Cyber Crime News
Guardian
77
Image Credit: Guardian
M&S contractor ‘investigating whether it was gateway for cyber-attack’
- An Indian company operating Marks & Spencer's IT helpdesk is investigating if it was used as a gateway for cybercriminals to access the retailer's systems.
- M&S confirmed that hackers used 'social engineering' techniques to gain access, with potential costs of up to £300m in profit.
- Tata Consulting Services (TCS), a contractor for M&S, is conducting an internal inquiry to determine if its employees or systems were linked to the cyber-attack.
- The Information Commissioner's Office (ICO) may impose fines for any loss of customer and staff data, as M&S faces disruptions in operations with its website not expected to be fully functional until July.
Read Full Article
4 Likes
Securityaffairs
22
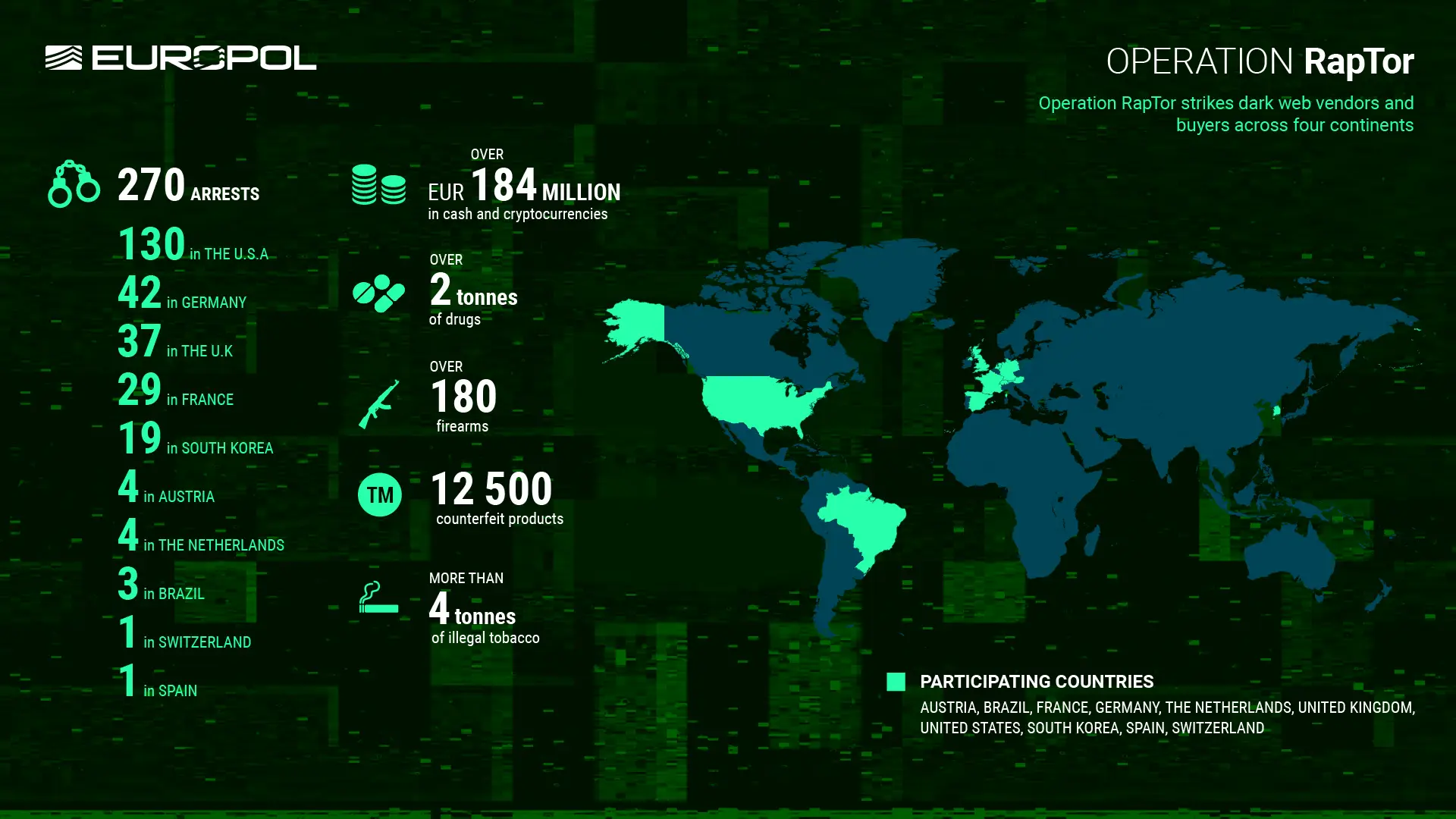
Image Credit: Securityaffairs
Operation RapTor led to the arrest of 270 dark web vendors and buyers
- Operation RapTor led to the arrest of 270 dark web vendors and buyers across 10 countries.
- The operation dismantled networks involved in trafficking drugs, weapons, and counterfeit goods.
- Europol supported the action by sharing intelligence packages with national authorities for targeted investigations.
- Authorities seized over €184M in cash and crypto, 2+ tonnes of drugs, 180+ firearms, 12,500 counterfeit items, and 4+ tonnes of illegal tobacco, striking a major blow to dark web criminal networks.
Read Full Article
1 Like
Cybersafe
438

Image Credit: Cybersafe
Chinese Hackers exploit Trimble Cityworks flaw to infiltrate U.S. Local Government Systems
- Chinese state-linked threat group UAT-6382 exploited a deserialization vulnerability in Trimble Cityworks software to compromise U.S. local government networks.
- The vulnerability, CVE-2025-0994, despite being patched, has been leveraged since January by UAT-6382 to breach municipal systems and deploy Chinese-language web shells and custom malware focused on utility networks.
- UAT-6382 used tools like AntSword, Chopper, Behinder, and a Rust-based malware loader named TetraLoader to maintain access, steal sensitive files, and implant backdoors across compromised environments.
- Indicators of compromise (IOCs) have been released by Cisco Talos to help organizations detect and defend against similar intrusions, highlighting the threat posed by APTs targeting critical infrastructure through known vulnerabilities.
Read Full Article
26 Likes
Cybersafe
118

Image Credit: Cybersafe
U.S. Dismantles DanaBot Malware Network in major Global cybercrime bust
- The U.S. Department of Justice (DoJ) announced the dismantling of the DanaBot malware infrastructure and indicted 16 individuals for running a global malware-as-a-service (MaaS) operation causing over $50 million in damages.
- Operation Endgame, targeting DanaBot, led to the seizure of its command-and-control servers, with the malware infecting over 300,000 devices globally through spam emails.
- DanaBot evolved from a banking trojan into a multifunctional platform involving credential theft, keylogging, video capture, and ransomware facilitation, attracting cybercriminal affiliates through monthly fees.
- The takedown reflects a broader crackdown on cybercrime, with private sector collaboration playing a key role in disrupting criminal operations and increasing challenges for cybercriminals to operate freely.
Read Full Article
7 Likes
TechJuice
369

Image Credit: TechJuice
Firefox and Chrome Vulnerable to Cyber Threats, NCERT Warns
- NCERT issues urgent advisory warning of serious vulnerabilities in latest versions of Firefox and Chrome browsers.
- Firefox vulnerabilities showcased at Pwn2Own contest; Chrome's WebAssembly flaw poses significant risk.
- Several critical zero-day vulnerabilities reported with active exploitation, allowing attackers to execute arbitrary code and deploy malware.
- Users and organizations advised to apply available patches and take immediate mitigation measures to prevent cyber threats.
Read Full Article
22 Likes
Siliconangle
169

Image Credit: Siliconangle
Cybersecurity researcher discovers database with millions of login credentials
- A cybersecurity researcher discovered an exposed Elasticsearch database with millions of login credentials on May 6.
- The database contained 184 million records taking up 47 gigabytes of storage space, with login credentials associated with millions of accounts from various services like Google, Facebook, Roblox, Discord, and others.
- There were 220 email addresses with .gov domains linked to government agencies in at least 29 countries, including the U.S., UK, and Australia.
- The database was hosted on infrastructure operated by World Host Group, a U.K.-based hosting provider, which took it down after being notified by the researcher.
Read Full Article
10 Likes
Livebitcoinnews
50

Image Credit: Livebitcoinnews
Coinbase Insider Attack Exposes Data of 69K Users
- 69K plus consumers’ data exposed in a Coinbase breach where hackers bribed overseas support staff to steal customer information.
- Data breach exposed personal information of users but no passwords or funds were compromised; Coinbase Prime users were unaffected.
- Hackers obtained names, email addresses, addresses, phone numbers, government IDs, and transaction data, leading to an extortion request of $20 million.
- Coinbase took steps to help affected users, including reimbursement for social-engineering attack losses, offering identity protection, and enhancing security measures.
Read Full Article
3 Likes
Dataprivacyandsecurityinsider
305

Data Breach Lawsuits Surge Against Chord Specialty Dental Partners
- Seven proposed class action lawsuits have been filed against Chord Specialty Dental Partners following a September 2024 data breach affecting over 173,000 individuals.
- Plaintiffs allege that the company failed to properly secure and protect patient data, breaching state and federal laws including the FTC Act and HIPAA.
- Exposed data included sensitive information such as Social Security numbers, bank details, medical records, and more, leading to potential harm for affected individuals.
- Plaintiffs seek damages and improved data protections as the legal battle unfolds, underscoring the importance of cybersecurity in healthcare and the consequences of data breaches.
Read Full Article
18 Likes
Dataprivacyandsecurityinsider
369

AI Service Provider Faces Class Actions Over Catholic Health Data Breach
- AI service provider Serviceaide Inc. is facing two proposed class action lawsuits over a data breach linked to Catholic Health System Inc. in Buffalo, New York.
- The breach exposed the personal information of over 480,000 individuals, including patients and employees.
- The lawsuits allege that Serviceaide negligently failed to protect sensitive data in its Elasticsearch database, which was publicly accessible for months before disclosure.
- Plaintiffs claim that Serviceaide delayed notifying affected individuals for seven months after the incident, seeking nationwide representation for those impacted and pursuing damages, injunctive relief, and attorneys' fees.
Read Full Article
22 Likes
Dataprivacyandsecurityinsider
63

Privacy Tip #444 – Best Phishing Campaigns are from HR or IT
- Phishing campaigns, including emails, SMS texts, and QR codes, continue to deceive people despite their belief in spotting them.
- A summary by KnowB4 reveals that HR or IT impersonation schemes are the most successful in phishing tests conducted between January and March 2025.
- Employees are highly susceptible to interacting with links related to internal team topics and various file types like PDFs, HTML, and .doc, along with falling for trusted brand impersonations.
- The summary also highlights the risk posed by QR code scams, such as those related to company policies, DocuSign requests, and seemingly innocent messages, urging caution while interacting with them.
Read Full Article
3 Likes
TechCrunch
118
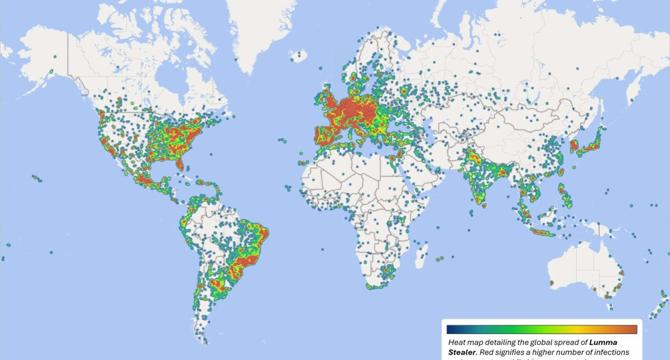
Image Credit: TechCrunch
Microsoft says Lumma password stealer malware found on 394,000 Windows PCs
- Microsoft and law enforcement conducted a court-authorized takedown of Lumma, an info-stealer malware operation found on over 394,000 Windows PCs worldwide, mainly in Brazil, Europe, and the United States.
- Civil action was taken by Microsoft to seize 2,300 domains serving as the malware's command and control servers, while the Justice Department seized five domains linked to the Lumma infrastructure.
- Lumma password stealer is typically hidden in illegitimate games or cracked applications downloaded online, stealing logins, passwords, credit cards, and cryptocurrency wallets to sell to other hackers. It can also provide a backdoor for further malware installation like ransomware.
- Such password-stealing malware, including Lumma, has been associated with cyberattacks targeting tech firms like PowerSchool and Snowflake, resulting in substantial data theft.
Read Full Article
7 Likes
Silicon
424
Image Credit: Silicon
EU Sanctions Entities, Individuals Amid Russian Hybrid Threats
- The European Union has implemented sanctions against individuals and entities engaged in Russian hybrid operations and destabilizing activities.
- 21 individuals, including politicians and military personnel, as well as six entities, such as fishing companies and news agencies, are now subject to EU restrictive measures and sanctions.
- The Council of the European Union has expanded the scope of sanctions to target tangible assets related to Russia's destabilizing activities, including vessels, aircraft, real estate, and digital communication networks.
- Sanctioned individuals and entities are accused of engaging in activities like undersea cable sabotage, media manipulation, spreading propaganda, and disrupting civil aviation.
Read Full Article
25 Likes
Medium
142
Image Credit: Medium
7 Cybersecurity Tips to Protect Your Data
- Cybersecurity involves protecting digital information like login details, files, and messages, as most data is now online.
- Basic habits and not complex tools are sufficient to stay safe from hackers who often exploit small mistakes made by individuals.
- Using different, long, and complex passwords with symbols and numbers for each account is recommended to enhance security.
- Regularly updating software, enabling automatic updates, and being cautious with emails to avoid phishing attacks are crucial steps in maintaining cybersecurity.
Read Full Article
8 Likes
Securityaffairs
433
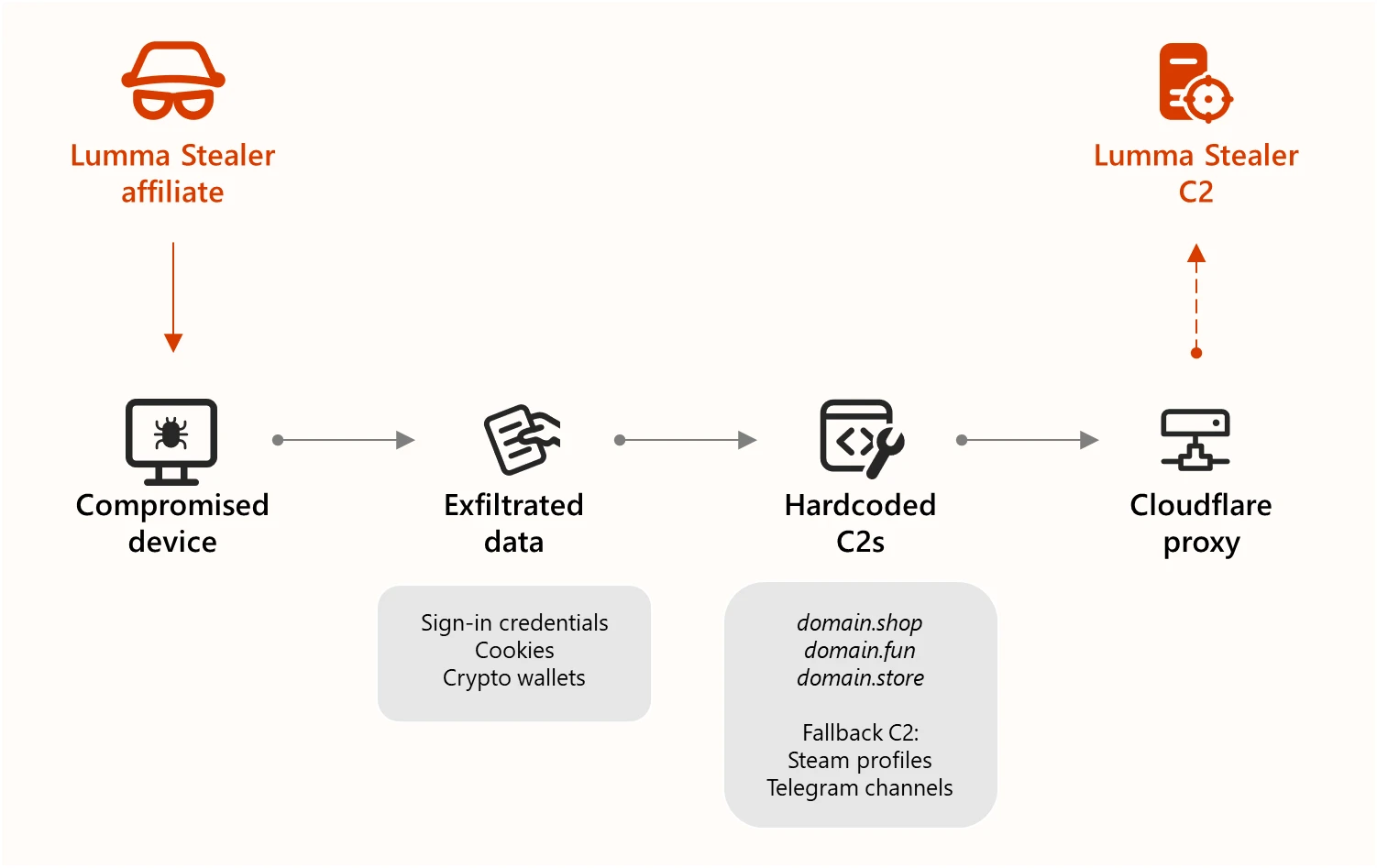
Image Credit: Securityaffairs
Law enforcement dismantled the infrastructure behind Lumma Stealer MaaS
- Law enforcement, with the help of Microsoft, Europol, and Japan’s JC3, dismantled the infrastructure behind Lumma Stealer Malware-as-a-Service (MaaS) operation, seizing 2,300 domains used for command-and-control.
- The malware, known as Lumma Stealer, targeted over 394,000 Windows systems, including those of global manufacturers, to steal sensitive data like passwords, credit card information, and crypto wallet keys.
- Microsoft's Digital Crimes Unit sinkholed over 1,300 domains used by Lumma Stealer to reroute victims to safe servers for analysis and cleanup, showcasing the collaboration between law enforcement and tech companies against cyber threats.
- The FBI and US CISA released a joint advisory containing tactics, techniques, and procedures associated with Lumma Stealer, along with indicators of compromise (IOCs), emphasizing the importance of public-private partnerships in combating cybercrime.
Read Full Article
26 Likes
Medium
78

Image Credit: Medium
Kashyap Divyansh – The 19-Year-Old Cybersecurity Visionary Behind GDG VAPT,
- Kashyap Divyansh, a 19-year-old cybersecurity researcher and developer, is making a mark through code, community, and vision at Silver Oak University.
- Recognizing the lack of cybersecurity awareness in Indian educational institutions, Kashyap founded DSCYBERS to provide real-world cybersecurity education and training.
- Kashyap developed GDG VAPT, an AI-powered open-source framework for web application security, combining AI automation with ethical hacking capabilities.
- Kashyap aims to empower students across India in cybersecurity and position India as a global cybersecurity powerhouse with his future projects.
Read Full Article
4 Likes
For uninterrupted reading, download the app