Cyber Crime News
TechCrunch
288

Image Credit: TechCrunch
Health giant Kettering still facing disruption weeks after ransomware attack
- Kettering Health in Ohio is still recovering from a ransomware attack, causing significant disruption in its operations for the past two weeks.
- Core components of the electronic health record system have been restored, allowing for updates and access to records, but issues with phone lines and services persist.
- Patients are facing challenges such as difficulty in refilling medications, closed emergency rooms, and delays in care due to manual record-keeping processes.
- The ransomware gang called Interlock is believed to be behind the attack, with hackers potentially trying to negotiate a ransom payment, making Kettering Health the latest in a series of healthcare companies targeted by cyberattacks.
Read Full Article
17 Likes
Medium
396

Image Credit: Medium
A Peek Into Nova Scotia, Canada’s Cyberspace & The Dangers In Our Digital Lives
- Recent cyberattacks in Nova Scotia, Canada have exposed the vulnerabilities of individuals' personal information in the digital realm.
- Nova Scotia Power fell victim to a ransomware attack, compromising over 140,000 Social Insurance Numbers and affecting a quarter of a million people.
- The PowerSchool breach impacted approximately 35,000 students and 3,200 employees, with stolen data including personal details and encrypted passwords.
- The MOVEit breach exposed records of teachers, students, and pension plan recipients in Nova Scotia, highlighting widespread vulnerabilities.
- Individuals affected by these breaches face challenges in safeguarding their identities, leading to financial hardships and emotional distress.
- The growing trend of cyberattacks targeting various sectors necessitates organizations to prioritize information security and proactive measures.
- To protect personal information, individuals are advised to monitor accounts, use strong passwords, enable two-factor authentication, avoid phishing attempts, and stay informed about cybersecurity threats.
- As technology integrates into daily life, the importance of cybersecurity is crucial to mitigate risks in the digital age and protect against evolving cyber threats.
- The breaches in Nova Scotia serve as reminders of the digital world's vulnerabilities, emphasizing the need for vigilance and awareness to safeguard personal data.
- Staying informed, vigilant, and proactive can help individuals and communities navigate the digital landscape and protect against potential cyber threats.
Read Full Article
23 Likes
TechDigest
405

Image Credit: TechDigest
Cartier and North Face become latest retailers hit by cyber attacks
- Cartier and The North Face have confirmed customer data breaches following separate cyber attacks.
- The North Face detected a 'small-scale' attack in April, while Cartier reported an 'unauthorized party' gaining temporary access to their system.
- Both companies had customer names and email addresses stolen, but no financial information was compromised.
- The cyber attacks on these retailers highlight an increasingly threatening landscape for the retail sector, with a growing number of high-profile breaches taking place.
Read Full Article
24 Likes
Securityaffairs
284
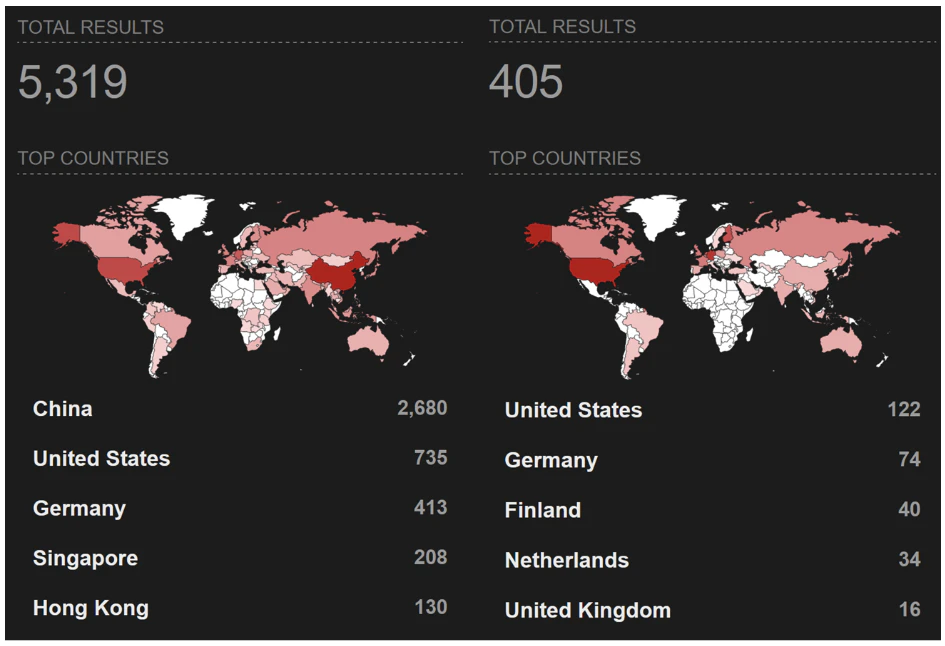
Image Credit: Securityaffairs
Cryptojacking campaign relies on DevOps tools
- A cryptojacking campaign, known as JINX-0132, is targeting exposed DevOps servers like Docker and Gitea to mine cryptocurrency secretly.
- The threat actors exploit misconfigurations and vulnerabilities in tools like Nomad, Consul, Docker, and Gitea to deliver the miner.
- The attackers rely on public GitHub tools and XMRig versions instead of custom malware, making attribution and clustering difficult.
- This campaign highlights the importance of securing DevOps tools properly, as 25% of cloud environments use these technologies, with 5% exposed directly to the internet and 30% of those misconfigured.
Read Full Article
17 Likes
Pymnts
347

Image Credit: Pymnts
Report: Coinbase Learned of Data Breach in January
- Coinbase was aware of a data breach at an outsourcing company back in January, which was publicly disclosed in a filing with the SEC on May 14.
- The breach was discovered when an employee from the outsourcing company in India was found taking photos of data on her work computer.
- Cybercriminals attempted to extort Coinbase for $20 million after a 'small group' of company insiders copied data from customer support tools.
- Coinbase initiated measures like firing compromised employees, setting up a reward fund, and reimbursing customers tricked by cybercriminals, with potential costs estimated between $180 million and $400 million.
Read Full Article
20 Likes
Medium
379

Image Credit: Medium
Understanding and Mitigating Phishing and Social Engineering Attacks
- Phishing and social engineering attacks exploit human psychology to trick individuals into disclosing sensitive information or taking harmful actions.
- Phishing involves sending deceptive emails or texts, and the goal is to acquire confidential data like passwords or credit card information.
- Spear phishing targets specific individuals or organizations with personalized messages to increase credibility and success rates.
- Whaling is a form of spear phishing that targets high-profile individuals for potentially large payoffs.
- Vishing involves phone calls to gather personal information by posing as legitimate entities like banks or companies.
- Smishing uses text messages with malicious links to deceive recipients into giving away sensitive data.
- Pretexting involves fabricating scenarios to engage victims and extract their information, often by impersonating trustworthy figures.
- Scammers use baiting attacks to entice victims with appealing offers that lead to security breaches.
- Understanding the signs of phishing, such as generic greetings and urgent demands for sensitive information, can help individuals avoid falling for scams.
- Practicing caution with email attachments, verifying suspicious communications independently, and enabling two-factor authentication are recommended safeguards against social engineering attacks.
Read Full Article
22 Likes
Securityaffairs
85
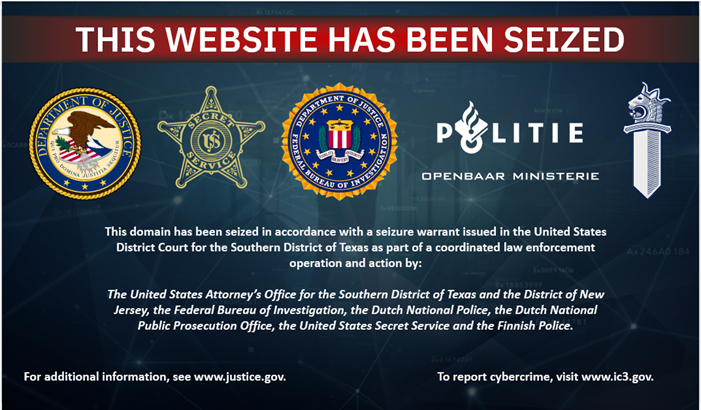
Image Credit: Securityaffairs
Police took down several popular counter-antivirus (CAV) services, including AvCheck
- On May 27, 2025, authorities seized crypting service sites (including AvCheck, Cryptor, and Crypt.guru) used by cybercriminals to test malware evasion capabilities.
- An international law enforcement operation, spearheaded by the U.S. Department of Justice, dismantled an online cybercrime syndicate providing encryption services to help malware evade detection.
- The operation, named Endgame, involved global efforts from U.S., Dutch, Finnish, and other national police forces to shut down malware services. The seized domains offered counter-antivirus tools for cybercriminals.
- CAV services like AVCheck enable cybercriminals to test their malware against antivirus programs discreetly, allowing them to gain unauthorized access to computer systems undetected. Undercover agents confirmed the services were linked to ransomware groups behind attacks in the U.S. and abroad.
Read Full Article
5 Likes
Managedmethods
347

Image Credit: Managedmethods
How Artificial Intelligence Phishing Detection Is Reshaping K–12 Email Protection
- Artificial intelligence phishing detection is revolutionizing email security in K–12 education by combating socially engineered and personalized threats.
- Current email filters in schools often fail to catch sophisticated phishing attempts that impersonate trusted entities, leading to targeted attacks and ransomware incidents.
- New AI-powered phishing detection tools utilize reasoning AI to analyze emails contextually, flagging convincing phishing messages that evade traditional filters.
- ManagedMethods introduces Advanced Phishing tool for K–12, leveraging AI to enhance cybersecurity defenses and protect students, staff, and district finances efficiently.
Read Full Article
20 Likes
Securityaffairs
198

Image Credit: Securityaffairs
A cyberattack hit hospitals operated by Covenant Health
- A cyberattack hit three hospitals operated by Covenant Health, leading to a shutdown of all systems to contain the incident.
- The cyberattack impacted services at St. Mary’s Health System and St. Joseph Hospital, requiring adjustments in outpatient lab services.
- Covenant Health Systems, a non-profit Catholic regional health care system, experienced the cyberattack, starting on May 26, 2025.
- At this time, no ransomware group has claimed responsibility for the attack, while previous cyberattacks have targeted healthcare organizations in the U.S.
Read Full Article
11 Likes
Silicon
45
Image Credit: Silicon
Victoria’s Secret, Adidas Hit By Cyber-Attacks
- Victoria's Secret and Adidas were hit by cyber-attacks, affecting their online and in-store services.
- Victoria's Secret paused online orders and some in-store services after a security incident, while Adidas reported stolen customer contact information from a third-party provider.
- Recent incidents of cyber-attacks also impacted British retailers like Marks & Spencer and the Co-op Group in late April.
- UK authorities are investigating potential connections to a hacking group called Scattered Spider, which has a history of targeting companies in various sectors using social engineering techniques.
Read Full Article
2 Likes
Securityaffairs
280

Image Credit: Securityaffairs
Security Affairs newsletter Round 526 by Pierluigi Paganini – INTERNATIONAL EDITION
- Two Linux flaws found can expose sensitive data. Meta stopped covert operations from Iran, China, and Romania spreading propaganda.
- US Treasury sanctions Funnull Technology for cyber scam facilitation. ConnectWise faces cyberattack from a sophisticated nation-state actor.
- Victoria’s Secret website offline due to a cyberattack. APT41 uses Google Calendar for malware control.
- New AyySSHush botnet compromises 9,000 ASUS routers. Czech Republic accuses China’s APT31 for a cyberattack.
Read Full Article
16 Likes
Guardian
312
Image Credit: Guardian
UK banks urged to beef up anti-fraud systems for international payments
- UK banks and payment firms are urged to strengthen their anti-fraud systems for international payments due to an increase in scammers tricking people into sending money abroad.
- Cases of authorised push payment (APP) scams decreased by 20% last year, but the total amount lost to APP fraud only decreased by 2% to £450m.
- A notable increase in APP scams involving international payments has been observed, with victims unlikely to get their money back as these transactions are not covered by the new reimbursement rules.
- Fraud tactics in the UK and Europe include fake sales websites, malicious app scams, 'ghost taps' using card details, and AI-driven identity fraud.
Read Full Article
18 Likes
TechCrunch
13

Image Credit: TechCrunch
White House investigating how Trump’s chief of staff’s phone was hacked
- The White House is investigating the hacking of chief of staff Susie Wiles' phone, where attackers accessed contacts and impersonated her.
- Hackers used AI to imitate Wiles' voice in phone calls and sent text messages from a different number.
- Authorities are determining if the cloud account associated with Wiles' device was compromised or if a more advanced cyberattack was involved.
- This is the second time Wiles has been targeted by hackers, with a previous incident involving Iranian hackers obtaining Vice President JD Vance's dossier.
Read Full Article
Like
Schneier
307

Why Take9 Won’t Improve Cybersecurity
- The "Take9" cybersecurity awareness campaign suggests pausing for nine seconds before clicking on links or downloading files, but it is not practical or effective in improving cybersecurity.
- A similar campaign called "Stop. Think. Connect." from 2016 also failed to make a significant impact in cybersecurity awareness.
- The concept of pausing for nine seconds lacks scientific basis and does not address the root causes of cybersecurity vulnerabilities.
- Pausing may help break habits but does not help individuals differentiate between legitimate actions and potential attacks.
- A successful awareness campaign should guide users through a process of suspicion and evaluation, offering specific guidance on how to make better decisions.
- Current phishing attacks have evolved to be more sophisticated, making it challenging for users to detect scams even with pauses or awareness training.
- Blaming users for falling victim to cyberattacks is not productive, as it ignores the role of system design in creating insecure environments.
- Security awareness campaigns should not solely rely on user behavior change but also require improved system designs and comprehensive cognitive support.
- Meaningful cybersecurity improvements demand more than a pause and necessitate a holistic approach to address the complex interactions influencing decision-making.
- Relying on awareness campaigns alone without addressing system vulnerabilities perpetuates a flawed blame-the-user mentality that undermines overall cybersecurity efforts.
Read Full Article
18 Likes
Securityaffairs
176
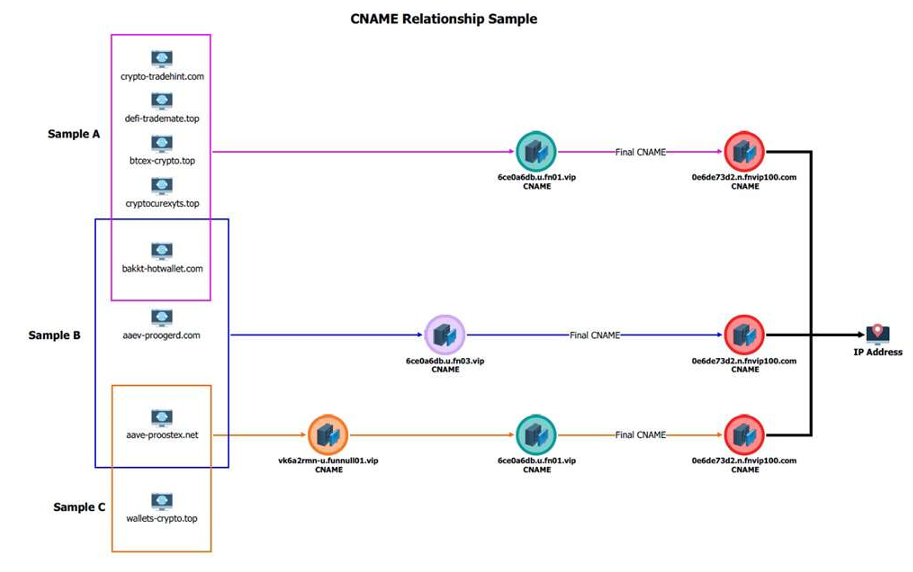
Image Credit: Securityaffairs
US Treasury sanctioned the firm Funnull Technology as major cyber scam facilitator
- The U.S. Treasury sanctioned Funnull Technology and Liu Lizhi for facilitating romance scams leading to significant losses in cryptocurrency fraud.
- Funnull Technology Inc. aided in cyber scams by providing infrastructure for fake platforms, resulting in over $200 million in losses for U.S. victims.
- Romance scams involve scammers building fake romantic relationships to exploit victims for financial gain by manipulating them into sending money or sensitive information.
- The FBI issued a FLASH alert highlighting indicators of compromise associated with Funnull's malicious cyber activities, including patterns of IP address activity and domain migrations.
Read Full Article
10 Likes
For uninterrupted reading, download the app