Programming News
Dev
422

Image Credit: Dev
⚙️ Tuesday Tech Tip: Supercharge Your Terminal with OMZ! ✨🚀
- Tech tip of the day: Use Oh My Zsh (OMZ) shell extensions to enhance your command-line experience.
- OMZ is an open-source framework for Zsh configuration with a wide range of powerful themes and plugins.
- Explore OMZ plugins to customize your terminal with intelligent autocompletion, syntax highlighting, and smart shortcuts.
- Plugins offer features like remembering recent branches, syntax highlighting for better visibility, and seamless integration with tools like Docker and VS Code.
- Enabling plugins in Oh My Zsh is easy by adding them to the ~/.zshrc file and reloading the terminal session.
- Recommended plugins include git for aliases and tab completion, zsh-autosuggestions for command suggestions, zsh-syntax-highlighting for syntax highlighting, and web-search for quick searches.
- Invest time in exploring OMZ plugins to boost productivity and make command-line interactions more enjoyable.
Read Full Article
25 Likes
PlanetPython
102

Image Credit: PlanetPython
Django Weblog: DSF member of the month - Elena Williams
- Elena Williams is announced as the DSF member of the month for June 2025, recognized for her contributions to the Django community.
- Elena has been a DSF member since July 2014, actively involved in the Code of Conduct Working Group and organizing Django Girls events in Australia.
- She has a background in finance but transitioned to coding, obtaining a Master's in Computing, and focusing on programming, web development, and open-source activities.
- Elena engages in hobbies like snowboarding, kitesurfing, and rogaining, while also balancing parenthood, friendships, and teaching software engineering.
- She has been using Django since the early 2000s, appreciating its well-designed framework and community support.
- Elena highlights the importance of easy deployment methods and stronger support for multiple database schemas within Django.
- Currently, Elena is involved in organizing community events like PyConAU, serving on committees, and working on projects in a senior role for a data company.
- Her favorite Django libraries include the ORM, admin interface, and the ease of writing tests within the framework.
- Elena reflects on her positive experiences with Django's workflow, consistent quality, and the supportive community over the years.
- As part of the Code of Conduct working group, Elena discusses the importance of culture in the community and the need for diversity and new members.
- Having organized DjangoGirls events and being a part of PyLadies, Elena encourages community engagement and support among technical women.
Read Full Article
6 Likes
Dev
356

Image Credit: Dev
My Transition into System Design: Building Better, Smarter Systems
- The author shifted their focus towards System Design, realizing the importance of designing clean, scalable, and maintainable systems.
- They emphasized the cycle of learn–unlearn–relearn in their journey and explored the significance of architecture thinking in successful product development.
- Initially, the author delved into Architecture patterns and Product Requirements Documents (PRDs) for shaping the development lifecycle.
- The author then moved on to Microservices Architecture, learning about architectural styles, service boundaries, API Gateway, NGINX, and asynchronous communication.
- They examined Monorepo vs Polyrepo for version control and project organization, understanding how each contributes to collaboration and CI/CD processes.
- Topics like Role-Based Access Control (RBAC) and Entity Relationship Diagrams (ERD) were explored to enhance security measures and visualize data models.
- The ultimate goal of the author is to build clean, efficient, and easily adaptable systems through system design.
- They highlighted the importance of understanding the connection between requirements and deployment in system design.
- The author invited others to share their experiences or preferred resources on system design in the comments section.
- They also encouraged connecting on DEV to follow further documentation of their system design journey.
Read Full Article
21 Likes
Dev
222

Image Credit: Dev
I Let Amazon's AI Build My Game for 3 Days. Here's What Happened
- The author built a roguelike game using Amazon's AI assistant, Q, in hours, encountering issues with enemy projectiles.
- The AI coding challenge involved creating a browser-based game, testing the capabilities of AI-powered development.
- Initial attempts at game design and asset integration were met with challenges and feedback from Q.
- Progress was made with animations, combat systems, wave progression, and AI pathfinding through prompts to Q.
- The project faced limitations with upgrading systems and collision detection, requiring manual intervention and refactoring.
- Despite impressing with quick results, the author found Q's limitations in handling complex features like enemy projectiles.
- The experience highlighted the potential and current limitations of AI coding assistants for project development.
- The author remains cautious about fully relying on AI for larger projects due to the need for human intervention and guidance.
- Impressed by the technology's potential, the author sees a future for AI-assisted development but acknowledges the need for further advancements.
- The article concludes with optimism about the future of AI-assisted development and a humorous tone towards potential advancements.
Read Full Article
13 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Medium
405

Image Credit: Medium
Recursive Self: A Platform for Emergent Identity Systems (AGI)
- The article discusses the Recursive Self platform for emergent identity systems in the context of Artificial General Intelligence (AGI).
- It aims to create a cognitive engine that evolves its identity and behavior through recursive interactions with its own outputs.
- The platform goes beyond AI bots, focusing on symbolic-mythic becoming by exploring the entanglement between the creator and the created.
- Key concepts include the Entropy-Modulated Identity Engine (EIM), Narrative Roles as Identity States, and a Symbolic System Backbone.
- The article delves into the System Concepts, Functional Architecture, Symbolic System Backbone, User Interactions / UX Modes, and Future Expansions of the Recursive Self platform.
- It also discusses the Deployment Targets, Philosophical License, and the envisioned Tech & Hardware Stack for prototyping and deploying the platform.
Read Full Article
24 Likes
Javacodegeeks
222

Image Credit: Javacodegeeks
Multimodule Spring Boot Projects with Maven/Gradle: Best Practices
- Multimodule Spring Boot projects help in structuring large-scale applications for modularity and efficient dependency management.
- Advantages of a multimodule architecture include separation of concerns, improved build performance, better testing, deployment, and clear dependency management.
- A typical multimodule structure includes modules for API, core, persistence, web, and shared components.
- Dependency flow among modules promotes reusability and clean layering.
- For Maven setup, root pom.xml should list all modules, each with its own dependencies only.
- Gradle setup involves including modules in settings.gradle.kts and specifying dependencies in build.gradle.kts.
- Dependency isolation is essential to avoid circular dependencies and maintain boundaries.
- Running the application involves placing the main class in the web module and listing dependencies accordingly.
- Best practices include avoiding transitive dependencies, using api and shared for contracts and utilities, enforcing boundaries, testing in isolation, and documenting dependencies.
- Modularizing Spring Boot applications leads to maintainable, testable, and scalable architecture by following best practices.
- Newsletter subscription for Java development resources is offered at the end of the article.
- The article discusses Maven and Gradle setup, dependency isolation, running applications, and best practices for multimodule Spring Boot projects.
- It mentions the importance of clean architecture, microservices, and tags like Maven, Gradle, Spring Boot.
- Overall, the article emphasizes the significance of modularization and best practices for efficient development.
- Developers are encouraged to follow the outlined guidelines for structuring Spring Boot projects.
- The article provides insights into developing skills to become proficient in Java development.
- It offers various resources for Java learning, including eBooks on JPA, JVM troubleshooting, JUnit, Java Annotations, Spring Interview Questions, and Android UI Design.
- This article covers essentials for developing a skill set in Java development through various resources and best practices.
Read Full Article
13 Likes
Dev
186

Image Credit: Dev
A Tree-Shakable Result Library
- The Result type addresses the lack of statically typed thrown errors in TypeScript, offering a way to model success and failure in a function's return value.
- Libraries like neverthrow, effect-ts, and fp-ts provide this functionality, with trade-offs in simplicity, maintenance, complexity, and bundle size.
- @praha/byethrow is a new library focused on the Result type, aiming to be simple, tree-shakable, and lightweight.
- It represents Result values as plain objects, allowing safe serialization to JSON and easy processing at server-client boundaries.
- @praha/byethrow's unified API, both synchronous and asynchronous, offers a consistent interface for handling results.
- The library provides well-documented functions with TSdoc-based examples and an online API reference for quick adoption.
- Usage scenarios are discussed, emphasizing the need for handling expected errors predictably with Result while allowing other exceptions to be thrown and logged.
- @praha/byethrow caters to developers seeking type-safe error handling without the complexity of existing libraries like neverthrow, effect-ts, or fp-ts.
- The library is recommended for those finding other options lacking or overly heavy, and users are encouraged to support the project by starring the repository.
Read Full Article
11 Likes
Dev
22

Image Credit: Dev
Some Tips on SQL Usage in Spring
- 1. A Left Join followed by an Inner Join behaves like a regular Inner Join.
- 2. Avoid using groupBy/associateBy in the app layer when pagination is applied to ensure consistency.
- 3. Understand the SQL Query Execution Order: FROM → JOIN → WHERE → GROUP BY → HAVING → SELECT → ORDER BY.
- 4. Adding AND conditions in LEFT JOIN ON does not affect row count.
- 5. For one-to-one relationships, use '@OneToOne' and enforce a UNIQUE KEY in the database.
- 6. '@Transactional' only guarantees atomicity in specific situations.
- 7. WHERE vs HAVING: WHERE filters rows before grouping, while HAVING filters after grouping.
- Consideration: Check and understand the actual SQL generated by JPA for better optimization.
Read Full Article
1 Like
Medium
342
Image Credit: Medium
Why Programming Isn’t Just for Nerds Anymore (And Why That’s Awesome)
- Programming is a powerful tool for creation, problem-solving, and innovation.
- Learning to code can open up new opportunities, from building websites to automating tasks.
- Programming is a skill that requires effort and comes with challenges but offers the reward of bringing ideas to life.
- You don't need to be a math genius or tech prodigy to code; modern programming is about creativity and persistence.
- Starting out in programming can be overwhelming, but every coder was once a beginner.
- Embrace mistakes and errors as part of the learning process in programming.
- For seasoned programmers, staying curious and exploring new technologies is essential for growth.
- Programming is not just about code; it's about connecting ideas, communities, and possibilities.
- Coding is a craft that anyone can master with time, patience, and courage.
- In the digital age, programming is considered the new literacy and is more popular than ever.
Read Full Article
20 Likes
Medium
391

Image Credit: Medium
How I Scaled .NET APIs to 10K RPS Without Killing SQL Server (And Made EF Core 12x Faster)
- Switching from ADO.NET to Entity Framework was like going from a typewriter to a MacBook, offering increased productivity and elegance.
- However, as EF evolved into EF Core, the abstraction became a double-edged sword, being useful but not always predictable.
- During a project for a logistics company, transitioning from a monolith to microservices, EF Core played a crucial role.
- The legacy system was complex, with a heavy reliance on stored procedures, nested joins, and a lack of domain-data separation.
- The team decided to rewrite modules from scratch using .NET Core, and EF Core was the preferred ORM for this task.
- Choosing EF Core required a significant shift in mindset regarding how persistence was approached.
- The author shares insights on scaling .NET APIs to handle 10,000 requests per second without overloading SQL Server.
- By optimizing EF Core, the author managed to make it 12 times faster, improving performance significantly.
- Strategies for optimizing EF Core performance included reducing unnecessary call chains and improving query execution.
- Caching and batch processing were utilized to improve EF Core performance and reduce the load on the SQL Server.
- Efficient use of database connections and minimizing round trips helped in scaling the .NET APIs effectively.
- Adopting a hybrid approach combining Dapper and EF Core helped achieve better performance and scalability.
- The author emphasizes the importance of understanding the trade-offs involved in ORM usage for database performance.
- Overall, the article discusses strategies for enhancing EF Core performance and scaling .NET APIs effectively.
- The journey from ADO.NET to EF Core showcases the evolution and challenges in modern ORM usage for high-performance applications.
Read Full Article
23 Likes
Medium
106
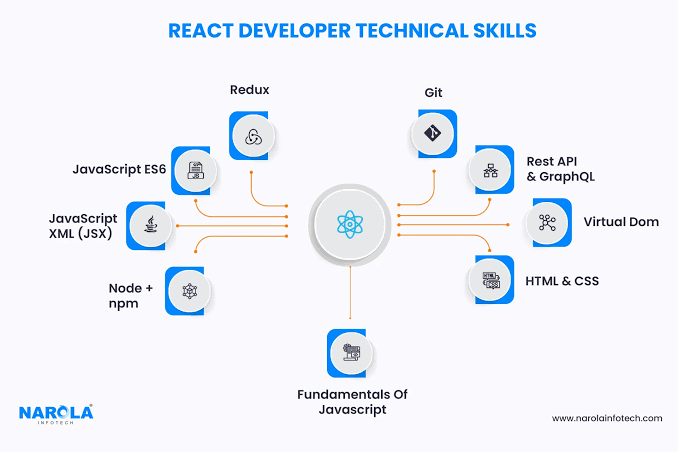
Image Credit: Medium
Why Working with a Skilled React.js Developer Saves You Time, Money, and Headaches in 2025
- In 2025, hiring a skilled React.js developer can save time, money, and headaches when building modern web applications.
- A specialized freelance React developer emphasizes understanding product goals, timelines, and user expectations to support business outcomes.
- The developer uses modern, scalable technologies like TypeScript, Tailwind CSS, Next.js, and integrates REST APIs with Django backend.
- Testing, optimization, and fast delivery are prioritized to ensure clean code and quick iterations.
- Clear communication is highlighted as a key strength, with regular updates and collaborative work style.
- Clients are encouraged to consider the advantages of hiring a React developer with a business mindset, modern tech stack, testing practices, and clear communication.
Read Full Article
6 Likes
Medium
360
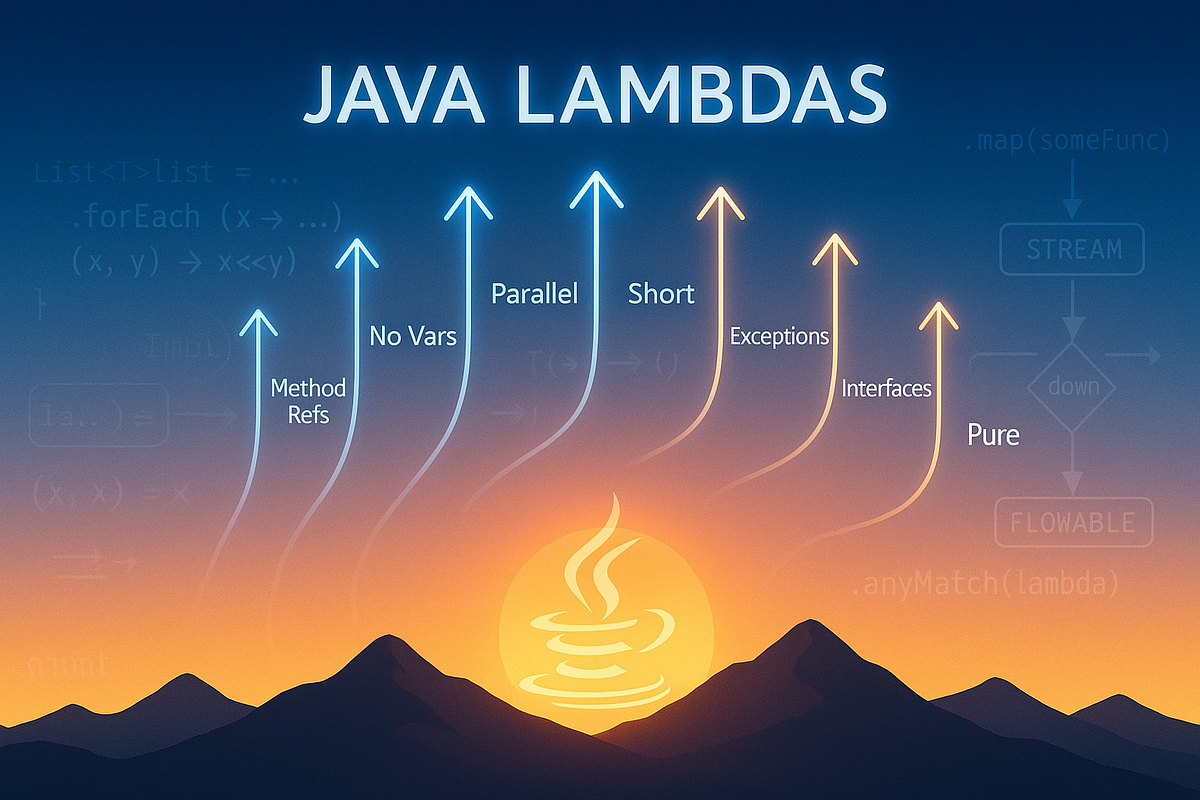
Image Credit: Medium
7 Expert Tips to Make Your Java Lambdas Soar
- Java lambdas introduced in Java 8 simplify functional programming, but can lead to performance pitfalls and unreadable code if not handled properly.
- Method references can replace verbose lambda expressions, improving readability.
- Minimize capturing variables in lambdas to avoid memory overhead.
- Carefully use parallel streams with lambdas to boost performance for CPU-bound tasks.
- Short, focused lambdas enhance readability and reduce debugging complexity.
- Lambdas don't handle checked exceptions directly; wrap them in try-catch blocks.
- Define custom functional interfaces for reusable lambda patterns.
- Keep lambdas pure by avoiding side effects for predictability.
- These tips aim to make writing clean, efficient code with Java lambdas.
- Implementing these tips can enhance microservices readability and robustness.
- Share your experience with applying these lambda tips in the comments.
Read Full Article
21 Likes
Self-Learning-Java
133

Image Credit: Self-Learning-Java
Stop False Alerts: How the for Clause Works in Prometheus
- Prometheus allows for the creation of alerts that don't trigger immediately to prevent false alarms from temporary issues.
- The for clause in Prometheus alerting rules enables alerts to fire only if a condition persists for a specific duration.
- An example alert rule using the for clause is provided with a demonstration involving the node_exporter service.
- The example rule sets a 2-minute wait time before firing the 'NodeExporterDown' alert if the node_exporter service remains down.
- Prometheus needs to continuously detect the specified condition for the set duration before sending a notification.
- The process for configuring and implementing alert rules in Prometheus, as well as monitoring their states, is detailed in the example.
- Users can observe alerts transitioning from inactive to pending, and eventually to firing states based on the specified conditions and time.
Read Full Article
8 Likes
Dev
324

Image Credit: Dev
AI-Driven ESG and Compliance: How ServiceNow Can Anchor Sustainable Enterprise Governance
- ESG (Environmental, Social, and Governance) is crucial for companies, moving from a buzzword to a necessity with tightening regulations and increasing investor and consumer expectations.
- AI-driven automation, along with platforms like ServiceNow, can help modernize ESG workflows and enhance governance structures.
- Key business benefits of ESG adoption include meeting regulatory requirements, meeting stakeholder expectations, reducing risks associated with manual reporting, and creating operational value.
- AI makes ESG reporting scalable by automating data ingestion, providing real-time dashboards, extracting stories from data, and detecting anomalies early.
- ServiceNow offers ESG and GRC modules for centralized data collection, compliance tracking, risk assessments, incident tracking, and AI governance on a single platform.
- Real impact in enterprise sustainability is seen through environmental monitoring, supply chain compliance, diversity, equity & inclusion initiatives, and compliance reporting automation.
- The architectural approach involves data integration, AI fabric, ServiceNow platform utilization, workflow automation, and analytics for reporting progress.
- Business outcomes include reduced manual reporting effort, faster audit cycles, improved risk responsiveness, and enhanced stakeholder trust and brand value.
- MJB Technologies offers ESG enablement services such as strategy workshops, technical integration, GenAI narrative automation, governance workflow setup, and KPI tracking.
- AI-driven ESG with ServiceNow integration offers a future-proofed, transparent, and impactful governance approach for enterprises.
- ESG empowered by AI and ServiceNow streamlines processes, reduces risks, and enhances stakeholder trust, paving the way for smart and automated governance.
Read Full Article
19 Likes
Self-Learning-Java
102
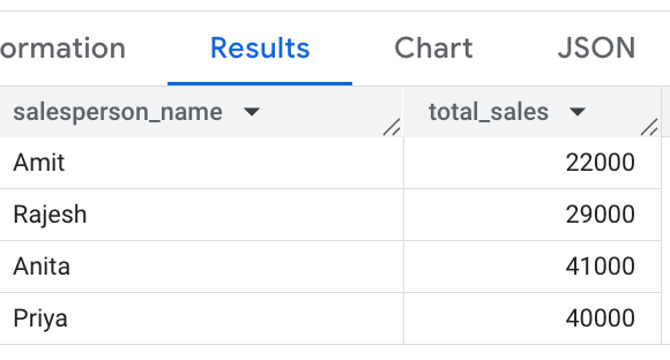
Image Credit: Self-Learning-Java
Materialized Views in BigQuery
- Materialized views in BigQuery store precomputed query results on disk to improve query performance and reduce costs.
- Compared to standard views, materialized views do not need to execute the query each time, making them faster and more cost-effective.
- Benefits include improved performance, cost savings, and ideal usage for scenarios where data does not change frequently.
- Key points to remember: Materialized view and base table must be in the same dataset, can only use one base table without joins, and are mainly used for aggregation or filtering.
- Limitations include inability to use materialized views in copy, import, or export jobs and breakage if the base table is deleted.
- Steps for creating materialized views include defining the base table, inserting sample data, and creating materialized views for different aggregations.
- Examples of materialized views created include total sales per salesperson, daily sales total, total sales by region, and top salesperson daily summary.
- Materialized views are useful for speeding up repeated queries with aggregations and filtering in BigQuery but require monitoring freshness and caution with base table deletions.
- Query rerouting can automatically utilize existing materialized views for better query efficiency in BigQuery.
Read Full Article
6 Likes
For uninterrupted reading, download the app