Malware News
Securityaffairs
351
Image Credit: Securityaffairs
Malicious NPM packages target PayPal users
- Threat actors deploy malicious NPM packages to steal PayPal credentials and hijack cryptocurrency transfers.
- "Using PayPal-related names helps these malicious packages avoid detection, making it easier for attackers to steal sensitive information.
- Malicious NPM packages use a preinstall hook to run hidden scripts, steal system info, obfuscate data, and exfiltrate it to attacker-controlled servers for future attacks.
- Fortinet researchers recommend watching for fake PayPal-related packages, checking network logs for odd connections, removing threats, updating credentials, and staying cautious when installing packages.
Read Full Article
21 Likes
Securityaffairs
401
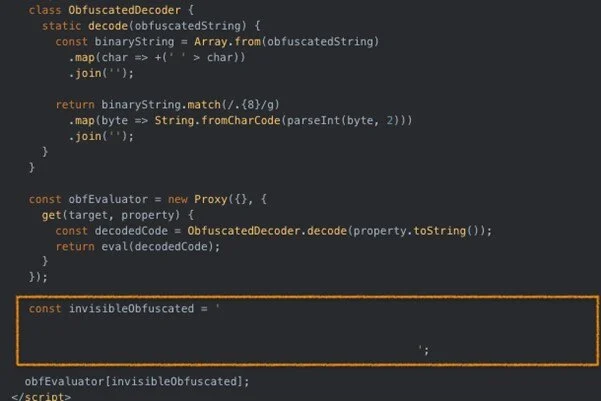
Image Credit: Securityaffairs
Tycoon2FA phishing kit rolled out significant updates
- The operators of the Phishing-as-a-Service platform Tycoon2FA have updated their kit to enhance evasion capabilities.
- The updates include advanced evasion tactics such as a custom CAPTCHA via HTML5 canvas, invisible Unicode in obfuscated JavaScript, and anti-debugging scripts.
- Tycoon2FA now uses invisible Unicode characters and JavaScript Proxy objects to complicate analysis and delay script execution.
- The phishing kit also implemented a custom HTML5 canvas-based solution to evade detection and hinder automated analysis.
Read Full Article
24 Likes
Securityaffairs
378
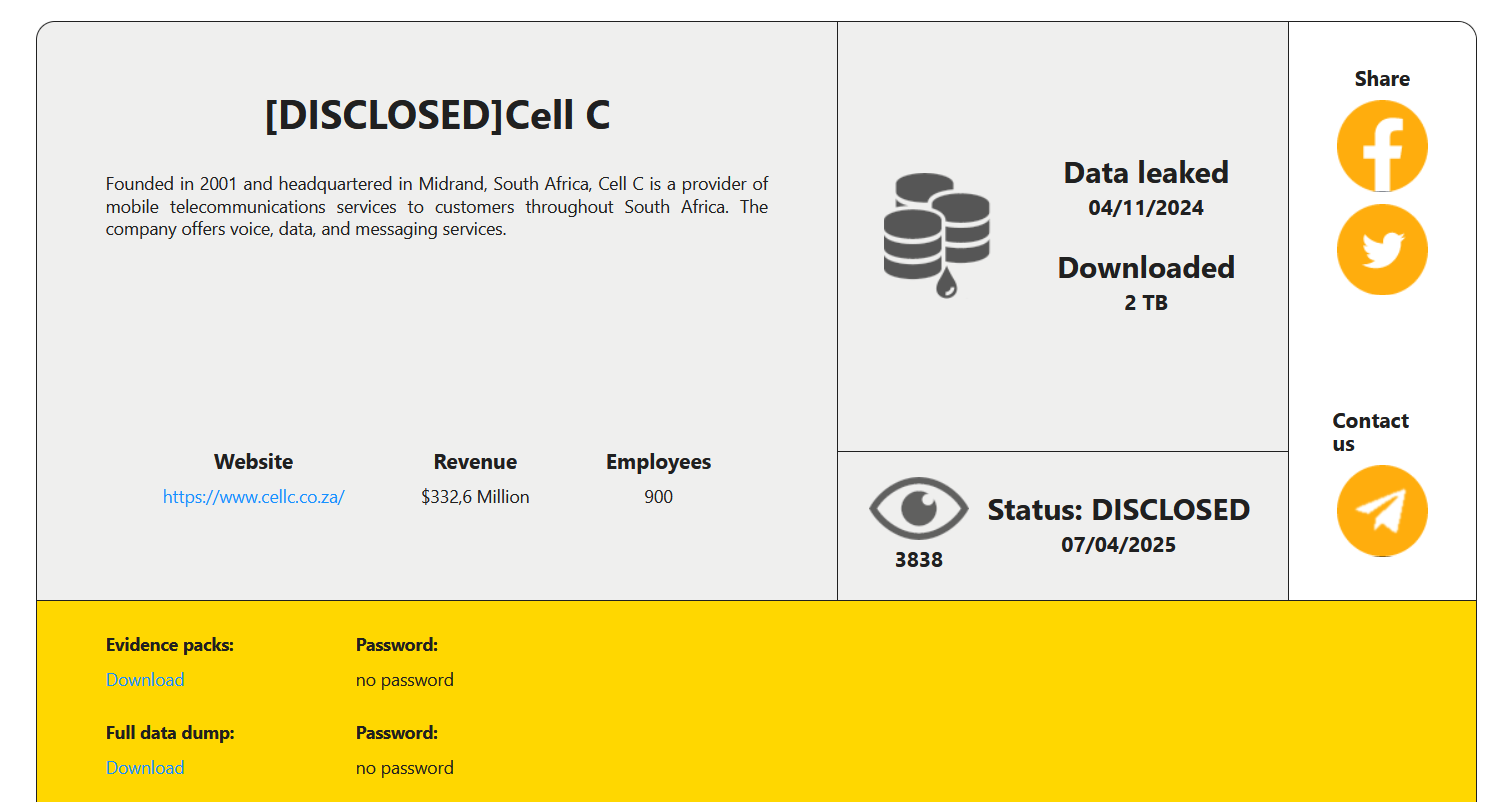
Image Credit: Securityaffairs
South African telecom provider Cell C disclosed a data breach following a cyberattack
- South African telecom provider Cell C confirms a data breach after a cyberattack.
- RansomHouse cyberattack group claims responsibility and leaks stolen data.
- Compromised data includes personal information, financial details, and identification documents.
- Cell C has taken immediate action, engaged cybersecurity experts, and provided guidance to affected stakeholders.
Read Full Article
22 Likes
Medium
49.6k

Image Credit: Medium
AI security will never be the same after Google Next 2025
- At Google Cloud Next 2025, security was a key focus with the introduction of Google Unified Security (GUS), an AI-powered platform that consolidates threat intelligence, cloud security, and enterprise browsing.
- GUS offers real-time visibility, scalable data fabric, and AI-augmented workflows to streamline security operations and enhance detection accuracy.
- Google introduced new AI agents to automate security functions and announced partnerships with Mandiant for threat intelligence and response solutions.
- Additional highlights include advancements in Data Security Posture Management (DSPM), tools for compliance and confidential computing, and enhanced mobile security.
Read Full Article
38 Likes
Cybersecurity-Insiders
160

Image Credit: Cybersecurity-Insiders
RansomHouse ransomware steals 2TB data from telecom giant
- Ransomware attack by RansomHouse results in a telecom giant, Cell C, losing approximately 2TB of data.
- The stolen data includes sensitive information of about 7.7 million customers, such as full names, contact information, ID numbers, banking details, and more.
- It is unclear why a telecom provider would store medical information.
- Cell C is taking steps to mitigate the damage and has brought in international cybersecurity experts to counteract RansomHouse's actions.
Read Full Article
9 Likes
Cybersecurity-Insiders
73

Image Credit: Cybersecurity-Insiders
Sensata Technologies hit by a ransomware attack
- Sensata Technologies, a manufacturer of sensors and electrical components, experienced a ransomware attack on April 6, 2025.
- Sensitive data, including shipping details and production information, was stolen in the attack.
- Sensata has no intention of complying with the ransom demands and has enlisted a third-party cybersecurity firm to guide them through the recovery process.
- Speculation suggests notorious hacking groups like Clop or LockBit may be involved in the attack.
Read Full Article
4 Likes
Securityaffairs
105
Image Credit: Securityaffairs
AkiraBot: AI-Powered spam bot evades CAPTCHA to target 80,000+ websites
- AkiraBot is a CAPTCHA-evading Python framework that has spammed over 80,000 websites.
- AkiraBot uses AI-generated messages to target small and medium-sized businesses.
- The spam framework bypasses CAPTCHA and network detection using rotating attacker-controlled domains and proxies.
- AkiraBot uses OpenAI's GPT-4o-mini to generate personalized spam messages and evades CAPTCHA services using Selenium WebDriver.
Read Full Article
6 Likes
Kaspersky
18

Image Credit: Kaspersky
Protecting against attacks in ZIP, RAR, CAB, MSI, ISO and other archives | Kaspersky official blog
- Archiving programs are commonly used by attackers to deceive users and extract stolen data, requiring cybersecurity attention to archive handling in operating systems and applications.
- Attackers exploit archiver vulnerabilities to deliver malware, bypass security warnings, and execute malicious files.
- Flaws in archivers like WinRAR and 7-Zip have been used by attackers to execute malicious actions, highlighting the importance of archive security.
- Archiver vulnerabilities, like Zip Slip, can lead to server compromises when handling uploaded archives, posing a risk to organizations with web apps allowing archive uploads.
- Attackers may corrupt archive contents to evade security tools, disguise malware in various file formats, and bypass security measures using legitimate archive features.
- Social engineering tactics combined with technical tricks are used by attackers to deceive users into interacting with malicious archives without detection.
- Protective measures like testing security tools, safe extraction setups, and monitoring archive usage on endpoints are recommended to enhance security when handling archives.
- Blocking dangerous archive formats, restricting disk image mounting, and training employees on safe archive handling practices are crucial steps in protecting against archive-related threats.
- Inclusion of archivers in vulnerability management programs and regular update maintenance are essential in ensuring archive security.
- Employee cybersecurity training should also cover awareness of phishing attacks and safe practices when handling various archive formats to prevent security breaches.
Read Full Article
1 Like
Siliconangle
388

Image Credit: Siliconangle
SpyNote Android malware resurfaces in campaign using spoofed app install pages
- Threat actors are using newly registered domains to deliver the SpyNote Android remote access trojan
- The SpyNote malware is delivered through spoofed app installation pages mimicking Google Play listings
- Once installed, SpyNote can record phone calls, capture keystrokes, and prevent its own uninstallation
- Users and enterprise security teams are advised to remain vigilant against spoofed app pages and avoid unknown sources for APKs
Read Full Article
23 Likes
Siliconangle
329

Image Credit: Siliconangle
First quarter of 2025 sets record for ransomware attacks and threat groups
- Ransomware attacks reached a record high in the first quarter of 2025, with over 2,000 victims.
- The threat landscape became increasingly fragmented with 70 active ransomware threat groups.
- The rise in attacks reflects a rapidly fragmenting threat environment, with more distinct groups involved.
- The diversification of attackers makes the threat environment less centralized and more unpredictable.
Read Full Article
19 Likes
Livebitcoinnews
320

Image Credit: Livebitcoinnews
Kaspersky Uncovers Crypto Theft Malware on SourceForge
- Kaspersky researchers have uncovered crypto theft malware on SourceForge, an open-source software platform.
- Sophisticated malware like ClipBanker and TookPS is distributed through pirated software on SourceForge.
- The malware lures users with promises of free Microsoft Office software while secretly stealing their cryptocurrency.
- Kaspersky advises users to avoid downloading pirated software and utilize trusted sources to protect their digital wallets and personal information.
Read Full Article
19 Likes
Cybersecurity-Insiders
192

Image Credit: Cybersecurity-Insiders
Clop targets Kellogg and Medusa Ransomware hits NASCAR
- WK Kellogg Co. has been targeted by a cyber attack, believed to be a ransomware attack, potentially stealing sensitive data.
- The Clop ransomware group, known for double extortion, is suspected to be behind the attack.
- Clop ransomware does not target Russian organizations, focuses on data exfiltration, and strikes during weekends or public holidays.
- NASCAR has experienced a data breach due to the Medusa Ransomware group, which has released a dataset containing personal information of NASCAR employees.
Read Full Article
11 Likes
TheNewsCrypto
82

Image Credit: TheNewsCrypto
Kaspersky Identifies a Crypto-Theft Malware on Microsoft’s SourceForge
- Kaspersky identified a malware disguised as a Microsoft Office plugin on SourceForge.
- The malware is programmed to use the attacker’s wallet address instead of the user’s wallet address and steal their crypto.
- Kaspersky alerted the crypto community about the malware, advising users to employ security practices while transferring cryptocurrencies.
- The malware replaces the user's wallet address with the attacker's address on the clipboard, tricking victims into sending their crypto to the attacker.
Read Full Article
4 Likes
Crypto-News-Flash
146

Image Credit: Crypto-News-Flash
Kaspersky Finds Malware Hiding in Fake Office Add-In Plugin
- A new malware campaign has been discovered by Kaspersky, targeting crypto users through a fake Microsoft Office plugin.
- The plugin disguises itself as a legitimate Microsoft Office add-in, but when installed, it uses the "clipboard hijacking" technique to replace crypto wallet addresses, diverting funds to the attacker.
- In addition to this campaign, nine Visual Studio Code extensions were also found spreading cryptominer malware, while a Trojan called Crocodilus targets Android devices to steal crypto wallet recovery phrases.
- A remote access trojan called StilachiRAT was discovered targeting Google Chrome and cryptocurrency wallet addons, highlighting the importance of securing browser wallets.
Read Full Article
8 Likes
Arstechnica
132

Image Credit: Arstechnica
“The girl should be calling men.” Leak exposes Black Basta’s influence tactics.
- A leak of 190,000 chat messages from the Black Basta ransomware group reveals it is a structured and efficient organization.
- The leaked messages show personnel with expertise in exploit development, infrastructure optimization, social engineering, and more.
- ExploitWhispers, the individual behind the leak, remains unidentified.
- The leak coincided with the unexplained outage of the Black Basta site on the dark web.
Read Full Article
7 Likes
For uninterrupted reading, download the app