Cyber Security News
Dev
338

Image Credit: Dev
Another security patch. Another missed opportunity.
- Many systems today are designed to operate without verifying user authentication, leaving them vulnerable to exploits and breaches.
- The recent zero-day vulnerability in Fortinet's system highlights the ongoing issue of systems having unchecked authority over sensitive data.
- Historical vulnerabilities in Fortinet's systems have showcased the risk of having 'login-optional' bugs that allow unauthorized access.
- Proposing a shift from 'access control' to 'authority control' to enhance security measures and prevent unauthorized access to sensitive data.
Read Full Article
20 Likes
Medium
389
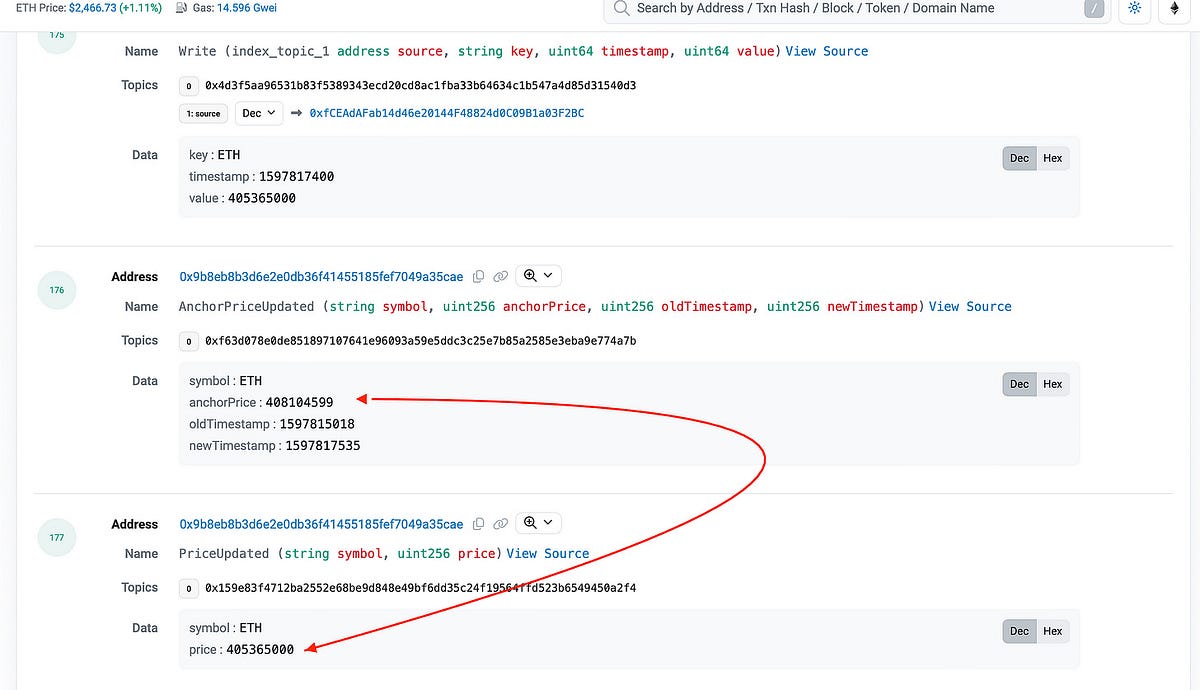
Image Credit: Medium
DeFi Summer: The Golden Days of Liquidation
- A new liquidation bot, address 0x8329F4, has been dominating the Compound v2 battlefield by winning liquidations consistently despite not being the fastest or most efficient.
- This successful performance by the new liquidator started after Compound introduced the Open Price Feed Proposal on August 20, 2020, aiming to increase transparency in asset price updates and community participation.
- The liquidator manipulated the system by posting prices and exploiting the protocol mechanics, ultimately using GasToken2 to increase profits by executing the liquidation in one atomic transaction.
- This incident showcases how understanding and leveraging protocol mechanics in DeFi can be more important than speed or gas optimization, ultimately leading to successful operations within the system.
Read Full Article
23 Likes
Cybersecurity-Insiders
444

Image Credit: Cybersecurity-Insiders
How a Turing Test Can Curb AI-Based Cyber Attacks
- AI has revolutionized industries but also poses a threat in cybersecurity through AI-driven attacks, leading to an arms race between cyber professionals and criminals.
- The Turing Test, designed by Alan Turing, could help mitigate AI-driven cyber threats by assessing machine behavior indistinguishable from humans.
- AI-powered cyber attacks automate processes, bypass traditional defenses, and create realistic attacks using NLP, making them faster and more scalable.
- Using the Turing Test in cybersecurity could involve bot detection through human-machine interaction, advanced behavioral analytics, and real-time adaptation.
- Challenges include the increasing sophistication of AI mimicking human behavior and the risk of false positives in security measures.
- Implementing human-like challenges in MFA processes, using deception technology, and analyzing attacker responses are ways to utilize the Turing Test in cybersecurity.
- Adopting AI-driven strategies like the Turing Test can enhance cybersecurity defenses against AI-powered attacks, requiring a shift in traditional security paradigms.
Read Full Article
26 Likes
Cybersecurity-Insiders
384

Image Credit: Cybersecurity-Insiders
UK Cyber Crime takes a new turn towards TV show the Blacklist
- Cybercriminals in the UK are now targeting retailers, drawing inspiration from the TV show The Blacklist and using similar names for their groups.
- Ransomware gangs like DragonForce are increasingly sophisticated, demanding ransom and selling stolen data on the dark web, leading to financial losses for companies and CEOs.
- NHS England is urging companies to bolster cybersecurity defenses, particularly as threats from groups like DragonForce pose multi-strike risks to public and private entities.
- The Co-Op experienced digital disruptions initially denied as a cyberattack, highlighting the need for enhanced cybersecurity measures amidst evolving ransomware threats.
Read Full Article
23 Likes
Dev
9

Image Credit: Dev
The Sender Policy Framework: Bare Bone Essentials
- SPF is an email authentication protocol designed to combat email address forgery and spoofing by allowing administrators to specify which hosts can send emails from a domain.
- SPF record types use TXT records to specify authorized sending hosts, and example SPF record includes declaration of version, authorized IPs, and handling of non-listed senders.
- Receiving mail servers verify SPF by checking the domain's SPF policy, parsing SPF mechanisms, and evaluating the sender's IP address based on these mechanisms to accept or reject the email.
- While SPF is a fundamental way to combat impersonation, it is recommended to use SPF in conjunction with DKIM and DMARC for enhanced email security and to regularly monitor and update SPF records for a robust email ecosystem.
Read Full Article
Like
Cybersecurity-Insiders
109

Image Credit: Cybersecurity-Insiders
Recent Evolution of Browser-based Cyber Threats, and What to Expect Next
- In 2024, browser security faced advanced cyber threats as enterprises transitioned to remote work, SaaS platforms, and BYOD policies.
- AI-powered attacks, abusive cloud hosting services, Phishing-as-a-Service, and zero-day vulnerabilities are key concerns.
- Menlo Security's report shows a significant surge in browser-based attacks using AI and sophisticated methods.
- Browser vulnerabilities are exploited for data theft, with a 140% increase in phishing attacks and 130% rise in zero-hour incidents.
- Traditional security tools struggle against techniques like obfuscation and fileless malware.
- Cloud services are targeted for hosting malicious content, with AWS and CloudFlare accounting for a high percentage of abuse.
- Ransomware attacks will increase, targeting critical sectors, while AI-driven deepfakes will aid in bypassing security tools.
- Smaller businesses will be more vulnerable to cyber threats due to limited resources, while IoT devices will face rising risks.
- Insider threats will escalate in remote work environments, necessitating advanced tools for detection and mitigation.
- Organizations should prioritize browser security, adopt strong measures, and leverage innovative tools for defense.
Read Full Article
6 Likes
Cybersecurity-Insiders
215

Image Credit: Cybersecurity-Insiders
Ransomware’s Next Target: Strengthening Critical Infrastructure Against Emerging Cyber Threats
- Ransomware poses a growing threat to critical infrastructure, with over 66% of US organizations experiencing attacks in the past year.
- Exploiting vulnerabilities in security practices and systems, ransomware targets sectors like energy, transportation, and healthcare.
- Legacy systems in energy and healthcare sectors make them vulnerable to ransomware attacks, resulting in significant financial costs and service disruptions.
- Ransomware tactics have evolved to include sophisticated operations, using AI and ML for automation and maximizing damage.
- Proactive defense strategies such as Zero Trust Architecture and AI-powered threat detection are crucial in combating ransomware.
- Quantum computing poses a future threat to cybersecurity, prompting the need for post-quantum cryptography and security measures.
- Organizations must focus on cyber resilience by planning for operations during attacks, testing backup systems, and implementing network segmentation.
- Collaboration between governments, industries, and cybersecurity firms is essential to establish cybersecurity standards and innovative defense solutions.
- A multi-layered approach combining proactive defense, cyber resilience, and quantum security preparation is key to protecting critical infrastructure.
- Continuous vigilance, adaptation to new attack methods, and security integration at every stage of design are crucial in staying ahead of cyber threats.
Read Full Article
12 Likes
Dev
393

Image Credit: Dev
Detecting SSH Brute Force Attacks with Python: Building a Simple Monitor
- Brute force SSH attacks pose a common threat to internet-exposed servers by guessing login credentials.
- Python can be used to detect brute force attacks by monitoring authentication logs and tracking failed login attempts.
- Building a Python-based SSH brute force monitor strengthens Python skills and understanding of security threats.
- Monitoring SSH authentication logs helps detect abuse patterns like multiple failed login attempts from the same IP.
- Python scripts can analyze log files, extract relevant information using regular expressions, and track failed attempts.
- The monitoring logic involves identifying failed login entries, counting attempts per IP, and flagging suspicious activity.
- Enhancements to the monitor can include features like GeoIP lookup, whitelisting, firewall integration, and email alerts.
- By adding features like time window tracking, concurrency, and success correlation, the monitor becomes more powerful.
- Understanding attack origin, tactics, and frequency is key to improving response strategies against brute force attacks.
- Building an SSH brute force monitor is a valuable project to enhance Python skills and gain practical cybersecurity experience.
Read Full Article
23 Likes
Dev
13

Image Credit: Dev
OWASP® Cornucopia 2.2 & Copi - A Game Engine for OWASP® Cornucopia Threat Modeling
- Grant Ongers bet a dinner at a vegan restaurant that Toby Irvine couldn't build an online game engine based on the game Cornucopia over a weekend.
- Copi, built with Elixir and Phoenix, now has almost 10,000 monthly users, and it is hosted on OWASP® Foundation's Fly.io account.
- OWASP Cornucopia 2.2 has been released, and Copi is available for deployment on Heroku.com or Fly.io with recommendations to use Fly.io.
- dotNET lab OWASP Cornucopia decks now have QR codes linking to the latest version, and OWASP 2025 Global AppSec EU will feature a demo lab for learning to play OWASP Cornucopia.
Read Full Article
Like
Dev
288

Image Credit: Dev
Exploring Security Risks and Vulnerabilities in Model Context Protocol (MCP): The Emerging Challenge for AI Systems
- The article delves into the security risks and vulnerabilities present in the Model Context Protocol (MCP) within AI systems.
- MCP is highlighted as a potential security nightmare lacking standardized security frameworks, concerning large enterprises for data breaches.
- Various historical software vulnerabilities are compared to potential threats in MCP, such as malicious packages, web scams, and containerization chaos.
- MCP's user-facing nature broadens the attack surface, posing significant security concerns due to its powerful functionality and rapid adoption rate.
- The precarious code quality of many MCP servers is criticized for being 'vibe-coded,' lacking security measures, documentation, and proper testing.
- MCP tools' vulnerabilities are demonstrated through attacks like Shadowing, Tool Poisoning, Cross-Tool Contamination, and Token Theft in a detailed manner.
- Proposed attack vectors like Rugpull, Embedding Attacks, Malicious Code Execution, and Server Spoofing are discussed with examples in the article.
- The article suggests adopting a Zero Trust Mindset, leveraging isolation, OAuth 2.1 properly, scrutinizing the supply chain, and monitoring emerging MCP defenses for security.
- It emphasizes the need for continuous vigilance and adaptation in securing AI ecosystems due to the evolving threats and challenges in MCP security.
- The Red Queen Effect in cybersecurity is referenced to convey the continuous arms race against evolving MCP vulnerabilities, highlighting the need for persistent security measures.
- Overall, the article serves as a cautionary stance on the emerging security challenges and vulnerabilities in MCP within AI systems, urging proactive security practices.
Read Full Article
17 Likes
Pymnts
105

Image Credit: Pymnts
Crypto Firms Grapple With Bank-Like Risks, Without the Regulation
- Crypto firms are facing bank-like risks without the regulation, leading to concerns about security vulnerabilities and potential breaches.
- Recent incidents, such as the breach at Coinbase, highlight the risks associated with centralized crypto platforms holding vast amounts of customer data and assets.
- Centralized crypto firms now handle money, identity, and financial services, amplifying the need for robust security measures and regulations.
- Exchanges like Coinbase, Binance, and Kraken are at risk of social engineering attacks targeting employees and customer data.
- Coinbase projected a cost of up to $400 million due to the recent breach and vowed to reimburse affected customers who sent funds to criminals.
- Rapidly growing FinTechs and crypto firms face challenges in scaling their security programs, particularly in regulatory gray areas.
- The breach at Coinbase exposed the vulnerability of centralized data storage, highlighting the need for enhanced security protocols.
- As crypto firms evolve, they are resembling traditional banks in terms of services offered but lack the same regulatory oversight and security standards.
- The concept of concentration of risk looms large as exchanges and custodians centralize critical functions, making them prime targets for cyberattacks.
- Security experts emphasize the importance of addressing architectural issues in the crypto market to prevent severe attacks from threatening this growing asset class.
Read Full Article
6 Likes
Dev
41

Image Credit: Dev
Building Scalable and Secure IT Infrastructure for Small and Medium Enterprises (SMEs)
- Small and Medium Enterprises (SMEs) encounter challenges in building scalable and secure IT infrastructure due to limited resources.
- Understanding the business's IT needs is crucial before beginning the infrastructure development.
- Starting with a cloud-based solution offers scalability and cost-efficiency without upfront hardware investments.
- Security should be a priority from the outset, including encryption, strong password policies, and regular software updates.
- Virtualization optimizes resources by running multiple virtual machines on a single server, reducing hardware costs.
- Building a robust network with scalability in mind is essential for internal operations and client interactions.
- Automation tools like AWS CloudFormation and Ansible help SMEs stay efficient and reduce human error.
- Compliance with data protection regulations such as GDPR, CCPA, or HIPAA is crucial for SMEs handling sensitive customer data.
- Focusing on cloud-based solutions, security, virtualization, network efficiency, and compliance can help SMEs establish a secure IT foundation.
- By adapting these strategies and prioritizing security, SMEs can effectively grow and thrive in the digital business landscape.
Read Full Article
2 Likes
Wired
219

Image Credit: Wired
Trump Signs Controversial Law Targeting Nonconsensual Sexual Content
- US President Donald Trump signed the Take It Down Act into law, requiring platforms to remove nonconsensual intimate visual content within 48 hours.
- Tech giants like Google and Microsoft support the law, which will be enforced by the Federal Trade Commission.
- Critics worry about potential misuse of the law to censor online content and lack of penalties for bad faith requests.
- The Take It Down Act resembles the Digital Millennium Copyright Act but lacks deterrence for abuse and an appeals process for removal decisions.
- There are concerns that the 48-hour deadline for content removal may lead to overcensorship by tech companies.
- Google and other tech firms express concerns about the accuracy of content removal requests under the new law.
- Some advocates argue that platforms should verify the identity of requestors to ensure legitimacy in removal requests.
- Critics fear that burdensome removal processes could attract FTC scrutiny and impact companies.
- Senators Ted Cruz and Amy Klobuchar, who supported the law, did not respond to concerns raised about its implications.
- The Take It Down Act's aim to protect individuals, particularly victims of nonconsensual intimate imagery, emphasizes the importance of swift action.
Read Full Article
13 Likes
VentureBeat
380

Image Credit: VentureBeat
Microsoft just launched an AI that discovered a new chemical in 200 hours instead of years
- Microsoft has launched a new enterprise platform called Microsoft Discovery that utilizes artificial intelligence to expedite scientific research and development.
- Microsoft Discovery employs AI agents and high-performance computing to facilitate research tasks without necessitating coding skills.
- The platform significantly accelerated the discovery of a novel coolant for data center cooling, a process that typically takes months or years, in just around 200 hours.
- Researchers can interact with supercomputers and complex simulations through natural language on Microsoft Discovery without the need for specialized programming knowledge.
- By democratizing advanced scientific tools, Microsoft Discovery aims to empower researchers and lower the barrier to utilizing cutting-edge research techniques.
- The platform employs a team of AI 'postdocs' to perform various scientific tasks, from literature reviews to simulations.
- Microsoft Discovery combines foundational models for planning with specialized models trained in scientific domains like physics, chemistry, and biology.
- The platform is built on a graph-based knowledge engine that establishes relationships between data and scientific research, enabling nuanced understanding across disciplines.
- Microsoft is partnering with various industries to implement Microsoft Discovery, including GSK for medicinal chemistry and Estée Lauder for product development.
- The platform is designed with future quantum computing capabilities in mind, creating a bridge between current AI-driven discovery and upcoming quantum computing capacities.
Read Full Article
22 Likes
Securityaffairs
274

Image Credit: Securityaffairs
Mozilla fixed zero-days recently demonstrated at Pwn2Own Berlin 2025
- Mozilla addressed two critical vulnerabilities in the Firefox browser that could have been exploited to access sensitive data or achieve code execution.
- The vulnerabilities were demonstrated as zero-day flaws during the recent Pwn2Own Berlin 2025 hacking contest.
- One vulnerability, CVE-2025-4918, involved an out-of-bounds access when resolving Promise objects.
- The other vulnerability, CVE-2025-4919, pertained to an out-of-bounds access when optimizing linear sums.
Read Full Article
16 Likes
For uninterrupted reading, download the app