Cyber Crime News
Managedmethods
4

Image Credit: Managedmethods
AI in K-12 Cybersecurity: Hype or Helpful?
- AI-powered K-12 cybersecurity solutions are being marketed as the next frontier in data protection amidst rising threats like phishing and ransomware in schools.
- The education sector is highly targeted for cyberattacks, with 63% of lower education organizations hit by ransomware in the last year.
- AI in K-12 cybersecurity can help detect phishing attacks that traditional filters might miss and spot unusual behavior or patterns across user accounts.
- Automating response and remediation processes, reducing alert fatigue, and prioritizing threats are key benefits of AI in K-12 cybersecurity.
- AI is not a replacement for human expertise, user training, cyber hygiene, patching, backups, or multi-factor authentication, but it can complement these measures.
- Understanding the type of AI used in cybersecurity solutions and its integration capabilities is crucial for effective implementation.
- Smarter email protection tools, like Advanced Phishing, utilizing AI models can enhance cybersecurity in schools by understanding context and intent behind emails.
- AI-powered K-12 cybersecurity, when tailored and transparent, can significantly improve email security, save time, integrate seamlessly, and enhance overall cyber defense.
- Adopting targeted AI solutions that align with workflow and save time is advisable for enhancing K-12 cybersecurity measures.
- Exploring AI-powered K-12 cybersecurity solutions to strengthen email security and combat threats like phishing and ransomware is recommended for schools.
Read Full Article
Like
TechJuice
186

Image Credit: TechJuice
Katz Stealer Malware Targets Major Web Browsers, Crypto Wallets
- Katz Stealer malware is targeting popular web browsers like Google Chrome, Microsoft Edge, Brave, and Mozilla Firefox to steal sensitive data including login credentials and cryptocurrency wallet information.
- The malware uses a multi-stage infection method involving obfuscated JavaScript code, PowerShell scripts, and a .NET-based loader payload to evade detection and inject itself into legitimate processes.
- Katz Stealer employs evasion tactics like geofencing, virtual machine detection, and sandbox evasion to avoid detection, while also exploiting Windows tools to elevate its capabilities without user intervention.
- The malware can exfiltrate data from various applications and platforms such as cryptocurrency wallets, communication platforms, email clients, gaming platforms, VPN setups, and FTP clients, showcasing its versatility and extensive threat scope.
Read Full Article
11 Likes
Securityaffairs
381
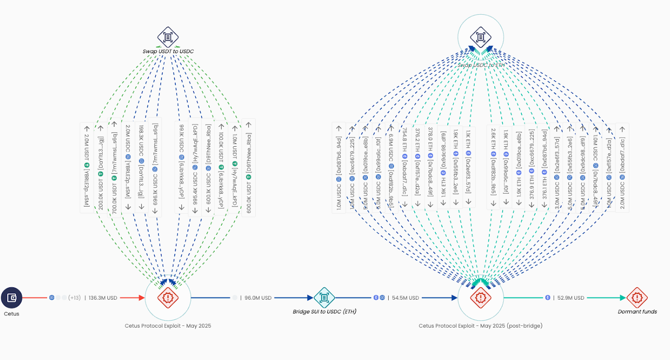
Image Credit: Securityaffairs
Crooks stole over $200 million from crypto exchange Cetus Protocol
- Cetus Protocol suffered a $223 million crypto theft and is willing to drop legal action if the stolen funds are returned.
- The platform was paused as the investigation confirmed the cyber heist last week.
- $162 million of the compromised funds have been successfully paused, and recovery efforts are underway with the Sui Foundation.
- The hack was due to a vulnerable package but has since been fixed, with the company offering a $5 million bounty for tips to identify the attacker.
Read Full Article
22 Likes
Securityaffairs
231
Image Credit: Securityaffairs
Marlboro-Chesterfield Pathology data breach impacted 235,911 individuals
- SafePay ransomware attacked Marlboro-Chesterfield Pathology, compromising personal data of 235,000 individuals.
- The breach occurred on January 16, 2025, leading to the unauthorized access of internal systems.
- Stolen information included names, addresses, birth dates, medical treatment details, and health insurance data.
- Marlboro-Chesterfield Pathology notified the US Department of Health and Human Services about the breach affecting 235,911 people.
Read Full Article
13 Likes
Kaspersky
440
Image Credit: Kaspersky
How scammers exploit genuine Microsoft business notifications
- Scammers are exploiting genuine Microsoft business notifications to send phishing emails to potential victims.
- Cybercriminals insert custom text into legitimate thank-you messages from Microsoft to trick recipients.
- The scammers replace billing information in the emails with their phone numbers, prompting victims to call for 'assistance.'
- Victims who call the provided phone number may be tricked into installing malware, highlighting the need for employee training and robust security measures.
Read Full Article
26 Likes
Silicon
59

Image Credit: Silicon
UK, US Police Target Ransomware Gangs In Latest Action
- Law enforcement authorities in the UK, the US, and five other countries collaborated in a Europol-coordinated action targeting ransomware gangs.
- The action resulted in the takedown of 300 servers, seizure of 650 internet domains, and 3.5 million euros in cryptocurrency.
- Notorious malware strains like Trickbot and Danabot were neutralized, along with other malware such as Bumblebee, Lactrodectus, Qakbot, Hijackloader, and Warmcookie.
- Authorities issued international arrest warrants against 20 key actors providing or operating initial access services to ransomware gangs, with many suspects being Russian citizens or Russian-language speakers.
Read Full Article
3 Likes
Securityaffairs
231
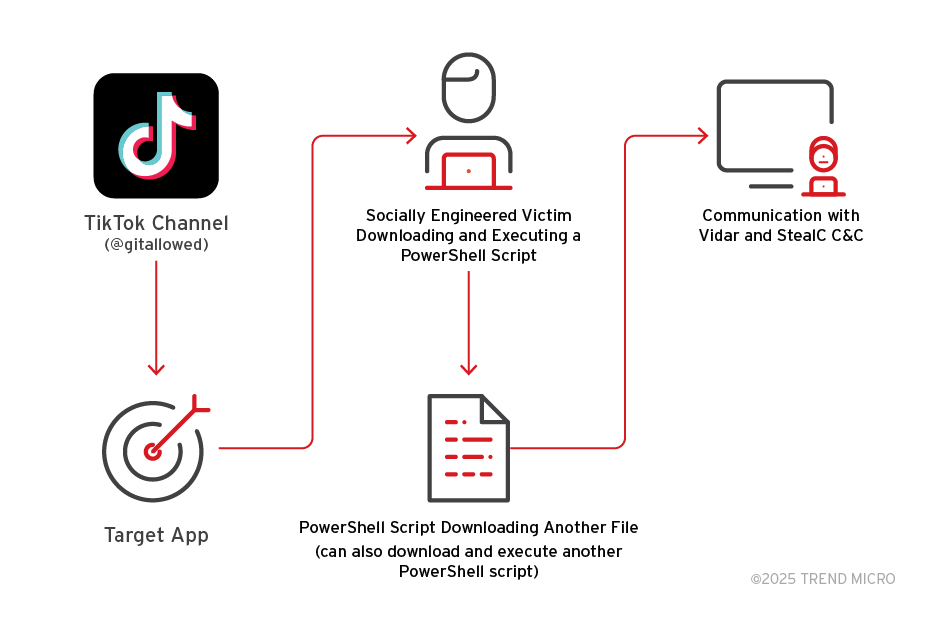
Image Credit: Securityaffairs
Fake software activation videos on TikTok spread Vidar, StealC
- Cybercriminals are using AI-generated TikTok videos to spread Vidar and StealC malware in ClickFix attacks.
- The videos trick users into executing PowerShell commands disguised as software activation steps, reaching over 500,000 views.
- Malware-laden TikTok videos provide step-by-step instructions to download Vidar or StealC malware, connecting to command-and-control servers after infection.
- Traditional security controls focusing on malicious code detection are less effective against social media-based malware distribution, highlighting the need for a more holistic defense approach.
Read Full Article
13 Likes
Silicon
413
Image Credit: Silicon
Police Probe Hacking Gang Over Retail Attacks
- British authorities are investigating hacking group Scattered Spider for recent hacks on UK retailers, including Marks & Spencer's systems breached via a third-party contractor, likely India-based TCS.
- Scattered Spider, a group of mainly English-speaking individuals in the UK and US, is known for using social engineering techniques like tricking IT help desks into clicking on links or resetting accounts.
- Investigations by the National Crime Agency suggest Scattered Spider may be involved, with past hacks on casinos and Transport for London connected to the group. TCS is internally probing its involvement in the M&S hack.
- Several arrests related to Scattered Spider have been made, including UK citizen Tyler Buchanan and others in the US and the UK. The group has worked with various hacking groups and faces charges of theft and disruption.
Read Full Article
24 Likes
Medium
172
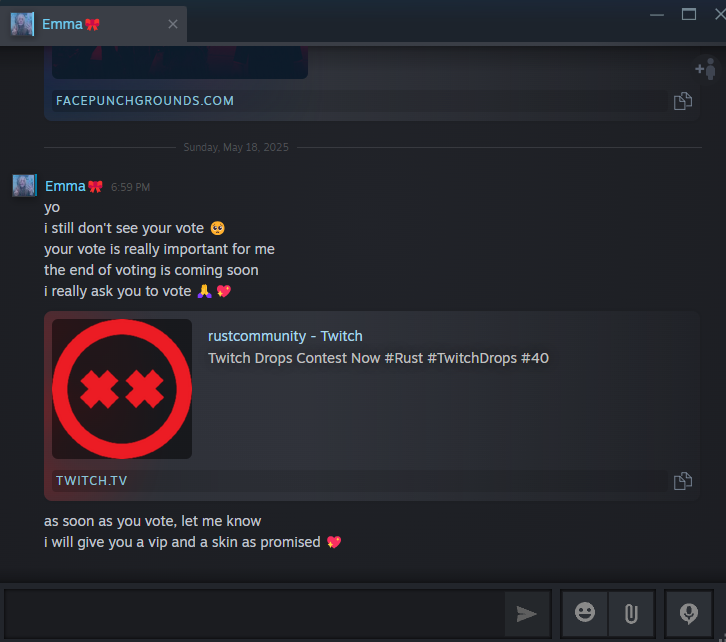
Image Credit: Medium
Twitch Bait and Switch: How I Uncovered a Steam Phishing Operation
- A researcher uncovered a phishing campaign targeting gamers through Twitch, a fake Facepunch-branded site, and a Telegram bot.
- Upon clicking 'Vote Now' on the site, redirection to a newly registered domain with Facepunch branding occurred.
- The phishing site contained obfuscated JavaScript controlling redirection logic, potentially compromising Steam sessions without needing user credentials.
- The researcher was able to capture and monitor the attacker's bot traffic in real time, exposing ongoing phishing attempts.
Read Full Article
10 Likes
Securityaffairs
50

Image Credit: Securityaffairs
Security Affairs newsletter Round 525 by Pierluigi Paganini – INTERNATIONAL EDITION
- Silent Ransom Group targeting law firms, FBI warns.
- Leader of Qakbot cybercrime network indicted in U.S. crackdown.
- Operation RapTor results in arrest of 270 dark web vendors and buyers.
- Chinese threat actors exploit Trimble Cityworks flaw to breach U.S. local government networks.
Read Full Article
3 Likes
Securityaffairs
350

Image Credit: Securityaffairs
Operation ENDGAME disrupted global ransomware infrastructure
- Operation ENDGAME coordinated by Europol and Eurojust dismantled global ransomware infrastructure from May 19 to 22, taking down 300 servers, 650 domains, and seizing €21.2M in crypto.
- Law enforcement efforts included Europol setting up a Command Post in The Hague with investigators from various countries, leveraging Eurojust's support for effective judicial cooperation.
- Authorities also seized €3.5M in cryptocurrency, targeting initial access malware strains like Bumblebee, Lactrodectus, Qakbot, and issuing 20 international arrest warrants for key operators.
- Germany will list 18 suspects on the EU Most Wanted list, accused of providing tools for ransomware attacks, showcasing law enforcement's adaptability in disrupting ransomware services.
Read Full Article
21 Likes
TechJuice
59

Image Credit: TechJuice
Massive Data Leak Exposes Login Details of 184 Million Netizens
- Security researcher Jeremiah Fowler discovered a massive data leak in May 2025, totaling over 47 GB of data, with no identifiable metadata.
- The leaked data included plaintext usernames and passwords, indicating potential use by cybercriminals or researchers employing infostealing malware.
- Analysis of a sample of 10,000 records revealed compromised accounts from major platforms like Facebook, Google, Instagram, Roblox, Discord, Microsoft, Netflix, PayPal, and others.
- Containing email addresses with .gov domains from 29 countries, the leak poses significant national security risks, prompting swift action by the World Host Group to take the database offline.
Read Full Article
3 Likes
Securityaffairs
63

Image Credit: Securityaffairs
Silent Ransom Group targeting law firms, the FBI warns
- The FBI warns that the Silent Ransom Group, also known as Luna Moth, has been targeting U.S. law firms for 2 years using callback phishing and social engineering tactics.
- The group gains remote access to systems and steals sensitive data to extort victims. They have previously enabled Ryuk and Conti ransomware attacks through BazarCall campaigns.
- SRG started posing as IT staff in phone calls since March 2025, tricking employees into granting remote access and exfiltrating data without needing admin privileges.
- After stealing data, SRG extorts victims with ransom emails and pressures employees into negotiations. They operate a data leak site but do not always follow through on threats to publish the data.
Read Full Article
3 Likes
TechDigest
161

Image Credit: TechDigest
Russian-led cybercrime network dismantled, India’s TCS potential link to M&S cyber-attack
- European and North American cybercrime investigators have dismantled a malware operation directed by Russian criminals, resulting in the issuance of international arrest warrants for 20 suspects.
- The mother of a 14-year-old boy who took his own life after becoming obsessed with AI chatbots can continue her legal case against the company behind the technology, signaling accountability for real-world harm caused by AI products.
- Indian IT firm TCS is investigating its potential role as the gateway for the cyber-attack on Marks & Spencer, as M&S reported hackers gaining access via a third party working with them.
- Samsung's upcoming Galaxy S25 Edge boasts a bleeding-edge design with a lightweight and thin build, a high-quality display, and Qualcomm's latest Snapdragon 8 Elite chipset.
Read Full Article
6 Likes
Securityaffairs
314

Image Credit: Securityaffairs
Leader of Qakbot cybercrime network indicted in U.S. crackdown
- U.S. authorities indicted Russian national Rustam Gallyamov for leading the Qakbot botnet, which infected over 700,000 computers and facilitated ransomware attacks.
- Qakbot, also known as QBot, is an info-stealing malware active since 2008, spread via malspam campaigns, and has been used by major ransomware gangs.
- The U.S. Justice Department filed a civil forfeiture complaint to seize over $24 million in cryptocurrency from Gallyamov as part of a multinational cybercrime crackdown.
- The FBI performed a sinkholing of the Qakbot botnet, identified over 700,000 infected computers, and seized illicit proceeds worth over $24 million, despite Gallyamov continuing attacks till January 2025.
Read Full Article
18 Likes
For uninterrupted reading, download the app