Cyber Security News
Tech Radar
340

Image Credit: Tech Radar
This Microsoft 365 phishing campaign can bypass MFA - here's what we know
- Researchers spotted a new phishing campaign, abusing Dynamics 365 Customer Voice, a Microsoft tool with over 500,000 users including Fortune 500 companies.
- Attackers are using phishing emails with fake Dynamics 365 Customer Voice links to steal login credentials from victims.
- The phishing emails focus on financially related topics, targeting organizations in various sectors, including community groups, universities, news outlets, health information groups, and more.
- The attackers have targeted over 3,000 emails, aiming at more than a million different inboxes belonging to 350 organizations, with the ability to capture MFA codes as well.
Read Full Article
20 Likes
Eu-Startups
308

Dutch VC fund TIN Capital bags an additional €15 million for their ‘European Cyber Tech Fund V’
- Dutch VC fund TIN Capital secures an additional €15 million for their cybersecurity fund 'European Cyber Tech Fund V', targeting a fund size exceeding €60 million.
- Support for this funding includes Invest-NL, InnovationQuarter, ROM Regio Utrecht, Dutch investors, and family offices, aiming to strengthen European cybersecurity companies.
- TIN Capital, solely focused on cybersecurity investments since 2018, backs companies in cybersecurity, IoT Security, Privacy Enhancing Technologies, among other areas, with investments ranging from €1-10 million.
- Investments in European cybersecurity innovations are crucial for safeguarding Europe's digital future, as echoed by various investors supporting TIN Capital's fund.
Read Full Article
18 Likes
Minis
1.5k
Image Credit: Minis
995 Crore Passwords Stolen In Biggest Data Breach Ever: Report
- In what's being called the largest data breach ever, 995 crore passwords were leaked by a hacker known as "ObamaCare".
- The dataset, named Rockyou2024, combines passwords from various breaches, posing a significant risk of credential stuffing and unauthorized access. This compilation, alongside other leaked databases, could lead to widespread data breaches, financial fraud, and identity thefts.
- Cybernews researchers urge enhanced cyber hygiene practices to mitigate risks. The breach underscores the critical need for robust cybersecurity measures globally, emphasizing the ongoing threat posed by large-scale data breaches.
Read Full Article
29 Likes
Minis
2.6k

Image Credit: Minis
Shadowy hacker claims he has data of 375 million Airtel users, Airtel says no breach in its systems
- A hacker claims to possess data of 375 million Airtel users, including sensitive information like phone numbers, Aadhaar numbers, and more.
- Airtel denies any breach, attributing the claim to misinformation aimed at damaging its reputation. The alleged data sale surfaced on forums frequented by cybercriminals, sparking concerns despite Airtel's assurances.
- Security experts debate the validity of the claim, urging vigilance in cyber hygiene practices like password updates, monitoring accounts, enabling 2FA, and avoiding phishing. Airtel emphasizes its systems' security while acknowledging past data breaches in Indian companies.
Read Full Article
24 Likes
Minis
1.3k
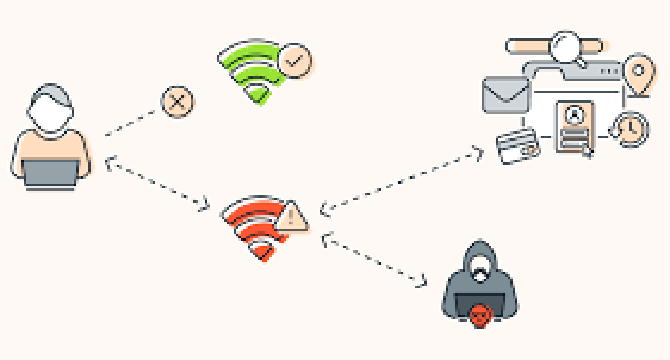
Image Credit: Minis
What is an evil twin attack? How to spot and avoid them
- Evil twin attacks are a form of cybercrime where hackers create fake Wi-Fi access points that mimic legitimate networks.
- When users connect to these deceptive networks, hackers can intercept sensitive information, such as login credentials and financial data. To protect yourself, avoid unsecured Wi-Fi networks, disable auto-connect, and use a VPN to encrypt your data.
- Always verify the network name before connecting and prefer using your personal hotspot in public spaces. Regularly update your devices and software to patch vulnerabilities, and enable two-factor authentication for added security. Stay vigilant to keep your data safe from evil twin attacks.
Read Full Article
29 Likes
Minis
1.1k

Image Credit: Minis
Explained: What Is Snowblind Malware That Can Steal Bank Data From Android
- Snowblind is a new Android malware targeting banking information. Discovered by cybersecurity firm Promon, it infiltrates devices through malicious apps that appear legitimate.
- The malware exploits the "seccomp" feature in the Linux kernel to bypass Android's security, using accessibility services to monitor screens and steal login information. It can disable biometric and two-factor authentication, increasing the risk of fraud and identity theft.
- Snowblind operates quietly in the background, making it hard to detect. It likely spreads outside official app stores through social engineering attacks, tricking less tech-savvy users.
Read Full Article
23 Likes
Minis
1.9k
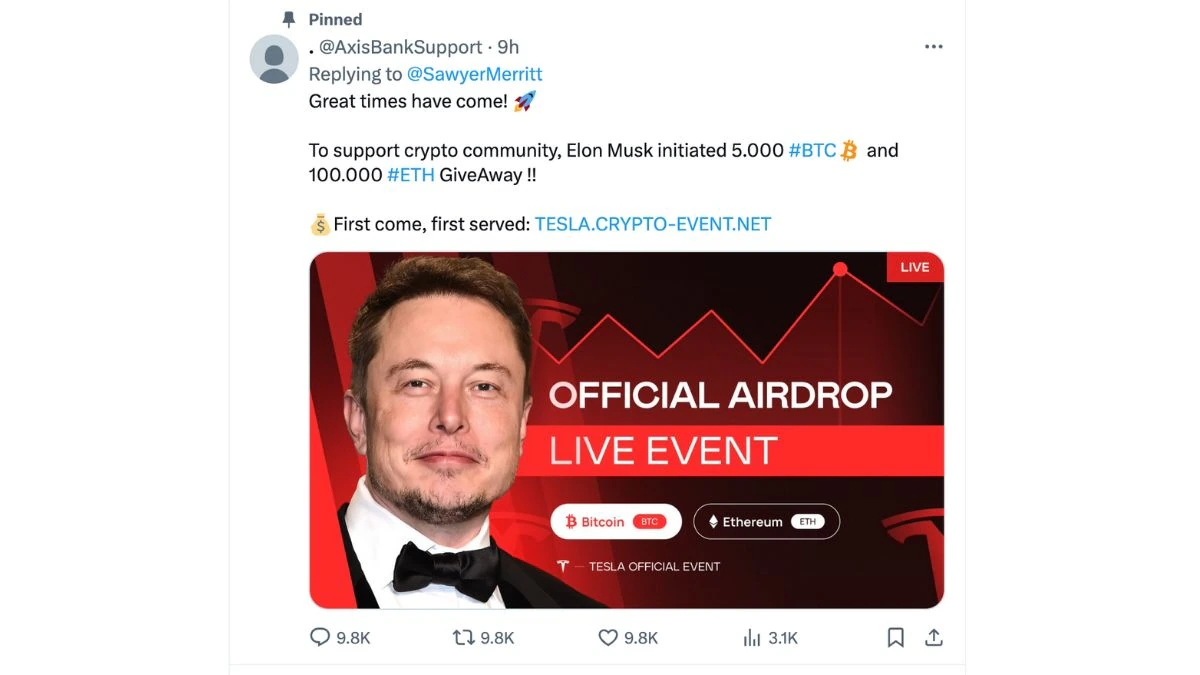
Image Credit: Minis
Axis Bank official support page on X hacked; fraudsters share post on Elon Musk, bitcoin
- Axis Bank's official support page on X (formerly Twitter) was recently compromised in a cyberattack. The attackers replaced the page's name with a period and posted about a crypto event and a Bitcoin giveaway.
- This unauthorized post was also pinned to the page. The incident underscores vulnerabilities in online security, impacting Axis Bank's digital presence and potentially influencing customer trust.
- Investigations are ongoing, emphasizing the critical need for robust cybersecurity measures amid rising threats in the digital landscape. Axis Bank has yet to provide further details or statements regarding the breach.
Read Full Article
21 Likes
Minis
1.2k

Image Credit: Minis
Meet the 22-YO Indian Techie Who Received ‘Hall of Fame’ Recognition from NASA & Apple
- Muneeb Amin Bhat, a 22-year-old from Zungalpora, Kashmir, has emerged as a cybersecurity prodigy, receiving accolades from major companies like Apple and NASA
- Despite limited resources in his village, Muneeb's fascination with computers began at a young age. Through self-learning and perseverance, he mastered ethical hacking, uncovering vulnerabilities for over 60 international organizations.
- His notable discoveries earned him recognition in Apple and NASA's Hall of Fame, showcasing his impact on global cybersecurity. With plans to pursue a career in cybersecurity after completing his degree, Muneeb exemplifies the power of passion and determination in overcoming obstacles.
Read Full Article
28 Likes
Minis
760
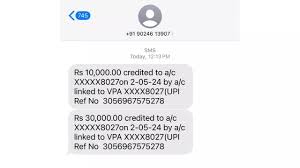
Image Credit: Minis
Bengaluru techie shares new fraud criminals are using to steal your money
- As online fraud cases surge, Bengaluru-based entrepreneur Aditi shared a cautionary tale on X, warning about a new scam tactic exploiting SMS messages.
- During an office call, Aditi received a call from someone claiming to transfer money to her father. After receiving SMS alerts mimicking bank notifications, the caller alleged mistakenly sending Rs 30,000 instead of Rs 3,000 and urged Aditi to return the excess. Alert to discrepancies in the SMS alerts, Aditi avoided the scam.
- This incident underscores the need for vigilance, urging individuals to verify transactions through secure channels, as reliance on SMS notifications alone can be exploited by cybercriminals.
Read Full Article
4 Likes
Minis
1.1k

Image Credit: Minis
Every rupee lost to fraud in India costs companies Rs 4, says this study
- The latest study by LexisNexis reveals alarming trends in fraud in India, with every rupee lost costing companies Rs 4.
- Digital channels now account for 51% of fraud cases, surpassing physical fraud for the first time. The impact extends beyond financial losses, affecting consumer satisfaction and conversion rates.
- To combat this, businesses must adopt advanced fraud management solutions like AI and biometric authentication. With fraud on the rise, it's crucial for organizations to prioritize security measures to protect against evolving threats and maintain trust in digital transactions.
Read Full Article
18 Likes
Minis
1k

Image Credit: Minis
Several ICICI Bank users report seeing other customers' details using iMobile app
- Several ICICI Bank customers are experiencing a critical glitch on the iMobile app, where they can view other users' credit card details, including full card numbers, expiry dates, and CVVs.
- ICICI Bank acknowledges the issue, attributing it to erroneous mapping of approximately 17,000 new credit cards to wrong users, constituting 0.1% of their portfolio. They assure prompt action, blocking affected cards and issuing new ones.
- Customers can report fraud to the National Cyber Crime or ICICI Bank's helpline. Precautions advised include setting up PINs, avoiding unsecured Wi-Fi, and cautious browsing habits.
Read Full Article
6 Likes
Minis
684

Image Credit: Minis
Dating apps under fire for privacy failings, warns Mozilla Report
- Dating apps like Tinder and Bumble face criticism for neglecting user privacy, says Mozilla. Their report flags 22 platforms for failing basic security standards, amid a shift towards younger, tech-savvy users.
- Despite efforts to regain popularity, apps resort to intrusive data practices. Shockingly, 90% share or sell personal data, with Match Group singled out for vague policies. Zoë MacDonald of *Privacy Not Included condemns these practices, calling them dealbreakers.
- The gravity of privacy breaches was highlighted by The Wall Street Journal, exposing exploitation on platforms like Grindr. While some apps use AI for safety, concerns persist about data misuse in matchmaking. Mozilla urges apps to protect users' data to foster meaningful connections.
Read Full Article
3 Likes
Minis
997

Image Credit: Minis
Google hosted over 100 YouTube videos promoting AI deepfake porn
- Google removed over 100 YouTube videos after promoting AI deepfake porn, including apps used for non-consensual image alteration. Forbes uncovered videos advertising AI apps removing clothes from images, with victims facing bullying.
- The platform also hosted ads for "deep nude" services. Google removed 27 ads and YouTube took down 11 channels and 120+ videos. NCOSE criticized Google's profit cycle from nudify apps.
- AI-generated deepfake porn, even of children, is a rising concern. Apple promptly removed similar apps, contrasting with Google's response. Victims of AI exploitation expressed ongoing trauma. AI's misuse remains a pressing issue for online safety.
Read Full Article
25 Likes
Minis
777

Image Credit: Minis
Why millions of dollars are being offered to hack and crack iPhones, Android phones, WhatsApp and more
- Startups are offering millions to hackers who can discover zero-day vulnerabilities in popular devices and apps. Crowdfense, for instance, offers up to $30 million, with iPhone exploits fetching $7 million and Android exploits $5 million.
- Exploits for Chrome, Safari, WhatsApp, and iMessage can earn hackers between $3 and $5 million. These companies sell the exploits to organizations, including governments, for tracking criminals. Google reports that Commercial Surveillance Vendors were behind 75% of known zero-day exploits targeting Google products in 2023.
- Tech companies are enhancing their defenses against zero-days, with notable investments reducing their prevalence.
Read Full Article
11 Likes
Minis
1.1k

Image Credit: Minis
How Indian Woman In US Lost Life Savings To Scammer She Met On Hinge
- Shreya Datta, a 37-year-old Indian woman in the US, lost her life savings and retirement funds, totaling $450,000, to a sophisticated cryptocurrency romance scam orchestrated by a fraudster she met on Hinge.
- The scam, known as "pig butchering," exploited her desire for companionship, using digitally altered deepfake videos and persuasive tactics to manipulate her into fake crypto investments.
- Despite reporting the crime to the FBI and Secret Service, Datta faces little hope of recovery, highlighting the devastating impact of such scams and the need for increased awareness and support for victims.
Read Full Article
26 Likes
For uninterrupted reading, download the app