Cyber Crime News
TechCrunch
299

Image Credit: TechCrunch
Major US grocery distributor warns of disruption after cyberattack
- United Natural Foods (UNFI), a major distributor of groceries, was hit by a cyberattack, leading to disruptions in fulfilling and distributing customer orders.
- UNFI became aware of unauthorized access to its IT systems last Thursday, prompting the shutdown of parts of its network.
- The company is implementing workarounds to continue servicing customers, but the intrusion has caused ongoing disruptions in its business operations.
- The cyberattack at UNFI is the latest in a series affecting the retail and grocery supply chain, with no timeline provided for system recovery.
Read Full Article
18 Likes
Bitcoinist
375

Image Credit: Bitcoinist
Locked Out No More? Coinbase Cracks Down On Account Freezes
- Coinbase has reduced unnecessary account freezes by 82%, CEO Brian Armstrong announced.
- Dor Levi, a new team member, has played a significant role in stopping the freezing of good accounts.
- A data breach affecting over 70,000 accounts has raised concerns among users about the security of their information.
- Coinbase will continue to comply with legal restrictions on account freezes, and users are encouraged to contact support for details.
Read Full Article
22 Likes
Securityaffairs
299
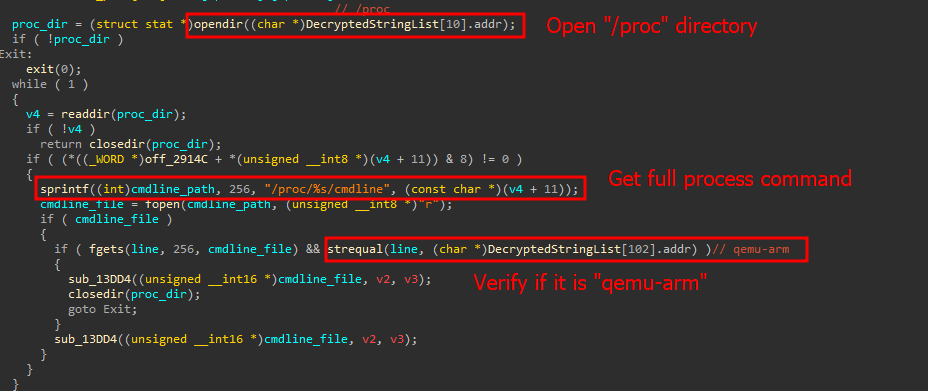
Image Credit: Securityaffairs
New Mirai botnet targets TBK DVRs by exploiting CVE-2024-3721
- A new variant of the Mirai botnet exploits CVE-2024-3721 to target DVR systems.
- The variant uses a command injection vulnerability in TBK DVR-4104 and DVR-4216 devices to execute malicious commands.
- This Mirai variant includes new features like RC4 string encryption and anti-virtual machine checks.
- Over 50,000 exposed DVRs have been found as potential targets in countries like China, India, Egypt, Ukraine, Russia, Turkey, and Brazil.
Read Full Article
18 Likes
Securityaffairs
0

Image Credit: Securityaffairs
BadBox 2.0 botnet infects millions of IoT devices worldwide, FBI warns
- BadBox 2.0 malware infects millions of IoT devices globally, forming a botnet for cyber criminal activities, as warned by the FBI.
- FBI issues a Public Service Announcement (PSA) highlighting the use of the BADBOX 2.0 botnet by cybercriminals to exploit IoT devices, predominantly made in China.
- The malware gains unauthorized access to devices, targeting Android devices and compromising home networks to become part of the BADBOX 2.0 botnet for illicit purposes.
- FBI advises checking IoT devices for compromise signs, disconnecting suspicious ones, monitoring network traffic, avoiding unofficial app stores, and promptly patching vulnerabilities to mitigate risks.
Read Full Article
Like
TechBullion
255

Image Credit: TechBullion
Strengthen Digital Access with Secure Identity Verification
- Secure Identity Verification is crucial for enhancing security measures in the digital world, protecting users' information and fostering trust in online interactions.
- Implementing secure identity verification shields businesses and individuals from fraud and cybercrime by verifying user authenticity.
- It ensures that only verified users can access platforms requiring financial transactions or personal data, reducing risks associated with unauthorized activities.
- Identity verification not only safeguards businesses but also gives users peace of mind, encouraging confident engagement in digital environments.
- Advanced technologies like biometric verification streamline the verification process, providing both security and convenience for users.
- Compliance with regulatory standards is facilitated by secure identity verification tools, demonstrating a commitment to data security and legal adherence.
- Identity verification fosters customer trust by prioritizing data security and fraud prevention, leading to increased loyalty and positive brand reputation.
- Operational value is derived from secure verification processes, allowing businesses to allocate fewer resources to manual verifications and fraud investigations.
- By reducing the risk of fraud and unauthorized access, businesses can redirect resources towards enhancing customer service and innovation.
- Secure identity verification is essential for ensuring the security and efficiency of online transactions, bolstering confidence in digital payment systems.
Read Full Article
15 Likes
Securityaffairs
232

Image Credit: Securityaffairs
Over 950K weekly downloads at risk in ongoing supply chain attack on Gluestack packages
- A supply chain attack targeted NPM, compromising 16 popular Gluestack 'react-native-aria' packages with over 950K weekly downloads.
- The attack involved injecting malicious code with Remote Access Trojan (RAT) capabilities into packages' files, affecting 16 out of 20 packages.
- Approximately 960,000 weekly downloads were affected by the compromised packages, and researchers believe the same threat actors were behind a previous attack on the 'rand-user-agent' package.
- Aikido Security attempted to notify Gluestack about the ongoing supply chain attack but has not received a response yet, urging users to stay updated on the situation.
Read Full Article
14 Likes
Securityaffairs
201

Image Credit: Securityaffairs
Security Affairs newsletter Round 527 by Pierluigi Paganini – INTERNATIONAL EDITION
- Security Affairs newsletter Round 527 by Pierluigi Paganini – INTERNATIONAL EDITION
- 4 billion Chinese user records leaked in the largest known data breach. Fortinet flaws exploited to deploy Qilin ransomware. Russia-linked threat actors target Ukraine with PathWiper wiper. U.S. offers $10M bounty for RedLine malware info.
- Multiple cyber attacks reported worldwide. U.S. seizes criminal marketplace domains. Ransomware gang claims responsibility for Kettering Health hack. Cyber criminals defraud Hedera Hashgraph network users. Malware exploits and vulnerabilities identified.
- Intelligence and Information Warfare updates include Ukraine hacking Tupolev and DOJ accusations against Chinese researchers. Cybersecurity incidents such as Victoria's Secret security breach and largest data leak of 4 billion user records.
- AI and cybersecurity advancements highlighted in EU initiative and increase in cyber attacks with AI involvement. Ongoing developments in digital certificate security and threat actor collaboration.
Read Full Article
12 Likes
Medium
90
Image Credit: Medium
When Deleted Isn’t Gone — Privacy Risks in Electronics Repair
- The electronics repair industry, valued at around $19 billion globally, lacks sufficient regulatory oversight on customer privacy, leading to data exploitation risks.
- Recent research indicates that repair technicians frequently access and even share customers' private data, such as personal photos and videos, despite it being unnecessary for the repair task.
- Customers' assumption of deleted files being permanently erased is debunked, as skilled technicians can easily recover such data due to the technical aspects of data storage.
- Various studies highlight a high incidence of privacy violations within the electronics repair sector, with a significant percentage of technicians found to snoop on data or copy it without consent.
Read Full Article
5 Likes
Securityaffairs
152

Image Credit: Securityaffairs
Experts found 4 billion user records online, the largest known leak of Chinese personal data from a single source
- Over 4 billion user records were found exposed online in a massive breach linked to the surveillance of Chinese citizens.
- Cybersecurity researchers discovered a 631GB unsecured database containing around 4 billion records, mainly involving Chinese users, potentially used for profiling and surveillance purposes.
- The leaked data included information from WeChat, Alipay, and other sources, posing serious risks of phishing, fraud, blackmail, and state-backed intelligence activities.
- This incident represents the largest known leak of Chinese personal data from a single source, with affected individuals having no clear way to respond.
Read Full Article
9 Likes
Medium
309

Phishing Attacks-The Digital Con Game You Need to Avoid
- Phishing attacks involve attackers pretending to be trusted entities to trick individuals into revealing sensitive information or installing malware.
- These attacks exploit human tendencies like trust or fear, and spotting them has become harder with AI-generated content making phishing emails more convincing.
- Common types of phishing attacks include spear phishing, vishing, and smishing, each targeting different vulnerabilities.
- To protect yourself, verify sources, use two-factor authentication, keep software updated, be cautious with links, educate yourself and others about phishing, use anti-phishing tools, and report suspicious messages.
Read Full Article
18 Likes
Livebitcoinnews
237

Image Credit: Livebitcoinnews
DOJ Seizes $7.74M Crypto Linked to North Korean IT Workers
- United States Department of Justice seizes $7.74 million in cryptocurrency linked to North Korean IT workers to avoid U.S. sanctions and support weapons programs.
- The scheme involved fake identities, NFTs, and chain hopping to launder money, with the complaint targeting assets linked to a North Korean Foreign Trade Bank representative.
- North Korean IT professionals used sophisticated tactics like token swapping and purchasing NFTs to hide finances, with assistance from FBI, State Department, and Treasury Department.
- The forfeiture is part of broader efforts to crack down on North Korea's cybercrime activities, with investigations ongoing to seize additional assets related to sanctions evasion.
Read Full Article
14 Likes
Bitcoinist
305

Image Credit: Bitcoinist
US Seeks Forfeiture of $7.7M in Crypto Linked to North Korean IT Workers
- The US Department of Justice has filed a civil forfeiture complaint to seize $7.74 million in cryptocurrency linked to North Korean IT workers.
- The funds were earned through employment at blockchain firms using falsified identities, aiming to evade US sanctions and send illicit gains back to North Korea.
- The scheme involved money laundering tactics such as using fake identities, chain hopping, token swapping, NFT purchases, and fund transmission through online US-based platforms.
- US agencies are focusing on disrupting illicit financing networks, targeting North Korea’s digital revenue streams to enforce sanctions and limit funds for military development.
Read Full Article
18 Likes
Securityaffairs
381
Image Credit: Securityaffairs
Attackers exploit Fortinet flaws to deploy Qilin ransomware
- Qilin ransomware is now exploiting Fortinet vulnerabilities, including CVE-2024-21762 and CVE-2024-55591, for remote code execution.
- The ransomware group has been active since August 2022 and gained attention in 2024 for attacking Synnovis, a UK healthcare service provider.
- Threat actors are actively exploiting Fortigate vulnerabilities to deploy Qilin ransomware, with the attack being fully automated.
- Despite initially targeting Spanish-speaking countries, experts warn that the Qilin ransomware group could expand globally and is capable of independent intrusion operations.
Read Full Article
22 Likes
Securityaffairs
224
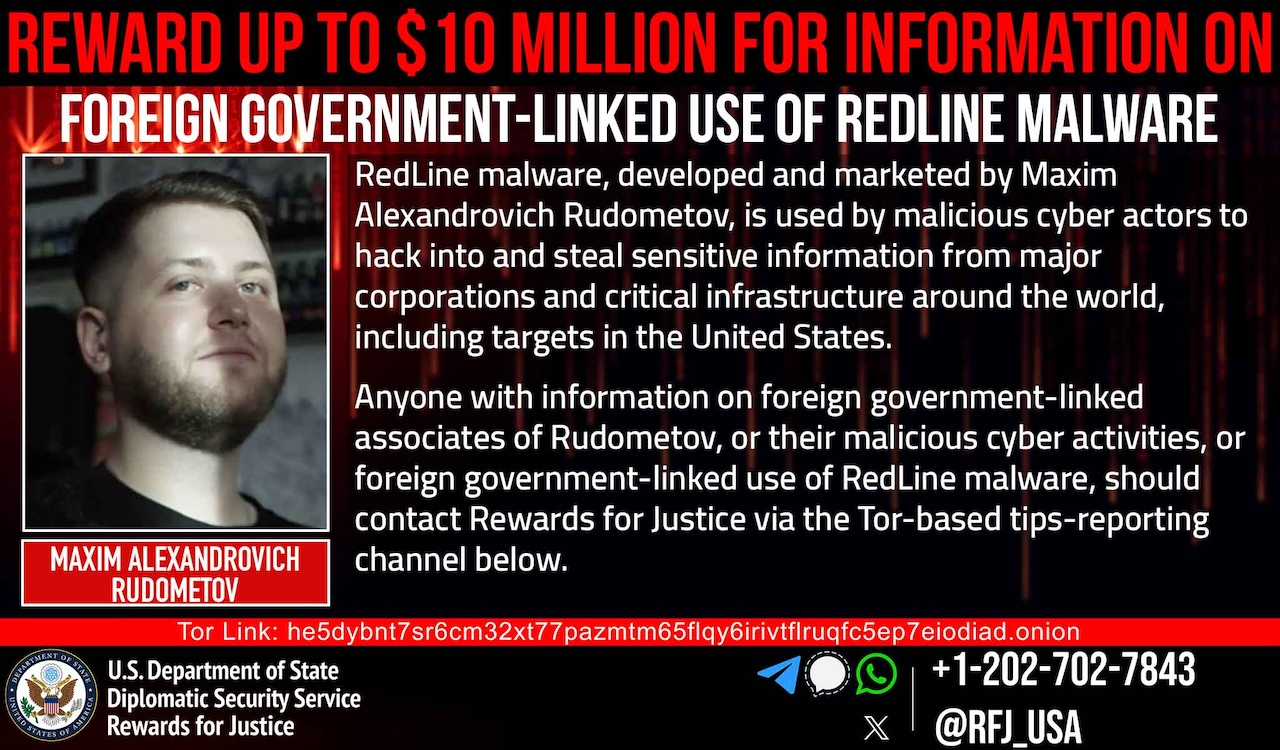
Image Credit: Securityaffairs
U.S. Offers $10M bounty for info on RedLine malware creator and state hackers
- The U.S. is offering up to $10 million for information on state hackers tied to the RedLine malware and its creator, Maxim Rudometov, associated with attacks on U.S. infrastructure.
- Maxim Rudometov, a Russian national, developed the information stealer malware RedLine and is being sought by U.S. authorities for cyber operations on critical infrastructure in the U.S.
- The reward is part of the US Department of State's Rewards for Justice program aiming to deter foreign government hackers targeting U.S. entities.
- An international operation led by Eurojust dismantled the RedLine and META malware infrastructure, affecting millions of victims worldwide and led to arrests in Belgium, seizure of servers in the Netherlands, and cooperation from multiple countries.
Read Full Article
13 Likes
Bitcoinist
300

Image Credit: Bitcoinist
US Seizes Crypto and 145 Domains in Major Darknet Takedown
- The US Department of Justice seized cryptocurrency assets and 145 internet domains linked to darknet marketplace BidenCash.
- BidenCash facilitated the sale of stolen credit card data and personal information to thousands of users, accumulating over 117,000 users and distributing more than 15 million compromised payment card numbers.
- Authorities seized cryptocurrency funds used by BidenCash and redirected the seized domains to law enforcement-controlled servers to prevent further illicit activities.
- The operation involved international collaboration with law enforcement bodies and marks a continuation of US efforts to dismantle cybercriminal infrastructure operating on the dark web.
Read Full Article
18 Likes
For uninterrupted reading, download the app