Cyber Crime News
Securityaffairs
269

Image Credit: Securityaffairs
Security Affairs newsletter Round 524 by Pierluigi Paganini – INTERNATIONAL EDITION
- US Government officials targeted with texts and AI-generated deepfake voice messages impersonating senior U.S. officials
- New botnet HTTPBot targets gaming and tech industries with surgical attacks
- Google fixed a Chrome vulnerability that could lead to full account takeover
- Coinbase disclosed a data breach after an extortion attempt
Read Full Article
16 Likes
Livebitcoinnews
279

Image Credit: Livebitcoinnews
New Zealand Man Busted in $265M Crypto Scam
- Authorities arrested a man from Wellington, New Zealand for his suspected involvement in a $265 million cryptocurrency fraud case.
- FBI-led investigation targeted 13 suspects across New Zealand and the United States, with funds being used for luxury purchases like cars, handbags, and rentals.
- The suspects manipulated seven victims to acquire cryptocurrency between March and August 2024, involving deceitful practices to hide the money trail.
- The FBI-led global investigation uncovered a complex network using international links and cryptocurrencies, highlighting the importance of addressing cybercrime in the crypto space.
Read Full Article
16 Likes
Securityaffairs
151
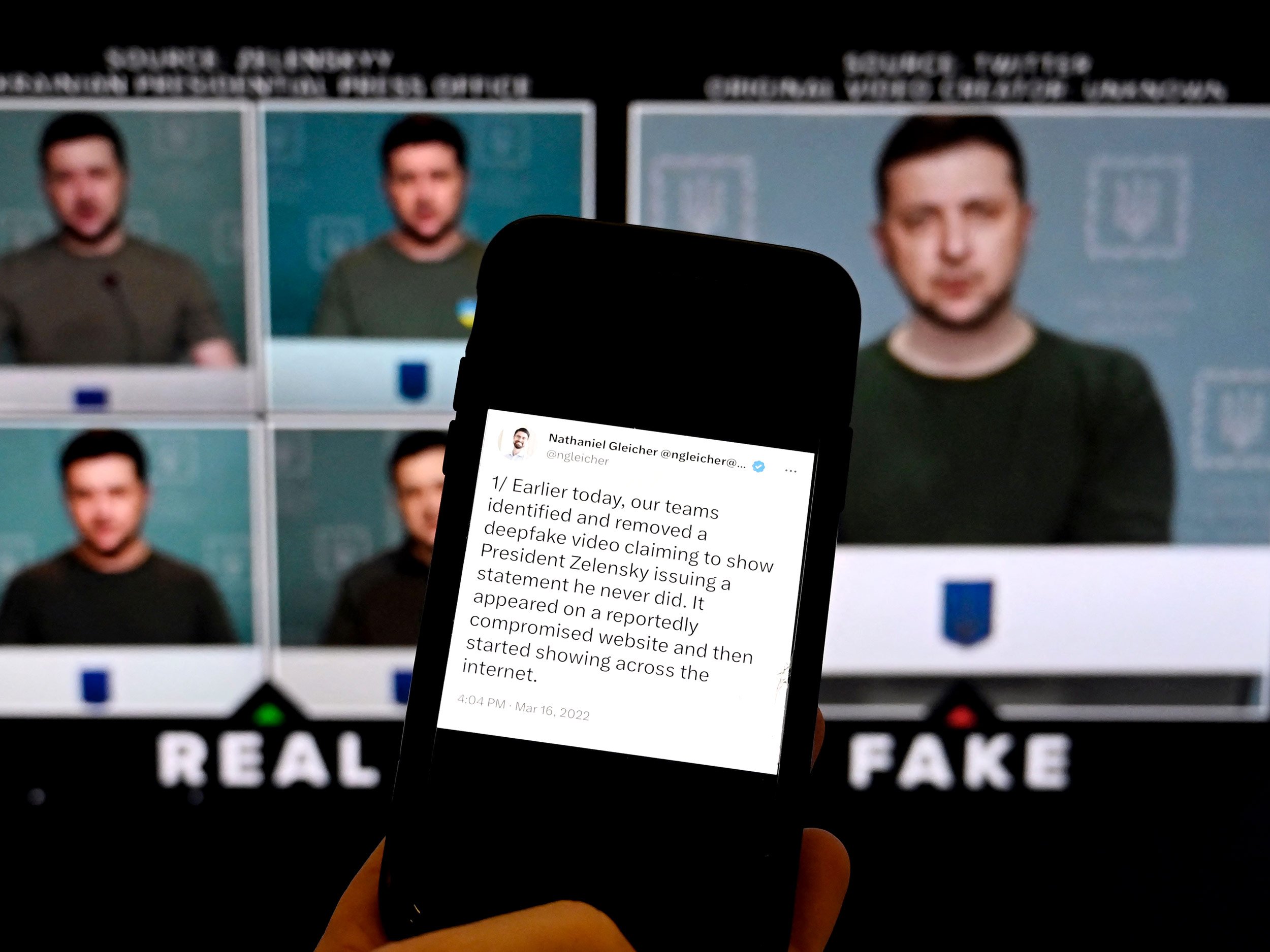
Image Credit: Securityaffairs
US Government officials targeted with texts and AI-generated deepfake voice messages impersonating senior U.S. officials
- The FBI warns ex-government officials of being targeted with deepfake texts and AI-generated voice messages impersonating senior U.S. officials.
- Threat actors have been using texts and AI voice messages since April 2025 to access personal accounts of officials and their contacts.
- Malicious links are sent to officials posing as messaging platform invites, allowing threat actors to extract data or funds through impersonation.
- To avoid falling for AI-powered scams, officials are advised to verify callers' identities, check for errors in messages, and avoid sharing sensitive information with unknown contacts.
Read Full Article
9 Likes
Securityaffairs
219

Image Credit: Securityaffairs
Shields up US retailers. Scattered Spider threat actors can target them
- Cybercrime group Scattered Spider, known for social engineering and extortion, is now targeting U.S. companies after focusing on UK retailers.
- UNC3944 (Scattered Spider) has hacked numerous organizations, including Twilio, LastPass, DoorDash, and Mailchimp, transitioning from telecoms to ransomware and broader sectors by 2023.
- Threat actors linked to Scattered Spider used DragonForce ransomware to target UK retailers, exploiting the large trove of PII and financial data held by retailers.
- Google experts suggest that UNC3944 targets sectors like Tech, Telecom, Finance, and Retail, focusing on large enterprises in English-speaking countries and beyond by using social engineering tactics for high-impact attacks.
Read Full Article
13 Likes
TechBullion
311

Image Credit: TechBullion
How to Get Your Crypto Back After a Phishing Scam: Emergency Action Plan 2025
- In 2023, users and investors lost $4.6 billion to crypto scams, showing a 30% decrease from the previous year, with crypto scams growing by 900% since the pandemic began.
- Phishing scams in crypto target victims to reveal sensitive information like passwords and private keys through deceptive messages from seemingly legitimate sources.
- Crypto transactions cannot be reversed once funds are transferred to another wallet, making recovery challenging but not impossible.
- Emergency steps to retrieve stolen cryptocurrency involve contacting recovery services like HackersTent, providing loss details and transaction histories for better recovery chances.
- Phishing attacks exploit human vulnerabilities, using fear, greed, and urgency to trick individuals into surrendering digital assets.
- Scammers target private keys and seed phrases that provide full control over wallets, emphasizing the importance of safeguarding these credentials.
- After falling victim to a phishing attack, securing remaining assets by isolating compromised devices, conducting scans for malware, and setting up a new secure wallet is crucial.
- Effective prevention methods against crypto scams include verifying offers, conducting thorough research on projects, monitoring wallet activities, and utilizing security tools like HackersTent Recovery Service.
- With $4.6 billion stolen in 2023, recovering stolen cryptocurrency requires quick action, secure practices, and professional help from blockchain forensics firms like HackersTent.
- Seeking immediate assistance after a scam, implementing strong security measures, verifying exchanges for recovery support, and utilizing professional blockchain forensic tools are essential for successful recovery.
Read Full Article
18 Likes
TheNewsCrypto
36

France Boosts Security for Crypto Entrepreneurs Amid Rise in Kidnappings
- France has increased security measures for crypto entrepreneurs and their families following a rise in crypto-related kidnappings.
- The measures include prioritizing access to police emergency lines, home security assessments, and safety briefings from French law enforcement.
- Interior Minister Bruno Retailleau aims to use tools to prevent and counter repeated kidnappings of professionals in the industry.
- Recent attacks in France include attempted kidnapping of a crypto platform CEO's daughter and grandson, highlighting the need for increased security in the crypto sector.
Read Full Article
2 Likes
Securityaffairs
412
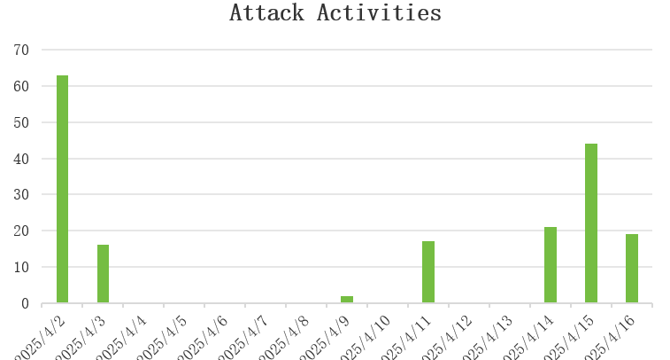
Image Credit: Securityaffairs
New botnet HTTPBot targets gaming and tech industries with surgical attacks
- A new botnet named HTTPBot is targeting China’s gaming, tech, and education sectors, as discovered by cybersecurity researchers.
- HTTPBot, a Go-based botnet detected in August 2024, intensified its activities by April 2025, engaging in highly targeted attacks using advanced DDoS tactics.
- The botnet employs various HTTP-based attack methods to conduct precise transactional DDoS attacks on critical interfaces, posing a systemic threat to industries reliant on real-time interaction.
- HTTPBot features 7 built-in DDoS attack methods, evades detection through techniques like Base64 encoding, and specifically targets the Windows platform, making it a significant threat in the cybersecurity landscape.
Read Full Article
24 Likes
Unite
9

Image Credit: Unite
The State of AI Security in 2025: Key Insights from the Cisco Report
- AI adoption is increasing rapidly, but organizations face significant security risks that need to be addressed for trust, privacy, and business continuity.
- Cisco's 'State of AI Security in 2025' report emphasizes the gap between AI adoption rates and organizational readiness to secure AI systems effectively.
- New threats in AI security include infrastructure attacks targeting AI frameworks like NVIDIA's Container Toolkit and Ray, as well as supply chain vulnerabilities.
- Emerging AI-specific attacks like prompt injection, jailbreaking, and training data extraction pose challenges to traditional cybersecurity methods.
- Attack vectors targeting AI systems include jailbreaking, indirect prompt injection, and training data poisoning, making AI systems vulnerable at various stages of their lifecycle.
- Cisco's research reveals vulnerabilities in top AI models, risks in fine-tuning models, training data extraction methods, and the ease and impact of data poisoning.
- AI is not only a target for cyber threats but also a tool for cybercriminals, enabling more effective attacks and personalized scams.
- Best practices for securing AI systems include risk management across the AI lifecycle, using established cybersecurity practices, focusing on vulnerable areas like supply chains, and educating employees on AI security risks.
- As AI adoption continues to rise, organizations need to prioritize security alongside innovation to navigate evolving security risks and opportunities in the AI landscape.
Read Full Article
Like
Pymnts
73

Image Credit: Pymnts
Coinbase Says Cybersecurity Incident Could Cost It $400 Million
- Coinbase disclosed a cybersecurity incident that could cost it up to $400 million.
- The company's investigation is ongoing, with estimated expenses ranging from $180 million to $400 million for remediation and customer reimbursements.
- The cyberattack involved data stolen from Coinbase, used for social engineering trickery leading to an attempted $20 million extortion.
- Coinbase is setting up a $20 million reward fund for information on the cyberattackers, as social engineering fraud rises by 56%.
Read Full Article
4 Likes
Guardian
137
Image Credit: Guardian
Scattered Spider hackers in UK are ‘facilitating’ cyber-attacks, says Google
- UK-based Scattered Spider hackers are 'facilitating' cyber-attacks on British and US retailers, according to Google.
- The hackers have targeted UK retailers like Marks & Spencer, the Co-op, and Harrods, with a shift to US organizations observed.
- Scattered Spider group employs tactics like pretending to be employees to gain access to company systems, prompting cybersecurity warnings.
- The group consists of native English speakers and is associated with ransomware attacks on targeted sectors like retail, including recent US operations.
Read Full Article
8 Likes
HRKatha
394

Image Credit: HRKatha
Were Coinbase employees responsible for data leak to hacker?
- A hacker has bribed Coinbase Global's contractors or employees outside the US to access confidential customer information and is now demanding a $20 million ransom.
- The hacker bribed customer-support employees to obtain customer data like names, addresses, and government identity pictures to potentially use in scams and extort money from the exchange.
- Coinbase CEO Brian Armstrong revealed the ransom demand on social media and stated that the breach may cost the exchange up to $400 million.
- Coinbase is improving security measures, offering compensation to affected users, and is ready to pay a $20 million reward for information leading to the hacker's apprehension.
Read Full Article
23 Likes
Securityaffairs
64

Image Credit: Securityaffairs
Nova Scotia Power discloses data breach after March security incident
- Nova Scotia Power confirmed a data breach after a security incident in April where sensitive customer data was stolen.
- In April, Nova Scotia Power and Emera experienced a cyber attack affecting their IT systems without causing power outages.
- The companies shut down affected servers due to unauthorized network access detected on April 25, impacting customer services.
- The data breach involved theft of customer information including names, contact details, account history, driver’s license numbers, and Social Insurance Numbers.
Read Full Article
3 Likes
Medium
183

Image Credit: Medium
The Great Steam “Hack” of 2025
- Headlines blared about '89 Million Steam Accounts Hacked', causing a stir in the gaming community.
- Hackers attempted to sell secret data for $5,000, but the actual 'stolen' data turned out to be expired SMS 2FA codes and unlinked phone numbers.
- Valve dismissed the incident as no breach, clarifying that only outdated codes were involved.
- Ultimately, the hackers did not gain access to valuable information like passwords or credit card details, leaving the gaming world relieved.
Read Full Article
11 Likes
TronWeekly
166

Image Credit: TronWeekly
Telegram Silently Dismantles $27B Darknet Giant Haowang Guarantee
- Telegram shut down the darknet marketplace Haowang Guarantee, formerly Huione Guarantee, following its clampdown on associated accounts and channels on May 13.
- Haowang Guarantee was involved in billions of dollars worth of illicit crypto transactions and was known for enabling online fraud, cybercrimes, and large-scale cryptocurrency laundering.
- Blockchain company Elliptic identified over $27 billion in contraband crypto-transactions linked to Haowang Guarantee, predominantly processed through Tether stablecoin.
- Despite the closure of Haowang Guarantee, another darknet market named Xinbi Guarantee has emerged on Telegram, conducting $8.4 billion in crypto transactions primarily through stablecoins.
Read Full Article
9 Likes
Securityaffairs
293

Image Credit: Securityaffairs
Coinbase disclosed a data breach after an extortion attempt
- Coinbase disclosed a data breach after rogue contractors stole customer data and demanded a $20M ransom.
- The breach, affecting under 1% of users, was reported to the SEC after a ransom demand was received on May 11, 2025.
- The unauthorized access was detected in previous months, leading to termination of involved personnel and implementation of heightened fraud-monitoring measures.
- Compromised data includes contact details, partial SSNs and bank info, ID images, account history, and limited internal documents but did not expose passwords, private keys, or customer funds.
Read Full Article
17 Likes
For uninterrupted reading, download the app