Cyber Security News
Dataprivacyandsecurityinsider
253

New Hires More Likely to Fall for Phishing + Social Engineering Attacks
- A recent study by Keepnet reveals that 71% of new hires click on phishing emails within 3 months of starting their job, making them 44% more susceptible to phishing and social engineering attacks compared to seasoned employees.
- The survey, based on responses from 237 companies, highlights that new employees lack adequate security training during onboarding and are more likely to be targeted due to their inexperience.
- New hires are particularly vulnerable to phishing attacks impersonating top company officials like the CEO or HR, with a 45% higher likelihood of falling for such emails compared to experienced staff.
- Providing adaptive phishing simulations and behavior-based training to new employees can reduce phishing risk by 30% post-onboarding, emphasizing the importance of early and continuous cybersecurity training for all staff.
Read Full Article
15 Likes
Securityaffairs
64

Image Credit: Securityaffairs
Kai West, aka IntelBroker, indicted for cyberattacks causing $25M in damages
- British national Kai West, also known as IntelBroker, has been indicted in the U.S. for operating a global hacking scheme that involved stealing and selling data, resulting in millions of dollars in damages.
- Kai West, aged 25, was arrested in France in February 2025 and is currently held in pre-trial detention as the U.S. seeks extradition for cybercrimes.
- West, who operated under the online alias 'IntelBroker,' is accused of leading CyberN[——] from 2023 to 2025, breaching over 40 organizations, stealing sensitive data, and causing over $25 million in damages by selling the stolen data.
- The charges against Kai West include computer intrusion and wire fraud, carrying potential sentences of up to 20 years. The case is being led by the Complex Frauds and Cybercrime Unit, with international partners assisting in the investigation.
Read Full Article
3 Likes
Medium
285

Image Credit: Medium
Why Video Game Enemies Are Getting Smarter (and Harder to Beat)
- Artificial intelligence (AI) is reshaping the gaming industry by enhancing gameplay, difficulty, and immersion.
- Smart NPCs now adapt, learn, and predict player moves using decision-making algorithms and neural networks.
- Procedural generation AI creates unique game worlds each time, offering infinite replayability in games like Minecraft and No Man’s Sky.
- AI is not only improving gameplay but also impacting storytelling, monetization strategies, and competitive balance in the gaming industry.
Read Full Article
17 Likes
Pymnts
817

Image Credit: Pymnts
Salesforce Says AI Is Doing 30% of Its Coding and Customer Service
- Salesforce's CEO, Marc Benioff, mentioned that AI is handling 30% to 50% of tasks in engineering, coding, and customer service at the company.
- Benioff highlighted the growth of AI's role in the work environment and the shift towards higher-value tasks for employees.
- The use of AI tools in industries is projected to contribute $3 trillion to $12 trillion in digital labor deployment.
- Salesforce is investing in AI agents and automation to increase productivity and efficiency, aiming to have 1 billion AI agents on its platform by year-end.
Read Full Article
13 Likes
TechCrunch
64

Image Credit: TechCrunch
US, French authorities confirm arrest of BreachForums hackers
- U.S. and French authorities have confirmed the arrests of five hackers accused of major hacks and involvement in a cybercrime forum.
- British national Kai West, known as IntelBroker, is indicted for leading a hacking group and causing over $25 million in damages targeting various victims.
- The hackers were involved in sensitive data sales and were part of a cybercrime forum named BreachForums, previously shut down by law enforcement agencies.
- West, along with four other individuals, faces extradition and charges related to computer intrusions, wire fraud, and more.
Read Full Article
3 Likes
TechCrunch
310

Image Credit: TechCrunch
Homeland Security warns of Iran-backed cyberattacks targeting US networks
- Homeland Security issued a bulletin warning of Iran-backed cyberattacks on U.S. networks.
- The bulletin highlighted expectations of Iranian government-backed hackers targeting U.S. networks amidst U.S.-Israel-Iran tensions.
- Recent events included U.S. and Israeli air strikes on Iran's nuclear program and cyberattacks by a pro-Israel hacking group.
- Iran's history includes offensive cyber capabilities, espionage operations, and disruptive cyberattacks targeting various entities.
Read Full Article
18 Likes
Pymnts
318

Image Credit: Pymnts
Visa and FIS to Offer Financial Institutions Value-Added Payment Capabilities
- Visa and FIS have expanded their partnership to offer new value-added payment capabilities to financial institutions, including stop payment services, wallet linking, and eCommerce fraud mitigation.
- The new offerings aim to help small financial institutions compete with larger ones by providing advanced solutions integrated into the FIS ecosystem.
- Expected by the end of the year, the new capabilities will include a digital campaign manager to facilitate marketing through various channels like augmented reality events and digital experiences.
- Visa and FIS collaboration targets enhancing growth and customer retention for financial institutions of all sizes, as outlined in a PYMNTS Intelligence report focusing on meeting digital-first generation expectations.
Read Full Article
19 Likes
The Verge
17
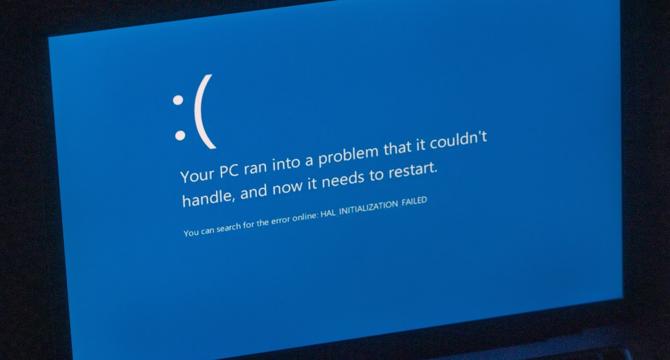
Image Credit: The Verge
Windows is getting rid of the Blue Screen of Death after 40 years
- Microsoft is overhauling the Blue Screen of Death (BSOD) error message in Windows 11 after nearly 40 years.
- The BSOD will be replaced by a Black Screen of Death, featuring a simplified black screen design without the traditional blue color, frowning face, and QR code.
- The new BSOD design will provide clearer information by listing the stop code and faulty system driver, aiding faster issue resolution without the need for complex analysis tools like WinDbg.
- Microsoft plans to introduce the new BSOD design in an upcoming update to Windows 11, aiming to improve clarity and the ability to pinpoint and rectify system issues more effectively.
Read Full Article
1 Like
Pymnts
193

Image Credit: Pymnts
Stablecoins ‘Perform Poorly’ as Money and Could Face Uphill Payments Battle
- Mastercard partners with Paxos to advance Global Dollar Network, boosting stablecoin payments.
- Competitors like Visa, Fiserv, and Stripe integrate stablecoin functionality into their platforms.
- Bank for International Settlements (BIS) report indicates stablecoins 'perform poorly' as money.
- Stablecoins face challenges in stability, acceptability, trust, compliance, and user experience.
Read Full Article
11 Likes
Secureerpinc
258

Image Credit: Secureerpinc
Why Investing in Cybersecurity Is Essential for Growing Businesses
- Investing in cybersecurity is crucial for businesses due to rising cyberattacks, with an average data breach cost of $4.35 million and global cybercrime cost estimated to surpass $10.5 trillion by 2025.
- Consequences of inadequate cybersecurity include compliance issues, reputation damage, and operational disruptions, emphasizing the need for proactive protection.
- Key elements for cybersecurity success include maintaining a strong online presence, endpoint protection, and implementing robust identity and access management strategies.
- A solid cybersecurity investment not only protects against threats but also enhances business resilience, customer trust, and overall business excellence in the rapidly evolving digital landscape.
Read Full Article
15 Likes
Global Fintech Series
215

Image Credit: Global Fintech Series
Experian Strengthens its Fraud Fighting Capabilities with Mastercard’s Identity Insights
- Experian integrates Mastercard's identity verification and fraud prevention technology into the Experian Ascend Platform to enhance decision-making and improve customer satisfaction.
- The collaboration aims to provide seamless and secure identity verification for Experian's global clients in various industries to combat fraud and cybercrime effectively.
- Mastercard's Identity Insights combined with Experian's fraud-detection capabilities offers robust protection against synthetic identity and application fraud on the Experian Ascend Platform.
- The joint solution by Experian and Mastercard delivers powerful identity assessment by uniting the Experian Ascend Platform with Mastercard's Identity Insights, streamlining customer processes and reducing fraud risks.
Read Full Article
12 Likes
Tech Radar
254

Image Credit: Tech Radar
People using ChatGPT as a security guru – and these are the questions everyone is asking
- Users are turning to ChatGPT for security advice, asking a range of questions from phishing avoidance to potential cybersecurity threats.
- NordVPN's research reveals both serious and bizarre security inquiries, with users seeking guidance on VPNs, data security, and even odd concerns like hackers stealing thoughts or passwords.
- There's a risk involved as users provide sensitive information to AI models like ChatGPT, unknowingly putting themselves at potential risk of scams, identity theft, and data breaches.
- Despite some lighthearted questions, the overall lack of cybersecurity understanding among users remains a concern, as hackers could exploit shared information for malicious purposes.
Read Full Article
15 Likes
Siliconangle
344

Image Credit: Siliconangle
New dope.security update offers native ChatGPT policy enforcement
- Dope.security Inc. has integrated native support for ChatGPT into its Cloud Application Control feature, allowing enterprise teams to manage access to OpenAI's tool directly on the endpoint.
- Administrators can now block, allow, or selectively enable ChatGPT based on roles and corporate policies, offering a balance between usability and control.
- The new integration enables administrators to configure ChatGPT access quickly via a user-friendly interface, applying rules such as domain-based permissions and department-specific access.
- Dope.security's platform enforces policies at the device level, enhancing decision-making speed and user experience while avoiding latency issues associated with traditional web gateways.
Read Full Article
20 Likes
Analyticsindiamag
259

Image Credit: Analyticsindiamag
India Lost ₹22,812 Crore to Cyber Fraud in 2024: Report
- India ranked second globally in 2024 for crypto attacks, recording 95 major attacks.
- Cybercrime complaints in India surged from 15.56 lakh in 2023 to 19.18 lakh in 2024, with citizens losing ₹22,812 crore in 2024.
- 82.6% of phishing campaigns in 2024 used AI-generated content, with a rise in QR code phishing attacks in India.
- Rural India is experiencing a rapid increase in cybercrime cases, highlighting the need for cybersecurity awareness and digital safety measures.
Read Full Article
15 Likes
Securityaffairs
236

Image Credit: Securityaffairs
Cisco fixed critical ISE flaws allowing Root-level remote code execution
- Cisco released patches to address two critical vulnerabilities in Identity Services Engine (ISE) and ISE Passive Identity Connector (ISE-PIC) that could allow remote attackers to execute code as root.
- The vulnerabilities, tracked as CVE-2025-20281 and CVE-2025-20282, enable remote, unauthenticated attackers to run arbitrary code with root privileges.
- No workarounds are available for these vulnerabilities, and Cisco provided fixed releases to address the issues.
- The Product Security Incident Response Team (PSIRT) states there have been no reported attacks in the wild exploiting these flaws.
Read Full Article
14 Likes
For uninterrupted reading, download the app