influence of leaked information from the Nintendo SDK while others dispute the extent of code copying.
- The controversy surrounding libogc serves as a reminder of the importance of transparency and ethical practices in the development and use of open source software.
- Despite the allegations, the availability and widespread use of libogc in the Wii homebrew community pose challenges in finding alternatives and moving away from the library.
- While concerns over the library's origins persist, the focus remains on the continuous development and usage of homebrew software on the Wii without significant legal repercussions from Nintendo.
- The situation surrounding libogc highlights the complexities and consequences of using questionable code sources in open source projects and the potential impact on the wider software development community.
Read Full Article
16 Likes
Byte Byte Go
261
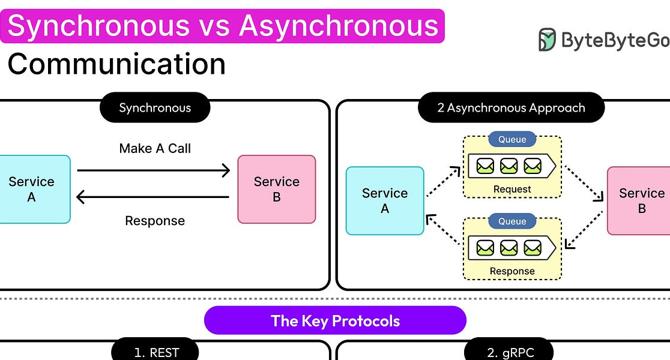
Image Credit: Byte Byte Go
Synchronous vs Asynchronous Communication: When to Use What?
- Systems often need to decide between using synchronous or asynchronous communication for interactions.
- Synchronous communication involves one service calling another and waiting for a response, while asynchronous communication decouples dependencies by allowing the sender to move on after triggering a message, job, or event.
- Synchronous communication offers predictability and ease of tracing but can lead to impacts if the called service slows down or fails. On the other hand, asynchronous communication provides flexibility but can be harder to debug and control.
- Choosing between synchronous and asynchronous communication depends on trade-offs like latency vs. throughput, simplicity vs. resilience, and real-time response vs. eventual progress.
Read Full Article
13 Likes
Medium
297

Image Credit: Medium
How to Create and Sell Digital Products: A Step-by-Step Guide
- Digital products are intangible offerings delivered electronically, representing a fast-growing segment of the online marketplace.
- Examples of digital products include e-books, online courses, stock photos, music, software, and mobile applications, offering unique features and appealing to diverse market segments.
- Selling digital products comes with advantages such as low production costs, as they can be reproduced infinitely without significant additional expenses.
- E-books, for example, can be sold multiple times without reprinting or physical shipping, making them cost-effective for creators.
Read Full Article
17 Likes
Insider
36
Image Credit: Insider
Cybersecurity execs face a new battlefront: 'It takes a good-guy AI to fight a bad-guy AI'
- Generative artificial intelligence, such as large language models (LLMs), faces security threats like prompt injections and data exfiltration.
- The use of AI in cybersecurity to protect LLMs comes with costs, posing challenges to organizations.
- LLMs powered chatbots are susceptible to novel attacks like prompt injections and data exfiltration, impacting security.
- OpenAI faced a security breach when DeepSeek, a Chinese AI model, allegedly used distillation to train models by prompting ChatGPT.
- AI vulnerabilities exploit the unpredictable nature of LLMs, posing risks of intellectual property theft and information exposure.
- Cybersecurity experts emphasize the importance of securing the API used to access AI models to prevent exploitation.
- Training an LLM creates a neural network without specific data access restrictions, making data protection challenging.
- Companies are deploying AI-driven security solutions to analyze user prompts and model responses to detect malicious activities.
- The use of security-tuned AI models for protection is part of an evolving defense strategy against AI vulnerabilities in the cybersecurity landscape.
- However, the cost implications of using large AI models for security purposes make smaller models an alternative due to lower computational requirements.
Read Full Article
2 Likes
Medium
292

Image Credit: Medium
This Simple Trick Will Make Your Code Cleaner Overnight!
- Unformatted code with inconsistent styles leads to frustration and bugs.
- Prettier is a code formatter that enforces a consistent style across projects.
- Consistent naming conventions like camelCase for variables improve code readability.
- Automating code formatting with tools like Prettier and ESLint boosts team productivity.
Read Full Article
17 Likes
For uninterrupted reading, download the app