Cyber Security News
Minis
1.5k

Image Credit: Minis
CEO Fraud Explained – The Rise of Whaling Phishing
- Whaling phishing, also known as CEO fraud, poses a significant threat to organizations worldwide.
- Perpetrators utilize social engineering tactics to impersonate high-profile executives, aiming to deceive employees into transferring funds or divulging sensitive information.
- These attacks often involve convincing email impersonations and may even employ sophisticated techniques like fake video calls.
- Preventive measures include scrutinizing email addresses for anomalies, requesting video meetings for verification, and implementing regular phishing simulation training for employees.
Read Full Article
2 Likes
Minis
2k

Image Credit: Minis
Zerodha's Nithin Kamath warns of phishing websites, fake trading apps targeting Indian investors
- Zerodha's Nithin Kamath warns of a new scam originating from China, where fraudsters create phishing websites mimicking Indian brokerage platforms.
- Users are deceived into downloading fake apps, aiming to extract money under the guise of familiar trading platforms. India has banned over 100 Chinese-operated scam websites linked to multiple bank accounts, complicating investigations.
- Funds are shuffled between accounts and converted into cryptocurrency to obscure the trail. Kamath's alert underscores the proliferation of international scams in recent years, emphasizing vigilance against sophisticated tactics exploiting trust in financial platforms.
Read Full Article
25 Likes
Minis
1.4k

Image Credit: Minis
Here’s why you shouldn’t charge your phone using a public USB station
- In today's tech-driven world, convenience often comes at a cost, particularly when it comes to charging our devices in public spaces.
- The threat of juice jacking looms large, where unsuspecting users risk data theft or malware infection by plugging into compromised USB ports. These ports, found in airports and malls, can be manipulated by cybercriminals to gain access to sensitive information or even take control of devices.
- To safeguard against such attacks, it's prudent to avoid public charging stations whenever possible, opting instead to carry personal chargers or USB data blockers for added security."
Read Full Article
34 Likes
Minis
1.2k

Image Credit: Minis
Hackers turn 3 million toothbrushes into cyber weapons, attack Swiss company
- In a groundbreaking cyber attack, three million smart toothbrushes were seized by hackers to launch a devastating Distributed Denial of Service (DDoS) assault on a Swiss company, resulting in substantial financial losses.
- This incident highlights the vulnerability inherent in the rapidly expanding Internet of Things (IoT) ecosystem. Cybercriminals exploited the connectivity features of these toothbrushes, infecting them with malware to flood the company's website with bogus traffic.
- This underscores the pressing need for heightened cybersecurity measures within the IoT domain.
Read Full Article
17 Likes
Minis
1.1k
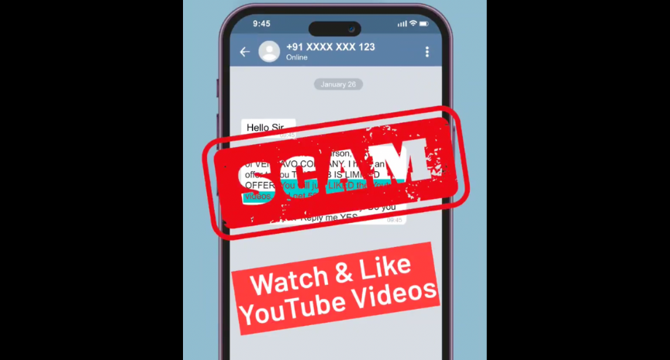
Image Credit: Minis
Major WFH Scam in Bengaluru Exposed
- Bengaluru Police have cracked down on a major work-from-home scam, arresting several individuals involved in a Rs 158 crore fraud. The Central Crime Branch apprehended suspects from Bengaluru, Mumbai, and Hyderabad, exposing a syndicate that lured victims through promises of remote job opportunities.
- Operating through platforms like WhatsApp, the fraudsters tricked people into completing tasks such as liking YouTube videos or installing apps, offering monetary rewards. However, the victims soon discovered their digital wallets were fake when attempting to withdraw funds.
- The police, prompted by a complaint, froze Rs 62.8 lakh across 30 bank accounts. The syndicate was linked to 2,143 cybercrime cases nationwide.
Read Full Article
21 Likes
Minis
1.6k

Image Credit: Minis
Massive 26 Billion Record Leak: Dropbox, LinkedIn, Twitter All Named
- A colossal data breach, termed the "Mother of all Breaches," has exposed a staggering 26 billion records, including sensitive data from platforms like Twitter, Dropbox, LinkedIn, Tencent, Weibo, Adobe, Canva, and Telegram.
- Uncovered by Security Discovery and Cybernews researchers, this 12-terabyte breach is likely orchestrated by a malicious actor or data broker.
- The aggregated data poses serious risks, enabling identity theft, phishing, cyberattacks, and unauthorized access. Although only a minor part is new, the inclusion of username-password combinations heightens concerns.
Read Full Article
34 Likes
Minis
1.1k

Image Credit: Minis
Why govt does not want you to dial *401#
- The Department of Telecom (DoT) has issued a warning about a call forwarding scam involving the code *401#. Scammers impersonate telecom customer service representatives, urging victims to dial *401# followed by an unknown mobile number, activating unconditional call forwarding.
- This allows fraudsters to intercept incoming calls, potentially gaining access to sensitive information like OTPs and personal details. To stay safe, the DoT advises users to disable call forwarding in their phone settings and avoid responding to suspicious numbers.
- Additionally, users should enhance phone security, refrain from sharing crucial information, and verify caller authenticity through official contact channels.
Read Full Article
26 Likes
Minis
127

Image Credit: Minis
Man gets 10,000 messages with OTPs, loses Rs 38,000: Report
- In a distressing incident in Bengaluru, a man lost over Rs 38,000 after falling victim to a sophisticated scam.
- Channakeshava KS, a sales executive, received an automated call falsely claiming a Swiggy food order. Pressing '1' as he hadn't placed any order, he unknowingly provided a one-time password (OTP). Subsequently bombarded with 10,000 OTPs, he realized the scam after Rs 38,720 was deducted from his LazyPay loan account.
- Despite reporting to the police and contacting Swiggy, who requested more time to investigate, the victim faces the aftermath of a meticulously orchestrated fraud, highlighting the need for heightened digital vigilance.
Read Full Article
4 Likes
Minis
1.2k

Image Credit: Minis
BFSI industry faces a talent crunch in cybersecurity roles
- Indian BFSI sector faces a talent crunch in cybersecurity, with demand surpassing the availability of skilled professionals.
- Indian curriculum lacks emphasis on practical cybersecurity courses, putting graduates at a disadvantage compared to those from foreign universities.
- Current active cybersecurity job openings in BFSI sector: 10,000-12,000; Overall demand across sectors: 35,000-40,000.
- Graduates struggle to secure roles despite hackathon participation. Companies, especially banks, prefer skilled individuals with cautious hiring practices due to data sensitivity.
Read Full Article
29 Likes
Minis
1.6k

Image Credit: Minis
The Most Common Passwords Used in India in 2023
- 'India's most common password in 2023 is '123456,' easily cracked in less than 1 second by hackers, reveals NordPass research.
- 'Admin' and '12345678' follow as the second and third most common passwords. Other frequently used passwords include '12345,' 'password,' 'Pass@123,' '123456789,' 'Admin@123,' 'India@123,' and 'admin@123.'
- 'UNKNOWN' ranks 20th, highlighting the widespread use of weak passwords.
Read Full Article
28 Likes
Minis
391

Image Credit: Minis
Woman pays Rs 5 handling fee for her online delivery, later loses Rs 80,000 to scammers
- The victim, Shifali Chaudhary, fell prey to scammers who posed as delivery agents, requesting a nominal Rs 5 handling fee for a parcel she was expecting.
- The scammer further confirmed the victim's delivery address through a phone call, adding a layer of legitimacy to the fraudulent scheme.
- Initially asked for Rs 5, Shifali ended up losing Rs 80,000 as scammers used the provided link to gain access to her sensitive banking details, executing unauthorized transactions.
- Scammers acquire personal details through diverse sources like data breaches, dark web purchases of stolen data, and exploiting publicly available information from social media and directories.
Read Full Article
20 Likes
Minis
1.5k

Image Credit: Minis
AI-powered WhatsApp video call the latest way to dupe people of their money
- Rising cyber fraud in India linked to increased tech usage, smartphones, and online payments.
- Scammers using AI to impersonate close relatives in WhatsApp video calls, tricking victims into transferring money.
- Delhi Police Cyber Crime Advisor, Kislay Choudhary, warns of such scams and highlights cases of successful fraud.
- Choudhary advises caution, suggesting verifying caller identity through a regular call to prevent falling prey to cyber fraud.
Read Full Article
32 Likes
Minis
1.6k
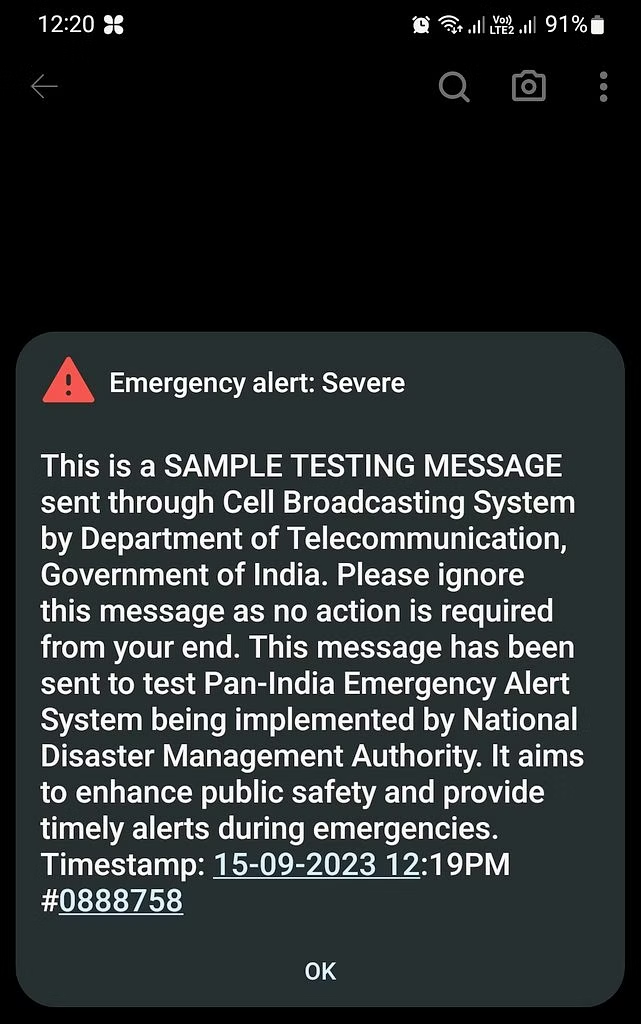
Image Credit: Minis
Received an Emergency Alert on your phone today? Here's what It means
- India conducted a successful test of its emergency alert system, sending a test flash to smartphones across the country.
- The test message, which included a loud beep and the alert "emergency alert: severe," was sent via the Cell Broadcasting System by the Department of Telecommunication.
- The purpose of the test was to assess the efficiency and effectiveness of mobile operators and cell broadcast systems in delivering emergency warnings.
- This is part of the government's collaboration with the National Disaster Management Authority to enhance public safety and disaster preparedness. Similar tests were done on July 20 and August 17.
Read Full Article
22 Likes
Minis
1.6k

Image Credit: Minis
Man clicks on Big Bazaar special discount ad on social media, loses over Rs 1 lakh
- A man from Delhi lost over Rs 1 lakh after clicking on a social media ad that promised a 75% discount at Big Bazaar but never delivered the purchased items.
- The man used his ICICI bank debit card for the transaction, which was subsequently hacked, resulting in unauthorized deductions from his account.
- The victim filed an FIR and reported similar scam offers in the names of Ali Khan and Monsoon Offers on Facebook.
- To stay safe while shopping online, users should verify the authenticity of the website, avoid making payments to unverified sources, and consider using cash on delivery when purchasing from unverified pages.
Read Full Article
21 Likes
Minis
1.5k

Image Credit: Minis
What is the AJIO scam and how scamsters are duping people
- The Delhi High Court has ordered a cyber cell investigation into a significant scam exploiting the name of AJIO, a shopping site owned by Reliance Retail.
- Scammers lured unsuspecting customers into depositing amounts ranging from ₹5,000 to ₹10 lakh, promising them the chance to win cash prizes through scratch cards after making the deposit.
- These fraudsters utilized the identity of AJIO in their communications to solicit these deposits, leading to the need for a thorough investigation.
Read Full Article
32 Likes
For uninterrupted reading, download the app