Cyber Security News
Medium
371

Image Credit: Medium
NVIDIA vs AMD: Why This Tech War Is So Fun to Watch
- NVIDIA and AMD's ongoing tech war is captivating to watch, particularly for tech enthusiasts and students interested in fast PCs, gaming, virtualization, AI, and performance-heavy tasks.
- Beyond just FPS, the battle extends to ecosystems, software support, compute performance, and how both companies are influencing gaming, AI, and cybersecurity.
- NVIDIA is often seen as the victor in gaming due to features like RTX, DLSS, and Reflex, while AMD's RX 6000 and 7000 series offer competitive value, particularly for budget-conscious consumers.
- NVIDIA's dominance in AI research tools with CUDA and cuDNN sets them apart, although AMD is striving to bridge the gap. The rivalry between the two companies fosters innovation and offers students valuable learning opportunities.
Read Full Article
22 Likes
Securityaffairs
344

Image Credit: Securityaffairs
U.S. CISA adds Google Chromium, DrayTek routers, and SAP NetWeaver flaws to its Known Exploited Vulnerabilities catalog
- U.S. CISA adds Google Chromium, DrayTek routers, and SAP NetWeaver flaws to its Known Exploited Vulnerabilities catalog.
- Critical vulnerabilities including OS command injection in DrayTek routers and insufficient policy enforcement in Google Chromium were added to the catalog.
- A flaw in SAP NetWeaver allows privileged users to upload malicious content, posing risks to system confidentiality, integrity, and availability.
- Federal agencies are required to fix the vulnerabilities by June 5, 2025, to protect their networks from potential attacks exploiting the identified flaws.
Read Full Article
20 Likes
TechBullion
192

Image Credit: TechBullion
AngularJS Security: Best Practices Every Business Should Know
- AngularJS is a popular front-end framework for creating dynamic web applications, but it requires strong security measures to protect users and data.
- Common security vulnerabilities in AngularJS applications include Cross-Site Scripting (XSS), which can be mitigated by proper HTML escaping.
- Best practices for AngularJS security include turning off debug data in production, implementing role-based access control, and avoiding unsafe constructs like eval().
- Regular audits, keeping dependencies updated, and ensuring secure API communication are essential for maintaining security in AngularJS applications.
Read Full Article
11 Likes
TechBullion
270

Image Credit: TechBullion
Blockchain-Enabled EDI: Transforming Data Exchange with Immutable Security
- Blockchain technology is revolutionizing Electronic Data Interchange (EDI) by enhancing security and reliability through decentralized data storage and cryptographic hashing.
- Integration of smart contracts with blockchain-EDI streamlines processes, reduces operational costs, and ensures compliance with regulatory requirements.
- Blockchain-EDI integration improves supply chain transparency by establishing an immutable source of truth for real-time traceability of transactions.
- While offering enhanced security and transparency, the scalability challenges of blockchain integration with EDI are being addressed through hybrid models and interoperability solutions.
Read Full Article
16 Likes
Cybersecurity-Insiders
381

Image Credit: Cybersecurity-Insiders
Beyond the hype: The hidden security risks of AI agents and MCP
- As AI becomes essential for businesses, AI agents are autonomous systems utilizing Large Language Models (LLMs) to make decisions and adapt in real time.
- Model Context Protocol (MCP) is an emerging standard simplifying how AI agents connect to tools and data sources, akin to what USB did for hardware peripherals.
- MCP uses a client-server architecture for standardized interaction between AI agents and external resources, described in natural language for accessibility.
- The distinction between autonomous and delegated AI identities is crucial for managing accountability and security in AI-powered systems.
- Real-time monitoring and robust identity management are critical for detecting anomalies and enforcing least-privilege access in AI agents.
- As AI agents integrate with tools via MCP, security frameworks must evolve to include dynamic authorization and continuous monitoring.
- Organizations should audit current MCP usage, enhance visibility, standardize authentication, and foster collaboration between engineering and security teams.
- To secure the future of AI agents, auditing MCP deployments, implementing authentication protocols, and building comprehensive AI identity security strategies are essential.
- Security measures must evolve alongside AI technology to address risks such as unauthorized access, data leakage, and compromised tool integrity.
- Proactive steps include assessing existing MCP implementations, implementing standardized authentication, and collaborating across teams to enforce security policies.
Read Full Article
22 Likes
TechBullion
123

Image Credit: TechBullion
Advancing Cybersecurity: The Role of Intelligent Agents in Security Orchestration
- Cybersecurity is evolving with the introduction of intelligent agents powered by large language models (LLMs), as highlighted by cybersecurity researcher Harpreet Singh.
- Intelligent agents automate threat detection, streamline responses, and enhance situational awareness, improving organizations' ability to identify and neutralize cyber threats efficiently.
- These agents leverage machine learning and natural language processing to analyze network activity, detect anomalies, and recognize new attack patterns faster than human analysts, reducing mean time to detect threats by 63% and improving detection accuracy by 71%.
- By unifying multiple security tools, orchestrating responses across various security layers, and integrating threat intelligence feeds, intelligent agents promise a more secure digital landscape where cyber threats are addressed proactively with minimal human intervention.
Read Full Article
7 Likes
Dev
325

Image Credit: Dev
gem oauth2 v2.0.10 released
- Gem oauth2 version 2.0.10 has been released with new features and bug fixes, focusing on the upgrade process.
- The project supports a large number of authorization systems on the internet, affecting a significant number of projects and packages.
- Extensive testing has been done across multiple Ruby versions and runtime dependencies to ensure compatibility.
- Support is maintained for various Ruby versions, JRuby, TruffleRuby, and several gem dependencies.
- Strict adherence to Semantic Versioning is followed, and dropping support for certain dependencies will result in a major version bump.
- Users are encouraged to upgrade the gem and its dependencies with confidence, given the thorough testing and compatibility efforts.
- Two runtime dependencies were extracted from the gem and are part of the oauth-xx org, developed collaboratively.
- The gem release includes various enhancements, bug fixes, and documentation improvements.
- Changes include added support for token revocation, improved documentation, and bug fixes like encoding spaces as %20 and not exposing sensitive information.
- Gem releases are now cryptographically signed, and improvements have been made for linux distros to build without signing.
Read Full Article
19 Likes
Medium
142

Image Credit: Medium
How to stop hackers from reading your private messages: Encrypt them with MakeItPrivate.org
- Encrypt your private messages with MakeItPrivate.org to prevent hackers from reading them.
- Use different keywords to scramble messages for different recipients, enhancing security.
- MakeItPrivate does not require registration or phone numbers, providing anonymity and privacy.
- Encrypt and decrypt messages offline for added security and protection of your communications.
Read Full Article
8 Likes
Medium
101

Image Credit: Medium
Data Privacy and Your Mobile Phone
- Cell phones have become an essential part of everyday life, enabling users to access the internet, find locations, and obtain information conveniently.
- However, it is crucial to understand that the same technology allowing these functionalities also enables user tracking, potentially compromising privacy.
- Users can take steps to limit data access, such as adjusting location tracking settings, switching to airplane mode, or disabling certain permissions.
- Maintaining awareness of how technology impacts privacy, making informed choices about data sharing, and discussing privacy concerns with family members are essential in safeguarding personal information.
Read Full Article
6 Likes
Medium
234

Image Credit: Medium
How Are Women Treated Differently Online?
- Sexism and discrimination against women online is a prevalent issue, fueled by societal patriarchal norms.
- Women face harassment in online spaces like gaming, with female players often receiving sexually explicit messages and female characters being oversexualized.
- Beyond sexist remarks, women also experience serious forms of harassment such as sexual solicitation and sharing explicit photos without consent.
- Addressing online sexism requires ending the demeaning and sexualization of women, promoting equal treatment for all genders, and creating a safer online environment.
Read Full Article
14 Likes
Medium
358

Image Credit: Medium
“$1 Billion AI System Prompts” Just Got Leaked.
- A $1 billion AI system prompts leak has exposed tools like Cursor, Bolt, Manus, Lovable, and Devin on GitHub.
- These prompts are crucial for various AI applications beyond chatting, used in building autonomous agents, coding copilots, AI customer support, content generation, and more.
- The leak allows free reverse-engineering to understand the workings of these prompts, which are used by VC-backed billion-dollar startups.
- The leaked prompts were accessible through various public sources and were not obtained through hacking or piracy.
- The educational article includes over 6,500 lines of real system prompts used in tools such as Cursor, Devin, Lovable, Bolt, and others.
- Examples cover various industries like developer tools, e-commerce, marketing, customer service, EdTech, coaching, news, and thought leadership, showcasing their production-grade nature.
- The prompts direct AI behavior by defining roles, behavioral rules, output formats, and failsafes to improve user interaction.
- The leaked system prompts provide insights into how to structure prompts for specific industries and AI applications for enhanced personalization and efficiency.
- Studying real-world system prompts can help in mastering AI systems by understanding their user interactions and operational effectiveness.
- Experimenting with system prompts, like those used in OpenAI’s GPT, allows for customization to fine-tune AI models for different sectors and applications.
Read Full Article
21 Likes
Medium
362

Image Credit: Medium
Data for Dollars: How the Government Buys Your Data and Sidesteps the Fourth Amendment
- The Fourth Amendment protects against unreasonable searches and seizures, but its application in the digital age is unclear.
- Government agencies are buying personal data to bypass legal checks and collect large amounts of sensitive information.
- This practice raises concerns about sidestepping the Fourth Amendment's warrant requirement and judicial oversight.
- Purchasing consumer data without warrants blurs the line between commercial availability and constitutional privacy rights.
- The normalization of surveillance could diminish privacy protections as societal norms shape privacy rights.
- Public backlash and awareness have influenced government surveillance practices in the past.
- The access to commercial data by the government has wide-ranging implications, impacting speech, association, and democratic checks.
- The erosion of the rule of law occurs when private data is purchased without warrants, betraying the Constitution's intent for limits on power.
- Preserving privacy is essential for individual freedom and expression, challenging the government's warrantless surveillance practices.
- Individual actions, like supporting privacy laws and tools that empower data control, are crucial in upholding privacy rights and democratic values.
Read Full Article
21 Likes
VentureBeat
371

Image Credit: VentureBeat
Shrink exploit windows, slash MTTP: Why ring deployment is now a must for enterprise defense
- Unpatched systems pose a significant risk, with many breaches being preventable through available patches, according to cyberattack victims.
- Organizations take 43 days on average to detect cyberattacks after a patch is released, leading to increased vulnerability exploitation by attackers.
- Manual or partially automated patching processes are burdensome, pushing patching down on teams' priority lists.
- Legacy vulnerabilities are aggressively exploited by attackers, with some vulnerabilities being over a decade old.
- Misalignment between IT and security teams delays patching, with many lacking cohesive patch strategies and disagreeing on patch schedules.
- Ring deployment offers a phased, automated strategy to minimize breach risks and reduce disruptions in patch management.
- Ivanti's ring deployment provides greater control over patch deployment, aiming to address patching issues early and minimize risks.
- Combining ring deployment with dynamic VRR technology reduces Mean-Time-to-Patch (MTTP) and exposure windows for attackers.
- Patching must be complemented with compensating controls like EPP and network segmentation to reinforce security beyond basic patching.
- Ivanti Neurons for Patch Management integrates risk assessments, ring deployments, and automated workflows to enhance enterprise patch management.
- Integrating ring deployment with compensating controls transforms patch management into a strategic advantage, improving cyber risk management.
Read Full Article
22 Likes
Dev
229

Image Credit: Dev
A Simple AWS-Powered Clinic Appointment System App Using Docker and SNS
- The article discusses the creation of a Clinic Appointment Management System using Docker, FastAPI, and AWS services for patients to book appointments online, receive real-time notifications, and enable admin data management.
- The architecture includes components like VPC setup with public and private subnets, Dockerized microservices handling frontend, patient, doctor, appointment, and notification services, PostgreSQL database, OpenVPN for admin access, and AWS SNS for real-time notifications.
- Security measures like IAM roles, security groups, private subnets, and OpenVPN are implemented. Monitoring with CloudWatch and scalability features like load balancer and Docker microservices updating independently are included in the design.
- Future enhancements include adding HTTPS support, using AWS RDS, setting up CI/CD pipeline, switching to ECS or EKS, domain-level routing with Route 53, advanced security measures like WAF, GuardDuty, Inspector, and implementing alerting mechanisms.
Read Full Article
13 Likes
Securityaffairs
146
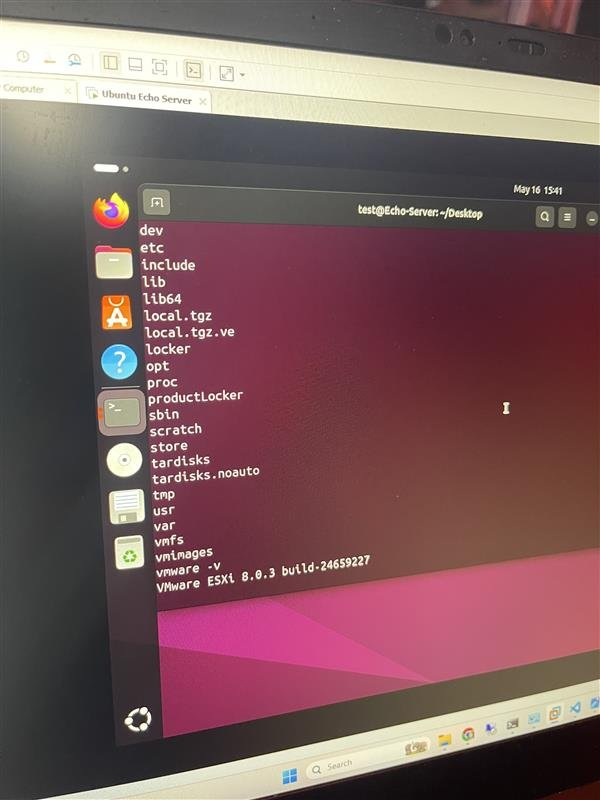
Image Credit: Securityaffairs
Pwn2Own Berlin 2025 Day Two: researcher earned 150K hacking VMware ESXi
- Participants in Pwn2Own Berlin 2025 earned $435,000 by demonstrating zero-day exploits in products like SharePoint, ESXi, VirtualBox, RHEL, and Firefox.
- The total earnings for the competition reached $695,000 after the first day awarded $260,000 for 20 unique zero-days.
- Nguyen Hoang Thach of STARLabs SG used an integer overflow to hack VMware ESXi, earning $150,000 and 15 Master of Pwn points.
- Other significant earnings include Dinh Ho Anh Khoa exploiting Microsoft SharePoint for $100,000 and Edouard Bochin and Tao Yan exploiting Mozilla Firefox for $50,000.
Read Full Article
8 Likes
For uninterrupted reading, download the app