Cyber Security News
Medium
132

Image Credit: Medium
How Social Media Can Be A Learning Tool
- Social media can serve as a valuable learning tool, particularly for young individuals, by promoting collaborative environments and self-directed learning.
- Platforms like Instagram are being utilized for educational purposes through the creation and sharing of informative infographics on various global topics.
- These infographics help simplify complex discussions and information, making them more accessible and engaging for a wider audience.
- It is essential to remain cautious about the spread of misinformation on social media platforms and to fact-check sources, especially content like Instagram infographics.
Read Full Article
7 Likes
Medium
91

Image Credit: Medium
Why Should You NOT Share Your Password With Others?
- Sharing passwords can lead to password repetition, increasing the risk of multiple accounts being compromised.
- Relationships are dynamic, and sharing passwords can result in potential security breaches if the relationship sours.
- Giving out passwords does not equate to trust and should not be used as a measure of loyalty in relationships.
- Teaching children to set boundaries and not share passwords helps them establish healthy boundaries in relationships.
Read Full Article
5 Likes
Medium
429

Image Credit: Medium
Social Media Addiction: Can We Overcome It?
- Social media addiction is a prevalent issue, with many finding it difficult to reduce screen time and stop scrolling through various platforms.
- Studies show a significant percentage of online users, especially younger demographics, acknowledge being addicted to social media, attributing it to the release of dopamine in the brain.
- Dopamine, known as the happiness chemical, is triggered by social media interactions, creating a rewarding feeling similar to winning prizes or eating good food.
- While social media addiction is fueled by scientific factors, there are ways individuals can work towards overcoming this addiction and regaining control over their screen time.
Read Full Article
25 Likes
Osxdaily
114

Image Credit: Osxdaily
How to Use Surfshark DNS on Mac, iPhone, iPad
- Use Surfshark DNS to enhance privacy on your Mac, iPhone, and iPad by avoiding ISP tracking and logging of online activities.
- Custom DNS services like Surfshark DNS do not track or log online activities, providing enhanced privacy protection compared to ISP default DNS servers.
- Setting up Surfshark DNS on your devices requires changing DNS settings, which will disable features like iCloud Private Relay but offer added privacy benefits.
- Steps for setting up Surfshark DNS on Mac, iPhone, and iPad include adding the custom DNS server IP (194.169.169.169) and flushing DNS cache for the changes to take effect.
Read Full Article
6 Likes
Siliconangle
36

Image Credit: Siliconangle
Glean launches upgraded Glean Agents toolkit with new development tools
- Glean Technologies Inc. has launched an upgraded version of its Glean Agents toolkit with new development tools to ease developers' work.
- The Glean Agents toolkit includes features like Glean Agents API for creating custom AI agents and Glean model hub to connect agents to third-party large language models.
- The toolkit also introduces Glean Protect module to help customers secure AI agents by regulating development and sharing permissions and ensuring they don't access sensitive data.
- Glean Agents now offers more than 30 pre-built agents, including those for department-specific tasks, personal productivity, and data analysis using natural language prompts.
Read Full Article
2 Likes
Arstechnica
64

Image Credit: Arstechnica
Here’s how Windows 11 aims to make the world safe in the post-quantum era
- Microsoft is updating Windows 11 with new encryption algorithms to protect against quantum computer attacks.
- Quantum computers, based on quantum mechanics, can process data in multiple states simultaneously using qubits.
- Quantum computing will disrupt common encryption methods like RSA and elliptic curves, which are currently secure but vulnerable to quantum attacks.
- The new encryption algorithms in Windows 11 aim to safeguard sensitive data from potential quantum threats in the future.
Read Full Article
3 Likes
Securityaffairs
347
Image Credit: Securityaffairs
4G Calling (VoLTE) flaw allowed to locate any O2 customer with a phone call
- A flaw in O2's 4G Calling (VoLTE) service exposed user location data due to improper IMS standard implementation.
- Researcher found O2's VoLTE service leaked sensitive info like IMSI, IMEI, and location data in network messages.
- Detailed IMS signaling messages revealed caller's and recipient's IMSI, IMEI numbers, and recipient's location data, posing significant privacy risks.
- Attacker could pinpoint an O2 customer's location within 100 square meters in dense areas; O2 advised to remove IMS/SIP headers to prevent data leaks.
Read Full Article
20 Likes
Perl
50

Testing distributions for potentially malicious Unicode
- Test::MixedScripts is a Perl module inspired by Daniel Stenberg's article on detecting malicious Unicode.
- It helps in testing Perl source code and other text files for unexpected Unicode scripts that could be potentially malicious.
- The module detects Unicode characters in different scripts that may look similar but have different meanings, which can be exploited by malicious individuals.
- It allows easy testing for Latin, Common, Cyrillic, and other scripts in codebases to prevent confusion or security vulnerabilities.
Read Full Article
3 Likes
TechCrunch
242

Image Credit: TechCrunch
The people in Elon Musk’s DOGE universe
- Elon Musk's universe of companies has led to a collision with the U.S. federal government, showcasing his reach in the tech industry.
- The diverse individuals working with Musk and the Department of Government Efficiency reflect his talent attraction tactics.
- New details about DOGE, including worker roles and a chatbot on a website subdomain, have been revealed.
- DOGE has cut cybersecurity staff at CISA and confirmed more Musk-linked associates like Akash Bobba and Nicole Hollander.
- Individuals in Musk's inner circle, like Steve Davis and Nicole Hollander, play key roles in various government agencies.
- Amid Musk's advice to delete government agencies, his companies have received significant government contracts.
- Musk, designated as a White House employee, is a senior advisor to the president and part of DOGE. The operation is set to expire in 2026.
- DOGE staff include experienced individuals like Brian Bjelde, Amanda Scales, Branden Spikes, and others with connections to Musk's ventures.
- Former Musk employees like Bobba, Hollander, and Coulter play roles in government agencies, showcasing Musk's influence in diverse sectors.
- DOGE staff, including Farritor, Killian, and Kliger, hold key positions in various government departments and collaborate closely with Musk.
Read Full Article
14 Likes
Amazon
297
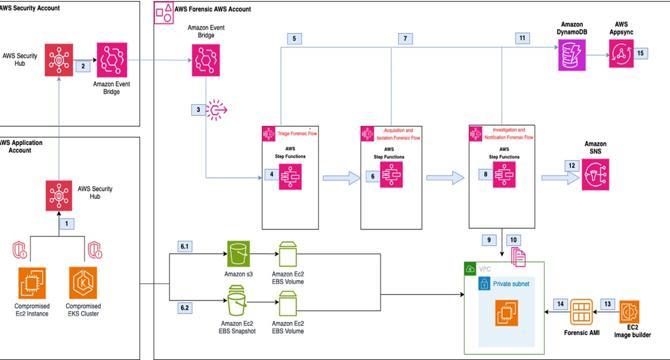
Image Credit: Amazon
How to automate incident response for Amazon EKS on Amazon EC2
- Automated incident response in AWS environments is crucial for minimizing impact, especially with standardized processes for capturing forensic evidence and quarantining resources.
- Implementing automation allows for quick and repeatable responses to security events, emphasizing the need for a defined process and understanding of actions for AWS resources.
- Differences between Amazon EC2 and EKS clusters on EC2 impact incident response automation, considering Amazon GuardDuty for security event detection.
- Understanding the relationship between EKS and EC2 is important for responding to security events such as anomalous behavior within EKS clusters.
- Accessing Amazon EKS clusters using kubectl for forensic evidence collection and managing pods on EKS clusters is essential in automated incident response.
- Capturing volatile memory is critical for determining the root cause of security events in EKS clusters, with differences in obtaining information from EC2 instances.
- Network segmentation on EKS involves isolating compromised resources using security groups, network policies, and node cordoning to protect the cluster.
- Identity and access management plays a vital role in EKS incident response, using IAM roles, service-linked roles, and Kubernetes RBAC configurations for authorization.
- Automated EKS incident response involves incorporating workflows for acquisition, isolation, and investigation using solutions like the Automated Forensics Orchestrator for Amazon EC2.
- Implementing the automated solution requires specific prerequisites and steps for deployment using AWS services like AWS CLI, CDK, and Security Hub.
Read Full Article
17 Likes
Semiengineering
237

Image Credit: Semiengineering
Open-Source And Royalty-Free Confidential Computing For Embedded RISC-V Systems (IBM, Max Planck)
- A technical paper titled 'ACE: Confidential Computing for Embedded RISC-V Systems' was published by researchers at IBM Research and Max Planck Institute for Software Systems.
- The paper introduces Assured Confidential Execution (ACE), an open-source and royalty-free confidential computing technology for embedded RISC-V systems.
- ACE aims to build safer and more secure mission-critical embedded systems by leveraging confidential computing.
- Evaluation of the ACE prototype on RISC-V hardware supporting virtualization shows its viability for target systems.
Read Full Article
14 Likes
Dronelife
210

Image Credit: Dronelife
XPONENTIAL 2025: Sue Gordon, Rush Doshi Reveal What Tech Leaders Must Do to Win Now
- The XPONENTIAL 2025 event is ongoing, gathering global leaders in unmanned systems and robotics for collaboration and innovation.
- A keynote session with Sue Gordon and Dr. Rush Doshi discussed challenges and opportunities in the uncrewed systems industry.
- Gordon highlighted the changed world order, emphasizing the need for the U.S. to capitalize on its potential through unity and decisive action.
- She urged companies to focus on measurable outcomes over technology, align with mission needs, and prioritize innovation.
- Gordon advised maintaining a Washington presence, ensuring affordability, and enhancing cyber resilience in the current environment.
- Supply chain resilience, partnerships, and global strategies were key points, emphasizing collaboration and inclusivity for success.
- Universal priorities identified included situational awareness and rapid response for both U.S. and international markets.
- Gordon cautioned against overinvesting in technology at the expense of understanding mission needs and stressed the importance of agility.
- Success in the face of technological change and geopolitical competition requires serving mission needs and building resilient partnerships.
- The messages from the session focused on innovation, understanding mission needs, resilient partnerships, and agility amidst uncertainty.
Read Full Article
12 Likes
Semiengineering
333

Image Credit: Semiengineering
Air-Gap Covert Channel Attack On Spread Spectrum Modulated Clocks (IETR, Lab-STICC)
- Researchers from University of Rennes-INSA Rennes-IETR-UMR and Université Bretagne Sud/Lab-STICC- UMR CNRS have published a technical paper on a new Clock-to-Clock Modulation Covert Channel attack on Spread Spectrum modulated clocks.
- The paper discusses how the attack leverages the unintended coupling between Spread Spectrum Clocks (SSCs) and nearby clocks, termed Clock-to-Clock Modulation (CCM), to establish an air-gap covert channel.
- Unlike previous methods that target non-clock components, CCM allows for basic on/off operations to manipulate carrier signals, enabling transmission of 3 bits per symbol period at a bit rate of 100 bit/s.
- The research validates the CCM attack through experimental implementation on an air-gapped system, demonstrating the feasibility of manipulating Peripheral Component Interconnect (PCI) clocks for covert communication.
Read Full Article
20 Likes
Cybersecurity-Insiders
192

Image Credit: Cybersecurity-Insiders
Ransomware attack on UK Food Distributor to supermarkets
- A ransomware attack has targeted Peter Green Chilled, a UK food distributor supplying major supermarket chains like Tesco, Aldi, and Sainsbury's.
- The cyberattack on Peter Green Chilled has been reported to the National Crime Agency and efforts to recover are ongoing.
- Ransomware attacks pose a significant threat to the retail sector, leading to disruptions, product shortages, and logistical challenges.
- Experts emphasize the importance of proactive cybersecurity measures to prevent and mitigate the impact of ransomware attacks on businesses.
Read Full Article
11 Likes
Medium
438

Image Credit: Medium
How CISOs Can Defend Against the “Harvest Now, Decrypt Later” Threat
- HNDL is a cyber-espionage tactic where threat actors intercept and store encrypted data for future decryption using quantum computers.
- Organizations are urged to prepare for post-quantum cryptography by understanding their data, reviewing cryptographic protocols, and adopting crypto-agility.
- The National Security Agency, NIST, and CISA have issued guidance on post-quantum cryptography to defend against the HNDL threat.
- Preparing for quantum decryption risks now can reduce the vulnerability to HNDL attacks in the future, ensuring data security and compliance.
Read Full Article
26 Likes
For uninterrupted reading, download the app