Information Technology (IT) News
Minis
887

Image Credit: Minis
Nordic region emerges as pocket of hope for Indian IT as other markets slow
- Indian IT giants, like TCS and Infosys, are thriving in the Nordic market, which grew from $24.4B in 2018 to $29.5B in 2023.
- With TCS having 20,000 employees and Infosys over 2,500, Indian companies are strategically expanding in the Nordics, establishing local centers and tailored strategies.
- Indian firms offer a 10-15% cost advantage, evidenced by deals like Infosys' $454M Danske Bank agreement, showcasing their prowess in digital transformation.
- Nordic clients choose Indian IT partners for sustainable cost reductions (1.5-2%), and managed-services outsourcing expenditures in the Nordics have rebounded by 9% in H1 2023.
Read Full Article
9 Likes
Minis
784
Image Credit: Minis
Platform Engineering: The Future of Software Development
- Platform engineering is a tech approach boosting app delivery and business value via self-service tools and automated infrastructure operations.
- It responds to the complexity of modern software architectures, alleviating the burden on non-expert end users managing intricate services.
- By 2026, 80% of large software engineering organizations are expected to establish platform engineering teams, acting as internal providers of reusable services and tools.
- Platform engineering involves dedicated product teams creating tailored engineering platforms, often starting with internal developer portals. The goal is to provide a seamless, self-service experience for developers and streamline the software development process.
Read Full Article
7 Likes
Minis
1.7k

Image Credit: Minis
Why techies prefer GCCs over IT services companies?
- Techies favor Global Capability Centers (GCCs) and product firms with offer acceptance rates of 65-70%, surpassing the 50-55% rates for traditional IT services.
- GCCs provide better learning curves and long-term projects, allowing tech professionals to gain in-depth knowledge, from conception to execution.
- Techies are attracted to GCCs for progressive HR policies, flexibility, LGBTQ+ inclusivity, and appealing campus facilities, with occasional short-duration foreign visits for training.
- Product firms and GCCs offer significantly higher annual salary increments (up to 80%) compared to IT services companies (limited to 50%).
Read Full Article
8 Likes
Minis
1.6k

Image Credit: Minis
Muskan Agrawal, India's 'top woman coder' and a BTech graduate, secures Rs 60 lakh job from LinkedIn
- Muskan Agrawal from IIIT Una secured a historic job offer of Rs 60 lakh per annum from LinkedIn, setting a new benchmark for the highest-ever salary package in the institute.
- Her journey started with winning the 'top woman coder' title at TechGig Geek Goddess in 2022, triumphing over 69,000 women coders.
- Muskan's active involvement in open-source projects earned her a spot in LinkedIn's mentorship program, providing valuable guidance from industry professionals.
- Joining LinkedIn in July 2023, Muskan now holds the role of a software development engineer, showcasing her skills and contributing to IIIT Una's successful placement record.
Read Full Article
22 Likes
Minis
900
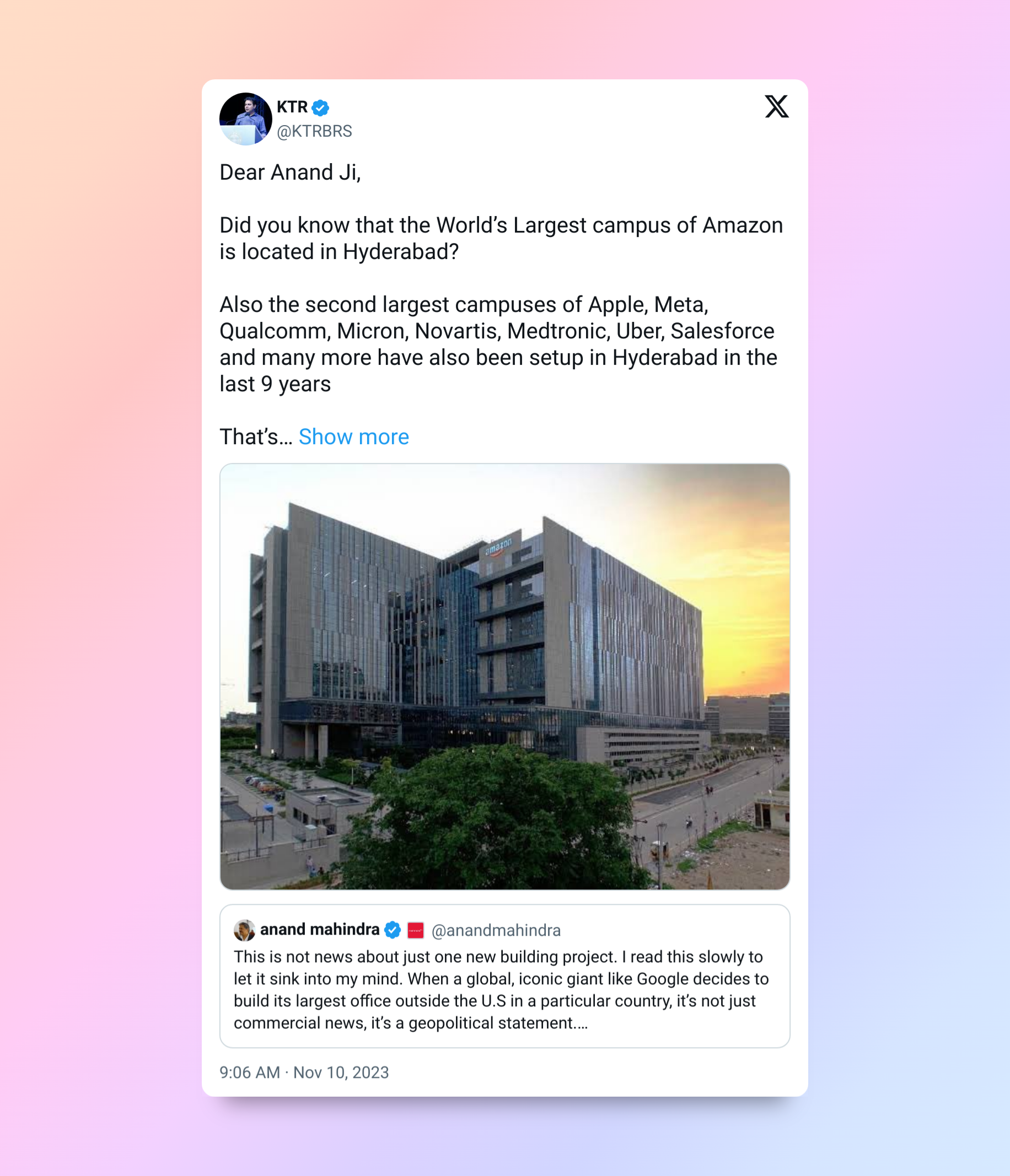
Image Credit: Minis
‘Amazon, Apple, Meta, Uber, Salesforce have campuses’: Telangana minister KTR on ‘Happening Hyderabad’
- Anand Mahindra heaped praises on India’s rapid growth, quoting a tweet on Google building its second-largest office outside of the US in Hyderabad.
- Responding to Anand Mahindra, the minister said that Amazon too has the world’s largest campus in Hyderabad. Not only that, Hyderabad houses the second-largest campuses of “Apple, Meta, Qualcomm, Micron, Novartis, Medtronic, Uber, Salesforce”. “That’s why I call it ‘Happening Hyderabad’,” he said.
- Social media users express pride in Hyderabad's rapid growth, crediting stable governance and government policies.
Read Full Article
8 Likes
Minis
2.5k

Image Credit: Minis
Software companies only offering 18-22% hikes to job jumpers
- Salary hikes for technology workers switching jobs have dropped by nearly half from the previous financial year due to slowing demand for tech services globally.
- Software firms are now offering hikes of 18-22% to those jumping jobs, while earlier, such candidates would command an increase of over 40% — even up to 100-120% — in remuneration, according to data from staffing firms accessed by ET.
- Offer ranges for many roles have dropped by as high as 35% - 40%, and the current salary ranges in offer are well in the moderated zone with no unusual hikes in play.
- Full stack engineers are witnessing an average of 8%-16% drop to getting Rs 12 - 28 Lakh per annum this year as compared with Rs 15 - 32 Lakh per annum in FY22.
Read Full Article
15 Likes
Minis
2.2k

Image Credit: Minis
IT staffers stick to jobs after great resignation
- In 2021 and early 2022, the IT job market was highly competitive, with IT employees receiving multiple job offers and ghosting employers after accepting offers. This created a nightmare for HR executives.
- Fast forward to the present, and it's now a job seeker's market, with significantly lower employee attrition rates. TCS's attrition rate dropped to 14.9%, and Infosys's attrition rate nearly halved to 14.6% in the September quarter.
- Weakening global economic conditions and geopolitical events like the Ukraine war have led to a drop in IT demand, causing some companies to cut hiring and even reduce overall employee numbers.
Read Full Article
2 Likes
Minis
1.3k
Image Credit: Minis
Data scientists, cloud engineers get highest salaries in IT companies
- Data scientists and cloud engineers are highly demanded and highest-paid tech professionals in India's IT and ITeS industry.
- Data scientists earn an average of Rs 11 lakh per year, while cloud engineers earn around Rs 10.51 lakh annually.
- Program managers in non-core IT roles have the highest salaries, averaging Rs 26 lakh, thanks to their managerial responsibilities.
- Demand for data scientists and cloud engineers is driven by the increasing digitization of businesses and the importance of data-driven decision-making.
Read Full Article
21 Likes
Minis
1.1k

Image Credit: Minis
'Will honour past offers before going to campuses': Wipro
- The company pledges to honor all pending offer letters before resuming on-campus hiring for freshers.
- Wipro has experienced a hiring slowdown, with a net reduction of 5,051 employees in the second quarter of FY24.
- The attrition rate decreased from 17.3% in the previous quarter to 15.5% in Q2.
- The company reported a slight drop in revenue for Q2FY24, with gross revenue at Rs 225.2 billion ($2.7 billion), and a 2.3% decline in IT services segment revenue.
Read Full Article
8 Likes
Minis
3.1k

Image Credit: Minis
TCS, Infosys, Wipro, HCLTech employee count drops by 21,000 in second quarter
- Top four IT companies in India saw a decline of 21,213 employees in Q2 of FY24 compared to Q1 headcount.
- TCS had the steepest decline in headcount, with 6,333 fewer employees, the largest drop in at least five years.
- Infosys, the second-largest IT company, saw its headcount decrease by 7,530 employees, while HCLTech had 2,299 fewer employees, and Wipro saw a reduction of 5,051 employees.
- Wipro's attrition rate fell to 15.5% in the September quarter, while large peers like TCS, Infosys, and HCLTech also saw a decrease in their attrition rates, signaling improved employee retention.
Read Full Article
13 Likes
Minis
3.7k

Image Credit: Minis
As TCS calls staff back to office, focus is on dress code
- TCS is urging employees, especially recent hires, to embrace a professional dress code as they return to the office.
- Milind Lakkad, TCS's Chief Human Resource Officer, emphasizes the significance of working from the office for instilling TCS values and professionalism.
- The company's dress code policy expects associates to follow business casuals (tucked-in full-sleeved shirts with trousers for men and business dresses for women) from Monday to Thursday. Business formals are required for formal events and client visits. Fridays allow for smart casuals.
Read Full Article
36 Likes
Minis
1.3k

Image Credit: Minis
India's top IT firms grapple with record high employee wage costs
- Employee wage costs at Tata Consultancy Services (TCS) reached a six-year high, constituting 77.4% of total expenditure in the September quarter.
- HCL Technologies also experienced a similar increase, with employee wage costs making up 69.6% of their total expenses during the same period.
- Infosys, on the other hand, observed a slight decrease in employee expenses, but they still accounted for more than 60% of total expenses, highlighting cost pressures in the industry.
- The industry trend showcases a concern regarding high employee costs, driven by lateral hiring at a 30% hike and challenges in retaining talent amidst efforts to reduce expenses by limiting campus recruitment.
Read Full Article
17 Likes
Minis
5.6k

Image Credit: Minis
TCS, Infosys, HCLTech: Hiring crashes across Indian IT companies in Q2 FY24
- All three major IT companies reported a significant decline in headcount numbers during the second quarter of the fiscal year 2024.
- Tata Consultancy Services (TCS) witnessed a net decline of 6,333 employees on a quarterly basis, with a decrease in headcount both on a quarterly and yearly basis.
- Infosys reported a net fall of 7,530 employees sequentially and has also slowed down on hiring, attributing it to a significant fresher bench.
- HCL Technologies (HCLTech) saw a net headcount decline of 2,299 in Q2 FY24, marking the second consecutive quarter of headcount decline. CEO and MD C Vijayakumar mentioned that freshers hired in the last 18 months were ready to be deployed, reducing the need for new hires.
Read Full Article
12 Likes
Minis
1.8k

Image Credit: Minis
Tech companies in Israel may shift operations to India if war escalates: Report
- Global technology companies in Israel may consider shifting their business operations to India, the Middle East, or Eastern Europe if the Israel-Hamas conflict escalates further.
- Over 500 global companies, including Microsoft, Intel, and Google, operate in Israel, with Indian firms like Wipro and TCS also having a presence in the country.
- The Israeli high-tech industry, which has been a rapidly growing sector, may face disruptions due to the conflict, potentially involving a full-scale invasion of the Gaza Strip.
- Intel, Israel's largest private employer and exporter, is closely monitoring the situation and taking steps to safeguard its workers as the conflict continues.
Read Full Article
26 Likes
Minis
1.2k

Image Credit: Minis
26-year-old Bengaluru techie dies after collapsing 500 mt before Ironman triathlon finish line
- A 26-year-old techie, Kamakhya Siddharth Shrivastava, died during an Ironman triathlon in Goa, collapsing just 500 meters from the finish line.
- Shrivastava, an associate manager in Bengaluru, was participating in the individual category of the Ironman 70.3 Goa race.
- He received immediate medical assistance and was rushed to a nearby hospital but succumbed to multiple organ failure the following day.
- The Ironman 70.3 Goa race involves swimming, cycling, and running. The event drew participants from over 50 nations.
Read Full Article
13 Likes
For uninterrupted reading, download the app