Cyber Security News
BGR
296
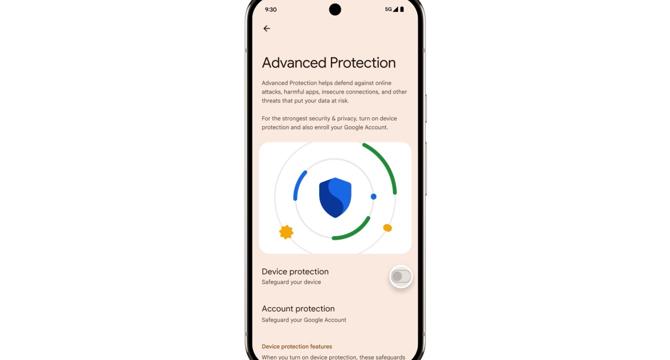
Image Credit: BGR
8 new Android 16 security features that will make your phone safer than ever
- Google announced several upgrades to Android, enhancing security for users' personal data and valuables.
- Themes of the event included Android 16 design, Gemini AI, and a focus on security, especially relevant due to increased hacking and scams using AI technology.
- New security features aim to protect against various threats, including theft, data extraction, and state-sponsored espionage targeting high-value individuals.
- These security enhancements will benefit both Android 16 devices and older versions, providing a safer user experience.
Read Full Article
17 Likes
Droid-Life
211

Image Credit: Droid-Life
Google’s Find My Device Becomes “Find Hub” Because It’s for Devices and People
- Google has rebranded its Find My Device app to Find Hub to encompass tracking for both devices and people.
- Find Hub will offer features like tracking smart devices, watches, earbuds, smart tags, as well as people, with plans to integrate satellite connectivity.
- Google will expand supported devices for Find Hub, add nearby finding capabilities through UWB and Moto Tag, and partner with airlines for luggage recovery using Bluetooth tags.
- Find Hub will also connect to satellites to enable communication with friends and family in areas with no cellular connectivity.
Read Full Article
12 Likes
TechCrunch
115

Image Credit: TechCrunch
Google announces new security features for Android for protection against scam and theft
- Google announced new security and privacy features for Android at the Android Show, including protections for calls, screen sharing, messages, device access, and system-level permissions.
- The aim is to protect users from scams, secure their details if a device is stolen, and enhance device security against various attacks.
- Actions like tapping on unsafe links or downloading unknown apps are blocked to protect users from potential scams during a call.
- New features include preventing side-loading apps from unverified sources and ensuring users cannot disable Google Play Protect while on a call.
- Google is adding screen-sharing protection and testing warning screens with select banks to prevent fraud through screen-sharing.
- Enhancements in Google Messages now include AI-based detection of various scam types and adding verification keys for encrypted conversations.
- Theft protection measures include Identity Check protection, biometric authentication for critical settings, and better protection for Factory Reset.
- Additional features include improved Google Play Protect detection, new measures for Advanced Protection Mode, and introducing Find My Hub for tracking items, friends, and family.
Read Full Article
6 Likes
TechCrunch
32
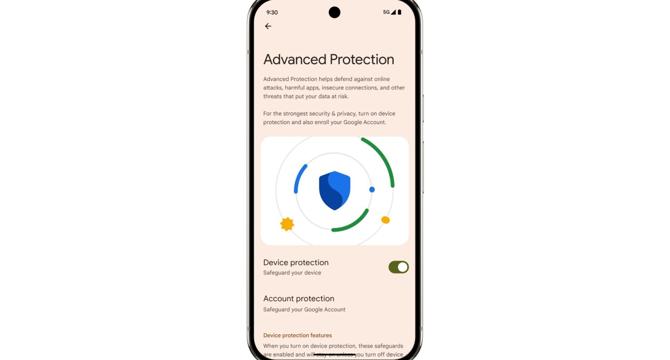
Image Credit: TechCrunch
Google is adding new device-level features for its Advanded Protection program
- Google is adding new device-specific features to its Advanced Protection program with the Android 16 release, aimed at protecting public figures from digital threats.
- The new features include storing device logs accessible only by the user, protection from spam calls, auto-restart functionality for locked devices, and intrusion logging for threat analysis.
- Additional features include USB protection that allows charging only from new USB connections, prevention of auto-reconnecting to unsecured Wi-Fi networks, and private conversation processing to detect potential scams during phone calls.
- Advanced Protection devices will automatically restart after 72 hours if locked, and the new measures are designed to enhance security for public figures and prevent device compromises.
Read Full Article
1 Like
Wired
451

Image Credit: Wired
Google Is Using On-Device AI to Spot Scam Texts and Investment Fraud
- Google is expanding its AI flagging feature, Scam Detection, to alert users about potential scams like crypto scams, financial impersonation, gift card scams, and more in the Google Messages app.
- Scammers, particularly from Chinese groups, send fraudulent messages demanding payments or personal information, leading to data theft when users click on provided links.
- AI on-device allows detection of sophisticated scams like investment or romance scams that evolve over time, where scammers build trust before exploiting victims.
- Companies like O2 and scam baiter Kitboga use AI to combat scammers, while Meta introduces pop-up warnings in chat messages for potential payments.
- F-Secure has created a tool to identify and block scam messages, aiming to reduce the success rate of scammers by adding friction to contacting unknown accounts.
- Google has seen positive impacts from using machine learning to detect scam messages in real time, with plans to expand these protections to third-party communication platforms.
- The company is testing scam detection for phone calls and aims for broader deployment in the future to combat various forms of fraudulent activities.
Read Full Article
27 Likes
The Verge
402
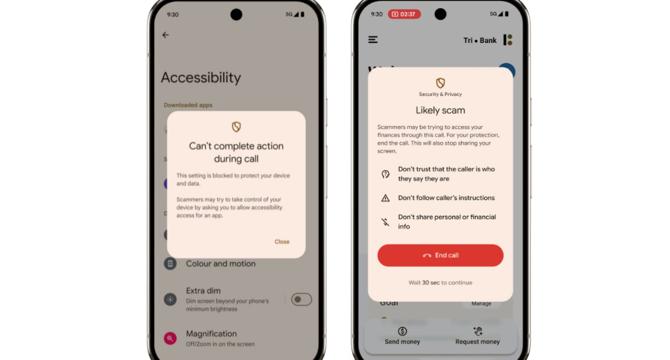
Image Credit: The Verge
Android launches new protections against phone call scammers
- Google is introducing new features on Android to protect users from phone call scams, such as automatically blocking app installations while on a call with an unknown contact.
- Android will prevent users from granting accessibility permissions to apps during phone calls to safeguard against potential device takeovers.
- A new Android feature will discourage users from opening banking apps while screen-sharing during calls to combat screen-sharing scams.
- These protections add to Android's existing scam detection tools like AI caller identification and scam detection in Google Messages for various types of scams.
Read Full Article
24 Likes
TechCrunch
42
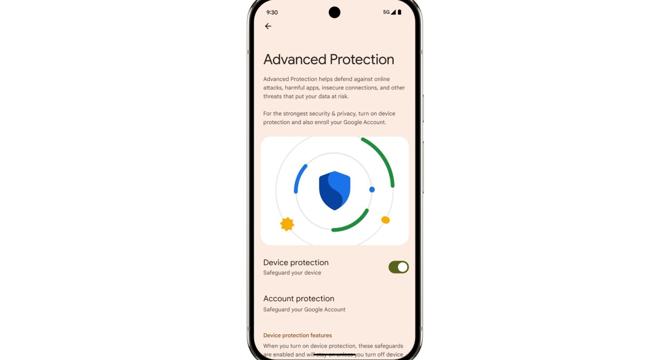
Image Credit: TechCrunch
Google is adding new device-level features for its Advanced Protection program
- Google is adding new device-specific features to its Advanced Protection program with the Android 16 release.
- The new features include storing device logs accessible only by the user, protection from spam calls, and an auto-restart feature.
- Additional security measures such as intrusion logging, USB protection, auto-restart after 72 hours, and prevention from connecting to insecure Wi-Fi networks are being implemented.
- The program will also include a feature to process conversations on the device to detect potential scams during phone calls.
Read Full Article
2 Likes
Pymnts
441

Image Credit: Pymnts
Adyen and JCB Roll out Card-on-File Tokenization Service
- Adyen partners with JCB to offer and implement card-on-file (COF) tokenization service for eCommerce merchants.
- JCB plans to implement COF tokens globally to enhance the security of credit card transactions.
- The COF tokenization service replaces sensitive card data with secure tokens, reducing the risk of data breaches.
- Tokenization offers increased convenience and improved transaction authorization rates, benefiting both customers and merchants.
Read Full Article
26 Likes
Tech Radar
55

Image Credit: Tech Radar
Co-op hackers may still be “in the system” as cyberattack disruption continues
- Co-op is facing disruptions from a cyberattack, leading to critical systems being offline and hindering restocking in some stores.
- Hackers may still have access to Co-op's networks, causing concerns about potential data breaches.
- Co-op's CEO confirmed that a limited amount of customer data was accessed by the cybercriminals, emphasizing the importance of data protection.
- The cyberattack on Co-op follows a similar incident at M&S, leading to disruptions in operations and deliveries from large depots.
Read Full Article
3 Likes
Tech Radar
400

Image Credit: Tech Radar
Browser extensions are increasing the attack surface, putting employees and businesses at risk
- Browser extensions are increasing the attack surface, putting employees and businesses at risk according to the 2025 Enterprise Browser Extension Security Report by LayerX.
- Almost all enterprises have at least one extension installed with over half running more than ten, exposing sensitive data to potential risks.
- More than half of extensions have 'high' or 'critical' risk permissions, with 53% of them allowing access to sensitive data.
- To mitigate the threats, enterprises are advised to audit all browser extensions, categorize them based on risk profiles, and analyze permissions meticulously to enforce adaptive security policies.
Read Full Article
24 Likes
TechCrunch
197

Image Credit: TechCrunch
Government email alert system GovDelivery used to send scam messages
- An email notification system used by U.S. federal and state government departments, GovDelivery, has been used to send scam emails, targeting residents with fake toll messages.
- The U.S. state of Indiana is investigating fraudulent messages concerning unpaid tolls purportedly sent by state agencies through GovDelivery, which contained disguised links to malicious sites.
- Indiana confirmed a contractor's account was hacked to send scam messages, but stated that no current state systems were compromised.
- Granicus, the company behind GovDelivery, confirmed the breach was due to a compromised user account but asserted that their systems were not breached.
Read Full Article
11 Likes
Pymnts
118

Image Credit: Pymnts
Crypto’s Institutional Future Could Hinge on Solving the Risk Puzzle
- Institutional adoption of digital assets like cryptocurrencies requires mature blockchains for institutional use.
- Risk poses a significant obstacle to the increased interest in digital assets by regulated institutions.
- The regulatory landscape for digital assets is evolving, with major financial institutions exploring stablecoins and blockchain adoption.
- To unlock the future of payments with digital assets, the industry must address the challenges of risk exposure and control.
Read Full Article
6 Likes
Cybersecurity-Insiders
290

Image Credit: Cybersecurity-Insiders
Now ransomware starts infecting Central Processing Units aka CPUs
- Ransomware is now targeting Central Processing Units (CPUs), a critical component of computing devices.
- This new form of malware infects the CPU itself, making it difficult to remove even after hardware changes.
- Malicious actors can manipulate the microcodes of a processor, potentially compromising the entire system.
- The development of CPU-targeting malware represents a significant evolution in cybercriminal tactics, posing new challenges for cybersecurity professionals.
Read Full Article
17 Likes
Tech Radar
441

Image Credit: Tech Radar
A third of enterprises have been breached despite increased cybersecurity investment
- Despite increased cybersecurity investment, a significant number of organizations have been breached, with 67% of firms experiencing a data security breach in the last 24 months.
- Nearly a third of companies have suffered a breach of data as a result of cyber attacks, leading to disruptions like unplanned downtime, breach of data, and financial losses.
- Confidence in government cybersecurity support is low, with only 14% of organizations being confident in their government's aid. US enterprises are increasing spending on penetration testing to simulate cyberattacks and identify vulnerabilities.
- The pace of changes in enterprise environments has outpaced traditional testing methods, with 96% of organizations making IT changes quarterly, but only 30% conducting penetration testing at the same frequency, highlighting the need for scalable security validation strategies.
Read Full Article
26 Likes
Unite
179

Image Credit: Unite
Jailbreaking Text-to-Video Systems with Rewritten Prompts
- Researchers have tested a method for rewriting blocked prompts in text-to-video systems to bypass safety filters without altering their meaning, exposing the frailty of current safeguards.
- Various closed-source video models aim to prevent users from generating unwanted content, but determined individuals have found ways to coerce systems into producing restricted material.
- A new collaborative effort from Singapore and China has introduced an optimization-based jailbreak method for text-to-video models, successfully tricking systems like Kling by rewriting prompts discreetly.
- The method focuses on rewriting prompts that circumvent safety filters while maintaining original meaning, achieved through an iterative optimization process with three objectives.
- The approach, tested on platforms like Pika, Luma, Kling, and Open-Sora, outperformed previous methods in breaking system safeguards, highlighting limitations in current safety filters of text-to-video models.
- The study conducted by eight researchers from various universities utilized ChatGPT-4o to rewrite prompts and bypass safety filters, showcasing the system's effectiveness in generating prompts that evade detection.
- A prompt mutation strategy was implemented to enhance consistency in bypassing filters, leading the system to select prompts that remained effective across multiple uses.
- The research methodology aimed to preserve original input meaning while bypassing safety filters, resulting in improved attack success rates and semantic alignment with the original prompts compared to baseline methods.
- Notably, Open-Sora exhibited high vulnerability to adversarial prompts, emphasizing the need for improved safety mechanisms in such open-source models to mitigate risks posed by malicious prompts.
- The method achieved higher attack success rates and maintained stronger semantic alignment with input prompts across various text-to-video models compared to baseline approaches, demonstrating its efficiency and effectiveness.
- The study emphasizes the necessity for advanced safety measures in text-to-video models and suggests that the new method balances attack success with semantic integrity, enhancing the generation of safer content.
Read Full Article
10 Likes
For uninterrupted reading, download the app