Cyber Security News
Lastwatchdog
0

RSAC Fireside Chat: Enterprise browsers arise to align security with the modern flow of work
- The browser has become the new operating system of business in the enterprise workspace security landscape.
- As SaaS, remote work, and generative AI have become prevalent, the browser has taken on a central role in accessing cloud data and interacting with AI agents.
- Endpoint tools struggle to monitor browser sessions, traditional file systems are fading, and network perimeter defenses are becoming less relevant.
- Different strategies are emerging to address this shift, with some creating new enterprise browsers while others focus on enhancing existing browsers with cloud-based security solutions.
Read Full Article
Like
Cybersecurity-Insiders
173

Image Credit: Cybersecurity-Insiders
Catfishing via ChatGPT: A Deep Cybersecurity Concern
- The advancement of AI and natural language processing has led to ChatGPT, which can create human-like responses, raising cybersecurity concerns.
- Catfishing involving fake personas for deception has evolved with AI tools like ChatGPT, enabling automated manipulation.
- ChatGPT's ability to mimic human conversations facilitates scalable, automated catfishing operations across various platforms.
- AI-driven catfishing poses challenges due to scalability, realism in interactions, psychological manipulation, exploitation of personal data, and detection difficulties.
- Real-world examples show AI's role in creating fake profiles, engaging victims emotionally, and leading to financial exploitation.
- Combatting AI-powered catfishing requires awareness, education, enhanced detection tools, regulations, and leveraging AI for good purposes.
- Individual vigilance, along with collaborative efforts between stakeholders, is essential to mitigate the risks associated with AI-driven deception.
- As AI technologies advance, ensuring ethical and responsible use is crucial in preventing sophisticated scams like catfishing via ChatGPT.
- It is imperative for users to understand the potential risks of AI-driven deception to protect against digital manipulation and exploitation.
- Staying informed and proactive is key in combating emerging threats in cybersecurity, highlighting the need for collective efforts in safeguarding online interactions.
Read Full Article
10 Likes
Cybersecurity-Insiders
191

Image Credit: Cybersecurity-Insiders
Google Warns Users About Phishing Scam Targeting 2 Billion Active Accounts
- Google has issued a security alert regarding a phishing scam targeting its 2 billion active accounts.
- Fraudulent emails from '[email protected]' claim data compromise to steal personal information.
- Recipients are urged to click on links leading to fake government actions threatening data inspection.
- Google emphasizes it never requests sensitive data like passwords or OTPs via email.
- Phishing links direct users to malicious sites harvesting login details and financial information.
- Scammers use Gmail to distribute malicious content, posing a new level of deception.
- Google advises users to report phishing attempts, keep devices updated, and use anti-malware solutions.
- Staying cautious and informed is crucial in staying safe from evolving cyber threats.
- The incident highlights the need for enhanced security measures to combat phishing scams.
- Vigilance and cybersecurity practices are key to protecting personal data in the digital age.
Read Full Article
11 Likes
Cybersecurity-Insiders
118

Image Credit: Cybersecurity-Insiders
The Cybersecurity Gap Is No Longer Talent—It’s Tempo
- Security researcher Matt Keeley used GPT-4 to generate a working exploit for a critical vulnerability in just a few hours after its disclosure.
- The rapid advancement of artificial intelligence has shifted exploit development from elite craftsmanship to prompt engineering, making the threat landscape flatter.
- Adversaries are now moving 47 times faster than human operators due to AI streamlining every step of the offensive kill chain.
- Organizations need to prioritize real-life attack paths, intelligently assess risks, and continuously validate fixes to combat AI-powered attacks in the new cybersecurity reality.
Read Full Article
7 Likes
Cybersecurity-Insiders
173

Image Credit: Cybersecurity-Insiders
It’s Time to Move Away from the “Phonebook” Approach to Cybersecurity
- Traditional cybersecurity methods are facing limitations due to the evolving digital landscape, leading to increased vulnerabilities and risks.
- The reliance on relational data models resembles a static 'phonebook' approach, which fails to capture the dynamic nature of modern cyber threats.
- Attackers exploit real-world connections and relationships, not just static lists, making social engineering highly effective in breaching systems.
- Traditional cybersecurity approaches based on relational databases are computationally expensive and slow when dealing with complex cyberattacks.
- Graph-based cybersecurity solutions are gaining popularity for modeling relationships and information more effectively to enhance defense mechanisms.
- Graph technology enables faster response times by eliminating complex queries and providing a clearer understanding of network relationships.
- By leveraging machine learning and AI in conjunction with graph technology, organizations can bolster cybersecurity defenses while laying the groundwork for future advancements.
- Adopting adaptive cybersecurity strategies is crucial for staying ahead of cyber threats and improving defense capabilities against sophisticated attacks.
- Graph databases offer a powerful way to navigate and understand the intricate relationships within cybersecurity landscapes, ensuring better protection for organizations.
- Enhanced cybersecurity measures are essential to counter the growing cyber threat landscape and prevent adversaries from exploiting vulnerabilities more effectively.
Read Full Article
10 Likes
Securityaffairs
452

Image Credit: Securityaffairs
SK Telecom revealed that malware breach began in 2022
- SK Telecom revealed that the security breach disclosed in April began in 2022.
- SK Telecom, South Korea's largest wireless telecom company, detected a malware attack in April affecting 27 million users.
- The breach exposed data like phone numbers, IMSIs, SIM keys, and HSS-stored info of users.
- Investigations found that the breach began in 2022, went undetected for nearly three years, and involved 25 malware types across 23 servers.
Read Full Article
27 Likes
Medium
315

Image Credit: Medium
When pixels lie: how Deepfakes are haunting teen life
- Deepfakes have evolved from a distant sci-fi threat to a concerning reality in high schools, where AI-generated media is causing chaos among teenagers.
- Popular tools like FaceMagic and Zao provide teens with easy access to face-swapping, voice-cloning, and video manipulation capabilities.
- Teenagers now have the power to create realistic deepfakes that can easily damage someone's reputation or cause emotional harm.
- The widespread accessibility of deepfake technology has shifted it from harmless theory to a weapon for humiliation and deception.
- Platforms like YouTube and TikTok contribute to the spread of deepfakes by boosting content that garners clicks, leading to ethical concerns.
- Legislation around deepfakes is still in its early stages, with some states having laws focusing on specific aspects like nudity or politics.
- Victims of deepfakes, especially teens and women, report severe emotional trauma comparable to real-life harassment and bullying.
- Efforts to combat deepfake misuse include promoting media literacy, implementing safeguards in tools, and seeking legal recourse when necessary.
- Schools can play a crucial role in educating students about the risks and ethical considerations surrounding deepfake technology.
- Ethical developers are called upon to enhance tools with features like watermarking and consent-based inputs to mitigate potential harm.
- Deepfakes have the potential to amplify storytelling and creativity when used transparently, but misuse in low-stakes environments can have detrimental effects.
Read Full Article
18 Likes
Medium
86

Securing Agentic AI Systems: New Challenges in Autonomous Decision-Making
- Agentic AI systems are autonomous actors capable of setting goals, planning actions, interacting with tools and APIs, storing memory, and adapting based on feedback.
- Security risks associated with Agentic AI systems arise from autonomous loops leading to unintended consequences, memory as a potential attack vector, and tool access/API abuse.
- To enhance security for Agentic AI systems, actionable best practices are recommended, including implementing guardrails, following zero-trust principles, securing memory, ensuring observability and auditing, and conducting adversarial agent testing.
- The AI security community is urged to collaborate on developing frameworks, threat models, testing tools, and observability tools to ensure the safety of autonomous AI systems.
Read Full Article
5 Likes
Fintechnews
63
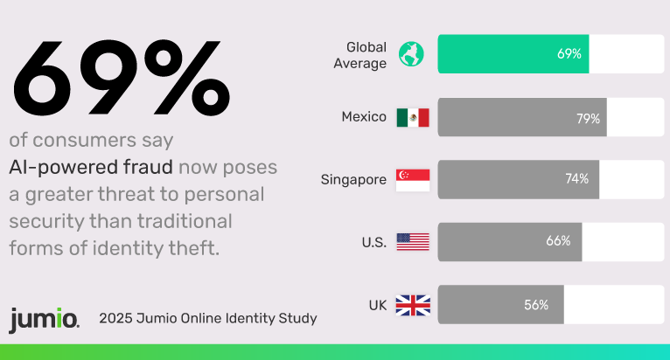
Image Credit: Fintechnews
Singaporeans More Concerned About AI-Powered Fraud Than Global Average
- A recent study by Jumio indicates a decline in consumer trust in the digital world, driven by AI-powered fraud and deepfakes.
- Globally, 69% of respondents believe AI-enabled fraud poses a greater threat to personal safety than traditional identity theft.
- In Singapore, 74% of respondents consider AI scams a bigger risk, and 71% find them harder to detect than conventional methods.
- There is a growing unease about the authenticity of online content and personal security, with consumers looking towards Big Tech for prevention and willing to spend more time on identity verification.
Read Full Article
3 Likes
Dev
319

Image Credit: Dev
AI is Quietly Changing Everything. Are you Keeping Up?
- AI is significantly impacting various sectors, including research, logistics, production, and internet search, prompting companies to innovate or risk falling behind.
- Google is leveraging AI to revolutionize web search, while AI is increasingly involved in software development and audit processes, potentially changing the future of coding.
- Companies like Nvidia are introducing AI-powered robots that can revolutionize operations in factories, hospitals, and cities, signaling a major technological shift.
- The rapid advancements in AI suggest an imminent intelligence explosion that could accelerate progress exponentially in the coming years, urging enterprises to adapt and innovate to stay competitive.
Read Full Article
19 Likes
Dev
0

Image Credit: Dev
Understanding Docker Security Basics: Building a Strong Foundation
- Docker simplifies application deployment and accelerates development cycles through containerization.
- Understanding Docker security is crucial to prevent vulnerabilities and data breaches.
- Containers share the host OS kernel, presenting unique security challenges.
- Isolating processes and managing resources with namespaces and control groups are core Docker security features.
- Implementing the principle of least privilege is essential for container security.
- Using minimal and trusted base images, scanning for vulnerabilities, and employing multi-stage builds enhance image security.
- Network segmentation, firewall rules, and encryption are key for network security in Docker.
- Advanced runtime security features like Seccomp, AppArmor, and SELinux minimize risks.
- Monitoring, logging, and updating Docker components regularly are vital for a strong security posture.
- Mastering secure orchestration, secret management, image signing, and incident response planning enhances Docker security.
Read Full Article
Like
Microsoft
301

Image Credit: Microsoft
One Pipeline to Rule Them All: Ensuring CodeQL Scanning Results and Dependency Scanning Results Go to the Intended Repository
- In the world of code scanning and dependency scanning, ensuring CodeQL scanning results and Dependency Scanning results go to the correct repository is crucial.
- Improper configuration may lead to results getting published to the wrong repository, causing chaos.
- To address this issue, utilizing inferred publishing is recommended to automatically detect the repository based on the current working directory.
- Using inferred publishing helps ensure that scan results go to the intended repository, preventing misplacements.
- When using inferred publishing, errors may occur in multi-repo scenarios due to ambiguity in determining the valid Git repository.
- To handle errors, setting 'workspaceRepo: true' can explicitly identify the correct repository for analysis and publication.
- The configuration provided in the guide is applicable not only to CodeQL static analysis but also to Dependency Scanning.
- It is crucial to ensure that Dependency Scanning results are also directed to the intended repository by configuring the pipeline appropriately.
- By adopting inferred publishing and best practices, developers can efficiently manage their code scanning workflows and enhance security measures.
- Configuring the pipeline correctly using inferred publishing can significantly impact the team's security workflows and overall code scanning efficiency.
Read Full Article
18 Likes
Siliconangle
438

Image Credit: Siliconangle
Atera debuts IT Autopilot to offload Tier 1 tasks from technicians
- Atera Networks Ltd. has launched IT Autopilot, an autonomous IT solution that builds upon the success of AI Copilot to resolve Tier 1 support tickets, automating tasks like password resets and system reboots.
- IT Autopilot can handle up to 40% of IT workloads with fast response times of 0.1 seconds and average resolution times of 15 minutes, allowing IT teams to focus on strategic initiatives.
- A survey revealed that 85% of respondents believed a four-day work week would be achievable if Tier 1 support responsibilities were automated, showing the need to address technician burnout and improve service levels.
- Atera positions IT Autopilot as a secure extension of internal IT teams, offering features like hands-free issue resolution, reduced end-user friction, and faster ticket turnaround times to enhance productivity and efficiency.
Read Full Article
26 Likes
Siliconangle
63

Image Credit: Siliconangle
Palo Alto Networks stock slips despite earnings and guidance beats
- Shares in Palo Alto Networks Inc. fell over 3% in late trading despite the company reporting beats in its fiscal Q3 earnings and giving better-than-expected earnings guidance.
- For the quarter ending on April 30, Palo Alto Networks posted adjusted earnings per share of 80 cents, up from 66 cents in the previous year, with revenue of $2.29 billion, a 15% increase year-over-year.
- The company's strong performance was fueled by growth in Next-Generation Security, leading to NGS annual recurring revenue of $5.09 billion and an operating income increase of 23%.
- Palo Alto Networks also announced acquisitions, including Protect AI Inc., and introduced new platforms like Cortex Cloud and enhancements like Cortex XSIAM to strengthen its AI-driven security operations.
Read Full Article
3 Likes
Dev
123

Image Credit: Dev
Specter-AAL
- Specter-AAL is a C-based Arithmetic Abstraction Layer (AAL) that utilizes elementary arithmetic operations to challenge modern cryptographic assumptions.
- Key features of Specter-AAL include being written in pure C, custom modular arithmetic logic, educational insights, and showcasing cryptographic implications.
- Ideal for cryptographic research, embedded & IoT devices, and academic use, Specter-AAL demonstrates how simple arithmetic can pose a threat to RSA implementations.
- Specter-AAL serves as a research tool and a philosophical challenge, questioning whether simplicity can outperform complexity and if elementary operations can become a hidden threat.
Read Full Article
7 Likes
For uninterrupted reading, download the app