Cyber Security News
Tech Radar
13

Image Credit: Tech Radar
GlobalX airline helping Trump deportations hit by cyberattack
- GlobalX airline involved in deportations of illegal aliens from the US into El Salvador and Venezuela faced a cyberattack.
- Anonymous hacktivists attacked GlobalX's website, stating they targeted the company for deporting illegal aliens.
- GlobalX reported the cyberattack to the SEC, initiated incident response protocol, and brought in third-party experts.
- The company is investigating the breach but believes its operations were not disrupted or impacted materially.
Read Full Article
Like
Wired
9
Image Credit: Wired
An $8.4 Billion Chinese Hub for Crypto Crime Is Incorporated in Colorado
- Elliptic's research reveals a Chinese-language service on Telegram called Xinbi Guarantee, registered in the US, facilitating $8.4 billion in transactions, mostly from scam victims.
- The underground marketplace offers a range of illegal services including money laundering, sex trafficking, child-bearing surrogacy, and targeted harassment.
- Telegram took action to ban accounts related to Xinbi Guarantee and Huione Guarantee after being alerted to illicit activities.
- Huione Guarantee, a similar service, had facilitated $24 billion in transactions, leading to US Treasury's intervention.
- Xinbi Guarantee, although banned by Telegram, remains a hub for various criminal activities and services like dummy bank accounts and sex workers.
- Critically, Xinbi Guarantee was found to enable money laundering for North Korean state-sponsored cybercriminals, involving funds from cryptocurrency thefts.
- The market also offered services such as threats, feces throwing, and trafficking, with Xinbi Guarantee merchants providing illicit offerings like stolen data and scam facilitation.
- While Xinbi Guarantee was strikingly illegal, it was legally registered in the US, possibly to project legitimacy, yet its current status is marked as 'delinquent.'
- Chinese companies, legitimate or not, incorporating in the US is a tactic to establish credibility and formalize connections in the country.
- Both Xinbi Guarantee and Huione Guarantee relied heavily on Telegram for communication and Tether cryptocurrency for payments, contributing to the growth of Chinese-language darknet markets.
Read Full Article
Like
Socprime
69

Image Credit: Socprime
Noodlophile Stealer Detection: Novel Malware Distributed Through Fake AI Video Generation Tools
- Adversaries are using fake AI-powered tools to distribute the Noodlophile information-stealing malware through fake Facebook groups and viral posts, targeting over 62,000 users.
- Defenders are facing the challenge of detecting Noodlophile Stealer, a new malware spread through fake AI generation tools that steal sensitive data from compromised systems.
- Security engineers can utilize the SOC Prime Platform to access Sigma rules for Noodlophile Stealer detection, enriched with actionable metadata and AI-powered Uncoder AI for advanced capabilities.
- The Noodlophile Stealer malware is distributed through fake AI-generated videos, targeting users seeking AI-based video and image editing tools, and combines browser credential theft, wallet exfiltration, and optional remote access deployment.
Read Full Article
4 Likes
Global Fintech Series
301

Image Credit: Global Fintech Series
Kyriba Unveils Agentic AI TAI to Transform Finance with Security, Compliance & Trust
- Kyriba introduced its agentic AI solution, TAI, to enhance finance operations with safe and compliant generative AI use.
- TAI simplifies workflows, identifies risks, and improves decision-making across treasury, payments, risk management, and working capital.
- Kyriba's TAI aims to bridge the 'Trust Gap' in AI-driven financial transformation by prioritizing data privacy and empowering leaders to make informed decisions.
- TAI was showcased at Kyriba's annual customer conference, emphasizing transparency, security, and human oversight in leveraging AI for finance and treasury operations.
Read Full Article
9 Likes
Tech Radar
405

Image Credit: Tech Radar
ASUS DriverHub driver management tool targeted by RCE vulnerability
- ASUS DriverHub, the driver management tool, had a critical vulnerability allowing remote code execution, now patched.
- Security researcher found the flaw that could run malicious code remotely, affecting ASUS devices.
- ASUS released a patch for the vulnerabilities (CVE-2025-3462 and CVE-2025-3463), urging users to update DriverHub.
- Although the flaw only affects motherboards and not laptops or desktops, ASUS strongly recommends applying the update.
Read Full Article
24 Likes
Siliconangle
317

Image Credit: Siliconangle
Orca Security acquires Opus to expand AI-driven cloud security automation
- Orca Security Ltd. has acquired Opus Security Inc. to expand AI-driven cloud security automation.
- Opus, founded in 2022, focuses on autonomous vulnerability management through intelligent AI security agents.
- Opus's platform integrates with over 100 security tools, offering a multilayered prioritization framework to focus on critical vulnerabilities.
- Orca plans to integrate Opus' expertise to autonomously identify, prioritize, remediate, and prevent cloud security risks at scale.
Read Full Article
19 Likes
Arstechnica
377
Image Credit: Arstechnica
New attack can steal cryptocurrency by planting false memories in AI chatbots
- A new attack has been discovered that can steal cryptocurrency by planting false memories in AI chatbots.
- The attack involves causing AI-powered bots to redirect payments to an account controlled by the adversary through simple text input.
- The exploit targets ElizaOS, an open source framework that uses large language models to facilitate blockchain-based transactions for users through predefined rules.
- The framework, previously known as Ai16z, is seen as a potential tool for automating interactions within decentralized autonomous organizations (DAOs).
Read Full Article
22 Likes
Siliconangle
294

Image Credit: Siliconangle
Cato Networks launches AI-driven Autonomous Policies to streamline SASE management
- Cato Networks has launched Cato Autonomous Policies, an AI capability in the Cato SASE Cloud Platform aiming to automate policy management.
- Autonomous Policies are designed to optimize and enhance all SASE policies, offering AI-driven recommendations for security, access, and networking improvements.
- This innovation streamlines policy management, reduces risk, eliminates manual upkeep, simplifies compliance, and paves the way for proactive governance in SASE.
- The first use case is firewall-as-a-service, targeting firewall rule bloat to ensure accurate, efficient, and compliant policy management across different deployment scenarios.
Read Full Article
17 Likes
Tech Radar
184

Image Credit: Tech Radar
New ClickFix campaign spotted hitting both Windows and Linux machines
- ClickFix, a malware attack that tricks users into running console commands, has now been observed targeting Linux devices by cybersecurity researchers.
- The attack involves showing popups on compromised websites instructing users to update their browsers or complete CAPTCHA tests, leading them to run malicious commands.
- The particular attack linked to a Pakistani threat actor named APT36 redirects Linux victims to a CAPTCHA page that prompts them to run a shell command, posing as an innocuous process so far.
- The attack, still in its experimental phase, has not caused significant harm yet. It downloads only a harmless JPEG file, but the potential risks remain concerning.
Read Full Article
11 Likes
TechCrunch
94

Image Credit: TechCrunch
Marks & Spencer confirms customers’ personal data was stolen in hack
- Marks & Spencer confirms customers’ personal data was stolen in a recent hack, including names, dates of birth, addresses, phone numbers, and more.
- The company is resetting online account passwords as a precautionary measure.
- Marks & Spencer is facing disruptions and outages across its stores, leading to empty grocery shelves and online ordering system remaining offline.
- Ransomware gang DragonForce claimed responsibility for cyberattacks on Marks & Spencer, Co-op, and Harrods in the U.K., with Co-op confirming customer data theft.
Read Full Article
4 Likes
Securityaffairs
46

Image Credit: Securityaffairs
Moldovan Police arrested a 45-year-old foreign man participating in ransomware attacks on Dutch companies
- A 45-year-old foreign man was arrested in Moldova for participating in ransomware attacks on Dutch companies in 2021.
- The arrest was a result of a joint international operation involving Moldovan and Dutch authorities, with the suspect wanted for cybercrimes including ransomware attacks and money laundering.
- The suspect was linked to a ransomware attack on the Netherlands Organization for Scientific Research, resulting in €4.5 million in damages, attributed to the DoppelPaymer ransomware operation.
- In a related development, Europol announced an international operation targeting key members of the DoppelPaymer ransomware group in March 2023.
Read Full Article
2 Likes
Siliconangle
455
Image Credit: Siliconangle
ClearVector raises $13M to expand identity-driven threat detection platform
- ClearVector Inc. has secured $13 million in funding to expand its identity-driven threat detection platform that focuses on real-time detection of threats by monitoring identity behaviors across different environments.
- The cybersecurity startup aims to redefine cybersecurity by shifting from traditional threat detection to identity-driven security, addressing issues with existing security approaches that struggle to deal with identity-based attacks.
- ClearVector's platform utilizes identity graph technology to monitor behaviors of human, machine, third-party, and AI identities within an organization, allowing for visibility, attribution, and anomaly detection to indicate malicious activity.
- The Series A funding round was led by Scale Venture Partners LP, with participation from Okta Ventures, Inner Loop Capital, and Menlo Ventures LP, highlighting the industry's recognition of the value of ClearVector's approach to cybersecurity.
Read Full Article
27 Likes
Securityaffairs
78
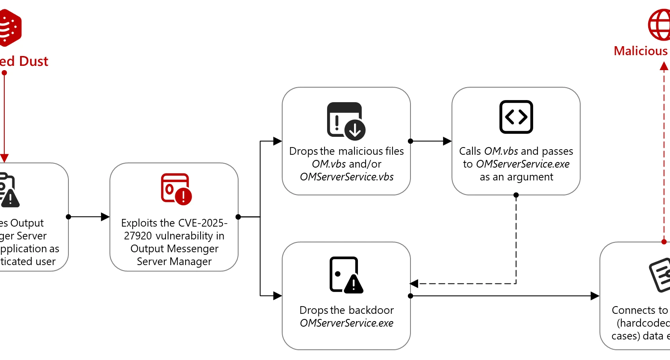
Image Credit: Securityaffairs
APT group exploited Output Messenger Zero-Day to target Kurdish military operating in Iraq
- A Türkiye-linked group, Marbled Dust, exploited a zero-day vulnerability in Output Messenger (CVE-2025-27920) to spy on Kurdish military targets in Iraq since April 2024.
- Marbled Dust, active since 2017, primarily targets organizations in Europe and the Middle East, with a history of using DNS hijacking in campaigns.
- The group targeted various entities, including government entities, Kurdish political groups, telecommunication, ISPs, NGO, and Media & Entertainment sectors.
- The exploit allowed the group to upload malicious files, gain access to user communications, steal data, compromise credentials, and deploy backdoors for exfiltration.
Read Full Article
4 Likes
Medium
432
Image Credit: Medium
Hotels are Always Watching
- Hotels, similar to airports and banks, extensively use surveillance cameras in their public areas like lobbies, entrances, and elevators.
- Guests often overlook the extent of surveillance in hotels, from the front desk to public spaces, raising questions about privacy boundaries.
- Security cameras are commonly found in all public areas, leading to concerns about the extent of monitoring guests are subject to.
- Understanding the prevalence of surveillance in hotels sheds light on the balance between security measures and guests' privacy.
Read Full Article
26 Likes
Securelist
32

Image Credit: Securelist
Using a Mythic agent to optimize penetration testing
- Researchers are using post-exploitation frameworks like Mythic to enhance penetration testing practices to stay ahead of threat actors.
- A proactive approach in learning new technologies and techniques employed by threat actors is crucial for security professionals.
- Kaspersky emphasizes detecting tools and techniques used by threat actors in real-world attacks for enhanced security.
- Behavioral analysis, exploit prevention, and fileless threats protection are integral in countering sophisticated attacks.
- Layered security solutions like EDR, NDR, and XDR are essential for quick detection and response to potential threats.
- Pentesters face challenges due to the detectability of popular tools by security solutions.
- Open-source pentesting frameworks like Sliver and Havoc have limitations in payload size and stability.
- Balancing in-house solutions and open-source tools is crucial for effective pentesting.
- Pentesting payloads are divided into modules to manage execution and maintain covert communications.
- The Stage 1 module of the pentesting payload requires dynamic functionality, minimal system traces, and compliance with OPSEC principles.
Read Full Article
1 Like
For uninterrupted reading, download the app