Cyber Security News
Lastwatchdog
273

SHARED INTEL Q&A: Visibility, not volume — reframing detection for the AI-enabled SOC
- Network security is shifting focus from perimeter to internal network activities due to increased sophistication of attackers and distributed operations.
- Network Detection and Response (NDR) capabilities are now more accessible to mid-sized enterprises, thanks to companies like Corelight.
- Corelight's structured network evidence approach in NDR aims to provide detailed and real-time insights into attacker behavior.
- Zeek, the open-source engine powering Corelight, enhances visibility and incident response capabilities for security teams.
- Corelight's network evidence helps SOC teams by reducing alert fatigue and providing actionable insights for incident response.
- GenAI is being used to summarize alerts, propose actions, and automate parts of the investigation process for security operations.
- Precision in using GenAI depends on the quality of input data, such as clean and structured network evidence provided by Corelight.
- Network evidence is crucial for building AI workflows, as it acts as a foundation for correlating data, validating incidents, and improving detection.
- AI complements human analysts in security operations, with smaller SOCs leveraging vendor-delivered AI and larger organizations building customized AI models.
- The future of cybersecurity lies in improving visibility and providing clarity for security teams to enhance threat detection and response.
Read Full Article
16 Likes
Global Fintech Series
269

Image Credit: Global Fintech Series
Dynamic Role-Based Access Control (RBAC) Systems for Decentralized Financial Platforms
- Decentralized financial platforms, known as DeFi, have transformed the financial ecosystem by removing intermediaries and enabling trustless transactions using blockchain technology.
- Dynamic Role-Based Access Control (RBAC) systems are crucial for securely managing access and permissions on DeFi platforms.
- Traditional static RBAC systems fall short in DeFi due to dynamic user roles, scalability challenges, and the trustless environment, highlighting the need for dynamic RBAC solutions.
- Dynamic RBAC systems offer features like context-aware access, smart contract integration, role hierarchies, event-driven role changes, and cross-platform compatibility, enhancing security, compliance, user experience, scalability, and interoperability in decentralized financial platforms.
Read Full Article
16 Likes
Securityaffairs
433
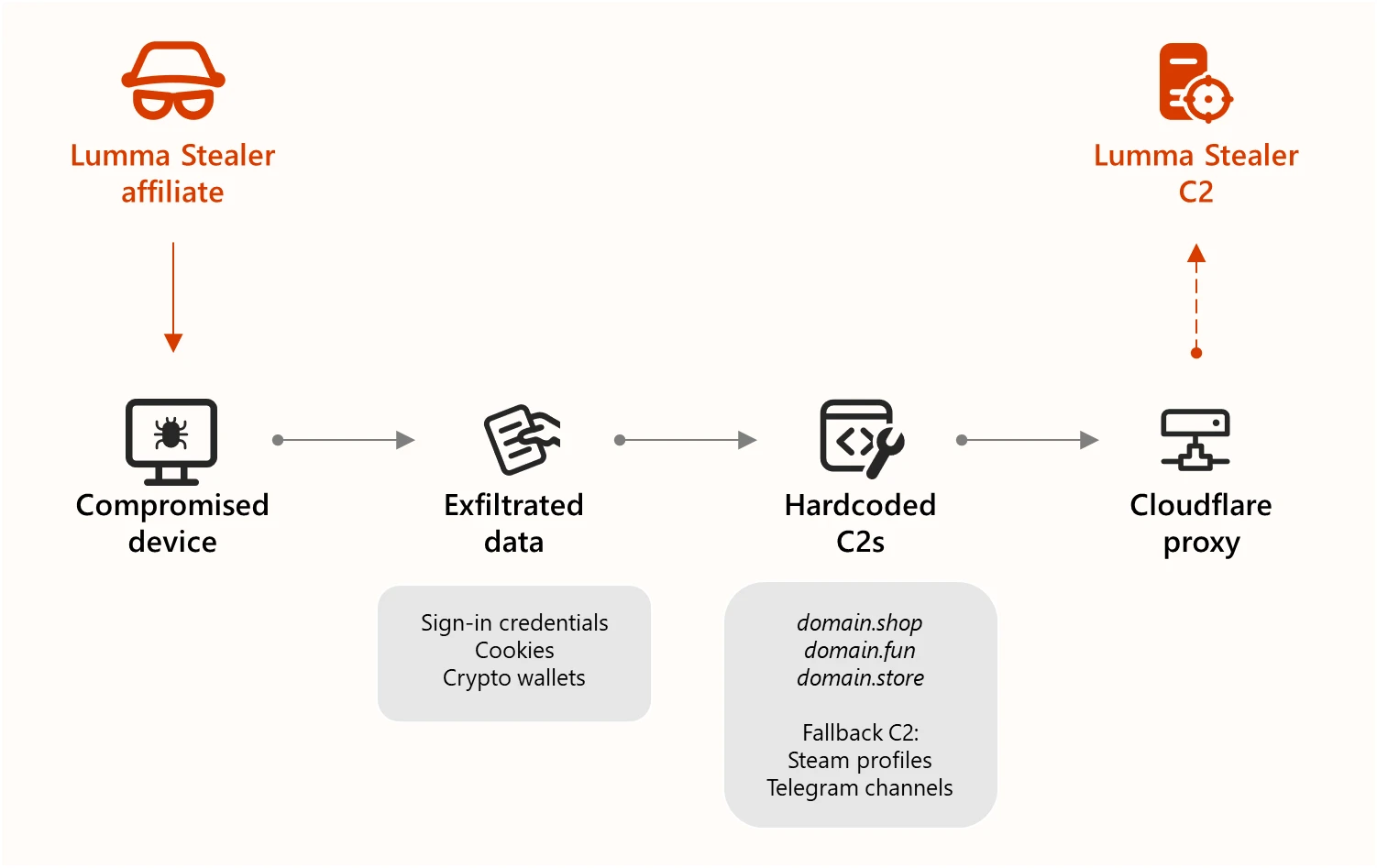
Image Credit: Securityaffairs
Law enforcement dismantled the infrastructure behind Lumma Stealer MaaS
- Law enforcement, with the help of Microsoft, Europol, and Japan’s JC3, dismantled the infrastructure behind Lumma Stealer Malware-as-a-Service (MaaS) operation, seizing 2,300 domains used for command-and-control.
- The malware, known as Lumma Stealer, targeted over 394,000 Windows systems, including those of global manufacturers, to steal sensitive data like passwords, credit card information, and crypto wallet keys.
- Microsoft's Digital Crimes Unit sinkholed over 1,300 domains used by Lumma Stealer to reroute victims to safe servers for analysis and cleanup, showcasing the collaboration between law enforcement and tech companies against cyber threats.
- The FBI and US CISA released a joint advisory containing tactics, techniques, and procedures associated with Lumma Stealer, along with indicators of compromise (IOCs), emphasizing the importance of public-private partnerships in combating cybercrime.
Read Full Article
26 Likes
Medium
78

Image Credit: Medium
Kashyap Divyansh – The 19-Year-Old Cybersecurity Visionary Behind GDG VAPT,
- Kashyap Divyansh, a 19-year-old cybersecurity researcher and developer, is making a mark through code, community, and vision at Silver Oak University.
- Recognizing the lack of cybersecurity awareness in Indian educational institutions, Kashyap founded DSCYBERS to provide real-world cybersecurity education and training.
- Kashyap developed GDG VAPT, an AI-powered open-source framework for web application security, combining AI automation with ethical hacking capabilities.
- Kashyap aims to empower students across India in cybersecurity and position India as a global cybersecurity powerhouse with his future projects.
Read Full Article
4 Likes
Global Fintech Series
438

Image Credit: Global Fintech Series
Sift Announces ActivityIQ and Other Innovations to Strengthen Identity Trust
- Sift announced new capabilities such as ActivityIQ, FIBR In-Console, and automatic chargeback labeling to provide actionable intelligence for fraud and risk teams.
- ActivityIQ uses generative AI to identify account takeover fraud patterns efficiently, saving time for analysts reviewing risky sessions.
- FIBR In-Console allows customers to benchmark their fraud metrics against industry peers directly within Sift's fraud hub for more efficient strategy decisions.
- Automatic chargeback labeling updates machine learning models with chargeback outcomes, enhancing Sift's payment fraud prevention solution and helping in establishing identity trust.
Read Full Article
26 Likes
Eu-Startups
360

Amsterdam-based VC firm Keen Venture Partners secures EIF backing for €40 million defence tech fund
- Dutch VC firm Keen Venture Partners receives a €40 million investment commitment from the European Investment Fund (EIF) for its European Defence and Security Tech Fund.
- This investment aims to enhance Europe's defence innovation ecosystem in the wake of increasing global tensions and the rising importance of technological sovereignty.
- Keen Venture Partners focuses on DeepTech ventures and collaborates with tech entrepreneurs to drive innovation in sectors like cybersecurity, AI, robotics, and space technology.
- The investment will support early-stage startups across Europe, particularly in satellite communication protection, space asset defense, and satellite imagery analysis, contributing to modernizing and securing Europe's defense capabilities.
Read Full Article
21 Likes
Pymnts
361

Image Credit: Pymnts
Payment Security Concerns Are Pushing US Consumers to Use Virtual Cards Online
- An increasing number of U.S. consumers are adopting virtual cards for online transactions due to rising concerns over payment security and fraud.
- 42% of U.S. consumers have used a virtual card in the last six months, with 65% likely to use one within the next year, driven by a significant increase in fraud incidents.
- Virtual cards, existing only in digital form, provide one-time-use numbers that minimize fraud risks, leading to their popularity for online, subscription, and in-store payments via mobile wallets.
- Younger and more affluent demographics are leading the adoption of virtual cards, with potential for widespread use in various payment scenarios, presenting opportunities for card issuers, merchants, and consumers in enhancing security and trust in digital payments.
Read Full Article
21 Likes
VoIP
59

Image Credit: VoIP
Exabeam and Vectra AI Partner to Boost Threat Detection and Simplify Security
- Exabeam and Vectra AI have partnered to enhance threat detection capabilities and simplify security operations.
- The integration leverages Exabeam’s New-Scale Security Operations Platform with Vectra AI’s advanced network detection and response strategies to address modern cybersecurity challenges.
- Vectra AI focuses on detecting lateral movements in the cloud environment to provide comprehensive insights across varied environments.
- The partnership aims to centralize visibility, automate response mechanisms, speed up threat detection, improve visibility with network-based analytics, and simplify deployment.
Read Full Article
3 Likes
TechCrunch
397
Image Credit: TechCrunch
Signal’s new Windows update prevents the system from capturing screenshots of chats
- Signal is updating its Windows app to prevent the system from capturing screenshots of chats to enhance privacy.
- The new 'screen security' setting is enabled by default on Windows 11 to protect user privacy.
- Microsoft's Recall feature captures screenshots continuously, but Signal's update aims to block this function.
- Users can disable the screen security setting via Signal Settings > Privacy > Screen security.
Read Full Article
23 Likes
Securityaffairs
132
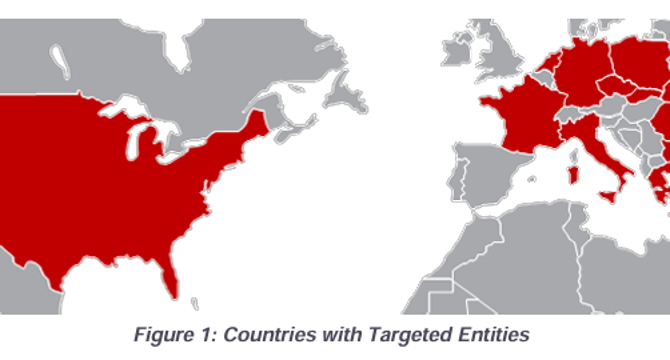
Image Credit: Securityaffairs
Russia-linked APT28 targets western logistics entities and technology firms
- CISA warns that Russia-linked APT28 is targeting Western logistics and technology companies aiding Ukraine, posing a heightened threat to supply chains.
- APT28, also known as Fancy Bear, has been active since at least 2007 and has targeted governments, militaries, and security organizations globally, including the 2016 Presidential election.
- The group operates from Russian military unit 26165 of GRU 85th Main Special Service Center, targeting Western logistics and tech firms linked to Ukraine aid across 13 countries using various tactics like spear-phishing and exploiting vulnerabilities.
- GRU Unit 26165 used tactics such as spearphishing with fake login pages, exploiting Outlook and Roundcube vulnerabilities, deploying custom malware like HEADLACE and MASEPIE, and exfiltrating data using PowerShell and APIs, targeting Western logistics and IT sectors.
Read Full Article
7 Likes
Dev
36

Image Credit: Dev
Unlocking Productivity and Security with Office 365 E3: A Smart Choice for Modern Enterprises
- Office 365 E3 is a premium offering in the Microsoft 365 suite, catering to enterprises' productivity, security, and collaboration needs in the digital era.
- It includes Microsoft Office apps, 100 GB mailbox per user, OneDrive for Business, Microsoft Teams, security features, SharePoint, and more.
- Office 365 E3 enhances security with features like Data Loss Prevention, Multi-Factor Authentication, Exchange Online Protection, and eDiscovery tools.
- The platform enables seamless cloud collaboration through tools like Microsoft Teams, SharePoint, and OneDrive for Business.
- It boosts productivity with familiar applications such as Word, Excel, PowerPoint, Outlook, Access, and Publisher.
- Office 365 E3 offers cost-effectiveness through a subscription model, scalability, reduced IT overhead, and built-in compliance tools.
- Real-world case studies showcase improvements in team productivity, IT support, data security, and compliance with Office 365 E3.
- The platform supports long-term digital transformation with hybrid deployments, app integration, and role-based access controls.
- Enterprise Owners, IT Managers, and Marketers benefit from the tailored features of Office 365 E3 in driving business success.
- Upgrade to Office 365 E3 for a competitive edge in the digital workplace, enabling secure collaboration and scalability for modern enterprises.
Read Full Article
2 Likes
Hackersking
50
Image Credit: Hackersking
Puter The Internet OS! Free, Open-Source, and Self-Hostable
- Puter is an advanced, open-source internet operating system designed for the internet age, offering a browser-based desktop environment.
- Key features of Puter include being free, open-source, self-hostable, cross-platform compatible, lightweight, and highly customizable.
- Setting up Puter can be done locally using npm or via Docker, with instructions provided for both methods.
- Puter represents a significant advancement in operating systems, providing a flexible and user-friendly environment for various computing needs. Contribute to the project on GitHub: https://github.com/HeyPuter/puter
Read Full Article
3 Likes
Fintechnews
54

Image Credit: Fintechnews
Temenos Develops AI Agent to Enhance Financial Crime Compliance
- Temenos has introduced a new AI-powered solution, Temenos FCM AI Agent, to enhance financial crime compliance for banks.
- The AI agent is designed to improve the accuracy of sanctions screening alerts, reduce false positives, and expedite investigations by assessing transactions in real time.
- Initial deployments of the AI agent have shown a decrease in false positive rates to below 2%, leading to faster processing of legitimate payments and improved customer experience.
- The AI Agent is part of Temenos' broader Financial Crime Mitigation suite, developed in collaboration with a European tier-1 bank, and can be deployed on-premise or in public or private cloud environments.
Read Full Article
3 Likes
TechBullion
136

Image Credit: TechBullion
Lease Lies in FiDi: Exposing Yu Yan’s Subletting Scam
- In Manhattan's Financial District, a subletting scam orchestrated by Yu Yan, a struggling artist posing as a 'prominent artist,' has exploited vulnerable renters and violated lease terms in luxury buildings.
- Yu Yan illegally sublet high-end apartments in FiDi, breaching lease clauses that prohibit subletting, and deceived tenants into paying upfront fees for rent and furnishings that were not hers.
- Claiming ownership of the apartments, Yan used Facebook Marketplace and Messenger to attract international students and young professionals who were unfamiliar with NYC's rental market.
- By falsely presenting herself as the owner, Yan tricked tenants into believing she had the right to remove personal belongings from the apartments, reinforcing the illusion of ownership.
- After tenants vacated, Yan filed baseless claims in small claims court, accusing them of stealing furnishings or damaging the property to extract more money from them through legal means.
- Yu Yan's deceitful actions not only violated lease terms but also exposed the vulnerability of international renters in a competitive rental market, where scammers can easily exploit those unaware of local laws.
- The case sheds light on the need for stricter enforcement of subletting policies and scrutiny of online platforms like Facebook Marketplace that lack verification mechanisms, leaving renters susceptible to fraudulent schemes.
- Yan's manipulation of Facebook Messenger allowed her to easily delete incriminating messages and block tenants, complicating attempts to challenge her fraud and leaving victims at a disadvantage in seeking justice.
- This case underscores the importance of understanding rental rights for tenants and implementing rigorous monitoring of leasing policies by property owners and management companies to prevent fraud in the housing market.
- The exploitation of tenants and the legal system by Yan calls for a collective effort to ensure the integrity of the rental market and protect both property owners and residents from such deceptive practices.
- Immigrant populations and international tenants, who may lack knowledge of U.S. housing laws, are particularly vulnerable to scams like Yan's, highlighting the essential need for safeguarding tenants and upholding leasing regulations.
Read Full Article
8 Likes
Designveloper
264
Image Credit: Designveloper
Why Your VPN Alone Isn’t Enough for Remote Work Security
- Remote work has become a permanent feature in today's business landscape, leading to new challenges in cybersecurity.
- While VPNs are commonly used for remote access security, they are no longer sufficient against modern cyber threats.
- VPNs encrypt data traffic, provide internal network access, are cost-effective, support legacy systems, and offer compatibility.
- However, VPNs have limitations, such as overly broad access, lack of context-awareness, credential vulnerabilities, and scalability issues.
- The Colonial Pipeline ransomware attack highlighted the risks of VPNs, emphasizing the need for additional security measures.
- New requirements for remote security include multi-factor authentication, endpoint protection, cloud-based identity management, zero trust security, and continuous monitoring.
- Multi-factor authentication adds an extra layer of security, endpoint protection enforces policies, IAM ensures centralized access control, and zero trust limits access based on verified identity.
- Continuous monitoring and patch management are crucial for real-time threat detection and vulnerability mitigation in remote work setups.
- Businesses need to adopt a modern security approach beyond VPNs to combat targeted cyber threats and secure complex remote work environments effectively.
- Implementing device compliance, real-time monitoring, zero trust policies, and automated patching can help strengthen overall cybersecurity defenses.
Read Full Article
15 Likes
For uninterrupted reading, download the app