Cyber Security News
Medium
12

Image Credit: Medium
Decentralized Wireless Networks: Are They Sustainable?
- Decentralized wireless networks, known as DeWi, aim to democratize network access and challenge traditional telcos.
- Pioneers like Helium, Pollen Mobile, and XNET are implementing unique approaches to spectrum, scalability, and user incentives.
- Challenges arise in sustaining the networks due to issues like token rewards attracting excessive hardware deployment and insufficient data demand.
- Security concerns, such as fraudulent activities like signal manipulation and identity spoofing, threaten the integrity and sustainability of DeWi networks.
Read Full Article
Like
Tech Radar
423

Image Credit: Tech Radar
British man behind ‘IntelBroker’ hacker group charged with stealing millions
- A British man named Kai West has been charged by US law enforcement for allegedly hacking numerous organizations worldwide as part of the 'IntelBroker' cybercrime group, causing over $25 million in damages.
- West faces potential sentences of up to 20 years in prison for wire fraud and conspiracy to commit computer intrusions. The IntelBroker group targeted around 40 victims globally, including well-known firms such as AMD, Apple, and CISCO.
- The group's scheme, which allegedly ran from December 2022 to February 2025, involved selling stolen data to collect approximately $2 million. West, arrested in France, is currently facing extradition to the US.
- Authorities traced West to IntelBroker through a purchase of stolen data, linking his real identity via a cryptocurrency transaction and his Gmail account. This case highlights the FBI's efforts to combat cybercriminals globally.
Read Full Article
25 Likes
HRKatha
418

Image Credit: HRKatha
“Adapt & upskill or be a lagger”: Zerodha co-founder warns
- Nikhil Kamath, co-founder of Zerodha, emphasizes the importance of upskilling and continuous learning in anticipation of job losses to automation.
- Skills in AI, cybersecurity, big data, creative thinking, and environment preservation will be in high demand, while 39% of current skills are expected to lose relevance.
- By 2030, 92 million jobs will vanish, but 170 million new jobs will be created, with a net gain of 78 million jobs for those willing to adapt.
- While businesses plan to upskill or retrain employees, concerns linger over skill gaps, training availability, and the automation of certain roles.
Read Full Article
24 Likes
TechBullion
376

Image Credit: TechBullion
Best Digital Tools for Tracking and Managing Maritime Shipments
- Digital tools are essential for tracking and managing maritime shipments efficiently in the fast-paced shipping industry.
- Platforms like SHIPNEXT offer reliable real-time tracking and advanced technology to enhance shipment management.
- Carrier tracking systems provide clarity and confidence in monitoring shipments across the maritime supply chain.
- Investing in modern software for tracking and logistics is crucial for global businesses to stay competitive.
Read Full Article
22 Likes
Securityaffairs
393
Image Credit: Securityaffairs
APT42 impersonates cyber professionals to phish Israeli academics and journalists
- Iran-linked APT42, known as Educated Manticore, targets Israeli journalists, cybersecurity experts, and academics with phishing attacks by impersonating security professionals.
- APT42 focuses on highly targeted spear-phishing using techniques such as credential harvesting, surveillance operations, and malware deployment.
- The threat actors created fake Gmail login pages and Google Meet invitations to steal email credentials and 2FA codes from victims, gaining unauthorized access to their accounts.
- The group used custom phishing kits mimicking Gmail, Outlook, and Yahoo, employing live keyloggers and WebSocket connections to control the stolen data.
Read Full Article
23 Likes
Global Fintech Series
161

Image Credit: Global Fintech Series
Byzanlink Secures $1M in Private Investment to Build Next-Gen Infrastructure for Tokenized Finance
- Byzanlink, a RWA tokenization platform, has secured $1 million in a private funding round.
- The funding round included early supporters like Outlier Ventures, NTDP Saudi, Smart IT Frame, and angel investors.
- Byzanlink, based in Dubai’s DMCC, aims to modernize access to institutional-grade investment opportunities through blockchain-based tokenization.
- With the new capital, Byzanlink plans to accelerate product development and strengthen operational frameworks to support regulatory alignment and institutional adoption.
Read Full Article
9 Likes
Hackernoon
312

Image Credit: Hackernoon
I Built an AI Copilot That Thinks in Exploits, Not Prompts
- Kuwguap shares the evolution of AI copilot RAWPA from basic tools to thinking brain.
- Community feedback led to integrating LOLBAS, GTFOBins, and WADCOMS into the app.
- New Neural Pathway Methodology gives RAWPA a learning capacity using real-world data.
- RAWPA's Neural Brain offers adaptive intelligence and personalized guidance for pentesters.
- The project, aiming to assist and rejuvenate pentesters, is community-driven and evolving.
Read Full Article
18 Likes
Medium
262
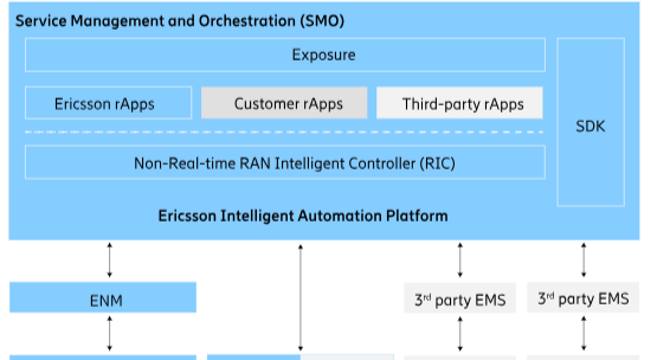
Image Credit: Medium
From Reactive to Proactive: How Ericsson’s Intelligent Automation Platform (EIAP) is…
- Telecom networks are evolving to handle the complexities of 5G and future 6G technologies, requiring dynamic and intelligent systems.
- Ericsson's Intelligent Automation Platform (EIAP) is a comprehensive solution designed to transform telecom networks by incorporating automation, security, operations, optimization, ecosystems, and innovation.
- EIAP offers features like Intelligent RAN Automation, Service Management and Orchestration, Non-Real-Time RAN Intelligent Controller, and rApps for various network management functions.
- Key benefits of EIAP include AI-driven proactive intelligence, enhanced security measures for Open RAN, innovative ecosystem development, and improved operational efficiency for telecom operators in deploying 5G services.
Read Full Article
15 Likes
Dev
55

Image Credit: Dev
How to Run AI Models Privately on Your AI PC with Model HQ; No Cloud, No Code
- Model HQ by LLMWare transforms any PC into a private, high-performance AI workstation.
- Enjoy 100+ AI models, fast document search, and natural language tools locally.
- No cloud dependency, vendor lock-in, or compromise on data privacy. Privacy-first AI experience.
Read Full Article
3 Likes
Medium
89

Image Credit: Medium
Is Your Password Safe? Some mistakes You Must Avoid?
- It is important to avoid mistakes when setting passwords to ensure security.
- Using the same password for multiple sites increases the risk of hacking.
- Simple or easily guessable passwords like 'qwerty' or '12345678' are weak and easily cracked.
- Changing passwords regularly, at least every few months, is recommended for increased security.
- Avoid typing passwords on public computers or shared systems to prevent unauthorized access.
Read Full Article
5 Likes
Siliconangle
419

Image Credit: Siliconangle
How open-source developers can meet global cybersecurity laws — before it’s too late
- Countries worldwide are updating their cybersecurity laws to address new attack pathways in the digital realm, impacting open-source developers.
- The EU's Cyber Resilience Act (CRA) is set to influence open-source and enterprise software development globally, with mandatory compliance required by December 2027.
- Developers need to focus on secure-by-design development and transparency, as non-compliance with cybersecurity laws could lead to severe penalties, including fines up to 2.5 times annual revenue per infraction.
- Open-source developers must adapt to new concepts like software bill of materials and ensure compliance with evolving cybersecurity standards to navigate the regulated landscape while maintaining innovation.
Read Full Article
25 Likes
Siliconangle
214

Image Credit: Siliconangle
Chronosphere redefines cloud-native observability with Logs 2.0 and real-time data control
- Chronosphere Inc. is redefining cloud-native observability with its platform by providing deep real-time visibility into complex, distributed systems.
- Chronosphere focuses on open-source standards to allow customers to control their data format for observability in cloud-native environments.
- Chronosphere introduces Logs 2.0, a new product offering end-to-end log management capabilities integrated with metrics and traces for proactive performance management.
- Chronosphere tackles ballooning telemetry data issues by offering data control, cost optimization, and intelligent signal prioritization for cloud-native environments.
Read Full Article
12 Likes
Gritdaily
43

Image Credit: Gritdaily
The Challenge of Ultra-Luxury: How to Ensure Total Security Without Compromising Design or Freedom
- Tyrian Residences in Estepona, Spain showcases strong security measures without compromising architectural integrity.
- The building offers 40 residences designed as villas in the sky with top-notch amenities and WELL-certified design.
- Security features include a gated entry point, laser detection, network of cameras, automatic bollards, and smart card access.
- Privacy is ensured through private elevators, dual entrances for residents and staff, and smart card-controlled access across all areas.
Read Full Article
1 Like
Siliconangle
376

Image Credit: Siliconangle
F5 introduces post-quantum cryptography tools for application security
- F5 Inc. introduces new post-quantum cryptography solutions to enhance application security against quantum computing threats.
- These new tools aim to protect sensitive data across various environments and address vulnerabilities posed by quantum computing attacks.
- F5 emphasizes the importance of transitioning to post-quantum cryptography to avoid disruptions and ensure secure operations.
- The platform offers end-to-end security, compliance support, and performance optimization through integrated post-quantum encryption capabilities.
Read Full Article
22 Likes
Dev
351

Image Credit: Dev
🛡️ How RedXShield is Changing Africa’s Cybersecurity Game
- RedXShield is an African-built cybersecurity platform that stands out for learning from African attack patterns, unlike most tools trained on Western data.
- Key features of RedXShield include local threat intelligence, lightweight API, explainable AI, and being MIT licensed.
- The tool focuses on African-first detection, provides transparent results, and has been successfully implemented in various cybersecurity initiatives.
- Developed by Dennis Muchiri, RedXShield has won awards, protects African fintech companies, and emphasizes the importance of local solutions for global impact in cybersecurity.
Read Full Article
21 Likes
For uninterrupted reading, download the app