Operating Systems News
Macdailynews
238

Image Credit: Macdailynews
Apple exported $17 billion in iPhones from India in 2024
- Apple exported iPhones worth over 1.5 trillion rupees ($17.4 billion) from India in the last fiscal year, diversifying its manufacturing base.
- India's smartphone exports, driven by increased iPhone shipments, reached over 2 trillion rupees, marking a 54% increase from the previous year.
- Apple has expanded in India due to manufacturing disruptions in China, and subsidies and local assembly partnerships have aided the process.
- There are potential plans for Apple to shift more manufacturing to India and Southeast Asia due to US levies on China and anticipated tariffs.
Read Full Article
14 Likes
Idownloadblog
197
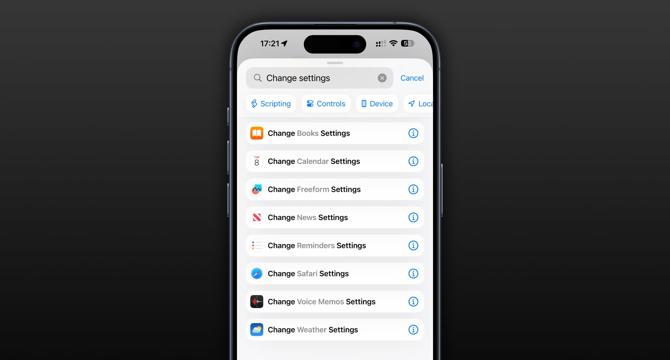
Image Credit: Idownloadblog
iOS 18.4: New Shortcuts actions to change settings in apps ahead of Siri’s AI update
- Apple has added new actions for its Shortcuts app to change settings in built-in apps in the latest iOS 18.4 update.
- The new actions allow for granular control over settings in apps like Apple TV, Books, Calendar, Clock, Maps, Messages, Notes, Reminders, Safari, Voice Memos, Weather, and more.
- These actions include toggling settings, opening specific conversations, changing preferences, and more.
- These updates are likely related to the delayed Siri update, which will support complex queries and chain together multiple in-app actions.
Read Full Article
11 Likes
Macdailynews
235
Image Credit: Macdailynews
Apple stock bounces; U.S. stocks rally as tariff fears subside, Dow jumps
- Apple stock (AAPL) has faced turbulence in 2025, but signs of a rebound are emerging despite recent challenges.
- After hitting an all-time high on December 26, 2024, the stock plummeted due to delays in Apple Intelligence features and U.S. import tariff concerns.
- However, in Tuesday trading, AAPL is showing resilience, up around 3%, with analysts and investors pointing to several factors fueling its recovery.
- Factors include robust fundamentals, persistent consumer demand, and optimism surrounding Apple's pipeline.
Read Full Article
14 Likes
Hackaday
445
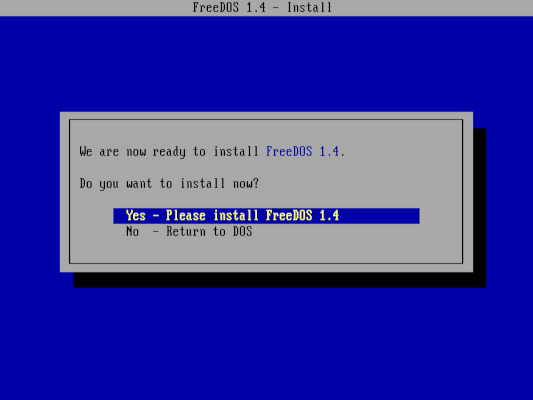
Image Credit: Hackaday
FreeDOS 1.4 Released
- The FreeDOS project has released version 1.4, providing a modern, fully supported operating system for DOS applications.
- The recent release adds new features and updates to existing components, including the FreeCOM command shell.
- It is the first stable release since version 1.3 that was launched in 2022.
- Released in 1994, FreeDOS has become the de facto replacement for MS-DOS and offers improvements for modern hardware.
Read Full Article
26 Likes
Discover more
- Programming News
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Arstechnica
41

Image Credit: Arstechnica
Back to basics: Microsoft tests overhauled Start menu in Windows 11 beta builds
- Microsoft tests overhauled Start menu in Windows 11 beta builds.
- The new Start menu in Windows 11 displays up to two rows of pinned apps and a scrollable list of installed apps.
- Users can choose to display apps in a vertically scrollable list, a horizontal grid, or sorted by category.
- The new Start menu allows turning off the "Recommended" section and showing a full list of installed apps.
Read Full Article
2 Likes
Macdailynews
341

Image Credit: Macdailynews
President Trump’s U.S. import tariffs spur iPhone sales rush
- The newly imposed U.S. import tariffs have resulted in a surge of customers rushing to Apple stores to buy iPhones, fearing steep price hikes.
- Apple's retail stores reported higher sales over the weekend than in previous years in major markets.
- Some customers are upgrading their iPhones during the off-peak season in anticipation of price increases due to tariffs.
- Despite speculations, iPhones are not expected to cost thousands of dollars apiece due to tariffs.
Read Full Article
20 Likes
The Verge
206

Image Credit: The Verge
Microsoft’s new Windows 11 Start menu is bigger and fixes a major pain point
- Microsoft is working on a new Windows 11 Start menu design that is bigger and more customizable.
- The updated Start menu allows users to disable the recommended feed of files and apps.
- The new design keeps everything on one scrollable page and provides easy access to all apps.
- Microsoft has started testing this new Start menu design and plans to roll it out to Windows 11 users soon.
Read Full Article
12 Likes
Macdailynews
321

Image Credit: Macdailynews
EU decision on Apple due in coming weeks, antitrust chief says
- The decision on whether Apple and Meta have violated tech regulations will be announced in the coming weeks, according to EU antitrust chief.
- The European Commission has been investigating Apple and Meta for possible infringements of the Digital Markets Act since March of last year.
- Both companies are expected to face modest fines for violations of the Digital Markets Act.
- The US has warned the EU against excessive regulation of American technology firms.
Read Full Article
19 Likes
TechViral
225
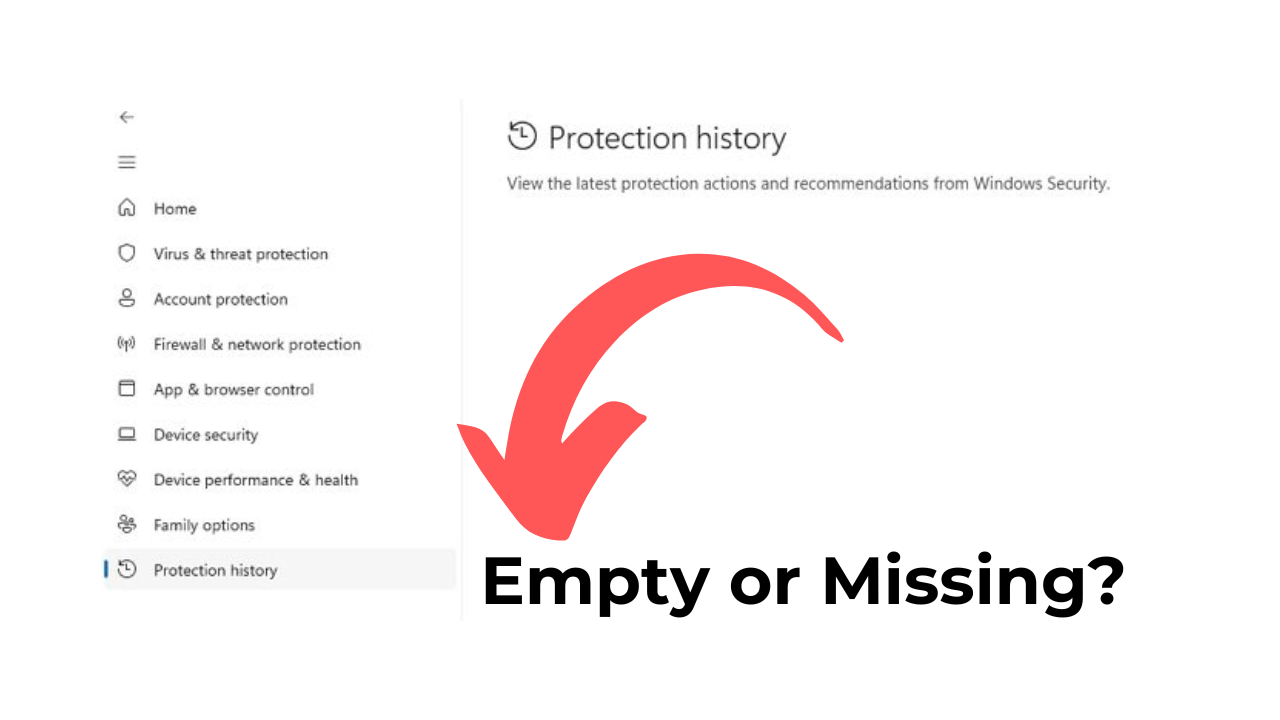
Image Credit: TechViral
Windows Security Protection History Empty/Missing? 8 Ways to fix it
- Windows Security, a built-in antivirus program on Windows 10 and Windows 11, helps protect PCs from threats and malicious files.
- Some Windows 11 users are experiencing issues with the Protection History option in the Windows Security app.
- Protection History displays actions taken by the security software to safeguard the PC, such as scan results and blocked threats.
- To fix the Missing Protection History issue, users can try restarting their Windows 11 PC.
- Disabling any third-party security program being used can also resolve the empty Protection History problem.
- Clearing existing detection history files and manually deleting scan history are recommended steps to address the issue.
- Restarting real-time protection and cloud-delivered protection after these actions can help the Protection History feature work correctly.
- Repairing or resetting the Windows Security app may also fix the Protection History display problem.
- Running SFC and DISM commands can help resolve system file corruption that causes the blank Protection History issue.
- Re-registering the internal components of Windows Security through PowerShell can also assist in resolving the problem.
Read Full Article
13 Likes
Alvinashcraft
151

Dew Drop – April 8, 2025 (#4399)
- Various topics were covered in the Dew Drop on April 8, 2025, including Model Context Protocol (MCP) server building, AI in .NET, SOLID principles in Angular, and Git's 20th anniversary.
- The article also discussed security best practices for ASP.NET developers, building chat interfaces with KendoReact, and using OpenAPI overlays for specialization within domains.
- In the AI sphere, topics ranged from LLMs to AI coding assistants, multimodal search, and Cloud Native Infrastructure for GenAI applications.
- Design, methodology, and testing were highlighted with topics such as GitLab vs GitHub, data visualization, and alternative design approaches with functional programming.
- Additionally, the article covered mobile, IoT, and game development updates, along with various screencasts, podcasts, and community-related announcements.
- Events like the Global AI Bootcamp 2025 were mentioned, along with database updates, information on SharePoint, Microsoft Teams, Windows 11 Insider Preview, and more.
- The article also touched on miscellaneous topics such as tariffs, Golang's popularity trends, and a selection of curated link collections for further reading.
Read Full Article
9 Likes
Dev
119
Image Credit: Dev
Installing Linux Mint with LVM and LUKS
- The article discusses installing Linux Mint with LVM and LUKS for a work laptop setup, emphasizing ease of use and flexibility.
- Using LVM for disk partitioning allows for easy extension of filesystems and optimal storage management.
- For LUKS setup, creating a LUKS container and unlocking it is crucial before setting up LVM.
- Partitioning the disk involves creating EFI, /boot, and LUKS partitions using tools like gparted or parted.
- Creating LVM shards within the LUKS container involves using parted for a GPT filesystem table and creating multiple partitions.
- After creating shards, LVM PhysicalVolumes are initialized, followed by creating volume groups like system and user.
- Logical volumes like root and home are then created within the volume groups for installing the OS.
- Configuring LUKS for auto-mounting and setting up LVM bootstrap in the initramfs stage is important for seamless booting.
- Scripts are used to enable LUKS unlocking and LVM discovery during the boot process for a successful setup.
- By following the detailed steps provided in the article, users can achieve a secure and efficient Linux Mint installation with LVM and LUKS.
Read Full Article
7 Likes
Rockpapershotgun
330
Image Credit: Rockpapershotgun
Assassin's Creed Shadows adds a self-driving horse, but I implore you not to use it
- Ubisoft is adding an update to Assassin's Creed Shadows that allows players to activate auto-pathing on their horse, essentially turning it into a self-driving car with hooves.
- This update includes other features such as the ability to reset the skill tree, the option to dismantle or sell multiple items at once, and improvements to boss fights.
- While some players may find the auto-pathing feature helpful, it raises questions about the purpose of playing these games and the impact on the sense of exploration and presence.
- The author suggests that enabling auto-pathing in open world games can contribute to a loss of playfulness and presence, detaching players from the detailed virtual worlds and encouraging disengagement.
Read Full Article
19 Likes
Ubuntu
404

Ubuntu developer images now available for OrangePi RV2: a low-cost RISC-V SBC
- Canonical announces availability of Ubuntu developer images for OrangePi RV2 RISC-V SBC.
- OrangePi RV2 offers low-cost, power-efficient form factor with KY-X1 octa-core SoC and 2 TOPS AI accelerator.
- Ubuntu developer images unlock a range of possibilities in education, prototyping, and machine learning at the edge.
- Canonical's partnership with RISC-V community aims to support and promote the open standard.
Read Full Article
24 Likes
Gizchina
32

Image Credit: Gizchina
Microsoft Confirms End of Windows 10 Support – 240 Million Users at Risk
- Microsoft confirms that Windows 10 support will end on October 14, 2025.
- Approximately 240 million users still operating on Windows 10 need to take action.
- Lack of regular updates leaves systems vulnerable to attacks by spyware or malware.
- While enterprises will receive staggered support for a cost, individual users will need to update their hardware or purchase a new computer to run Windows 11.
Read Full Article
1 Like
Tech Radar
422

Image Credit: Tech Radar
Windows 11 users are getting fixes for some longstanding bugs in 24H2 today, including the cure for a seriously annoying File Explorer glitch
- Microsoft is deploying the monthly patch for Windows 11 24H2 today
- The update includes a fix for a File Explorer bug where the flyout menu extended upwards instead of down
- The patch also resolves issues with wake-from-sleep functionality, including a Blue Screen of Death upon waking
- Microsoft is gradually rolling out the fixes, and users may have to wait to receive them
Read Full Article
25 Likes
For uninterrupted reading, download the app