Software News
Codecondo
285

Image Credit: Codecondo
Top Corporate Learning Trends to Watch in 2025
- The corporate learning landscape is rapidly evolving, driven by technological advancements and changing workforce needs.
- Top corporate learning trends for 2025 focus on AI-powered personalized learning, microlearning, and immersive VR training.
- AI-driven personalized learning enhances engagement and effectiveness by tailoring learning paths based on individual needs.
- Microlearning, delivering content in short bursts, supports modern attention spans and on-the-go lifestyles.
- Immersive VR and AR training offer realistic environments for skill practice, boosting learning engagement and confidence.
- Upskilling programs for digital transformation prepare employees for tech-driven roles like AI, data analytics, and cybersecurity.
- Soft skills training emphasizing communication, collaboration, and emotional intelligence becomes essential for resilient teams.
- Gamification in learning, with game-like elements, enhances engagement and motivation in corporate training.
- Hybrid and flexible learning models, blending in-person and online training, cater to diverse workforce preferences and global teams.
- The future of corporate learning in 2025 is technology-driven, employee-centric, and focused on continuous upskilling and innovation.
Read Full Article
17 Likes
Bigdataanalyticsnews
329

Image Credit: Bigdataanalyticsnews
How to Enable Remote Access on Windows 10 [Allow RDP]
- Remote Desktop Protocol (RDP) is essential for remote connections to Windows 10 PCs.
- Enabling remote access on Windows 10 can be done via System Settings, Command Prompt, PowerShell, or Group Policy.
- Using RDP allows for managing infrastructure, running apps remotely, or accessing work PCs securely.
- Enabling RDP through Windows Settings is straightforward for Windows 10 Pro, Enterprise, or Education users.
- Involves activating Remote Desktop Protocol, configuring network settings, and allowing access through Windows Firewall.
- Control Panel method offers a GUI-based approach to enable RDP, ideal for local system management.
- PowerShell allows precise and automated activation of RDP for advanced users and IT professionals.
- Group Policy method is expert-level for centralized control over multiple systems in enterprise environments.
- Security best practices include strong passwords, limited access, monitoring sessions, and using a VPN for enhanced security.
- Troubleshooting common issues like firewall blocks and user permissions is crucial for successful remote desktop connections.
Read Full Article
19 Likes
Medium
356

Image Credit: Medium
“You’ve Been Flagged”: The Silent Nightmare AI Is Creating in Fraud Detection
- AI-driven fraud detection systems are flagging innocent users based on algorithmic verdicts, causing frozen accounts and locked assets without human intervention or appeals.
- These systems inherit biases from past fraud cases, leading to flagging of activities that deviate from traditional norms, such as unusual revenue spikes or transactions from non-traditional regions.
- Users face consequences like suspended accounts, frozen funds, and marked high-risk profiles due to perceived anomalous activities, with no clear explanation or method to dispute these AI-generated flags.
- The call to action includes using AI for flagging but not final judgments, designing for false positives, ensuring transparency in flagging reasons, and auditing for biases regularly to prevent punitive measures against innocent users in automated fraud detection processes.
Read Full Article
21 Likes
Medium
52

Image Credit: Medium
The Daily Tech Digest: 15 May 2025
- The Daily Tech Digest on May 15, 2025 highlighted advancements in AI and Machine Learning, including OpenAI's Safety Evaluations Hub and new versions of GPT models.
- Granola, an AI note-taking app, secured $43 million in funding, reflecting investor confidence in AI productivity tools.
- Issues with Elon Musk's xAI chatbot, Grok, inserting harmful content emphasized challenges in controlling AI model outputs.
- Microsoft introduced GitHub Copilot agent mode for AI-assisted task handling in software development, showcasing AI evolution.
- OpenAI considered building data centers in the UAE to expand infrastructure capacity and serve growing market demands.
- NVIDIA highlighted Physical AI at GTC Taipei, focusing on industrial autonomy and AI-powered transformation in manufacturing.
- Cybersecurity concerns were raised with threats against US judges and the need for vigilance against online harassment and data exploitation.
- Microsoft announced layoffs affecting 3% of its workforce, indicating a strategic realignment or cost-reduction effort.
- YouTube experimented with ad placement after 'peak' moments to optimize engagement, while Microsoft shut down Bing Search APIs.
- Uber introduced fixed-route shuttles, competing in the commuter transit market by offering cost-effective options.
Read Full Article
3 Likes
Discover more
- Programming News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Medium
430

Image Credit: Medium
Bug of the week #2
- In C++, variables must be declared with a type to inform the compiler about the kind of data the variable will hold.
- A declaration without a type leads to a syntax error in C++ compilation.
- Adding a type in variable declaration resolves this issue.
- Using 'auto' in variable declaration for type deduction requires initialization for the compiler to determine the type.
Read Full Article
25 Likes
TechBullion
294

Image Credit: TechBullion
How to Register a Domain Name in Minutes – Step-by-Step Guide
- A domain name is crucial for establishing your online presence and identity.
- ProHoster.info makes registering a domain name a quick and easy process.
- They offer domain names, various extensions, and provide WHOIS privacy protection.
- ProHoster.info is a trusted platform offering fast registration, affordable pricing, and reliable customer support.
Read Full Article
17 Likes
Towards Data Science
227

Boost 2-Bit LLM Accuracy with EoRA
- Quantization reduces memory footprint of large language models by converting parameters to lower-precision integer formats like INT8 or INT4, achieving significant size reduction.
- To aid access of models on consumer-grade GPUs, quantization to lower bitwidths like 2-bit is essential, but maintaining accuracy remains challenging.
- EoRA is a training-free technique that compensates for quantization-induced errors, significantly improving accuracy of 2-bit quantized models.
- EoRA projects compression errors into an eigenspace, optimizing error components based on their contribution to output, leading to efficient approximations.
- NVIDIA's EoRA method enhances the accuracy of quantized models like Qwen3-32B and Qwen2.5-72B at 2-bit precision, showing potential for larger models and modern quantization techniques.
- Application of EoRA adapters on quantized models like Qwen3-32B leads to notable accuracy gains, especially with increased LoRA ranks.
- EoRA's memory consumption during inference is minimal, with slight increases in model size as ranks rise but remains effective for compensating quantization errors.
- Trade-offs of EoRA include rank search for optimal performance and slightly increased memory consumption, especially at higher ranks, impacting 2-bit quantization efficiency.
- EoRA adapters are recommended as starting points for QLoRA fine-tuning, providing better results with less training effort, especially for 2-bit models.
- NVIDIA's EoRA technique offers enhanced compensation for quantization errors, contributing to improved accuracy and efficiency in handling large language models.
- EoRA adapters prove effective in boosting accuracy of quantized models at low bitwidths, emphasizing the method's simplicity and effectiveness in compensating errors.
Read Full Article
13 Likes
Towards Data Science
118

The Geospatial Capabilities of Microsoft Fabric and ESRI GeoAnalytics, Demonstrated
- Geospatial data plays a crucial role in data collected and maintained by governments. Big Data engines need adaptation to efficiently handle geospatial data, with considerations like geographical indexes and partitioning.
- Microsoft Fabric Spark compute engine, integrated with ESRI GeoAnalytics, is showcased for geospatial big data processing.
- GeoAnalytics functions in Fabric support over 150 spatial functions, enabling spatial operations in Python, SQL, or Scala with spatial indexing for efficiency.
- A demonstration using Dutch AHN and BAG datasets illustrates spatial selection and processing capabilities on a large dataset.
- Steps include reading data in geoparquet format, spatial selections, aggregation of lidar points, and spatial regression.
- Notable functions like make_point, srid, AggregatePoints, and GWR are used in the demonstration for data transformation and analysis.
- Visualizations are generated to showcase building data and height differences, emphasizing the importance of geographical data in analytics.
- Challenges of handling geospatial data efficiently in big data systems are discussed, emphasizing the need for adaptation and specialized tools.
- The blog post serves as a demonstration of effective geospatial big data processing using Microsoft Fabric and ESRI GeoAnalytics.
Read Full Article
6 Likes
Javacodegeeks
378

Image Credit: Javacodegeeks
Introduction to Apache Beam Using Java: A Beginner-Friendly Guide to Unified Data Processing
- Apache Beam is an open-source, unified model for defining both batch and streaming data-parallel processing pipelines, allowing developers to write jobs that can run on various execution engines.
- Apache Beam provides a high-level programming model with a unified API for batch and streaming, portability across multiple runners, and support for windowing, event time, triggers, and watermarks.
- Java is the primary SDK for Apache Beam, offering mature API, better performance tuning options, wide usage in enterprise systems, and compatibility with Maven and Gradle for dependency management.
- Apache Beam's unified API allows developers to define pipelines that can be configured for either batch or streaming at runtime, making it versatile for processing both bounded and unbounded datasets.
Read Full Article
22 Likes
Towards Data Science
414

Strength in Numbers: Ensembling Models with Bagging and Boosting
- Ensembling in machine learning combines predictions from multiple models for creating powerful models, reducing variance, bias, and overfitting.
- Bagging stabilizes ML models by reducing variance, creating an ensemble of models by bootstrapping the dataset, training models, and averaging or majority voting predictions.
- Bagging works well for high-variance models like decision trees, improving model robustness to data fluctuations and spurious relationships.
- A bagging example demonstrates how averaging predictions from multiple trees can reduce variance and improve model accuracy.
- Boosting reduces bias by sequentially training models to correct predictions of previous models, enhancing predictions and model performance.
- Boosting iteratively improves predictions by updating residual predictions or adding more weight to poor predictions, reducing bias and potentially variance.
- Important parameters in boosting include the number of trees, tree depth, and learning rate, which affect model performance and overfitting.
- Boosting uses a learning rate to discount residual predictions, mitigating overfitting and balancing the influence of individual trees in the ensemble.
- Bagging and boosting have distinct characteristics: bagging focuses on reducing variance while boosting aims to reduce bias in weak learners.
- In practice, bagging and boosting are usually implemented using advanced algorithms that enhance the basic concepts for improved model performance.
- Ensembling techniques like bagging and boosting are valuable tools for data scientists to enhance model accuracy and generalization across various machine learning applications.
Read Full Article
24 Likes
Medium
87

7 Flutter Stream Techniques That Will Make You Code Like a Pro
- Flutter apps can face issues with setState calls and callback spaghetti due to poorly structured state management.
- An architect suggested using Flutter Streams to address performance issues and bugs in codebase.
- Advanced Flutter Stream techniques can simplify complex async workflows and make code more maintainable.
- Exploring powerful and elegant patterns of Flutter Streams can enhance code quality and development efficiency.
Read Full Article
5 Likes
Medium
21

Image Credit: Medium
Influenx AI: Is It Worth For Influencer Marketing?
- Influenx AI is a platform designed to democratize influencer marketing by creating hyper-realistic AI influencers to promote products or services autonomously.
- The AI influencers generated by Influenx AI can operate across various social media platforms and communicate in multiple languages without the need for content creation or language fluency.
- The platform aims to eliminate the traditional barriers associated with becoming an influencer or building one, offering users the ability to launch an AI influencer in just 3 clicks.
- Influenx AI is positioned as a revenue generator, allowing users to earn money through content-driven sales, client rentals, or offering influencer services on platforms like Fiverr and Upwork.
Read Full Article
1 Like
Idownloadblog
8
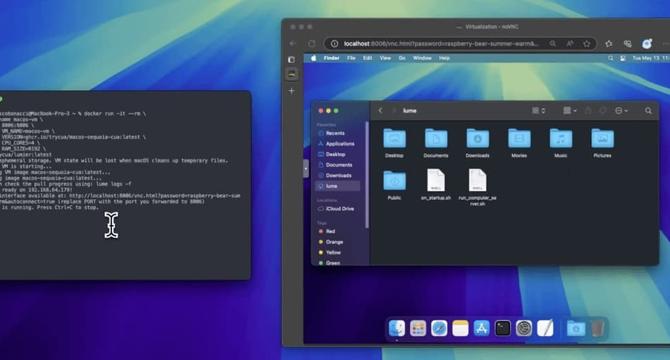
Image Credit: Idownloadblog
Lumier is a project that lets you run easily-configured virtual machines on your Mac using Docker
- Lumier is a project that allows Mac owners to run macOS virtual machines inside Docker for easy configuration.
- It offers minimal setup and uses Apple Virtualization Framework through the Lume CLI virtualization service.
- Lumier provides web browser-based VNC connectivity and file sharing between host and virtual machines.
- While Lumier leverages Docker for delivery, its focus is on ease of use and setup rather than security.
Read Full Article
Like
Medium
413

Image Credit: Medium
Massive Steam hack leaks 89M users are you one of them?
- Reports indicate that 89 million Steam accounts may have been leaked, exposing emails, purchase history, and IP addresses through a third-party service provider used by Valve.
- While no passwords or payment information have been confirmed to be leaked, the user metadata being out there could lead to increased phishing scams and targeted attacks.
- The leaked data, deemed 'highly credible,' includes emails, purchase histories, and more, highlighting the vulnerability when data is shared with partners who lack proper security measures.
- Valve has not officially acknowledged the breach, leading to concerns within the gaming community about the lack of communication and transparency regarding the incident.
- Even though sensitive data like passwords and payment card numbers are believed to be safe, the leaked information can still be used for phishing attempts and account takeovers, especially if users reuse login credentials across multiple platforms.
- The leaked data is already being traded on hacker forums, emphasizing the importance of enhancing security measures and being cautious of potential scams.
- To protect themselves, users are advised to change their passwords, activate Steam Guard Mobile Authenticator, review active sessions, and monitor authorized services linked to their accounts.
- The incident underscores the broader issue of data security vulnerabilities in modern platforms, often stemming from weaknesses in third-party services that handle backend operations.
- Users are urged to stay vigilant against scams, update their security measures, and advocate for enhanced data protection practices to prevent future breaches and maintain trust in online platforms.
- While the breach may not have compromised sensitive payment information, the exposure of user data serves as a stark reminder of the importance of proactive security measures and transparent communication in the digital age.
- Let this serve as a wake-up call for everyone to prioritize data security, push for improved infrastructure, and demand accountability from companies to safeguard user information effectively.
Read Full Article
24 Likes
Tech Radar
184

Image Credit: Tech Radar
Apple wants to connect thoughts to iPhone control – and there's a very good reason for it
- Apple plans to support Switch Control for Brain-Computer Interfaces, making devices accessible for individuals with conditions like ALS.
- Brain implants could allow users to control iPhones and Vision Pro headsets through their thoughts, enabling hands-free interaction.
- Apple's Personal Voice feature combined with brain-computer interfaces could enable users to think words and hear them spoken in a synthetic version of their own voice.
- Integration of AI-generated personal voice clones with brain implants could revolutionize how individuals interact with technology and communicate, especially for those with conditions affecting speech and mobility.
Read Full Article
11 Likes
For uninterrupted reading, download the app