Cyber Security News
Macdailynews
352

Image Credit: Macdailynews
Germany asks Apple and Google to remove Chinese AI startup DeepSeek from app stores
- Germany's data protection commissioner has asked Apple and Google to remove the Chinese AI startup DeepSeek from their app stores due to data privacy concerns.
- DeepSeek is accused of illegally transferring users' personal data to China, with concerns raised about the protection of German users' data in China.
- Attempts were made to request DeepSeek to meet non-EU data transfer requirements or withdraw the app voluntarily, but the company did not comply.
- Several countries, including Italy and the Netherlands, have taken actions against DeepSeek, citing concerns about personal data use, while U.S. lawmakers plan to introduce a bill to ban AI models from China for government use.
Read Full Article
21 Likes
Medium
38

Millions Urged to Update Passwords After Massive Data Leak Found Online
- A massive data leak containing about 16 billion login records has been reported, with duplicate entries making it unclear how many unique accounts are compromised.
- Exposed information was related to popular services like Google, Facebook, and Apple, but no direct data breach has been reported by these companies.
- Cybersecurity expert Bob Diachenko led the investigation and found the exposed data due to poor server security, with plans to alert affected parties after accessing the files briefly.
- While experts suggest that the leaked data may not be new, the incident highlights the ongoing cybersecurity challenges faced by internet users.
Read Full Article
2 Likes
Medium
322

Image Credit: Medium
What happened to UC Browser?
- UC Browser, developed by UCWeb, a subsidiary of Alibaba Group, was a popular mobile browser known for its speed and small file size.
- The browser faced issues related to privacy concerns and data leakage to Chinese servers, jeopardizing user data security.
- In June 2020, the Indian government banned UC Browser and 58 other Chinese apps over national security concerns, leading to a significant decline in its user base.
- While still available in some countries, UC Browser's usage has plummeted, showcasing the impact of trust issues on user retention and app popularity.
Read Full Article
19 Likes
Tech Radar
317

Image Credit: Tech Radar
SMBs are being hit by malicious productivity tools – Zoom and ChatGPT spoofed by hackers
- Russian cybersecurity firm, Kaspersky, warns of rising cyberattacks impersonating productivity tools like Zoom, Microsoft Office, and ChatGPT targeting small and medium-sized businesses.
- Cybercriminals are using techniques like phishing campaigns and presenting fake offers to steal data or distribute malware by impersonating popular software tools.
- Kaspersky tracked over 4,000 unique malicious files targeting SMBs, with a 115% rise in ChatGPT spoofing incidents.
- To safeguard against such attacks, businesses are advised to establish clear software adoption procedures, define access rules, and conduct regular backups.
Read Full Article
19 Likes
TechJuice
390

Image Credit: TechJuice
NCERT Warns of Cyber Threats from Email Misconfigurations (Do This ASAP)
- National CERT warns of cyber threats stemming from email misconfigurations, emphasizing the need for immediate security measures.
- Email misconfigurations can lead to phishing attacks, business email compromise, and credential theft, posing risks to confidentiality and operational integrity.
- The advisory highlights major impacts like operational disruptions, credential theft, nationwide phishing campaigns, and loss of public trust due to misconfigured email systems.
- Recommendations include using strong passwords, enabling multi-factor authentication, enforcing email security protocols, and training on email-based threats to mitigate risks.
Read Full Article
23 Likes
Medium
12

Image Credit: Medium
Decentralized Wireless Networks: Are They Sustainable?
- Decentralized wireless networks, known as DeWi, aim to democratize network access and challenge traditional telcos.
- Pioneers like Helium, Pollen Mobile, and XNET are implementing unique approaches to spectrum, scalability, and user incentives.
- Challenges arise in sustaining the networks due to issues like token rewards attracting excessive hardware deployment and insufficient data demand.
- Security concerns, such as fraudulent activities like signal manipulation and identity spoofing, threaten the integrity and sustainability of DeWi networks.
Read Full Article
Like
Tech Radar
425

Image Credit: Tech Radar
British man behind ‘IntelBroker’ hacker group charged with stealing millions
- A British man named Kai West has been charged by US law enforcement for allegedly hacking numerous organizations worldwide as part of the 'IntelBroker' cybercrime group, causing over $25 million in damages.
- West faces potential sentences of up to 20 years in prison for wire fraud and conspiracy to commit computer intrusions. The IntelBroker group targeted around 40 victims globally, including well-known firms such as AMD, Apple, and CISCO.
- The group's scheme, which allegedly ran from December 2022 to February 2025, involved selling stolen data to collect approximately $2 million. West, arrested in France, is currently facing extradition to the US.
- Authorities traced West to IntelBroker through a purchase of stolen data, linking his real identity via a cryptocurrency transaction and his Gmail account. This case highlights the FBI's efforts to combat cybercriminals globally.
Read Full Article
25 Likes
HRKatha
420

Image Credit: HRKatha
“Adapt & upskill or be a lagger”: Zerodha co-founder warns
- Nikhil Kamath, co-founder of Zerodha, emphasizes the importance of upskilling and continuous learning in anticipation of job losses to automation.
- Skills in AI, cybersecurity, big data, creative thinking, and environment preservation will be in high demand, while 39% of current skills are expected to lose relevance.
- By 2030, 92 million jobs will vanish, but 170 million new jobs will be created, with a net gain of 78 million jobs for those willing to adapt.
- While businesses plan to upskill or retrain employees, concerns linger over skill gaps, training availability, and the automation of certain roles.
Read Full Article
25 Likes
TechBullion
378

Image Credit: TechBullion
Best Digital Tools for Tracking and Managing Maritime Shipments
- Digital tools are essential for tracking and managing maritime shipments efficiently in the fast-paced shipping industry.
- Platforms like SHIPNEXT offer reliable real-time tracking and advanced technology to enhance shipment management.
- Carrier tracking systems provide clarity and confidence in monitoring shipments across the maritime supply chain.
- Investing in modern software for tracking and logistics is crucial for global businesses to stay competitive.
Read Full Article
22 Likes
Securityaffairs
395
Image Credit: Securityaffairs
APT42 impersonates cyber professionals to phish Israeli academics and journalists
- Iran-linked APT42, known as Educated Manticore, targets Israeli journalists, cybersecurity experts, and academics with phishing attacks by impersonating security professionals.
- APT42 focuses on highly targeted spear-phishing using techniques such as credential harvesting, surveillance operations, and malware deployment.
- The threat actors created fake Gmail login pages and Google Meet invitations to steal email credentials and 2FA codes from victims, gaining unauthorized access to their accounts.
- The group used custom phishing kits mimicking Gmail, Outlook, and Yahoo, employing live keyloggers and WebSocket connections to control the stolen data.
Read Full Article
23 Likes
Global Fintech Series
162

Image Credit: Global Fintech Series
Byzanlink Secures $1M in Private Investment to Build Next-Gen Infrastructure for Tokenized Finance
- Byzanlink, a RWA tokenization platform, has secured $1 million in a private funding round.
- The funding round included early supporters like Outlier Ventures, NTDP Saudi, Smart IT Frame, and angel investors.
- Byzanlink, based in Dubai’s DMCC, aims to modernize access to institutional-grade investment opportunities through blockchain-based tokenization.
- With the new capital, Byzanlink plans to accelerate product development and strengthen operational frameworks to support regulatory alignment and institutional adoption.
Read Full Article
9 Likes
Hackernoon
313

Image Credit: Hackernoon
I Built an AI Copilot That Thinks in Exploits, Not Prompts
- Kuwguap shares the evolution of AI copilot RAWPA from basic tools to thinking brain.
- Community feedback led to integrating LOLBAS, GTFOBins, and WADCOMS into the app.
- New Neural Pathway Methodology gives RAWPA a learning capacity using real-world data.
- RAWPA's Neural Brain offers adaptive intelligence and personalized guidance for pentesters.
- The project, aiming to assist and rejuvenate pentesters, is community-driven and evolving.
Read Full Article
18 Likes
Medium
263
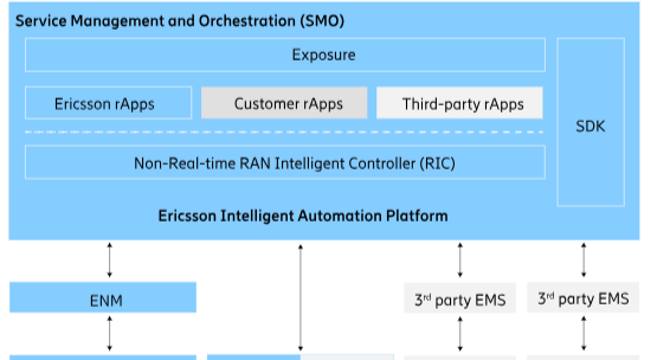
Image Credit: Medium
From Reactive to Proactive: How Ericsson’s Intelligent Automation Platform (EIAP) is…
- Telecom networks are evolving to handle the complexities of 5G and future 6G technologies, requiring dynamic and intelligent systems.
- Ericsson's Intelligent Automation Platform (EIAP) is a comprehensive solution designed to transform telecom networks by incorporating automation, security, operations, optimization, ecosystems, and innovation.
- EIAP offers features like Intelligent RAN Automation, Service Management and Orchestration, Non-Real-Time RAN Intelligent Controller, and rApps for various network management functions.
- Key benefits of EIAP include AI-driven proactive intelligence, enhanced security measures for Open RAN, innovative ecosystem development, and improved operational efficiency for telecom operators in deploying 5G services.
Read Full Article
15 Likes
Dev
55

Image Credit: Dev
How to Run AI Models Privately on Your AI PC with Model HQ; No Cloud, No Code
- Model HQ by LLMWare transforms any PC into a private, high-performance AI workstation.
- Enjoy 100+ AI models, fast document search, and natural language tools locally.
- No cloud dependency, vendor lock-in, or compromise on data privacy. Privacy-first AI experience.
Read Full Article
3 Likes
Medium
90

Image Credit: Medium
Is Your Password Safe? Some mistakes You Must Avoid?
- It is important to avoid mistakes when setting passwords to ensure security.
- Using the same password for multiple sites increases the risk of hacking.
- Simple or easily guessable passwords like 'qwerty' or '12345678' are weak and easily cracked.
- Changing passwords regularly, at least every few months, is recommended for increased security.
- Avoid typing passwords on public computers or shared systems to prevent unauthorized access.
Read Full Article
5 Likes
For uninterrupted reading, download the app