Cyber Security News
Securityaffairs
86
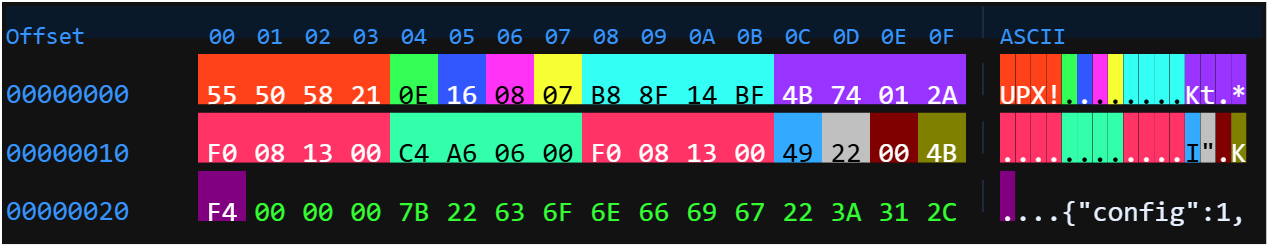
Image Credit: Securityaffairs
Prometei botnet activity has surged since March 2025
- Prometei botnet activity has surged since March 2025, with a new malware variant rapidly spreading, according to Palo Alto Networks.
- The botnet targets Linux systems for Monero mining and credential theft, using modular architecture and evasion tactics to avoid detection.
- Prometei allows attackers to control compromised systems for cryptocurrency mining and credential theft, with a focus on the Linux variant.
- First discovered in 2020, Prometei exploits vulnerabilities like EternalBlue and spreads through brute-force attacks.
- The malware primarily focuses on Monero mining and credential theft, displaying financial motivations without state ties.
- The latest Prometei variant is distributed via an HTTP GET request, utilizing UPX-packed Linux ELF files disguised as .php scripts.
- Prometei malware uses Ultimate Packer for eXecutables (UPX) for obfuscation, requiring analysts to strip a JSON config trailer for static analysis.
- Analyzing the configuration JSON reveals system information collected by the malware, including processor, motherboard, OS, uptime, and kernel details.
- Detection of the evolving Prometei botnet can be done with YARA rules targeting UPX and its configuration JSON trailer, but defenders must remain alert.
- The report provides Indicators of Compromise (IoCs) related to the Prometei botnet activity.
Read Full Article
5 Likes
VoIP
117

Image Credit: VoIP
SK Telecom Resumes New Subs After Cyber Breach Recovery
- SK Telecom faced a major cybersecurity breach affecting up to 26.9 million customers earlier this year.
- The breach occurred in summer 2022 but was only disclosed in April after being reported to KISA.
- 23 of SKT's servers were impacted, potentially exposing 9.32 gigabytes of USIM-related data.
- 26.9 million IMSI numbers were compromised in the breach.
- SKT offered free USIM card replacements to affected customers, leading to a nationwide shortage of USIMs.
- SKT paused new subscriber acquisitions due to the USIM shortage, following government advice for two months.
- The Ministry of Science and ICT in South Korea lifted the administrative guidance, allowing SKT to resume acquiring new subscribers after securing sufficient USIM stock.
- SKT received approval to onboard new customers and continues to prioritize USIM replacements for affected subscribers.
- Despite the progress, SKT's CEO estimates a potential loss of up to 2.5 million customers to rival operators, leading to a projected revenue loss of up to $5 billion over three years.
Read Full Article
7 Likes
Hackernoon
168

Image Credit: Hackernoon
AI Security Posture Management (AISPM): How to Handle AI Agent Security
- AI Security Posture Management (AISPM) focuses on securing AI agents, their memory, external interactions, and behavior in real-time, addressing new risks like hallucinated outputs and prompt injections.
- AI systems introduce entirely new challenges that traditional security tools were not designed to handle, emphasizing the need for AISPM in monitoring and securing AI reasoning and behavior.
- AISPM addresses unique vulnerabilities like AI hallucinations, prompt injection attacks, and complex, cascading interactions between AI agents that require a different approach to security posture.
- The four access control perimeters of AI agents include prompt filtering, RAG data protection, secure external access governance, and response enforcement to secure the entire flow of AI operations.
- AISPM principles focus on intrinsic security, continuous monitoring, chain of custody auditing, delegation boundaries, trust TTLs, and cryptographic validation between AI agents to ensure a secure AI environment.
- Tools and emerging standards for AISPM integrate access control with AI frameworks, support data validation and structured access, and standardize AI-to-system interactions to enhance security measures for AI systems.
- AISPM is essential as AI systems grow more autonomous, emphasizing the need for real-time risk assessment, secure data validation, and standardized interactions between AI agents for enhanced security and trust.
- The future of AISPM involves dynamic trust scoring for AI agents, controlling behavior at critical points, and ensuring trust, compliance, and safety in AI-driven applications.
Read Full Article
10 Likes
Semiengineering
324

Image Credit: Semiengineering
HW Security: Multi-Agent AI Assistant Leveraging LLMs To Automate Key Stages of SoC Security Verification (U. of Florida)
- Researchers at the University of Florida have published a technical paper on using large language models (LLMs) for SoC security verification.
- The paper introduces SV-LLM, a multi-agent assistant system that aims to automate and enhance SoC security verification processes.
- The traditional verification techniques for complex SoC designs face challenges in automation, scalability, comprehensiveness, and adaptability.
- LLMs offer advanced capabilities in natural language understanding, code generation, and reasoning, presenting a promising solution for SoC security verification.
- SV-LLM employs a multi-agent approach where specialized LLM agents collaborate to address various security verification tasks efficiently.
- The system integrates agents for tasks like verification question answering, security asset identification, threat modeling, test plan generation, vulnerability detection, and bug validation through simulation.
- Agents within SV-LLM use different learning paradigms such as in-context learning, fine-tuning, and retrieval-augmented generation (RAG) to optimize their performance.
- SV-LLM aims to reduce manual intervention, enhance accuracy, and speed up the security analysis process, aiding in early risk identification and mitigation during the design phase.
- The paper demonstrates the transformative potential of SV-LLM in hardware security through case studies and experiments, showcasing its practicality and effectiveness.
- Overall, SV-LLM introduces an innovative approach to SoC security verification leveraging LLMs and multi-agent systems for improved efficiency and accuracy.
Read Full Article
19 Likes
Hackernoon
73

Image Credit: Hackernoon
The 5 Most Common Messaging‑SDK Vulnerabilities (and How to Fix Them)
- A SaaS integrator experienced a data leakage incident in which client messages were sent to the wrong recipients due to a shared token vulnerability.
- Messaging-SDKs are vulnerable to attacks due to high-value data exposure, real-time blast radius, cultural haste in security implementation, and widespread attack surface.
- The top 5 vulnerabilities in messaging-SDKs include global access tokens & tenant confusion, missing signature/webhook verification, replay attacks, token leakage via logs & metrics, and unsafe attachment & media handling.
- Security testing tools like Microsoft RESTler, WuppieFuzz, Imperva API-Attack Tool, and OWASP ZAP are recommended to address vulnerabilities in messaging-SDKs.
- A DIY 10-minute test scenario involving token mismatch, signature tampering, replay attack, and attachment spoofing is suggested using Postman and Python.
- An automated test harness script can be integrated into CI pipelines to conduct cross-tenant ID swaps, signature removal & tampering, timestamp replays, attachment spoofing, and log redaction checks.
- Implementing security controls in SDKs and utilizing open-source fuzzers in CI can help contain breaches, reduce cognitive load, and earn audit trust without hindering product development.
Read Full Article
4 Likes
Global Fintech Series
103

Image Credit: Global Fintech Series
Bluefin and Authvia Partner to Enable Secure “Text, Click, Pay” Payments via PayConex
- Bluefin and Authvia have partnered to launch an integration enabling secure, app-free payments via SMS, RCS, and email using PCI-compliant tokenization technology.
- Authvia's TXT2PAY allows businesses to request PCI-compliant, tokenized payments within a message thread, simplifying the payment process for customers.
- Customers receive a payment link via text, click on it, and securely complete their payment, improving cash flow and the overall customer experience.
- The integration of TXT2PAY into Bluefin's PayConex platform ensures data protection standards are met and leverages PCI-validated security measures such as tokenization and encryption.
- This partnership aims to merge secure commerce with consumer behavior by offering a seamless payment solution directly through messaging channels people use daily.
Read Full Article
6 Likes
Hackernoon
389
Image Credit: Hackernoon
I Built an AI Copilot for Pentesting—Then Turned It Off
- A developer created RAWPA (Rodney the Advanced Web Pentesting Assistant) to assist with pentesting by providing additional ideas.
- RAWPA is not meant to automate the pentesting process but to offer guidance when the user's checklist runs out.
- The developer initially built an AI copilot using a RAG model, but faced challenges with noise in responses and code debugging.
- The AI feature was put on hold, and an admin panel with a toggle to switch off the AI was added.
- The developer is currently focusing on deep-dive research to validate methodologies for RAWPA.
- The project was inspired by lostsec's site, emphasizing the importance of tools that augment human thinking.
- Community input, including future feature ideas like gamification and collaborations, is shaping RAWPA's vision.
- The developer aims to make RAWPA a reliable, community-driven resource.
- More details on the development journey can be found on the developer's personal blog.
- Community engagement and feedback are encouraged to improve RAWPA.
- RAWPA's goal is to help individuals overcome obstacles in pentesting and facilitate learning.
- The developer can be reached on LinkedIn for methodologies, ideas, or suggestions.
- The overall focus is on assisting users in getting unstuck and enhancing their knowledge.
- For more information, visit the developer's blog at https://kuwguap.github.io/posts/series-2-implementing-wpa-in-rawpa-part-1/
Read Full Article
23 Likes
Dev
220

Image Credit: Dev
Understanding RSA vs. AES: Which Encryption Should You Use?
- Encryption plays a crucial role in ensuring secure communication in the digital world, with RSA and AES emerging as key encryption algorithms.
- RSA, or Rivest-Shamir-Adleman, is an asymmetric encryption algorithm utilizing separate public and private keys for encryption and decryption.
- RSA's strength lies in its reliance on the difficulty of factoring large prime numbers, making it ideal for key exchange, digital signatures, and authentication.
- However, RSA is known to be slower and computationally heavier compared to symmetric encryption techniques.
- AES, the Advanced Encryption Standard, functions as a symmetric encryption algorithm where the same key is used for both encryption and decryption processes.
- AES operates on data blocks using substitution-permutation networks, ensuring efficient encryption and decryption.
- It is recognized for its speed and lightweight nature, making it well-suited for tasks like bulk data encryption and is commonly used in various applications, including Wi-Fi security and messaging apps.
Read Full Article
13 Likes
Analyticsindiamag
65

Image Credit: Analyticsindiamag
India’s Toughest Customers and Agentic AI Might Be Zscaler’s Real Moat
- Zscaler's 'Zero Trust Exchange' is vital but agentic AI is gaining importance at their Zenith 2025 summit.
- India has become a key market for Zscaler, growing from 13th to 5th place in sales.
- Indian customers are known for being tough negotiators, driving Zscaler's technical advancements.
- Zscaler is investing heavily in India for development and sales due to the rapid adoption of technology.
- Adam Geller of Zscaler discusses the applications of generative AI in their products and the need to secure customer adoption of such AI.
- Zscaler is using AI to improve data identification internally and build tools that aid users.
- Zscaler processes 500 billion events daily, leveraging AI from predictive to generative AI and distributed AI agents.
- There's a concern over the shift to distributed AI agents, posing new risks with data control.
- Zscaler is an AI-first company with AI embedded in their products, focusing on improving AI capabilities.
Read Full Article
Like
Dev
121

Image Credit: Dev
Unlocking Hyper-Security: The Power of AI in Multi-Modal Biometric Systems
- The article explores the shift towards multi-modal biometric systems empowered by AI for heightened security in identity verification.
- Multi-modal biometric systems blend traits like facial recognition, voice recognition, and fingerprints for enhanced security.
- Advantages include increased security against spoofing, improved accuracy, and broader user applicability.
- Architectural fusion strategies like serial, parallel, and hierarchical fusion impact system resilience and effectiveness.
- Artificial Intelligence aids in feature extraction, robust fusion, liveness detection, and adaptive authentication in biometric systems.
- Use cases range from high-security access control to healthcare patient identification, showcasing diverse applications of multi-modal biometrics.
- Challenges include data integration, computational overhead, privacy concerns, bias mitigation, and regulatory compliance in biometric systems.
- Future trends include emerging modalities, blockchain integration, explainable AI, and continuous authentication for advanced biometric authentication.
- The article illuminates the potential and challenges of developing hyper-secure multi-modal biometric systems with AI for the future of digital security.
Read Full Article
7 Likes
Medium
410
Image Credit: Medium
What is the Dark Web and How to Keep Your Data Safe?
- The Dark Web serves various purposes, including privacy protection, avoiding tracking, and engaging in illegal activities.
- Accessing the Dark Web is not as simple as using regular search engines like Google or Bing; specialized tools like Tor are necessary, as it operates on unique network paths.
- Anonymity is crucial on the Dark Web, with most users avoiding real names or emails, making user tracing challenging due to hidden IP addresses.
- Illegal activities, such as the buying and selling of stolen data, hacking tools, and fake IDs, are common on the Dark Web, leading to various criminal acts being linked to its use.
- Hackers frequently steal login credentials from websites and then sell them on Dark Web platforms, including sensitive information like credit card details, passwords, and email accounts.
Read Full Article
24 Likes
Medium
346

Is your IP a Tor exit node?
- Tor routes internet traffic through volunteer-operated servers to provide anonymity and privacy.
- Legitimate users may utilize Tor for online privacy, but threat actors can exploit it for malicious activities.
- Detection of Tor activity within an organization should raise concerns and trigger investigations.
- A Python script has been developed to analyze network traffic and user authentication logs for detecting malicious Tor traffic.
- Communication with both entry and exit points of the Tor network may indicate a connection to a hidden C2 server.
- Accessing a user account from a Tor exit node could signify a threat actor using stolen credentials while hiding their IP address.
- The script utilizes a live list of Tor exit nodes from the Official Tor Project to identify malicious traffic.
- Timely ingestion of logs is crucial for accurate detection, as the list of active exit nodes changes frequently.
- Sophisticated threat actors may avoid Tor to prevent detection in corporate environments, opting for other techniques like commercial VPNs.
- Less advanced adversaries may still leverage Tor, leading to detectable patterns of traffic.
- Using commercial VPNs or compromised devices is a common tactic among threat actors to disguise malicious traffic.
- The script aims to identify potentially damaging but less sophisticated attacks relying on the Tor network.
- The full script can be found in the developer's Github Repository.
Read Full Article
20 Likes
Medium
103

Image Credit: Medium
The Unspoken Threat Of Digital Guilt Engineering
- A new form of cyber manipulation called digital guilt engineering is emerging, focusing on emotional control rather than monetary gain.
- Attackers leverage behavioral metadata, such as online behavior and emotional responses, to manipulate individuals without demanding money explicitly.
- Digital guilt engineering exposes vulnerabilities by knowing what triggers guilt, shame, or anxiety in individuals.
- Emotional manipulation is enabled by the leakage of behavioral metadata from mental health apps, increasing the risk of emotional blackmail.
- AI tools can now detect emotions like sadness or guilt with high accuracy, leading to personalized and emotionally manipulative messages.
- Recommendations include using mental health apps with end-to-end encryption, limiting app permissions, and being cautious about online content.
- Urgent actions needed include stronger data protection laws, third-party security audits for mental health apps, and awareness campaigns on emotional manipulation.
- Cybersecurity efforts should focus on safeguarding emotional and behavioral data, in addition to protecting devices.
Read Full Article
6 Likes
Embedded
385

Microchip Enhances TrustMANAGER Platform to Address Evolving Global Cybersecurity Standards for IoT Devices
- Microchip Technology upgrades TrustMANAGER platform to meet evolving global cybersecurity standards for IoT devices.
- Concern over outdated firmware on IoT devices leading to vulnerabilities addressed by Microchip's enhancements.
- TrustMANAGER platform now includes features like secure code signing, FOTA update delivery, and remote firmware management.
- Enhancements aim to ensure compliance with the European Cyber Resilience Act imposing strict cybersecurity obligations in the EU.
- Microchip aligning with ETSI EN 303 645 for consumer IoT security and ISA/IEC 62443 for industrial automation systems.
- ECC608 TrustMANAGER integrates Kudelski IoT’s keySTREAM SaaS for secure key and digital certificate management.
- Microchip's WINCS02PC Wi-Fi module achieves RED certification, meeting EU wireless device security directives.
- TrustMANAGER offers solutions for security, device lifecycle management, fleet management, and regulatory compliance in IoT.
- Fully compatible with MPLAB X IDE, TrustMANAGER is supported by CryptoAuth PRO board and CryptoAuthLib software library.
- Trust Platform Design Suite provides educational onboarding and firmware examples for AWS integration.
Read Full Article
23 Likes
Dev
229

Image Credit: Dev
CVE-2021-34473: Microsoft Exchange Server Remote Code Execution Vulnerability
- CVE ID: CVE-2021-34473
- Vulnerability Name: Microsoft Exchange Server Remote Code Execution Vulnerability
- Date Added: 2021-11-03, Due Date: 2021-11-17
- Description: Microsoft Exchange Server contains a remote code execution vulnerability
- Used in Ransomware Campaigns: Known
- Action: Apply updates per vendor instructions
- Additional Notes: https://nvd.nist.gov/vuln/detail/CVE-2021-34473
- Related Security News: Hackers target over 70 Microsoft Exchange Servers for stealing credentials, various ransomware campaign activities reported, Microsoft's discoveries of global cyber attacks by Sandworm subgroup, and more.
- More CVEs Info: Common Vulnerabilities & Exposures (CVE) List
Read Full Article
13 Likes
For uninterrupted reading, download the app