Cyber Security News
Securityaffairs
325

Image Credit: Securityaffairs
James Comey is under investigation by Secret Service for a seashell photo showing “8647”
- Former FBI chief James Comey is under investigation by the Secret Service for sharing an image of seashells arranged to display the numbers ‘8647,’ which some interpret as incitement to violence against Trump.
- The post on Instagram was later deleted, and the Secret Service is investigating the matter.
- The number '86' is slang for 'to reject' or 'to get rid of', and '47' is likely a reference to Trump being the 47th US president.
- Comey claims he did not know what the numbers meant and removed the post, stating he opposes violence.
Read Full Article
19 Likes
Securityaffairs
275

Image Credit: Securityaffairs
Pwn2Own Berlin 2025: total prize money reached $1,078,750
- Pwn2Own Berlin 2025 total prize money reached $1,078,750 over three days, with $383,750 awarded on the final day.
- Participants demonstrated 28 unique zero-days in products such as VMware Workstation, ESXi, Windows, NVIDIA, and Firefox, earning a total of $1,078,750, including 7 in the AI category.
- STAR Labs SG won the 'Master of Pwn' title with $320,000 and 35 points.
- Various participants exploited vulnerabilities, with exploits including a zero-day in ESXi earning $112,500, a heap-based buffer overflow in VMware Workstation earning $80,000, and a TOCTOU race condition in Windows earning $70,000.
Read Full Article
16 Likes
Hackernoon
412

Image Credit: Hackernoon
The Complete Guide to Crafting Security Headlines That Cut Through the Noise
- Crafting security headlines that stand out is essential to capture the attention of busy and skeptical security professionals.
- Your blog title is crucial as it is often the first impression readers get and determines if they click through.
- To create effective titles, focus on promising value, showing relevance, being clear, and reflecting the article's tone.
- Understand your cybersecurity audience, which includes a wide range of professionals like penetration testers and CISOs.
- Use proven title formats like 'How to,' listicles, 'X vs Y,' question-based, myth-busting, and explainer titles.
- Real-world examples, warning headings, career and learning topics, and tool-focused titles are also effective in cybersecurity.
- Additional tips include being specific, avoiding jargon, using natural keywords, and not resorting to clickbait.
- Testing alternate headlines and using a checklist before publishing can help refine and improve your blog titles.
- Remember that a good blog title should be clear, engaging, and honest in communicating the value of the content.
- Start with multiple potential titles, test them, edit them, and always keep the reader in mind when crafting security headlines.
Read Full Article
24 Likes
Hackernoon
394

Image Credit: Hackernoon
Your Next Data Breach Might Start with a Friendly Face
- Insider threats, whether malicious, negligent, or compromised, pose financial, reputational, and legal risks to companies.
- The most common insider threats include loss of confidential data, sabotage and system damage, phishing and credential leaks, and reputational damage.
- Prevention measures include restricting access, using Data Loss Prevention tools, implementing activity monitoring, and training staff regularly on cybersecurity best practices.
- By adopting intelligent tools, strict policies, and a security-aware culture, organizations can effectively mitigate insider threats and prevent costly consequences.
Read Full Article
23 Likes
Hackernoon
165
Image Credit: Hackernoon
IPinfo’s Free IP Geolocation API Is a Must-Have for Cybersecurity Teams
- IPinfo provides IP geolocation information which is crucial for cybersecurity teams to monitor suspicious traffic, log analysis, and OSINT.
- Their new free plan offers unlimited country-level IP geolocation and ASN data, making it beneficial for cybersecurity professionals and developers.
- Users can easily get started with IPinfo's API by signing up for a free account, obtaining an API key, and making API calls to retrieve IP information.
- IPinfo not only offers an API but also tools like a Command-Line Tool, Browser Extension, Bulk IP Lookup, and Python SDK for various cybersecurity use cases.
Read Full Article
9 Likes
Hackernoon
316

Image Credit: Hackernoon
MCP Servers Still Run Critical Infrastructure—Here’s How to Secure Them
- MCP (Master Control Program) servers, used in high-reliability applications, are crucial for industries but often overlooked in cybersecurity.
- The Vulnerable MCP Project serves as a teaching tool to highlight security risks in MCP environments and train professionals to protect legacy systems.
- Securing MCP servers is essential for compliance, uptime, and preventing data breaches in industries like finance and healthcare.
- Common vulnerabilities in MCP servers include insecure authentication, obsolete encryption protocols, hardcoded admin credentials, lack of monitoring, unpatched software, and no RBAC.
- Recommendations for securing MCP systems include implementing strong password policies, upgrading encryption protocols, using secrets management tools, logging and monitoring, regular patching, and enforcing RBAC.
- Tools like port scanners, vulnerability scanners, SSH hardening, and network segmentation can help in securing MCP servers.
- Real-world application examples include how a bank could secure its MCP system by auditing user accounts, enabling logging, shifting credentials to a secrets manager, testing patches, and conducting personnel training.
- To practice securing MCP servers, individuals can download the Vulnerable MCP Project, set it up in a sandboxed lab, and use tools like Wireshark, Metasploit, and OSINT tools in a controlled environment.
- Key takeaways include the importance of securing MCP servers, the neglect of legacy systems in security planning, the value of the Vulnerable MCP Project for hands-on learning, and the need for a mix of modern security practices and legacy-specific measures.
- While new technologies are essential, securing old systems like MCP is equally crucial, and projects like the Vulnerable MCP Project play a significant role in educating and securing these systems.
Read Full Article
19 Likes
Cybersecurity-Insiders
91

Image Credit: Cybersecurity-Insiders
SafeLine WAF: Best Security Choice for Small Businesses
- SafeLine WAF is a web application firewall designed to protect websites from various attacks like SQL injections, XSS, and zero-day attacks, utilizing a semantic analysis engine for advanced threat detection.
- Key features of SafeLine WAF include semantic analysis for threat detection, bot protection, HTTP flood DDoS protection, identity and access management, customizable security rules, and user-friendly setup and management.
- SafeLine WAF stands out due to its affordability, with options like a free edition for personal use, a Lite edition for $10 per month, and a Pro edition for $100 per month, making it accessible for small businesses and individuals.
- SafeLine WAF offers a comprehensive security solution that combines effective protection against cyber threats with user-friendly features and affordable pricing, making it an ideal choice for small businesses looking for powerful website security.
Read Full Article
5 Likes
Damienbod
302
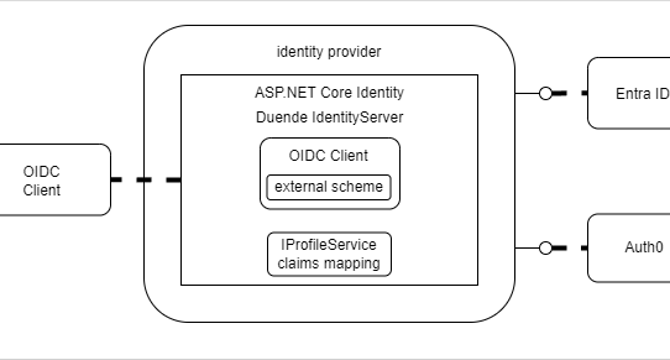
Image Credit: Damienbod
Using multiple external identity providers from ASP.NET Core Identity and Duende IdentityServer
- This blog post discusses integrating multiple external identity providers in ASP.NET Core Identity applications using Duende IdentityServer.
- The application acts as an identity provider for local and external users, handling claims mapping for each external authentication provider.
- Using Duende allows for robust OAuth and OpenID Connect authentication flows not supported by some other providers.
- Each external provider implements a separate scheme for the OpenID Connect flow, with options for shared or unique schemes.
- The article showcases how to configure external providers like Auth0 and EntraID using OpenID Connect in ASP.NET Core Identity.
- When using Microsoft.Identity.Web, a separate scheme is necessary for callback and logout handling.
- Claims mapping from external providers back to UI applications can be managed using Duende's IProfileService.
- For ASP.NET Core Identity-only solutions, claims transformation can be utilized for mapping claims.
- References to Duende IdentityServer documentation, Microsoft ASP.NET Core Identity guides, and sample code repositories are provided.
Read Full Article
18 Likes
Cryptonews
247

Binance and Kraken Thwart Social-Engineering Attacks Mirroring Coinbase Breach
- Binance and Kraken successfully blocked social-engineering attacks similar to the recent Coinbase breach.
- Coinbase faced potential losses of up to US$400M due to exposure of sensitive customer data after a failed extortion attempt of US$20M.
- The rise in scams and hacks in the crypto industry is attributed to the bullish market, prompting increased security measures and personnel spending.
- Cyber threats on crypto platforms have intensified amid rising asset prices, with Binance employing AI-powered bots to detect and prevent bribery attempts from scammers.
Read Full Article
14 Likes
Siliconangle
357

Image Credit: Siliconangle
JFrog and Nvidia partner on secure software supply chain for Enterprise AI Factory
- JFrog partners with Nvidia to power enterprise artificial intelligence with a focus on secure software supply chain.
- JFrog's platform will serve as the central software artifact repository and secure model registry within Nvidia's Enterprise AI Factory.
- The integration allows for secure visibility, governance, and management of software components including machine learning models and engines.
- The joint solution aims to enable rapid and trusted provisioning of AI and machine applications with full support for Nvidia's architecture.
Read Full Article
21 Likes
Cybersecurity-Insiders
128

Image Credit: Cybersecurity-Insiders
How to identify hackers sitting in a computer network
- Cybersecurity threats like advanced persistent threats (APTs) involve hackers gaining access to a computer network and remaining undetected.
- To identify hackers in a network, monitor unusual network traffic for spikes, odd activity times, and communication with unknown IPs.
- Look for abnormal user behavior like logins at odd times, accessing restricted files, or multiple failed login attempts.
- Check for new or unauthorized accounts, administrative changes, and increased privileged account activity.
- Examine unexpected software installations, like backdoors or RATs, through unknown processes or file changes.
- Watch for system slowdowns, high resource usage, or disk activity indicating malicious activities.
- Investigate disabled security alerts, altered logs, or configuration files as signs of tampering by hackers.
- Perform vulnerability scanning to identify outdated software, unpatched flaws, or misconfigured systems.
- Utilize threat intelligence feeds and collaborate with industry peers to stay ahead of cyber threats and hacker tactics.
- Vigilant monitoring, audits, and proactive security measures are crucial in detecting hackers within a network and preventing significant damage.
Read Full Article
7 Likes
Cryptonews
449

Crypto Wealth Spurs Demand for Bodyguards Amid Rising Kidnapping Threats
- A failed kidnapping attempt in Paris targeting a crypto executive’s family has raised concerns over physical threats to crypto holders.
- Private security firms are experiencing increased demand from crypto investors seeking protection services, including bodyguards.
- Firms like Circle and Robinhood are allocating millions annually for executive protection, recognizing personal security as crucial amid growing wealth exposure in the crypto industry.
- The rise in demand for private security follows incidents like the kidnapping attempt on a French crypto executive’s family and concerns over data leaks that have put wealthy holders at risk.
Read Full Article
27 Likes
Cybersecurity-Insiders
46

Image Credit: Cybersecurity-Insiders
Scam Messages and emails increase exponentially after M & S Cyber Attack
- A cyberattack on Marks and Spencer compromised personal data of nearly 9.4 million customers, exploiting a vulnerability created by human error.
- Hackers accessed sensitive information including order histories, dates of birth, and partial payment card details, but not complete card data.
- M&S reassured customers that full payment card details were not accessed due to limited data storage, with potential impact on online ordering.
- Increase in scam messages and emails reported by customers following the cyberattack, urging vigilance against potential spam campaigns using stolen information.
Read Full Article
2 Likes
Cybersecurity-Insiders
192

Image Credit: Cybersecurity-Insiders
Experts React: Coinbase Discloses Breach, Faces Up to $400 Million in Losses
- Coinbase, a major cryptocurrency exchange, has revealed a significant data breach exposing sensitive customer information, with attackers demanding a $20 million ransom.
- The breach could result in losses up to $400 million, considering regulatory fines, legal actions, and customer compensation, prompting an internal investigation by Coinbase and cooperation with law enforcement.
- Implications of the breach include risks for crypto users facing identity theft and phishing attacks, potential stock price volatility for investors, regulatory scrutiny, cybersecurity upgrades for Coinbase, and brand damage impacting revenue growth.
- Experts highlighted the growing challenge of protecting customer data in digital ecosystems, emphasizing the need for robust cybersecurity measures to safeguard sensitive information.
Read Full Article
11 Likes
Dev
160

Image Credit: Dev
Effortless Token Refresh in React Using Axios Interceptors
- Token rotation is a method to automatically refresh expired access tokens using a refresh token, providing a seamless user experience and enhanced security.
- Axios interceptors enable the implementation of token rotation in a React app by automatically fetching a new token when the access token expires without users noticing.
- The step-by-step example demonstrates how to handle token expiration and rotation using Axios interceptors in a React app, ensuring users stay logged in securely.
- Different token storage options like Local Storage, Session Storage, and HttpOnly Cookies are compared in terms of security and persistence, helping developers choose the most suitable option for their projects.
Read Full Article
9 Likes
For uninterrupted reading, download the app