Malware News
Securityaffairs
304
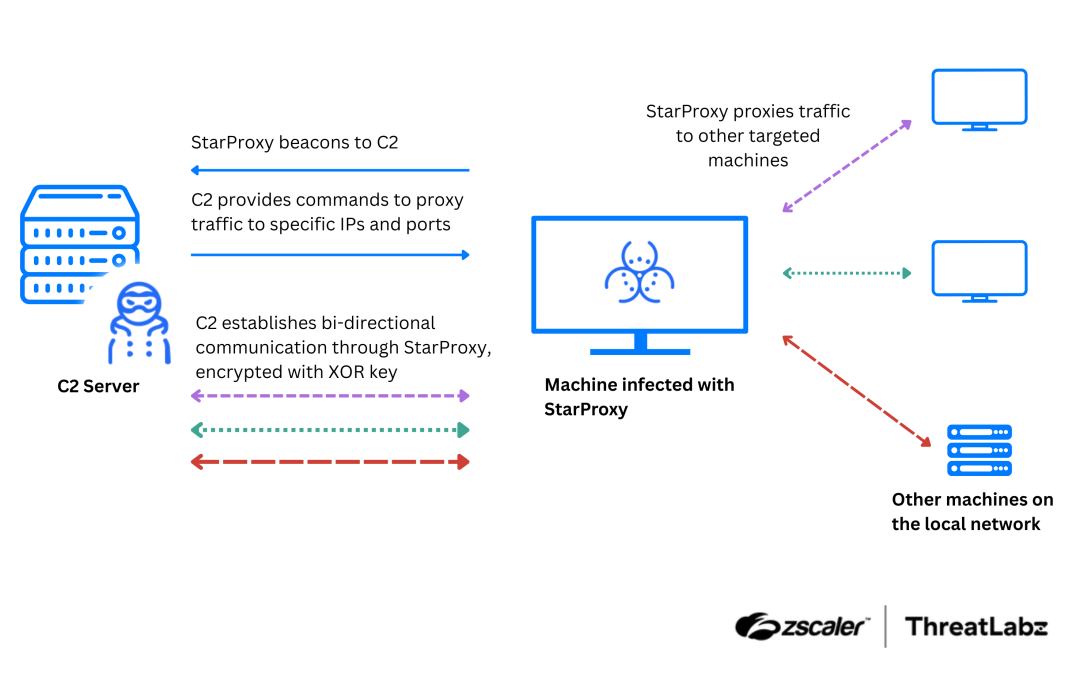
Image Credit: Securityaffairs
China-linked APT Mustang Panda upgrades tools in its arsenal
- China-linked APT group Mustang Panda deployed a new custom backdoor, MQsTTang, in recent attacks targeting Europe, Asia, and Australia.
- The APT group has been active since at least 2012, targeting American and European entities as well as Asian countries.
- Recent campaigns of APT Mustang Panda utilized European Union reports on the conflict in Ukraine as lures to deploy malware.
- The group has introduced new tools such as MQsTTang backdoor, StarProxy lateral movement tool, and several keyloggers for enhanced stealth and functionality.
Read Full Article
18 Likes
Cybersecurity-Insiders
190

Australia mandates reporting of ransomware payments
- Australia has mandated businesses to report ransomware payments.
- Starting from May 30, 2025, if a business in Australia decides to pay a ransom, it is legally required to report the incident to the government within 72 hours.
- The new requirement is part of the Cyber Security Act, aimed at improving the government's ability to respond to cyber threats and track cybercrime trends.
- The law applies to businesses and organizations in Australia with an annual turnover of $3 million or more, as well as public entities responsible for critical infrastructure.
Read Full Article
11 Likes
Securityaffairs
363
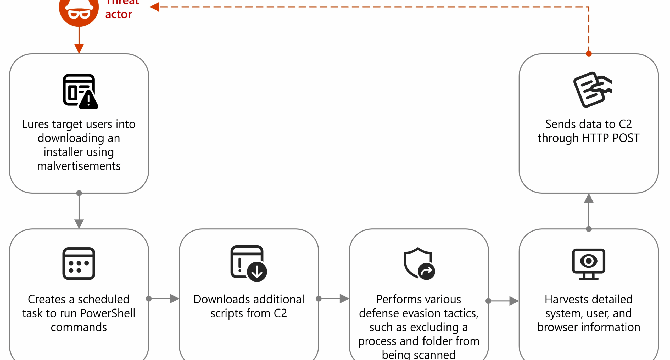
Image Credit: Securityaffairs
Node.js malvertising campaign targets crypto users
- Microsoft warns of a malvertising campaign using Node.js to deliver info-stealing malware via fake crypto trading sites like Binance and TradingView.
- Threat actors are increasingly using Node.js to deploy malware, bypass security tools, and persist in systems.
- In these attacks, malvertising is used to lure users to fake sites, and once executed, a malicious DLL collects system data and delivers further payloads.
- Microsoft has provided recommendations to mitigate threats related to the misuse of Node.js.
Read Full Article
21 Likes
Siliconangle
68

Image Credit: Siliconangle
IBM X-Force report finds shift from ransomware to credential theft in 2024
- Cybercriminals are shifting towards stealth and credential theft, as per IBM X-Force report.
- Identity attacks surged in 2024, with an increase in phishing emails delivering infostealers.
- Nearly one in three incidents in 2024 involved stolen credentials, allowing attackers to avoid detection.
- Ransomware attacks declined as operators adjusted to global enforcement crackdowns.
Read Full Article
4 Likes
Cybersecurity-Insiders
27

Evolving Threat of Ransomware: From Extortion to Data Poisoning
- Ransomware attacks have evolved from encryption and data theft to data poisoning tactics.
- Double extortion tactics involve exfiltrating sensitive information and threatening to leak it unless ransom demands are met.
- Data poisoning involves manipulating or corrupting data stored in a compromised database, with potentially catastrophic consequences.
- The evolving threat of ransomware requires stronger cybersecurity measures and proactive data integrity and recovery approaches.
Read Full Article
1 Like
Securityaffairs
327
Image Credit: Securityaffairs
Chinese Android phones shipped with malware-laced WhatsApp, Telegram apps
- Cheap Chinese Android phones are being shipped with trojanized WhatsApp and Telegram clones designed to steal cryptocurrencies through address swapping.
- The campaign targets low-end phones resembling well-known models and embeds malware in pre-installed apps.
- Attackers spoof device specifications to make phones appear as Android 14 with better hardware, fooling users and apps.
- The malware, dubbed Shibai, uses hidden modules to hijack updates, replace crypto wallet addresses, and exfiltrate chat data.
Read Full Article
18 Likes
Securityaffairs
269

Image Credit: Securityaffairs
Cyber Threats Against Energy Sector Surge as Global Tensions Mount
- Rising cyberattacks on the energy sector, linked to large-scale campaigns targeting national infrastructure for geopolitical aims, have been identified.
- Cybersecurity experts warn about the increase in targeted cyberattacks against enterprises in the energy sector worldwide.
- The vulnerability of American power grids to cyberattacks is a growing concern, as the number of susceptible points in electrical networks continues to increase.
- Technological advancements, such as cloud adoption and AI integration, have further increased cyber-risk scenarios for the energy sector.
Read Full Article
16 Likes
Securityaffairs
209

Image Credit: Securityaffairs
Government contractor Conduent disclosed a data breach
- Conduent, a business services provider, disclosed a data breach to the SEC.
- The cyberattack, which occurred in January, resulted in the theft of personal data including names and Social Security numbers.
- The company has restored operations and is investigating the full impact of data exfiltration, while notifying affected clients.
- No major operational impact was reported, but Conduent incurred costs for notifications and holds cyber insurance.
Read Full Article
12 Likes
Cybersecurity-Insiders
227

Image Credit: Cybersecurity-Insiders
DOGE Big Balls Ransomware turns into a big cyber threat
- Researchers have discovered a new variant of cyber-attack named DOGE Big Balls.
- The attack is distributed via a compressed zip file and triggers a ransomware payload.
- The ransom note instructs victims to contact Edward Coristine and demands payment in Monero.
- Organizations are urged to prioritize proactive cybersecurity measures to prevent such incidents.
Read Full Article
13 Likes
Securityaffairs
373
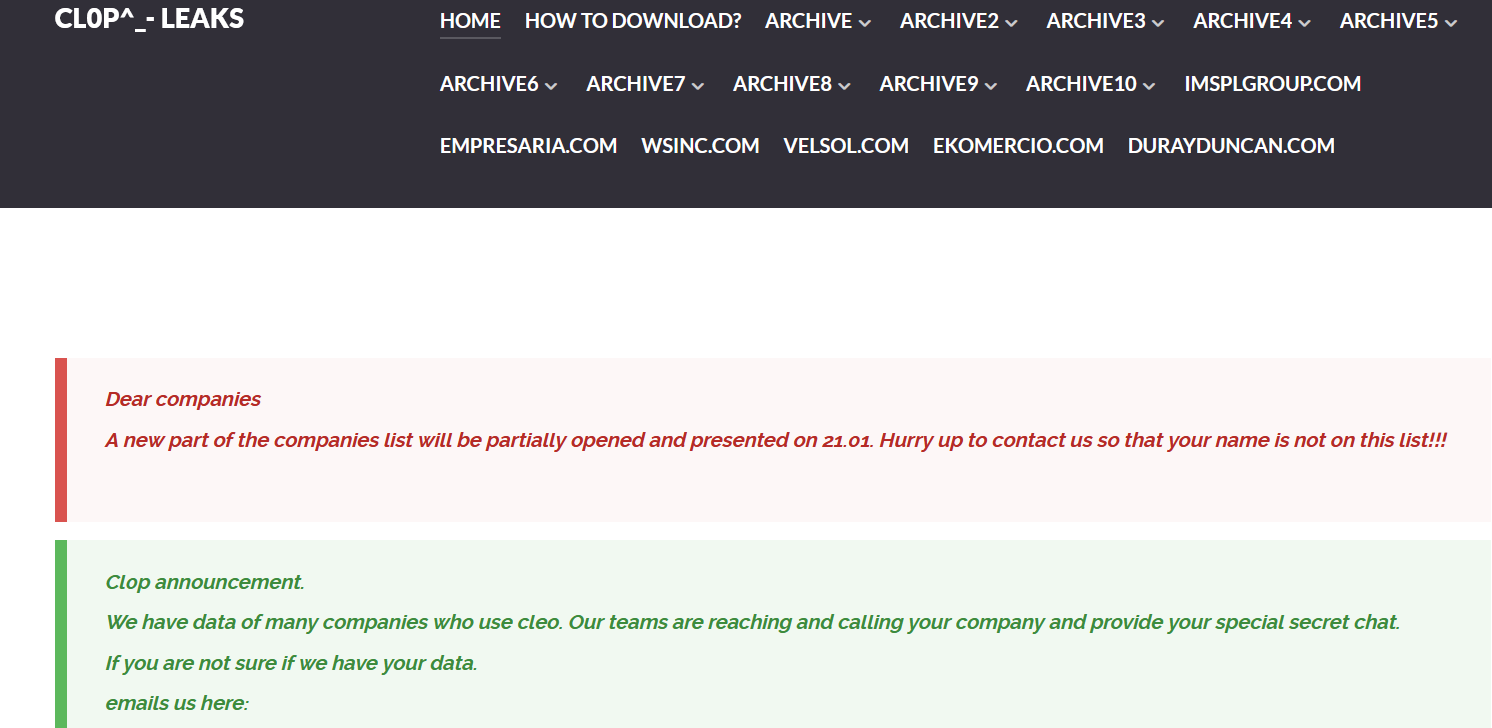
Image Credit: Securityaffairs
Hertz disclosed a data breach following 2024 Cleo zero-day attack
- Car rental giant Hertz Corporation disclosed a data breach that impacted its Hertz, Thrifty, and Dollar brands.
- Threat actors gained access to customer data via Cleo zero-day exploits in late 2024.
- The breach exposed customer data, including names, contacts, DOB, credit card information, and driver's license information.
- Hertz confirmed Cleo addressed the breach, notified law enforcement and regulators, and offers 2 years of free Kroll identity monitoring.
Read Full Article
22 Likes
Cybersafe
218

Image Credit: Cybersafe
Hertz Data Breach: Driver’s Licenses and Financial Details at Risk
- Hertz Corporation confirms data breach compromising personal information.
- Breach resulted from zero-day vulnerabilities in Cleo's managed file transfer platforms.
- Exposed data includes names, contact details, credit card numbers, driver's license information, and more.
- Clop ransomware group claims responsibility and leaks Hertz's data.
Read Full Article
13 Likes
Securityaffairs
268
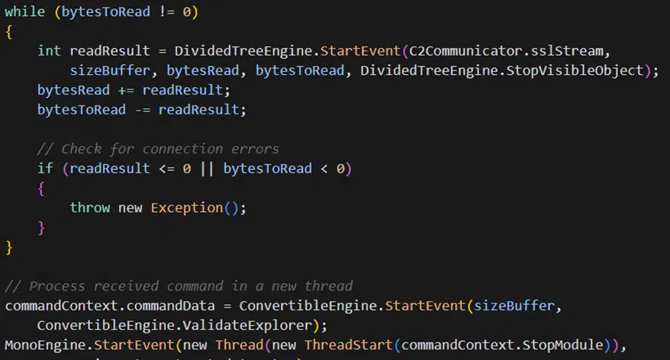
Image Credit: Securityaffairs
New malware ‘ResolverRAT’ targets healthcare, pharmaceutical firms
- New malware ‘ResolverRAT’ is targeting healthcare and pharmaceutical firms, using advanced capabilities to steal sensitive data.
- ResolverRAT spreads via phishing emails using localized languages and legal lures. Victims download a malicious file triggering the malware.
- ResolverRAT is a newly identified remote access trojan that combines advanced in-memory execution, API and resource resolution at runtime, and layered evasion techniques.
- The threat actor targets users in multiple countries with phishing emails in native languages, often referencing legal investigations or copyright violations to increase credibility.
Read Full Article
16 Likes
Cybersecurity-Insiders
141

Image Credit: Cybersecurity-Insiders
DaVita hit by ransomware attack
- DaVita, a major player in the kidney dialysis industry, has been targeted by a ransomware attack.
- No impact on patient-related services has been reported so far, but if the stolen data is released or sold, it may lead to phishing attacks and identity theft.
- Ransomware attacks have evolved into a double extortion model, where attackers not only encrypt files but also steal sensitive data.
- To protect against data extortion, organizations should backup and encrypt data, implement access control measures, maintain robust endpoint protection, configure firewalls correctly, train staff on cybersecurity, and practice safe application practices.
Read Full Article
8 Likes
Securityaffairs
350
Image Credit: Securityaffairs
Malicious NPM packages target PayPal users
- Threat actors deploy malicious NPM packages to steal PayPal credentials and hijack cryptocurrency transfers.
- "Using PayPal-related names helps these malicious packages avoid detection, making it easier for attackers to steal sensitive information.
- Malicious NPM packages use a preinstall hook to run hidden scripts, steal system info, obfuscate data, and exfiltrate it to attacker-controlled servers for future attacks.
- Fortinet researchers recommend watching for fake PayPal-related packages, checking network logs for odd connections, removing threats, updating credentials, and staying cautious when installing packages.
Read Full Article
21 Likes
Securityaffairs
401
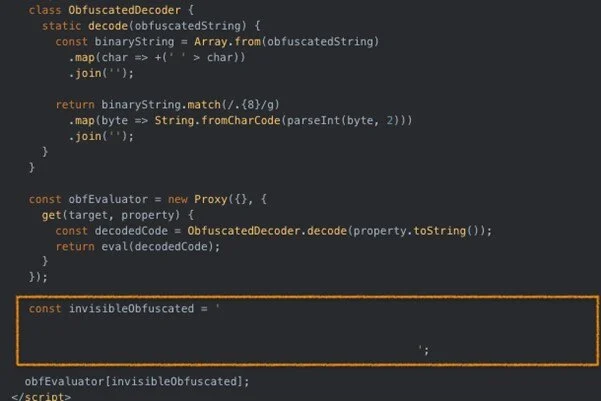
Image Credit: Securityaffairs
Tycoon2FA phishing kit rolled out significant updates
- The operators of the Phishing-as-a-Service platform Tycoon2FA have updated their kit to enhance evasion capabilities.
- The updates include advanced evasion tactics such as a custom CAPTCHA via HTML5 canvas, invisible Unicode in obfuscated JavaScript, and anti-debugging scripts.
- Tycoon2FA now uses invisible Unicode characters and JavaScript Proxy objects to complicate analysis and delay script execution.
- The phishing kit also implemented a custom HTML5 canvas-based solution to evade detection and hinder automated analysis.
Read Full Article
24 Likes
For uninterrupted reading, download the app