Cyber Security News
Dev
187

Image Credit: Dev
Simple Gas Optimization Techniques Every Ethereum Developer Should Know
- Gas optimization is crucial for Ethereum developers to reduce costs and improve efficiency.
- Using uint256 consistently, packing storage variables, and utilizing constants and immutables can help save gas.
- Avoiding loops over dynamic arrays, short-circuiting conditionals, and calculating instead of storing data are other gas-saving techniques.
- Utilizing custom errors instead of require('string') and cleaning up unused storage are also recommended for efficient gas usage.
Read Full Article
11 Likes
Dev
134

Image Credit: Dev
Enterprise Software Development: Shaping the Future of Technology
- Enterprise software development is undergoing a transformation with a focus on faster innovation, scalability, and security driven by automation, AI, cloud computing, and DevOps.
- Key trends include AI/ML integration, DevOps and SRE practices, cloud-native architectures, automation, low-code platforms, and the DevSecOps approach for security.
- The future of enterprise software development includes predictive analytics, AI-powered DevOps, edge computing, sustainable development, and hyperautomation.
- To stay competitive, organizations should leverage modern technologies like AI, DevOps, cloud-native architectures, and DevSecOps to build intelligent, scalable, and secure software.
Read Full Article
2 Likes
Tech Radar
68

Image Credit: Tech Radar
Microsoft secures the modern workforce against AI agents
- Microsoft introduced Entra Agent ID, a new identity management tool for AI agents.
- The Entra Agent ID is based on the Zero Trust security model and provides unique, secure digital identities to AI agents.
- Microsoft aims to facilitate collaboration between humans and AI agents in the future, emphasizing the need for security in this partnership.
- The Entra Agent ID integrates with platforms like ServiceNow and Workday, enhancing data security and compliance control for AI applications.
Read Full Article
4 Likes
Hackernoon
105

Image Credit: Hackernoon
Contractor Backdoor: Coinbase Faces $400M Blow in Major Data Breach
- Coinbase faces a $400 million bill due to a cyber attack by compromised overseas contractors, exposing sensitive customer information.
- The breach did not compromise passwords and private keys, but personal data leakage raises concerns regarding trust and anonymity in the industry.
- Coinbase refused to pay a $20 million ransom, emphasizing a firm position against cyber-extortion.
- The cybercriminals recruited rogue overseas support agents to steal customer data, highlighting vulnerabilities in the supply chain and prompting Coinbase to establish a U.S.-based customer support hub.
Read Full Article
6 Likes
Silicon
192
Image Credit: Silicon
Court Rules Delta Can Pursue CrowdStrike Over Mass Outage
- Delta Airlines can pursue claims against CrowdStrike in a lawsuit over a Windows outage last summer.
- A judge ruled that Delta can proceed with claims of gross negligence against CrowdStrike for a faulty software update.
- CrowdStrike is confident that the case will have no merit or damages will be limited to low millions of dollars under Georgia law.
- The worldwide outage caused by CrowdStrike's faulty update disrupted operations for many organizations, including causing Delta up to $500 million in costs.
Read Full Article
11 Likes
Wired
242

Image Credit: Wired
What to Expect When You’re Convicted
- The article discusses the prevalence of white-collar crimes in the tech industry, highlighting various criminal activities ranging from fraud to deepfakes and scams.
- A former inmate turned prison consultant shares insights on manipulating people in prison and helping offenders reduce their time through legal strategies.
- The consultant assists white-collar offenders, offering services to prepare them for incarceration and navigate the legal process effectively.
- He engages in activities like securing resentencing for over-sentenced individuals and ensures his clients understand their charges and legal options.
- By charging varying fees based on clients' circumstances, he provides a range of services including explaining laws, trial strategies, and even beating polygraph tests.
- He educates clients on prison life, the types of institutions, and political dynamics within prisons to help them adapt and survive during incarceration.
- Offering emotional support to clients and their families, the consultant plays a crucial role in preparing individuals for the challenges they will face in prison.
- While his tough-love approach and blunt communication style may unsettle some clients, he aims to provide practical guidance and psychological peace of mind.
- The consultant's unique blend of roles includes counselor, psychologist, life coach, and priest, reflecting the comprehensive support he offers to clients.
- Despite his brash demeanor, the consultant's experience and expertise are instrumental in guiding offenders through the complexities of the legal and prison systems.
Read Full Article
14 Likes
TechDigest
389

Image Credit: TechDigest
Over 50% of top oil & gas firms hit by data breaches in last 30 days
- Over 50% of the world's top oil and gas companies experienced data breaches in the last 30 days, as per Cybernews analysis.
- 94% of the largest oil and gas firms have faced at least one data breach, with 69% receiving a cybersecurity score of D or F.
- Issues like ransomware attacks and offline systems are common in breaches, impacting critical operations in the industry.
- Challenges include credential hygiene, email security vulnerabilities, insecure server configurations, SSL/TLS issues, and corporate credential theft.
Read Full Article
23 Likes
Securityaffairs
150

Image Credit: Securityaffairs
UK’s Legal Aid Agency discloses a data breach following April cyber attack
- The UK's Legal Aid Agency suffered a cyberattack in April, leading to a data breach where sensitive information of legal aid applicants was stolen.
- The cyberattack on the Legal Aid Agency, part of the UK Ministry of Justice, compromised personal data dating back to 2010, including contact details, national ID numbers, and financial information.
- The agency worked with authorities like the National Crime Agency and National Cyber Security Centre to investigate the breach and discovered that hackers accessed and downloaded significant amounts of personal data.
- In response to the breach, the Legal Aid Agency took down its online service, implemented security measures, and assured continued access to legal support for those in need.
Read Full Article
9 Likes
Vista InfoSec
233

Top 10 Influencers to Follow In Cybersecurity 2025
- Cybersecurity influencers play a crucial role in shaping the conversation around digital threats and risk management.
- Among the top influencers to follow in cybersecurity in 2025 are individuals like Robert Herjavec, known for blending boardroom strategy with cyber defense.
- Gary Hayslip, with diverse experience, offers practical CISO advice without technical jargon.
- Matthew Rosenquist simplifies complex cyber threats into actionable strategies, making cyber trends easy to understand.
- Brian Krebs is a prominent investigative cybersecurity journalist known for his coverage of critical breach news.
- Chuck Brooks provides insights on public-private partnerships and innovation at scale in cybersecurity and government tech policy.
- Naomi Buckwalter offers valuable advice on diversifying and growing the cyber talent pool, especially for newcomers and leaders.
- Helen Yu advocates for risk-aware leadership and smarter exposure management, communicating cyber issues effectively to executives.
- Christophe Foulon provides career development tips for breaking into cybersecurity and advancing in the field.
- Troy Hunt focuses on breach data analysis and identity security, offering practical insights and guidance in the cybersecurity realm.
Read Full Article
14 Likes
Insider
182

Image Credit: Insider
Meet the Yale student and hacker moonlighting as a cybersecurity watchdog
- Yale student Alex Schapiro, a rising senior, uncovers security flaws in tech companies and startups as an ethical hacker.
- He identified a vulnerability in the dating app Cerca that could expose user data, prompting the app to resolve the issue swiftly.
- Schapiro's expertise in ethical hacking has led to improvements in security measures for various companies, including those with significant revenues.
- His work highlights the importance of ethical bug hunting in safeguarding sensitive data as startups rapidly scale and attract investment.
- Schapiro's background in programming, inherited from his computer scientist mother, has driven his passion for uncovering and addressing cybersecurity flaws.
- He has contributed to enhancing security for companies by identifying vulnerabilities and assisting them in implementing bug bounty programs.
- Despite opportunities to found a tech startup, Schapiro prioritizes his liberal arts college experience and personal growth over immediate entrepreneurship.
- Schapiro's dedication to ethical hacking and cybersecurity, combined with his academic pursuits and industry internships, shapes his approach to building a safer digital ecosystem.
- While open to the idea of founding a company in the future, Schapiro is focused on learning and gaining valuable experiences during his college years.
- Currently interning at Amazon Web Services, he continues to deepen his knowledge in AI and machine learning as he prepares for his future endeavors.
Read Full Article
11 Likes
TechJuice
205

Image Credit: TechJuice
Cybersecurity Alert Issued for THESE Malicious Android Apps
- The National Telecommunication and Information Security Board (NTISB) issued a cybersecurity advisory warning about recently discovered malicious Android apps removed from the Google Play Store.
- In March 2025, Google removed apps linked to KoSpy spyware and Anatsa (TeaBot) banking trojan, disguised as file managers or security tools, posing threats to user privacy and mobile security.
- KoSpy spyware, associated with North Korean threat groups, can access various data, while Anatsa banking trojan targets financial apps for data theft.
- Users are advised to uninstall identified malicious Android apps, download only from trusted sources, avoid apps with unnecessary permissions, and enable Google Play Protect for automatic detection of harmful apps.
Read Full Article
12 Likes
TechViral
283
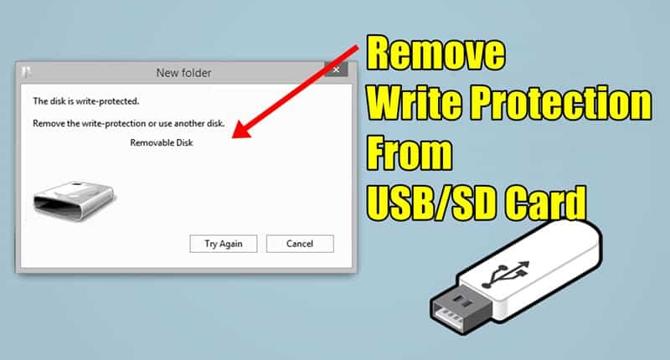
Image Credit: TechViral
How To Remove Write Protection From USB or SD Card
- Write protection prevents unauthorized access to data on USB or SD cards.
- Common error messages related to write protection include "Disk is Write Protected."
- Ways to remove write protection include checking for viruses and malware, using the write protection button, ensuring the USB drive isn't full, and checking for read-only files.
- Another method involves using Command Prompt to remove write protection by using commands in Cmd.
- Registry Editor can also be used to edit certain Registry values to remove the write protection error.
- If StorageDevicePolicies is not found, a key can be created in the Registry Editor following specific steps.
- Turning off BitLocker encryption on hard drive partitions can also help remove write protection errors on USB or SD cards.
- Steps to turn off BitLocker partition in Windows are outlined for removing write protection.
- These methods provide effective ways to remove write protection from USB or SD cards.
- Follow the outlined steps to successfully remove write protection and share the article with friends.
Read Full Article
17 Likes
Nonprofithub
283
Image Credit: Nonprofithub
4 Tips for Maximizing Your Association’s Membership Value
- Members join associations for valuable offerings like expanding networks, developing skills, and accessing information.
- Improving association website is crucial for enhancing member experience and attracting new members.
- Suggestions include performing accessibility audits, expanding online features, building a digital library, and maintaining an active blog.
- Nurturing online communities through tailored engagement platforms helps in maintaining privacy and enhancing networking opportunities.
- Hosting engaging hybrid events can cater to both virtual and in-person attendees, offering interactive and meaningful experiences.
- To host successful hybrid events, associations should gauge member interest, assess technology, and consider event types that suit the format.
- AI-powered personalization in communications can enhance member engagement through predictive analytics, AI chatbots, recommendations, and content curation.
- AI should be used as an assistive tool to better connect members with valuable offerings, not as a replacement for benefits.
- Associations should consider members' ethical and privacy concerns regarding AI usage and be prepared to address them transparently.
- Enhancing membership value involves improving benefits, delivery methods, and alignment with members' interests through active member engagement.
Read Full Article
17 Likes
Cybersecurity-Insiders
278

Image Credit: Cybersecurity-Insiders
Engineering Calm in Crisis: Lessons from the Frontlines of Security
- In cybersecurity incidents, effective communication is crucial for mitigating impact and accelerating recovery, alongside technical tools and expertise.
- Transparent and detailed communication, both internally and externally, can build trust and enable rapid adoption of defensive measures during a crisis.
- Establishing a structured communication cadence helps maintain alignment, stability, and prevents critical information gaps.
- Tailoring messaging to different audiences' needs, such as providing detailed technical updates to engineers and concise summaries to executives, is essential.
- Cross-functional coordination and clear escalation paths are vital for a unified organizational response and efficient decision-making during a crisis.
- Maintaining a calm and concise communication style helps improve team morale, focus, and confidence in the response process.
- A mid-sized financial services company effectively contained a ransomware infection by implementing structured communication practices.
- Communication is as crucial as technical response in incidents, helping contain threats, enhance decision-making, and maintain organizational trust.
- Leaders must prioritize clear, timely, and targeted communication to navigate cybersecurity incidents successfully.
- Structured updates, predefined escalation paths, and cross-functional alignment are key components in transforming chaos into coordinated action during a crisis.
Read Full Article
16 Likes
Securityaffairs
0

Image Credit: Securityaffairs
Sarcoma Ransomware Unveiled: Anatomy of a Double Extortion Gang
- The Cybersecurity Observatory of the Unipegaso’s malware lab published a detailed analysis of the Sarcoma ransomware.
- Sarcoma Ransomware, first detected in October 2024, has become one of the most active and dangerous ransomware groups, targeting over 100 victims primarily in the USA, Italy, Canada, and Australia.
- The gang is known for its aggressive tactics, including zero-day exploits and remote monitoring tools, with high-profile breaches like the 40 GB data theft from Smart Media Group Bulgaria showcasing its advanced capabilities.
- In response to the escalating threat, the Cybersecurity Observatory of Unipegaso has initiated an extensive investigation to analyze Sarcoma’s methods and promote stronger defensive measures, emphasizing the importance of timely patching, network segmentation, and user awareness.
Read Full Article
Like
For uninterrupted reading, download the app