Programming News
Medium
340

Image Credit: Medium
The Curious Case of LeetCode 523: Memorize or Prove? I Chose to Learn
- The author of the article discusses their experience with solving a specific problem on LeetCode and choosing to understand the 'why' behind the solution rather than just the 'what.'
- They found the official solution unsatisfying and decided to figure it out themselves from scratch, wanting to be able to explain it to others.
- Upon posting their detailed explanation, they received positive feedback from a higher-ranked user, emphasizing the value of clarity over speed in problem-solving.
- The author highlights the importance of understanding over memorization and emphasizes the value of explanations that help others comprehend solutions effectively.
Read Full Article
20 Likes
Dev
357

Image Credit: Dev
Flame Graph Performance Truth Analysis(1751213807259200)
- Discover how flame graphs revolutionized a junior computer science student's approach to performance optimization.
- Learn how to make data-driven decisions, focus on hot functions, and balance complexity.
- Flame graphs offer insight into program performance, guiding scientific performance analysis and optimization.
- Experience the transformative power of flame graphs in practical code practice and performance analysis.
Read Full Article
21 Likes
Medium
46
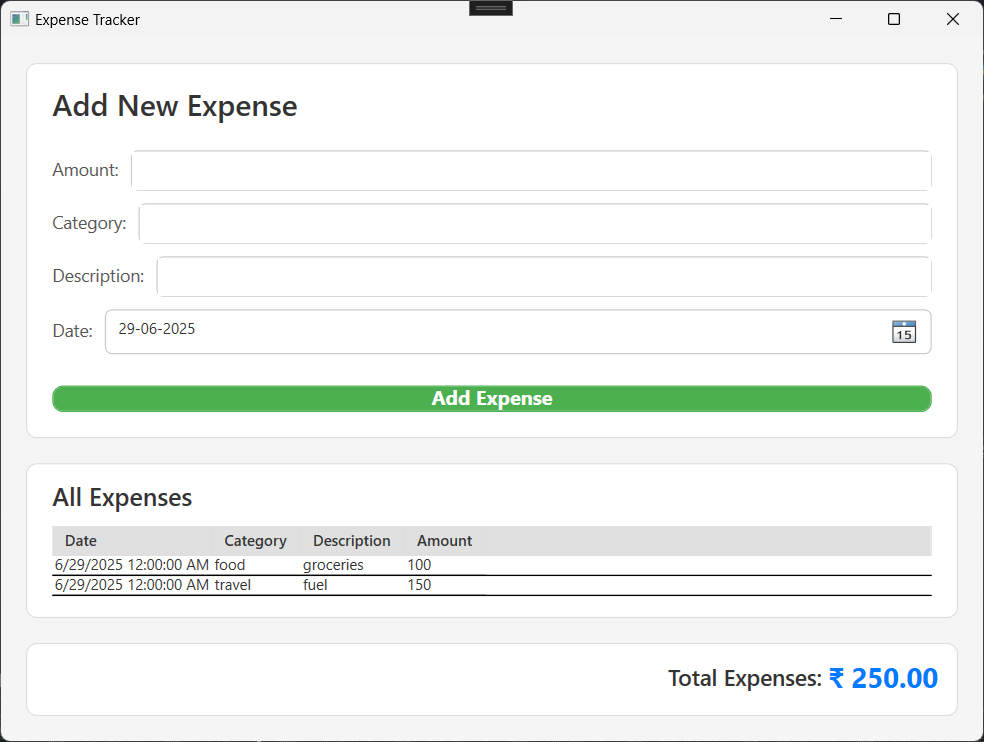
Image Credit: Medium
Building a WPF Expense Tracker with Gemini: A Developer’s Companion
- WPF paired with C# is a robust framework for developing desktop applications offering a separation of concerns between UI and logic, rich data binding capabilities, and customizable rendering.
- Gemini acted as an intelligent assistant in building a personal expense tracker by providing code snippets, explanations, and troubleshooting advice, significantly speeding up the development process.
- Gemini efficiently addressed XAML errors by suggesting targeted solutions, enhancing the debugging experience and acting as a mentor throughout development.
- The Expense Tracker project involved defining UI layout in XAML and implementing backend logic in C#, showcasing how AI can enhance software development by accelerating tasks and problem-solving.
Read Full Article
2 Likes
Dev
141

Image Credit: Dev
Global Bluetooth Chip Market Trends in 2025: Key Dynamics and Technological Advancements
- Global Bluetooth chip market projected to reach 7.5 billion units in 2025 with a 13% YoY growth driven by IoT and smart wearable demand.
- Key players in the market include Apple, leading in premium TWS market share, and JieLi Technology dominating the cost-performance segment.
- Technological advancements include Bluetooth 6.0 with enhanced transmission efficiency and LE Audio enabling multi-device sync and reduced latency.
- Challenges in the market include patent dominance by Apple/Qualcomm and the need for Chinese vendors to innovate in audio decoding and noise cancellation.
Read Full Article
8 Likes
Discover more
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Dev
293

Image Credit: Dev
Heartbeat of Modern Web Real Time Patterns User Design(1751213167065000)
- Explore the captivating realm of modern internet applications with real-time interactions. Discover the
- powerful backend technologies enabling instant feedback, seamless collaboration, and real-time updates in
- applications. Learn the significance of asynchronous programming and high-performance frameworks in achieving
- the pulse of real-time interaction for a thrilling development experience.
Read Full Article
17 Likes
Dev
76

Image Credit: Dev
🌐 Frameworks That Will Dominate Web Development in 2026
- Frameworks in 2026 prioritize speed, AI, scalability, and toolchain integration.
- Popular frameworks include Next.js, Astro, SvelteKit, Remix, and more.
- They cater to diverse needs like UI speed, resumability, and fullstack development.
Read Full Article
4 Likes
Dev
138

Image Credit: Dev
This Is How I Mastered TypeScript Like I'm 5 (Type Inference!)(7)
- TypeScript can infer types for variables without explicit declarations.
- Type inference helps by guessing the types based on assigned values.
- It is important to be explicit with types for empty or complex variables to avoid TypeScript inferring the 'any' type.
- TypeScript's type inference is beneficial for quick development but explicit type declarations are crucial for clarity and teamwork.
Read Full Article
8 Likes
Medium
154

Image Credit: Medium
Learning to Code Won’t Make You Smarter — But This Will
- Learning to code alone won't make you smarter; what matters is the ability to think like a coder.
- Memorizing syntax and completing courses may not help in solving real problems effectively.
- The focus should shift from coding to problem-solving for cognitive growth and technical skill improvement.
- Problem-solving is essential; coding is just a tool, and the mindset shift is crucial for success in complex tasks.
Read Full Article
9 Likes
Dev
247

Image Credit: Dev
Exploring ReplaySubject in RxJS: How to Replay Past Values in Angular
- ReplaySubject in RxJS allows for replaying multiple previously emitted values to new subscribers, unlike BehaviorSubject.
- It does not require an initial value and is beneficial when late subscribers must receive previously emitted data.
- An example implementation of ReplaySubject in an Angular app using HTML and TypeScript is provided, demonstrating its usage.
- ReplaySubject is structured to buffer and replay emitted values based on certain configurations, making it ideal for providing context to late subscribers.
Read Full Article
14 Likes
Dev
204

Image Credit: Dev
Macros Explained for Java Developers
- Java developers often use Project Lombok, Jakarta Bean Validation, AutoValue, MapStruct, or Immutables to reduce boilerplate and simplify code.
- Macros in languages like Lisp or Clojure are compile-time programs that transform code before execution, allowing the creation of new control structures and domain-specific languages.
- Java doesn't support macros directly but utilizes annotation processors and code generation tools like Lombok and MapStruct to achieve similar functionality within the language.
- Real macros in languages like Clojure enable developers to define new features, validators, and more, offering the ability to extend the language with custom syntax and behaviors.
Read Full Article
12 Likes
Medium
144

Image Credit: Medium
Today's Important Global and Regional News | Full Report
- Israeli forces are preparing for more extensive military operations against Iran despite the ceasefire, targeting perceived threats.
- In Gaza, a humanitarian crisis is escalating with over 66 children dying of starvation and severe malnutrition, drawing concern from international organizations.
- Hezbollah's leader asserts their capability to respond to Israeli aggression as a principled and humanitarian duty.
- Internal unrest in Israeli society is growing as soldiers reportedly refuse to go to Gaza, indicating dissatisfaction with war policies.
Read Full Article
8 Likes
Dev
80

Image Credit: Dev
CharacterKB: Your AI-Powered Companion for Fictional Characters
- CharacterKB is an AI platform changing how users interact with fictional characters.
- Utilizing MindsDB's Knowledge Bases, it offers character discovery, insights, analysis, and chat.
- AI tools like semantic search and psychological profiling enhance user experience.
- The tech stack includes MindsDB, FastAPI, React, OpenAI, and Google Custom Search API.
- CharacterKB integrates MindsDB functionalities for intelligent character discovery, chat, and enriched information.
Read Full Article
4 Likes
Dev
264

Image Credit: Dev
How to Fix React Hydration Mismatches with a Simple Inline Script Hack (Zero Flicker SSR)
- React's hydration process in server-side rendering (SSR) is critical for attaching event handlers to server-rendered HTML.
- Hydration mismatches can occur when server and client render different content; for example, based on browser cookies.
- A simple inline script hack is introduced to handle server/client content differences without triggering React's hydration errors.
- The approach involves using an inline script that runs before hydration, ensuring the content matches on both server and client sides.
Read Full Article
15 Likes
Dev
366

Image Credit: Dev
Supercharge Your React Native App State Handling with `useAppVisibility`
- Tracking app visibility states can be challenging and error-prone without proper handling.
- Learn to use useAppVisibility Hook for more efficient state management in React Native.
- The Hook exposes flags, emits callbacks, tracks durations, and plays nicely with TypeScript.
- Enhanced Hook offers typed API, duration tracking, predictable transitions, and cleanup on unmount.
- Improve app performance and user experience with proper app visibility handling techniques.
Read Full Article
22 Likes
Dev
46

Image Credit: Dev
Ecosystem Integration Patterns Third Party Design(1751203563983100)
- Choosing a framework is also about selecting an ecosystem for web development.
- The Rust framework discussed showcases seamless integration within the Rust ecosystem.
- Features include database and Redis integration, logging and monitoring, and configuration management.
- Benefits include efficiency, code quality, performance optimization, and reduced development time.
- The framework leverages the Rust ecosystem to enhance development and maintenance convenience.
Read Full Article
2 Likes
For uninterrupted reading, download the app