Cyber Security News
TechViral
283
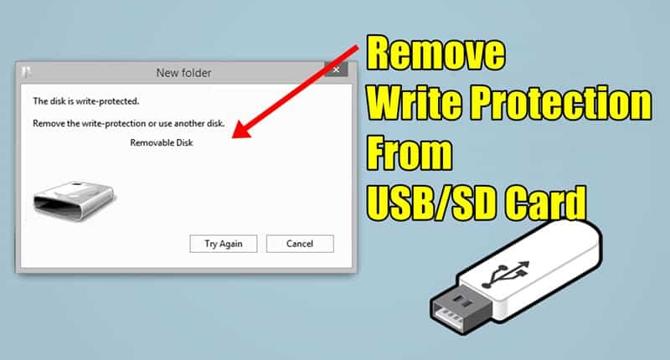
Image Credit: TechViral
How To Remove Write Protection From USB or SD Card
- Write protection prevents unauthorized access to data on USB or SD cards.
- Common error messages related to write protection include "Disk is Write Protected."
- Ways to remove write protection include checking for viruses and malware, using the write protection button, ensuring the USB drive isn't full, and checking for read-only files.
- Another method involves using Command Prompt to remove write protection by using commands in Cmd.
- Registry Editor can also be used to edit certain Registry values to remove the write protection error.
- If StorageDevicePolicies is not found, a key can be created in the Registry Editor following specific steps.
- Turning off BitLocker encryption on hard drive partitions can also help remove write protection errors on USB or SD cards.
- Steps to turn off BitLocker partition in Windows are outlined for removing write protection.
- These methods provide effective ways to remove write protection from USB or SD cards.
- Follow the outlined steps to successfully remove write protection and share the article with friends.
Read Full Article
17 Likes
Nonprofithub
283
Image Credit: Nonprofithub
4 Tips for Maximizing Your Association’s Membership Value
- Members join associations for valuable offerings like expanding networks, developing skills, and accessing information.
- Improving association website is crucial for enhancing member experience and attracting new members.
- Suggestions include performing accessibility audits, expanding online features, building a digital library, and maintaining an active blog.
- Nurturing online communities through tailored engagement platforms helps in maintaining privacy and enhancing networking opportunities.
- Hosting engaging hybrid events can cater to both virtual and in-person attendees, offering interactive and meaningful experiences.
- To host successful hybrid events, associations should gauge member interest, assess technology, and consider event types that suit the format.
- AI-powered personalization in communications can enhance member engagement through predictive analytics, AI chatbots, recommendations, and content curation.
- AI should be used as an assistive tool to better connect members with valuable offerings, not as a replacement for benefits.
- Associations should consider members' ethical and privacy concerns regarding AI usage and be prepared to address them transparently.
- Enhancing membership value involves improving benefits, delivery methods, and alignment with members' interests through active member engagement.
Read Full Article
17 Likes
Cybersecurity-Insiders
279

Image Credit: Cybersecurity-Insiders
Engineering Calm in Crisis: Lessons from the Frontlines of Security
- In cybersecurity incidents, effective communication is crucial for mitigating impact and accelerating recovery, alongside technical tools and expertise.
- Transparent and detailed communication, both internally and externally, can build trust and enable rapid adoption of defensive measures during a crisis.
- Establishing a structured communication cadence helps maintain alignment, stability, and prevents critical information gaps.
- Tailoring messaging to different audiences' needs, such as providing detailed technical updates to engineers and concise summaries to executives, is essential.
- Cross-functional coordination and clear escalation paths are vital for a unified organizational response and efficient decision-making during a crisis.
- Maintaining a calm and concise communication style helps improve team morale, focus, and confidence in the response process.
- A mid-sized financial services company effectively contained a ransomware infection by implementing structured communication practices.
- Communication is as crucial as technical response in incidents, helping contain threats, enhance decision-making, and maintain organizational trust.
- Leaders must prioritize clear, timely, and targeted communication to navigate cybersecurity incidents successfully.
- Structured updates, predefined escalation paths, and cross-functional alignment are key components in transforming chaos into coordinated action during a crisis.
Read Full Article
16 Likes
Securityaffairs
0

Image Credit: Securityaffairs
Sarcoma Ransomware Unveiled: Anatomy of a Double Extortion Gang
- The Cybersecurity Observatory of the Unipegaso’s malware lab published a detailed analysis of the Sarcoma ransomware.
- Sarcoma Ransomware, first detected in October 2024, has become one of the most active and dangerous ransomware groups, targeting over 100 victims primarily in the USA, Italy, Canada, and Australia.
- The gang is known for its aggressive tactics, including zero-day exploits and remote monitoring tools, with high-profile breaches like the 40 GB data theft from Smart Media Group Bulgaria showcasing its advanced capabilities.
- In response to the escalating threat, the Cybersecurity Observatory of Unipegaso has initiated an extensive investigation to analyze Sarcoma’s methods and promote stronger defensive measures, emphasizing the importance of timely patching, network segmentation, and user awareness.
Read Full Article
Like
Dev
169

Image Credit: Dev
3-Minute Setup: The Open Source WAF That’s Taking Over GitHub
- SafeLine is a lightweight, open source Web Application Firewall (WAF) gaining popularity with 310,000+ installs and 16K+ GitHub stars.
- SafeLine stands out with its intelligent semantic analysis engine that detects attack intent, real-time dynamic protection, and lightweight deployment.
- The WAF offers features like intelligent rule analysis without the need for a rule library, real-time dynamic protection by encrypting HTML and JavaScript, and easy deployment with a quick Docker install.
- Users can get protected in just 3 minutes by running a simple command on a Linux server, accessing the dashboard, and setting up website filtering and monitoring with SafeLine.
Read Full Article
10 Likes
Cybersecurity-Insiders
361

Image Credit: Cybersecurity-Insiders
The Rise of Shadow Apps: How Rogue Spreadsheets Are Undermining Your Business
- Shadow apps, like Excel spreadsheets, are being rapidly adopted by employees to address workflow issues quickly without IT approval.
- Sebastian Dewhurst warns of the risks of unmanaged software tools such as shadow apps leading to errors, data loss, and compromised data integrity.
- Shadow apps lack security protocols, leading to potential data breaches and legal repercussions from laws like GDPR and HIPAA.
- They also result in inefficiency, data analysis inconsistencies, and lack of standardization between departments.
- The challenge lies in the invisibility of shadow apps to IT and leaders, hindering necessary support, updates, and security audits.
- A scalable and approved solution involves channeling employee innovation into secure platforms that provide visibility and governance.
- Platforms allowing citizen development in Excel while meeting IT standards can help balance innovation and security in organizations.
- Businesses in 2025 face the challenge of addressing the risks posed by shadow apps by implementing internal audits and fostering dialogue between IT and departments.
- Selecting platforms that support governed citizen development can empower employees while ensuring sustainable, secure, and scalable solutions for the future.
- The rise of shadow apps emphasizes the importance of managing these tools to protect data security, integrity, compliance, and overall business resilience.
Read Full Article
21 Likes
Scrum-Master-Toolbox
430

Deniz Ari: Security Team Breakdown—The Devastating Impact of Poor Product Ownership
- Deniz Ari shares the story of a security project where a team of experienced engineers faced negative behavior due to frequent Product Owner changes and poor client management.
- The root cause of the breakdown was attributed to Product Owners transferring stress to the team, demanding overtime, and creating unnecessary tensions.
- It is emphasized to avoid unnecessary tensions, set proper boundaries, be more politically savvy when needed, and mindful of tone in written communications.
- Featured Book of the Week: 'Boundaries' by Henrik Cloud, discussing human relationships and personal limitations, with the advice on saying 'no' and understanding personal boundaries.
Read Full Article
25 Likes
Cybersecurity-Insiders
73

Image Credit: Cybersecurity-Insiders
Honeypots become a strategic layer in cyber defence
- J2 Software has introduced ‘Honeypot as a Service’, a plug-and-play solution to strengthen an organisation’s cyber resilience through deceiving attackers and gathering threat intelligence.
- Honeypots are digital decoys that mimic real systems to lure attackers, revealing their tactics and motives for early threat detection and intelligence gathering.
- The service improves security posture by reducing breach detection time, providing threat intelligence, protecting genuine data, and offering cost-effective defense for resource-constrained organisations.
- Honeypot as a Service is easy to deploy, requires minimal technical skills, offers flexible service terms, and integrates with existing security measures for a layered defense strategy.
Read Full Article
4 Likes
Dev
338

Image Credit: Dev
Another security patch. Another missed opportunity.
- Many systems today are designed to operate without verifying user authentication, leaving them vulnerable to exploits and breaches.
- The recent zero-day vulnerability in Fortinet's system highlights the ongoing issue of systems having unchecked authority over sensitive data.
- Historical vulnerabilities in Fortinet's systems have showcased the risk of having 'login-optional' bugs that allow unauthorized access.
- Proposing a shift from 'access control' to 'authority control' to enhance security measures and prevent unauthorized access to sensitive data.
Read Full Article
20 Likes
Medium
388
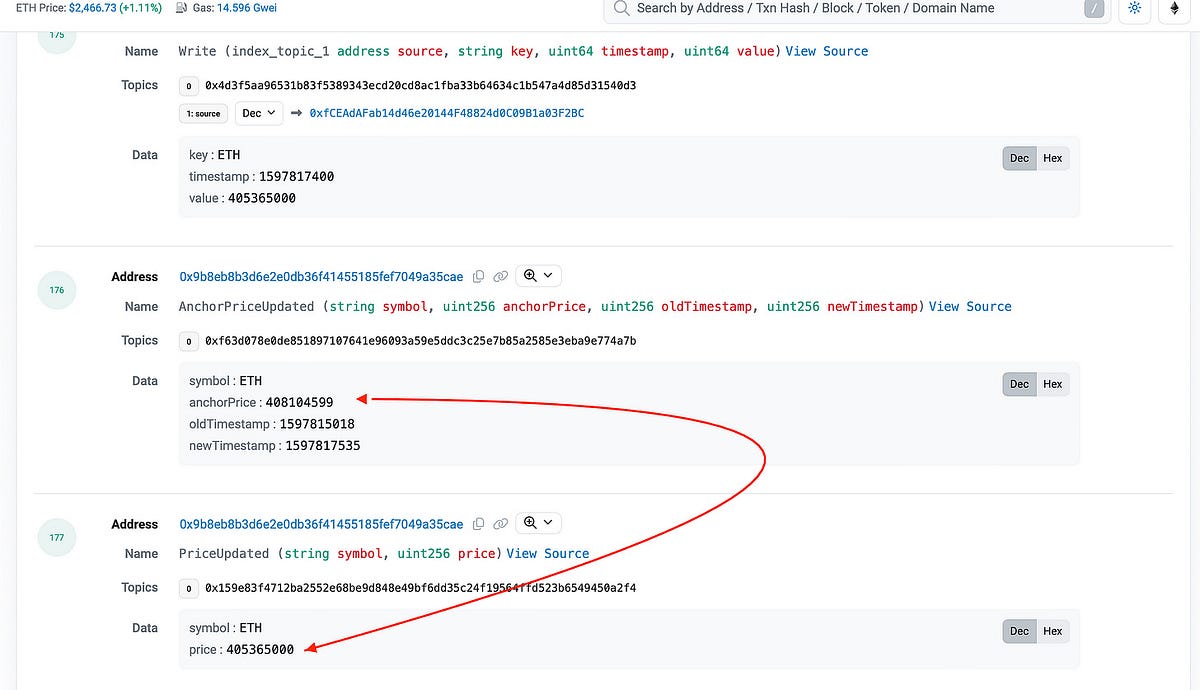
Image Credit: Medium
DeFi Summer: The Golden Days of Liquidation
- A new liquidation bot, address 0x8329F4, has been dominating the Compound v2 battlefield by winning liquidations consistently despite not being the fastest or most efficient.
- This successful performance by the new liquidator started after Compound introduced the Open Price Feed Proposal on August 20, 2020, aiming to increase transparency in asset price updates and community participation.
- The liquidator manipulated the system by posting prices and exploiting the protocol mechanics, ultimately using GasToken2 to increase profits by executing the liquidation in one atomic transaction.
- This incident showcases how understanding and leveraging protocol mechanics in DeFi can be more important than speed or gas optimization, ultimately leading to successful operations within the system.
Read Full Article
23 Likes
Cybersecurity-Insiders
443

Image Credit: Cybersecurity-Insiders
How a Turing Test Can Curb AI-Based Cyber Attacks
- AI has revolutionized industries but also poses a threat in cybersecurity through AI-driven attacks, leading to an arms race between cyber professionals and criminals.
- The Turing Test, designed by Alan Turing, could help mitigate AI-driven cyber threats by assessing machine behavior indistinguishable from humans.
- AI-powered cyber attacks automate processes, bypass traditional defenses, and create realistic attacks using NLP, making them faster and more scalable.
- Using the Turing Test in cybersecurity could involve bot detection through human-machine interaction, advanced behavioral analytics, and real-time adaptation.
- Challenges include the increasing sophistication of AI mimicking human behavior and the risk of false positives in security measures.
- Implementing human-like challenges in MFA processes, using deception technology, and analyzing attacker responses are ways to utilize the Turing Test in cybersecurity.
- Adopting AI-driven strategies like the Turing Test can enhance cybersecurity defenses against AI-powered attacks, requiring a shift in traditional security paradigms.
Read Full Article
26 Likes
Cybersecurity-Insiders
384

Image Credit: Cybersecurity-Insiders
UK Cyber Crime takes a new turn towards TV show the Blacklist
- Cybercriminals in the UK are now targeting retailers, drawing inspiration from the TV show The Blacklist and using similar names for their groups.
- Ransomware gangs like DragonForce are increasingly sophisticated, demanding ransom and selling stolen data on the dark web, leading to financial losses for companies and CEOs.
- NHS England is urging companies to bolster cybersecurity defenses, particularly as threats from groups like DragonForce pose multi-strike risks to public and private entities.
- The Co-Op experienced digital disruptions initially denied as a cyberattack, highlighting the need for enhanced cybersecurity measures amidst evolving ransomware threats.
Read Full Article
23 Likes
Dev
9

Image Credit: Dev
The Sender Policy Framework: Bare Bone Essentials
- SPF is an email authentication protocol designed to combat email address forgery and spoofing by allowing administrators to specify which hosts can send emails from a domain.
- SPF record types use TXT records to specify authorized sending hosts, and example SPF record includes declaration of version, authorized IPs, and handling of non-listed senders.
- Receiving mail servers verify SPF by checking the domain's SPF policy, parsing SPF mechanisms, and evaluating the sender's IP address based on these mechanisms to accept or reject the email.
- While SPF is a fundamental way to combat impersonation, it is recommended to use SPF in conjunction with DKIM and DMARC for enhanced email security and to regularly monitor and update SPF records for a robust email ecosystem.
Read Full Article
Like
Cybersecurity-Insiders
109

Image Credit: Cybersecurity-Insiders
Recent Evolution of Browser-based Cyber Threats, and What to Expect Next
- In 2024, browser security faced advanced cyber threats as enterprises transitioned to remote work, SaaS platforms, and BYOD policies.
- AI-powered attacks, abusive cloud hosting services, Phishing-as-a-Service, and zero-day vulnerabilities are key concerns.
- Menlo Security's report shows a significant surge in browser-based attacks using AI and sophisticated methods.
- Browser vulnerabilities are exploited for data theft, with a 140% increase in phishing attacks and 130% rise in zero-hour incidents.
- Traditional security tools struggle against techniques like obfuscation and fileless malware.
- Cloud services are targeted for hosting malicious content, with AWS and CloudFlare accounting for a high percentage of abuse.
- Ransomware attacks will increase, targeting critical sectors, while AI-driven deepfakes will aid in bypassing security tools.
- Smaller businesses will be more vulnerable to cyber threats due to limited resources, while IoT devices will face rising risks.
- Insider threats will escalate in remote work environments, necessitating advanced tools for detection and mitigation.
- Organizations should prioritize browser security, adopt strong measures, and leverage innovative tools for defense.
Read Full Article
6 Likes
Cybersecurity-Insiders
215

Image Credit: Cybersecurity-Insiders
Ransomware’s Next Target: Strengthening Critical Infrastructure Against Emerging Cyber Threats
- Ransomware poses a growing threat to critical infrastructure, with over 66% of US organizations experiencing attacks in the past year.
- Exploiting vulnerabilities in security practices and systems, ransomware targets sectors like energy, transportation, and healthcare.
- Legacy systems in energy and healthcare sectors make them vulnerable to ransomware attacks, resulting in significant financial costs and service disruptions.
- Ransomware tactics have evolved to include sophisticated operations, using AI and ML for automation and maximizing damage.
- Proactive defense strategies such as Zero Trust Architecture and AI-powered threat detection are crucial in combating ransomware.
- Quantum computing poses a future threat to cybersecurity, prompting the need for post-quantum cryptography and security measures.
- Organizations must focus on cyber resilience by planning for operations during attacks, testing backup systems, and implementing network segmentation.
- Collaboration between governments, industries, and cybersecurity firms is essential to establish cybersecurity standards and innovative defense solutions.
- A multi-layered approach combining proactive defense, cyber resilience, and quantum security preparation is key to protecting critical infrastructure.
- Continuous vigilance, adaptation to new attack methods, and security integration at every stage of design are crucial in staying ahead of cyber threats.
Read Full Article
12 Likes
For uninterrupted reading, download the app