Programming News
Dev
21

Image Credit: Dev
# Introducing Helpothon: Technology for Social Good
- Helpothon is a platform dedicated to leveraging technology for social good, empowering developers to innovate solutions for real-world problems.
- Key features of Helpothon include promoting technology for social good, fostering a community of collaboration and learning, and striving for a global impact through diverse perspectives.
- Developers can benefit from Helpothon by gaining experience with impactful projects, networking opportunities, and skill development in a supportive environment.
- Helpothon offers resources, project ideas, and mentorship opportunities for developers of all skill levels to contribute to making a global impact through technology for positive change.
Read Full Article
1 Like
The Pragmatic Engineer
227
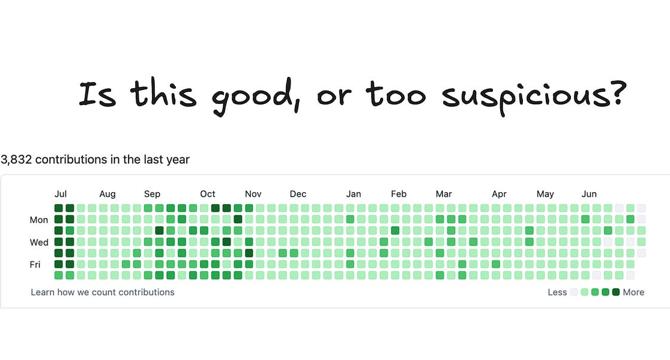
Image Credit: The Pragmatic Engineer
The 10x “overlemployed” engineer
- A software engineer in India scammed tech startups for a million dollars annually.
- Employed by multiple companies simultaneously, he excelled in interviews and then avoided work.
- Exposed by Y Combinator community, the engineer worked at 18 AI startups concurrently.
- Issue raises concerns about remote work, demand for AI engineers, and recruitment challenges.
- Remote work facilitated the scam, emphasizing importance of background checks and recruitment diligence.
Read Full Article
9 Likes
Medium
81

Image Credit: Medium
The journey of building decentralized connectivity takes another exciting step forward as $ROAM is…
- Trading $ROAM on PancakeSwap Solana DEX offers a seamless, permissionless experience for users with minimal transaction costs and rapid speeds, enhancing Roam Network's travel-to-earn ecosystem.
- Providing liquidity on PancakeSwap Solana allows users to earn rewards, support network stability, and contribute to efficient swaps, aligning with Roam Network's vision of decentralized global WiFi connectivity.
- The listing of $ROAM on Solana’s PancakeSwap DEX enables users to easily access tokens, redeem them for travel data, or stake them for additional benefits, integrating blockchain technology with travel needs.
- Roam Network's commitment to creating utility around $ROAM beyond speculation is exemplified through this listing, emphasizing user participation in building a decentralized connectivity ecosystem that is truly user-owned.
Read Full Article
4 Likes
Medium
21
Image Credit: Medium
You don’t need SignalR for real-time updates | Server-Sent Events in .NET/C#
- SignalR is not necessary for real-time updates in applications where separate parts need to be updated independently, such as notifications.
- Using SignalR for small data updates can be overkill as it holds an entire socket connection and operates in duplex mode.
- Server-Sent Events provide a more efficient approach for sending events with minimal client-side code and no delays between event occurrence and client reception.
- The article discusses creating an endpoint for Server-Sent Events, generating random values for notifications, updating the endpoint, and implementing the server-side and client-side parts for real-time updates.
Read Full Article
1 Like
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Medium
98

Image Credit: Medium
TypeScript Type Guards That Actually Matter
- Type guards in TypeScript help narrow types for safe and predictable code behavior.
- They ensure the compiler treats variables based on specific type-returning functions.
- By defining real type guard signatures, you control TypeScript's assumptions and type behavior.
- Type guards differentiate data shapes, enhance security, and guide TypeScript in handling types.
Read Full Article
5 Likes
Medium
365

Image Credit: Medium
Libraries In Solidity : Internal vs External
- Solidity libraries are collections of reusable functions that serve as smart contract modules for multiple contracts.
- There are two types of libraries in Solidity: internal and external, differing in integration into bytecode and runtime invocation.
- Internal libraries are embedded directly into the bytecode of the contract using them, while external libraries are standalone contracts deployed on the blockchain with their own address.
- Understanding the differences and nuances between internal and external libraries in Solidity is crucial for making informed architectural decisions when developing smart contracts.
Read Full Article
22 Likes
IEEE Spectrum
374

Image Credit: IEEE Spectrum
Ways to Bridge the U.S. Computer Science Education Gap
- About 58 percent of U.S. high schools offer dedicated computer science courses.
- Lack of CS education in schools highlights a skills gap in the U.S.
- Efforts aim to make CS courses mandatory in high schools and support teacher training.
- National policy needed to make computer science classes a graduation requirement.
- Inclusive teaching, early exposure, and empowered teachers can bridge the education gap.
Read Full Article
22 Likes
Dev
185

Image Credit: Dev
Memory Leak Terminator How Type Safety Saved My Graduation Project(1751563194544900)
- Junior computer science student shares experience with Hyperlane framework in building a project.
- Framework offers robust architecture, zero-cost abstractions, type safety, and performance guarantees.
- Features include context-driven architecture, middleware system, real-time communication support, and memory optimization.
- Performance analysis shows high throughput, low latency; framework excels in error handling and resilience.
- Future directions focus on WebAssembly, microservices, and ecosystem integration for modern web development.
Read Full Article
11 Likes
Dev
361

Image Credit: Dev
WebSocket Real Time Communication Guide(1751563101435600)
- As a junior computer science student, I explored WebSocket technology for real-time communication.
- WebSocket offers bidirectional, low-overhead messaging, ideal for chat systems and live updates.
- WebSocket Manager implementation showcases features like broadcasting, room management, and connection cleaning.
- Advanced WebSocket capabilities elevate real-time apps for multiplayer games and collaborative tools.
- Performance depends on serialization, connection handling, broadcasting efficiency, and memory management.
Read Full Article
21 Likes
Medium
17

Image Credit: Medium
A Way Out-My Journey From RagsTo Riches
- A determined individual shares their journey from struggling in school to building a successful SaaS tool.
- Starting with minimal coding knowledge, the individual embarked on a learning journey through various online resources.
- Despite facing imposter syndrome and feelings of inadequacy, the individual found motivation through humility and a love for the learning process.
- By focusing on personal growth, establishing healthy habits, and prioritizing deep work, the individual overcame challenges and achieved success in building their business.
Read Full Article
1 Like
Medium
17

Image Credit: Medium
The Iranian People: A Story of Unity in Times of War
- Iran's long history of resistance and unity has helped preserve its identity and culture despite numerous invasions and conquerors.
- The Iran-Iraq War from 1980 to 1988 showcased Iran's unity, with people from various ethnicities and religions standing together to defend their homeland.
- Even in modern times, Iranians continue to demonstrate solidarity in the face of challenges, showing a deep sense of national unity.
- The story of the Iranian people serves as a message to the world about the strength of unity in preserving a nation's identity and resilience.
Read Full Article
1 Like
Medium
413

Image Credit: Medium
Storing and Displaying User Avatars in Spring Boot Apps
- Handling user avatars in Spring Boot involves steps like upload validation and storage.
- Spring Boot simplifies file handling with features like handling multipart form data effortlessly.
- Validating uploaded avatars, storing them securely, resizing images, and controlling access are crucial.
- Ensuring authentication for avatar access, caching images, and careful handling of requests is important.
- Each step in the process, from upload to display, requires attention to details for success.
Read Full Article
24 Likes
VentureBeat
253

Image Credit: VentureBeat
Dust hits $6M ARR helping enterprises build AI agents that actually do stuff instead of just talking
- Dust, an AI platform, grows annual revenue to $6 million.
- Shift in enterprise AI adoption from chatbots to advanced systems.
- Dust's AI agents automate business tasks like updating CRM records and creating GitHub issues.
- Utilizes Model Context Protocol for secure data access and specialized orchestration.
- Represents trend of AI-native startups leveraging advanced AI capabilities for practical implementation.
Read Full Article
15 Likes
Javacodegeeks
228

Image Credit: Javacodegeeks
Dependency Injection in Micronaut vs. Spring: What You Need to Know
- Micronaut and Spring offer different approaches to dependency injection in Java development.
- While Spring uses runtime reflection, Micronaut utilizes compile-time analysis for DI.
- Micronaut excels in faster startup times and lower memory consumption compared to Spring.
- Understanding their differences can help developers choose the right framework for their projects.
Read Full Article
13 Likes
Krebsonsecurity
219

Big Tech’s Mixed Response to U.S. Treasury Sanctions
- U.S. Treasury sanctions Chinese national for connections to virtual currency scams.
- Tech companies like Facebook, PayPal, GitHub maintain accounts linked to the accused.
- Despite sanctions, big tech firms did not suspend online accounts of the individual.
- Silent Push flags multiple accounts, calls for tech companies to sever ties.
Read Full Article
13 Likes
For uninterrupted reading, download the app