Malware News
Minis
2y
1k
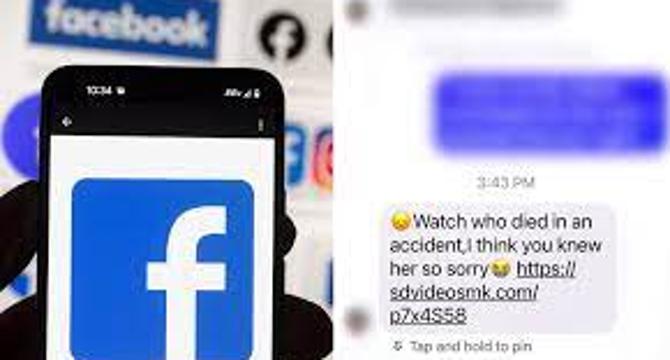
Image Credit: Minis
‘Look who just died’ Facebook scam is stealing personal info, money of users via fake news link
- A new scam called 'Look who just died' is circulating on the internet, where hackers trick Facebook users by posing as friends or family members of the victim, claiming that someone they know has passed away.
- The scam involves sending a message accompanied by a seemingly legitimate news article link. When users click on the link and enter their Facebook login details, hackers take over their accounts, potentially accessing personal information and even stealing money.
- Once hacked, the scammers send the same message to the victim's friend list, spreading the scam further. The attackers can collect sensitive data like email addresses, phone numbers, birth dates, and gain access to non-Facebook accounts as well.
- Risks include malware installation and data theft, urging caution and immediate password change.
Read Full Article
18 Likes
Minis
2y
944

Image Credit: Minis
Users of PornHub infected with Virus after cybercriminals release malware
- People across the US, UK and Australia have reportedly been exposed to a hard-to-detect virus known as Kovter due to their PornHub browsing.
- According to news.com.au, after visiting the adult website, users are shown fake pages for software updates such as Google Chrome or Firefox.
- This particular type of malware is known as 'malvertising' as it causes more dodgy ads to spread, leading to more victims of the attack.
- This type of malware attack is capable of infecting Chrome, Firefox and Microsoft Edge/Internet Explorer.
- If you think your computer has been compromised, best to get it checked by a professional.
Read Full Article
26 Likes
For uninterrupted reading, download the app