Malware News
Cybersecurity-Insiders
407

New cryptocurrency creation will lead to more ransomware attacks
- The emergence of a new cryptocurrency known as Meme Coin on the dark web is raising concerns among cybersecurity experts.
- Meme Coin is being heavily marketed as a rival to popular cryptocurrencies like Bitcoin and Ethereum.
- The development of such cryptocurrencies could provide opportunities for ransomware gangs to expand their operations and increase their wealth.
- If new cryptocurrencies gain traction and become widely accepted, tracking cybercriminals and dismantling their operations could become more challenging.
Read Full Article
24 Likes
Securelist
316

Image Credit: Securelist
Russian organizations targeted by backdoor masquerading as secure networking software updates
- Russian organizations targeted by backdoor masquerading as secure networking software updates.
- Sophisticated backdoor discovered targeting large organizations in Russia.
- Backdoor distributed inside LZH archives posing as ViPNet software updates.
- Backdoor enables attacker to steal files and launch additional malicious components.
Read Full Article
19 Likes
Cybersecurity-Insiders
126

Akira Ransomware shifts focus to SMBs
- Akira Ransomware has shifted its focus to smaller businesses (SMBs) and launched double-extortion attacks.
- This shift is due to cybercriminals realizing the value of targeting SMBs, generating an estimated $42 million in ransom payments in 2024.
- The cybercriminals exploit stolen credentials to infiltrate networks and deploy file-encrypting malware, demanding a ransom for the release of critical data.
- Akira Ransomware primarily targeted organizations in North America, Europe, and Australia, with sectors like education, finance, healthcare, and manufacturing being the most affected.
Read Full Article
7 Likes
Cybersecurity-Insiders
194

Ransomware Attacks on Financial Institutions: A Rising Threat with Multi-Layered Consequences
- Ransomware attacks on financial institutions have become a rising threat with multi-layered consequences.
- Hackers are utilizing double extortion techniques, where they encrypt sensitive data and demand payment for its decryption, while also threatening to release or sell the data if the ransom is not paid.
- The use of Distributed Denial-of-Service (DDoS) attacks is increasing in conjunction with ransomware attacks, causing disruptions and pressuring institutions to pay the ransom more quickly.
- The consequences of these attacks extend beyond immediate financial damage, including incident response, regulatory compliance violations, and the challenge of disaster recovery.
Read Full Article
11 Likes
Securelist
438

Image Credit: Securelist
Lumma Stealer – Tracking distribution channels
- Lumma Stealer, introduced in 2022 by the threat actor Lumma, has gained popularity in the cybercriminal underground with prices starting at $250.
- The threat involves human interaction, such as clicking links or running malicious commands, to execute the malware.
- Lumma Stealer uses various distribution methods like phishing emails, trojanized applications, and exploit kits for infection.
- One prominent distribution vector is the fake CAPTCHA scheme that tricks users into executing malicious commands.
- The fake CAPTCHA pages are promoted on pirated media sites, adult content sites, and fake Telegram channels related to cryptocurrencies.
- Users are deceived into clicking buttons that execute PowerShell commands, leading to malware downloads and installations.
- Lumma Stealer employs complex infection techniques like DLL sideloading and injecting payloads into legitimate software to avoid detection.
- The malware steals sensitive data like cryptocurrency credentials, 2FA data, browser credentials, and financial information.
- Communication with command and control servers is disguised as legitimate traffic to exfiltrate stolen data.
- Understanding the infection methods of Lumma Stealer is crucial for developing effective detection and prevention strategies.
Read Full Article
26 Likes
Securityaffairs
221
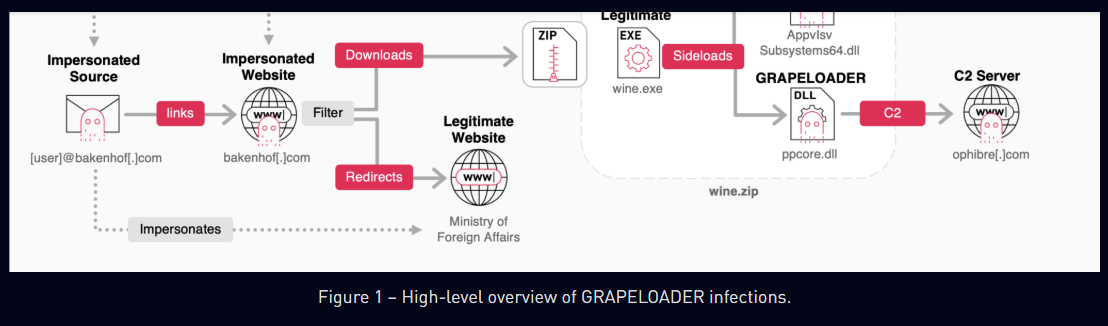
Image Credit: Securityaffairs
Russia-linked APT29 targets European diplomatic entities with GRAPELOADER malware
- Russia-linked cyberespionage group APT29, also known as Midnight Blizzard or Cozy Bear, targeted European diplomatic entities with a new malware loader named GRAPELOADER.
- The phishing campaign used fake wine-tasting invitations sent via domains like bakenhof[.]com and silry[.]com to deliver the malicious file, wine.zip.
- GRAPELOADER is an initial-stage downloader that ensures persistence by adding a registry entry to run on startup and connects to the command-and-control (C&C) server every 60 seconds.
- Researchers discovered a new variant of the WINELOADER malware, which shares similarities in code structure and obfuscation techniques with GRAPELOADER.
Read Full Article
13 Likes
Securityaffairs
144

Image Credit: Securityaffairs
Security Affairs newsletter Round 520 by Pierluigi Paganini – INTERNATIONAL EDITION
- Attackers exploited SonicWall SMA appliances since January 2025
- ASUS routers with AiCloud vulnerable to auth bypass exploit
- U.S. CISA adds Apple products and Microsoft Windows NTLM flaws to its Known Exploited Vulnerabilities catalog
- Entertainment venue management firm Legends International disclosed a data breach
Read Full Article
8 Likes
Cybersecurity-Insiders
344

Breaking the Cycle: Prioritizing Recovery Over Ransom Payments
- In 2024, businesses paid $813 million to cyber criminals as the result of ransomware.
- Ransomware attacks lead to immense financial burden and reputational damage for organizations.
- Organizations should prioritize investing in recovery processes over paying ransoms.
- The FBI urges organizations to stop paying ransoms as there is no guarantee of data recovery.
Read Full Article
20 Likes
Cybersecurity-Insiders
49

United Health offers Ransomware Loans
- UnitedHealth Group is offering interest-free loans to healthcare organizations affected by ransomware attacks.
- Change Healthcare, a major recipient of the loan program, suffered from ransomware attacks and received financial assistance from UnitedHealth Group.
- Over $9 billion has been disbursed through the loan program, with $3.2 billion successfully recovered.
- These loans help impacted organizations resume operations, cover essential costs, and avoid complete shutdowns.
Read Full Article
3 Likes
Securityaffairs
303
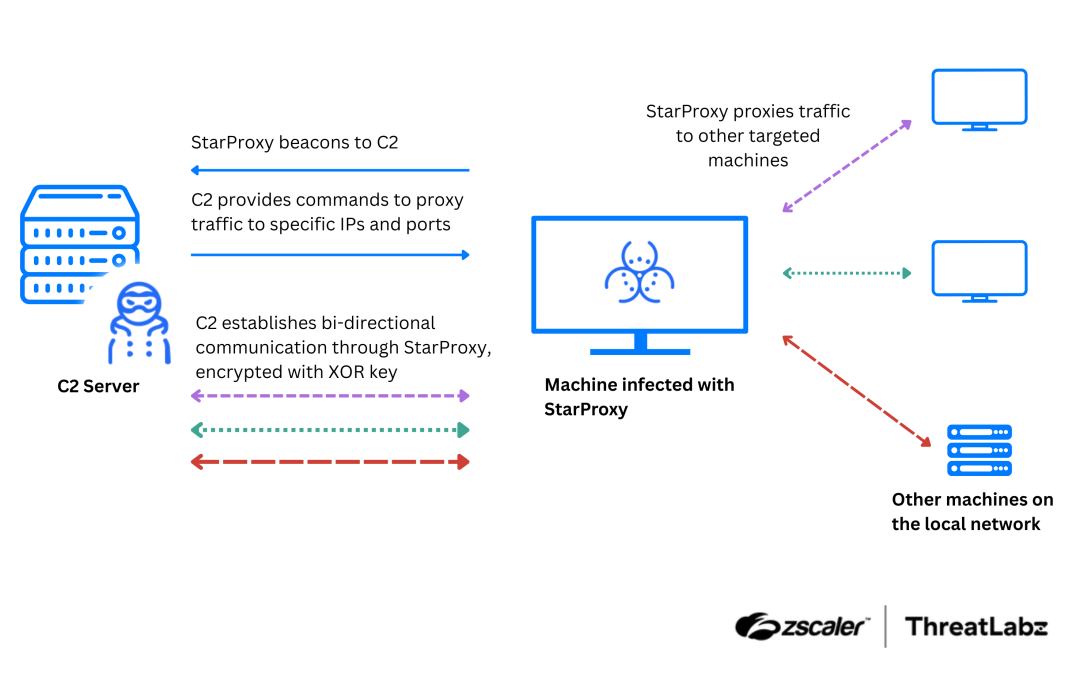
Image Credit: Securityaffairs
China-linked APT Mustang Panda upgrades tools in its arsenal
- China-linked APT group Mustang Panda deployed a new custom backdoor, MQsTTang, in recent attacks targeting Europe, Asia, and Australia.
- The APT group has been active since at least 2012, targeting American and European entities as well as Asian countries.
- Recent campaigns of APT Mustang Panda utilized European Union reports on the conflict in Ukraine as lures to deploy malware.
- The group has introduced new tools such as MQsTTang backdoor, StarProxy lateral movement tool, and several keyloggers for enhanced stealth and functionality.
Read Full Article
18 Likes
Cybersecurity-Insiders
190

Australia mandates reporting of ransomware payments
- Australia has mandated businesses to report ransomware payments.
- Starting from May 30, 2025, if a business in Australia decides to pay a ransom, it is legally required to report the incident to the government within 72 hours.
- The new requirement is part of the Cyber Security Act, aimed at improving the government's ability to respond to cyber threats and track cybercrime trends.
- The law applies to businesses and organizations in Australia with an annual turnover of $3 million or more, as well as public entities responsible for critical infrastructure.
Read Full Article
11 Likes
Securityaffairs
363
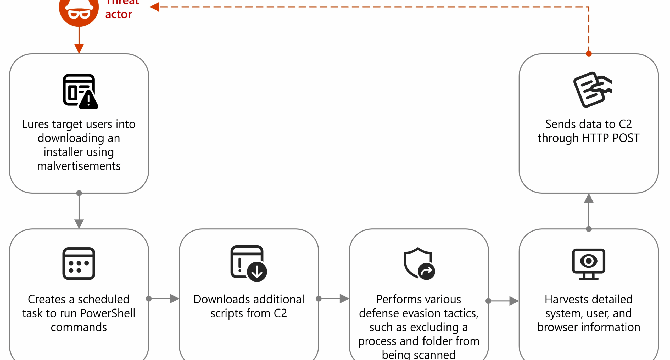
Image Credit: Securityaffairs
Node.js malvertising campaign targets crypto users
- Microsoft warns of a malvertising campaign using Node.js to deliver info-stealing malware via fake crypto trading sites like Binance and TradingView.
- Threat actors are increasingly using Node.js to deploy malware, bypass security tools, and persist in systems.
- In these attacks, malvertising is used to lure users to fake sites, and once executed, a malicious DLL collects system data and delivers further payloads.
- Microsoft has provided recommendations to mitigate threats related to the misuse of Node.js.
Read Full Article
21 Likes
Siliconangle
68

Image Credit: Siliconangle
IBM X-Force report finds shift from ransomware to credential theft in 2024
- Cybercriminals are shifting towards stealth and credential theft, as per IBM X-Force report.
- Identity attacks surged in 2024, with an increase in phishing emails delivering infostealers.
- Nearly one in three incidents in 2024 involved stolen credentials, allowing attackers to avoid detection.
- Ransomware attacks declined as operators adjusted to global enforcement crackdowns.
Read Full Article
4 Likes
Cybersecurity-Insiders
27

Evolving Threat of Ransomware: From Extortion to Data Poisoning
- Ransomware attacks have evolved from encryption and data theft to data poisoning tactics.
- Double extortion tactics involve exfiltrating sensitive information and threatening to leak it unless ransom demands are met.
- Data poisoning involves manipulating or corrupting data stored in a compromised database, with potentially catastrophic consequences.
- The evolving threat of ransomware requires stronger cybersecurity measures and proactive data integrity and recovery approaches.
Read Full Article
1 Like
Securityaffairs
327
Image Credit: Securityaffairs
Chinese Android phones shipped with malware-laced WhatsApp, Telegram apps
- Cheap Chinese Android phones are being shipped with trojanized WhatsApp and Telegram clones designed to steal cryptocurrencies through address swapping.
- The campaign targets low-end phones resembling well-known models and embeds malware in pre-installed apps.
- Attackers spoof device specifications to make phones appear as Android 14 with better hardware, fooling users and apps.
- The malware, dubbed Shibai, uses hidden modules to hijack updates, replace crypto wallet addresses, and exfiltrate chat data.
Read Full Article
18 Likes
For uninterrupted reading, download the app