Cyber Security News
Minis
1.7k

Image Credit: Minis
24-yr-old engineer cheated of ₹5 lakh on fake claim of getting Amazon job
- A Mumbai engineer, 24, fell for scammers promising an Amazon part-time gig, earning ₹1,500-₹5,000 daily for 'add-to-cart' screenshots.
- Fraudsters make small payments to engineer initially, building trust by showing compensation for screenshot submissions.
- Exploiting trust, scammers convince engineer to invest ₹5 lakh in Bitcoin, resulting in substantial financial loss.
- Incident underscores the risks of online deception, urging vigilance and skepticism to avoid falling victim to such scams.
Read Full Article
31 Likes
Minis
114
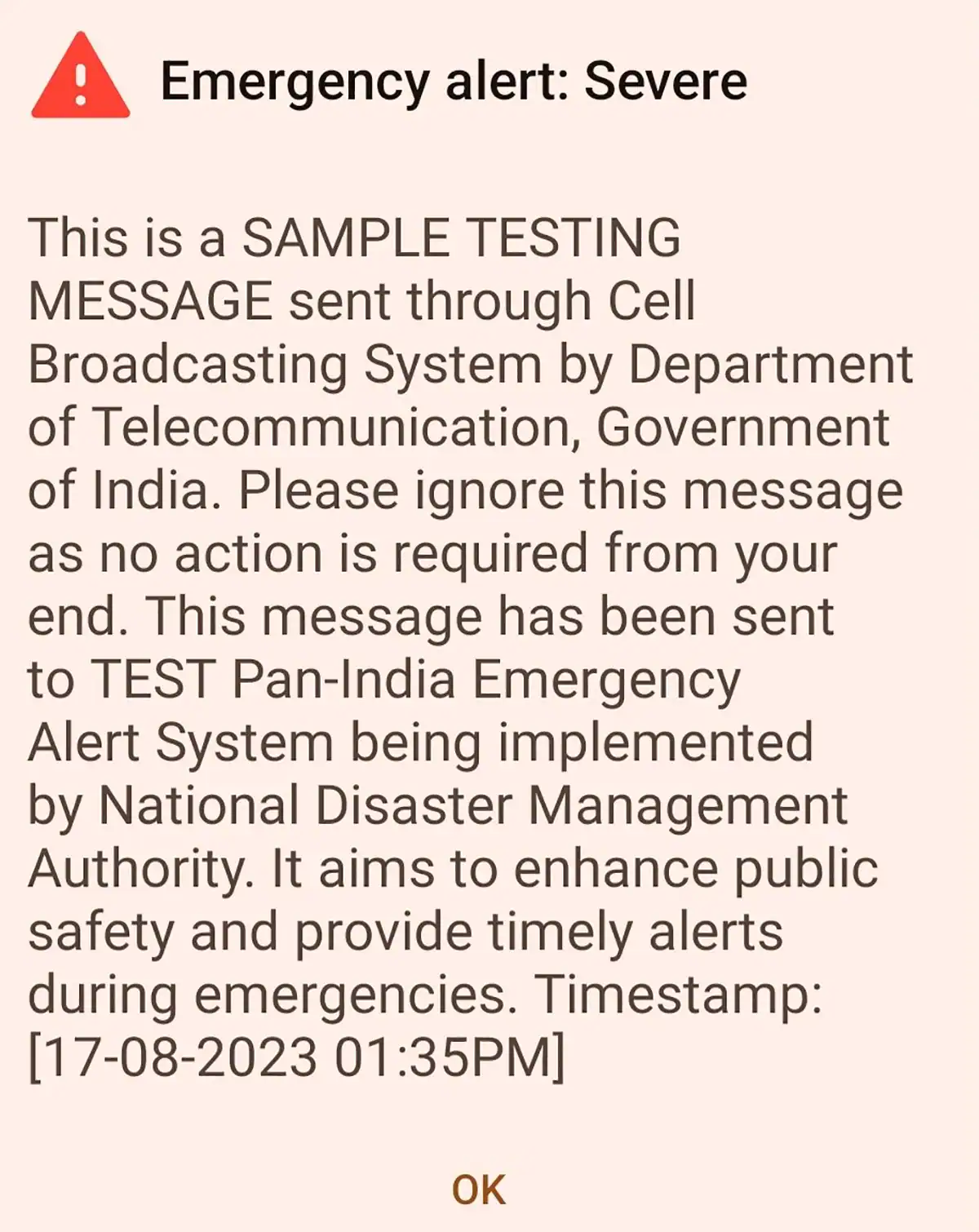
Image Credit: Minis
Received an Emergency Alert on your phone today? Here's what you need to know
- The Indian government conducted a test of its emergency alert system by sending a loud beep and 'emergency alert: severe' flash to smartphones.
- The message clarified that it was a sample testing message by the Department of Telecommunication, Government of India.
- The Pan-India Emergency Alert System aims to enhance public safety and provide timely alerts during emergencies.
Read Full Article
3 Likes
Minis
1.6k

Image Credit: Minis
Govt warns dating and matrimonial app users, says do not take any expensive gifts from online lovers
- India witnessing a rapid increase in online scams targeting people on various platforms like UPI apps, social media, and dating websites.
- Scammers exploiting emotions on dating and matrimonial sites, asking victims for money by promising expensive gifts.
- Reportedly, around two-thirds of Indian adults (66 per cent) have fallen victim to an online dating/romance scam, and victims have lost an average of Rs 7,966. merge this in any of the pointer
- Ministry of Finance issued advisory warning against customs duty payment requests. Official Indian Customs never asks for such payments via calls or SMS.
Read Full Article
31 Likes
Minis
1k

Image Credit: Minis
Govt issues high-risk warning for Google Chrome users, asks users to update browser immediately
- The Indian government's CERT-In agency has issued a high-severity warning about vulnerabilities in specific versions of Google Chrome, which could compromise user security.
- The identified vulnerabilities include type confusion, heap buffer overflow, out of bounds memory access, and other issues in various components of Chrome.
- Attackers could exploit these vulnerabilities by tricking users into visiting malicious websites, potentially gaining control of their computers and stealing personal information.
- Users should update Chrome, be cautious online, use strong passwords, enable two-factor authentication, and keep software updated.
Read Full Article
7 Likes
Minis
1.3k

Image Credit: Minis
Healthcare data breach detected on IIIT Delhi's informatics platform: Reports
- IIIT-Delhi's Portal for Health Informatics (PHI) suffered a data breach with the leak of sensitive information on a cybercrime forum, as reported by CloudSEK.
- The leaked database comprises 10,842 emails, 6,500 unique domains, and 29,000 unique URLs, along with other data.
- Surprisingly, out of the 82 leaked files, 54 were already publicly accessible on PHI's website prior to the breach.
Read Full Article
29 Likes
Minis
310

Image Credit: Minis
Know about Juice Jacking scam and ways to protect your data
- Juice jacking involves using public charging stations to steal sensitive data from unsuspecting users' devices, leading to potential financial harm.
- Fraudsters set up traps in locations like airports and hotels, enticing users with free charging to connect their devices to compromised stations.
- Once connected, attackers can steal passwords, contacts, and other personal information, or even install malware for continued access.
- To stay safe, avoid using public charging ports, use personal chargers or power banks, enable security features on your devices, be cautious with public Wi-Fi, and keep your software and antivirus updated.
Read Full Article
17 Likes
Minis
1.1k

Image Credit: Minis
Barbie malware: India among top five countries facing attacks, says McAfee research
- India among top three countries facing Barbie merchandise malware attacks, per McAfee report.
- Scammers using bogus movie downloads to spread malware, Barbie-related viruses, and steal personal info.
- Attackers exploit movie hype, target US and other countries with malware-laden files.
- Indian victims prompted to download malware-packed .zip files disguised as Barbie movie downloads.
Read Full Article
11 Likes
Minis
2.9k

Image Credit: Minis
How 15,000 Indians were duped of over Rs 700 Cr
- 15,000 Indians, including software professionals, duped in a Rs 700 crore cryptowallet fraud by Chinese operators.
- The scam involved luring victims through platforms like Telegram and WhatsApp to perform simple tasks, like liking YouTube videos or writing Google reviews, and promising lucrative returns.
- Victims were initially asked to invest small amounts and were paid some profits to gain their trust. However, they were later coerced into investing more money and ultimately lost significant sums.
- Nine people arrested in India, over 113 bank accounts used, funds converted into cryptocurrency and routed to China via Dubai.
Read Full Article
20 Likes
Minis
1.5k

Image Credit: Minis
8-yr-old buys AK-47 from the dark web using money he made working as a hacker
- An 8-year-old boy in the Netherlands managed to purchase an AK-47 and ammunition through the dark web, shocking his mother, Barbara Gemen, who is a human resources expert.
- The gun was delivered to their doorstep after being routed through Poland and Bulgaria to avoid customs checks, all facilitated by the dark web.
- The boy's involvement in cybercrime started innocently with online gaming but escalated as he joined a group of cyber-criminals, engaging in activities like money laundering and eventually buying the gun.
Read Full Article
28 Likes
Minis
773

Image Credit: Minis
Govt cautions internet users against ransomware 'Akira'; all you need to know
- The government has issued a warning about a ransomware called "Akira," which targets Windows and Linux-based systems. It steals important information and encrypts data to extort victims.
- Once the malware encrypts the data, it employs a double extortion tactic to force victims into paying the ransom. If the victim refuses to pay, the attackers release the stolen data on their dark web blog.
- To protect against such attacks, internet users are advised to practice basic online hygiene and follow protection protocols.
- As preventive measures, users should regularly maintain offline backups of critical data and ensure their passwords follow a strong password policy.
Read Full Article
11 Likes
Minis
1.2k

Image Credit: Minis
Doctor scammed out of Rs 1 crore in Telegram movie rating scam
- A 43-year-old doctor residing in Maharashtra fell victim to a scam on Telegram where scammers approached him with an enticing offer to earn money by rating movies online.
- Initially, the doctor managed to earn ₹830 through his first movie rating, which encouraged him to continue participating in the scheme. However, the scammers swiftly changed their strategy and demanded a deposit of ₹9,900 from him to unlock higher commissions.
- As the doctor complied with their demands and deposited the initial sum, the scammers continuously manipulated him by requesting varying amounts for withdrawing his commission.
- Unfortunately, the doctor ended up depositing a total of ₹1.09 crore to the scammers in hopes of earning a significant return.
Read Full Article
30 Likes
Minis
760

Image Credit: Minis
Pornhub accused of abusing user data by #StopDataPorn
- Lawmakers in the US are passing age-verification laws targeting explicit content sites like Pornhub.
- #StopDataPorn activists have filed a GDPR complaint against Pornhub, accusing the site of illegally processing personal data without consent and sharing it with unknown third parties.
- #StopDataPorn claims that Pornhub's actions violate GDPR Article 9, as they don't ask for consent when processing personal user data and engage in undisclosed sharing of personal information.
- Researchers have gathered evidence for the complaint, focusing on Pornhub's recommendation algorithm, which assigns sexual preferences without individuals' knowledge.
Read Full Article
18 Likes
Minis
1.5k

Image Credit: Minis
Zerodha's Nithin Kamath red flags ‘new scam’ in name of FedEx, Blue Dart
- Co-founder of Zerodha alerts about a scam using courier company names like FedEx and Blue Dart, where fraudsters pose as officials from CBI and crime branch.
- Victims receive calls claiming that their parcel was seized by police due to drugs, accompanied by official-looking notices and video calls from fake police officials. Money is demanded to release the package.
- Kamath advises staying calm, responding with "I will get my lawyer to speak to you," and not reacting impulsively to avoid falling victim to the scam.
- Twitter users share their similar scam experiences, thanking Kamath for raising awareness about evolving fraud tactics.
Read Full Article
27 Likes
Minis
335

Image Credit: Minis
Authorities sound alarm on Pink WhatsApp scam: Here's what you need to know
- Authorities in multiple states issue warnings regarding the Pink WhatsApp scam, following an advisory from the Central government.
- The scam involves a deceptive link disguised as an official update, specifically targeting Android users.
- Clicking on the fake link can result in the installation of malicious software on the user's phone. This poses a significant threat as the user's device becomes infected, and the malware has the potential to spread to other mobiles through WhatsApp contacts.
- The advisory emphasizes that not only does the user's phone become compromised, but the scam can also infect the devices of individuals who communicate with the user over WhatsApp.
Read Full Article
10 Likes
Minis
1.5k

Image Credit: Minis
Which chinese hacking groups are accused of targeting Microsoft and the United States
- Chinese hacking teams, including 'Volt Typhoon,' 'Backdoordiplomacy,' 'APT 41,' and 'APT 27,' have been linked to cyberattacks on government, military, and corporate targets.
- 'Volt Typhoon' is known for its focus on espionage and information gathering, as identified by Microsoft.
- These Chinese hacking groups have faced accusations of cyber espionage, intellectual property theft, and have prompted heightened cybersecurity measures.
Read Full Article
31 Likes
For uninterrupted reading, download the app