Programming News
Dev
148

Image Credit: Dev
📧 How to Validate Email Addresses in PHP: A Practical Guide
- Email validation is crucial to avoid fake or malformed emails, improve email deliverability, and enhance the user experience by catching typos early.
- PHP offers simple and reliable email validation through built-in functions and filters like filter_var() and regular expressions.
- Best practices include using filter_var() for validation, optionally checking MX records for domain validity, and providing clear feedback to users about invalid emails.
- Implementing email validation in both client-side (JavaScript) and server-side (PHP) is recommended to enhance lead quality and user experience.
Read Full Article
8 Likes
The Pragmatic Engineer
125
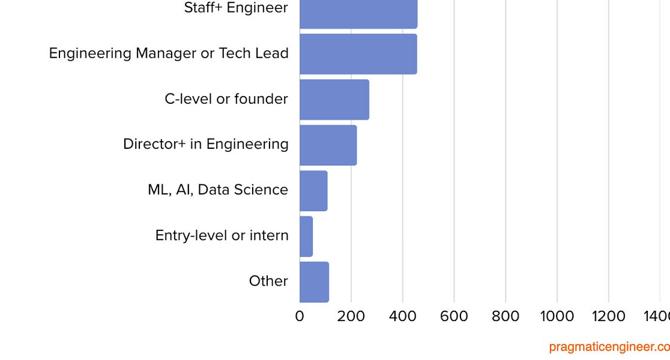
Image Credit: The Pragmatic Engineer
The Pragmatic Engineer 2025 Survey: What’s in your tech stack?
- The Pragmatic Engineer 2025 Survey reveals insights on the tech stack preferences of professionals.
- Over 2,900 tech professionals shared their opinions and tool choices, shedding light on current trends.
- From popular AI tools to most-loved programming languages and disliked tools, the survey covers various aspects.
- Insights on IDEs, terminals, version control, CI/CD, and cloud providers offer a comprehensive overview.
Read Full Article
7 Likes
Dev
167

Image Credit: Dev
Resource Management and Memory Efficiency in Web Servers(2170)
- Deep dive into resource management amid memory crisis in web server operations.
- Traditional approaches failed, leading to exploration of efficient resource management strategies.
- Framework implements sophisticated patterns for memory efficiency and performance in web servers.
- Approach includes memory allocation, connection pooling, and CPU utilization optimization techniques.
- Resource efficiency benchmarks highlight minimal allocation overhead and linear scaling characteristics.
Read Full Article
10 Likes
Dev
32

Image Credit: Dev
How a 10x Engineer Becomes a SCAMMER
- Soham Parekh, known for working multiple full-time jobs at the same time, is being called a scammer by some founders and developers.
- The concept of a '10x Engineer' can lead to being overworked and underpaid, prompting some to seek additional jobs for fair compensation.
- Critics view individuals taking on multiple roles as deceptive, but supporters argue it is a way to be compensated adequately for the work done.
- The key point emphasized is that delivery of quality work matters most, regardless of the number of jobs held, showcasing a gap in the current industry norms.
Read Full Article
Like
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Medium
306

Image Credit: Medium
GPT-5 just dropped: everything you need to know (no fluff, just facts)
- OpenAI has released GPT-5, its most advanced model yet, offering a significant improvement in performance, architecture, and flexibility.
- GPT-5 is not just an upgraded version of GPT-4 or Artificial General Intelligence (AGI).
- The article provides insights from various sources like official documentation, OpenAI announcement videos, Reddit threads, YouTube demos, and developer community reactions.
- Targeted at developers, hackers, and tech enthusiasts, the article aims to offer a comprehensive understanding of GPT-5 and its current applications.
Read Full Article
18 Likes
Dev
83

Image Credit: Dev
WebSocket Revolution in Real-Time Communication(0965)
- Exploring WebSocket technology for real-time web communication simplification and improved performance characteristics.
- Discovering a WebSocket framework that seamlessly integrates into web apps with enhanced performance.
- Evaluation of WebSocket's exceptional performance versus traditional HTTP polling and Server-Sent Events.
- Detailed examination of advanced WebSocket patterns, broadcasting, error handling, and real-world application examples.
- WebSocket's significant role in building scalable, efficient real-time applications highlighted with benchmark results.
Read Full Article
5 Likes
Dev
202

Image Credit: Dev
What Does Empathy Really Mean in Software Development?
- Empathy is essential in software development for communication, collaboration, and team effectiveness.
- A recent study explores the concept of empathy in software engineering using insights from real practitioners.
- The study identifies five key themes of empathy in software engineering, including understanding, perspective taking, embodiment, compassion, and emotional sharing.
- Empathy is a socio-technical skill that can enhance software quality and well-being by making it visible, addressing blockers, and offering strategies.
Read Full Article
12 Likes
Dev
184

Image Credit: Dev
Concurrency Mastery Through Advanced Async Programming(5161)
- Discover advanced async programming to achieve high concurrency in web development.
- Learn asynchronous models' efficiency in memory usage and scalability over traditional threading.
- Explore benchmark results, async patterns, error handling, testing, monitoring, and performance benefits.
Read Full Article
11 Likes
Medium
156
Image Credit: Medium
AI Gave Me Code That Looked Right — Then It Took Down Production
- The writer experienced a production server outage with an HTTP 500 error.
- The issue was caused by AI-generated code that appeared correct but brought down the system.
- The incident highlighted the potential risks of relying solely on AI code-generation tools for production systems.
- The writer learned from the experience and now approaches code written by AI tools with more caution to prevent future failures.
Read Full Article
9 Likes
Medium
335

Image Credit: Medium
X-Ray Vision for .NET 9: What Logs Couldn’t Tell Me in Production
- A team faced a production API slowdown in their .NET 9 microservices setup running on ECS Fargate despite normal readings from profilers and log aggregators.
- Despite having numerous traces, the team lacked clarity on the issue until they turned to AWS X-Ray for insight.
- The tool, though not as popular as others like OpenTelemetry, proved valuable in troubleshooting the bug that manifested only under large-scale conditions involving multiple services.
Read Full Article
20 Likes
PlanetPython
294

Image Credit: PlanetPython
Mike Driscoll: Creating TUI Applications with Textual and Python is Released
- Creating TUI Applications with Textual and Python introduces the Textual package, which facilitates building text-based user interfaces (TUIs) with Python for terminal and web browser applications.
- The book covers developing terminal applications using Textual and creating various applications such as a calculator, CSV viewer, text editor, MP3 player, ID3 editor, weather app, TUI for pre-commit, and an RSS reader.
- Readers can purchase the book on Amazon (Kindle and Paperback), Leanpub (eBook), and Gumroad (eBook) to learn how to use Textual and develop unique applications.
- The book aims to equip users with the knowledge and tools to craft striking TUI applications and includes challenges to enhance learning and spark creativity.
Read Full Article
17 Likes
Javacodegeeks
38

Image Credit: Javacodegeeks
Java 25 Features Overview
- Java 25 (JDK 25) introduces significant features for performance, observability, and language advancement.
- Enhancements include compact object headers, stable values, scoped values, JFR improvements, and Shenandoah GC.
- The release also includes API updates, structured concurrency, primitive types in patterns, and AOT improvements.
- Java 25 aims to enhance productivity, modularity, and application performance, solidifying its developer-friendly reputation.
Read Full Article
2 Likes
Logrocket
49

Image Credit: Logrocket
What to do when users just want the old version back
- Users often resist change in products due to unfamiliarity or unmet expectations.
- Guidelines for managing user resistance include explaining the 'why' and 'how' of changes.
- Incentivize early adoption, offer a 'back to old version' button, and engage opinion leaders.
- Launch strategies involve thorough testing, persuasive tactics, and user education on new features.
- Embracing change with a customer-focused approach can lead to successful product transitions.
Read Full Article
2 Likes
Self-Learning-Java
232
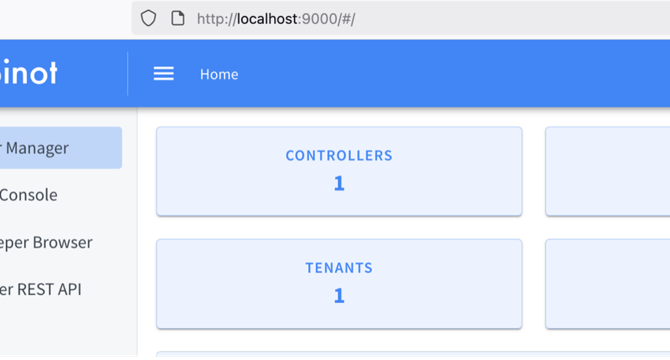
Image Credit: Self-Learning-Java
Ingesting Data into an Apache Pinot Real-Time Table from Kafka
- Apache Pinot can ingest records from sources like Apache Kafka for real-time analytics.
- Setup involves Kafka installation, topic creation, and log data ingestion for analysis.
- Guide covers schema definition, table configuration, and data source setup for testing.
- Configurations include Kafka topic creation, schema definition, table setup, and data ingestion.
Read Full Article
14 Likes
Dev
172

Image Credit: Dev
Swift 6.2 WebAssembly Revolution: Redefining Platform Boundaries
- Swift 6.2 introduces official WebAssembly support, reshaping cross-platform development for iOS developers.
- Transition from community efforts to Apple's official backing signifies a strategic shift for Swift.
- WebAssembly allows running Swift code in various environments, including web browsers and servers.
- Swift 6.2 simplifies setup for WebAssembly, enabling easy cross-compilation and execution of Wasm modules.
- Swift's WebAssembly empowers universal programming across iOS, web browsers, server environments, and more.
Read Full Article
10 Likes
For uninterrupted reading, download the app