Software News
Medium
383
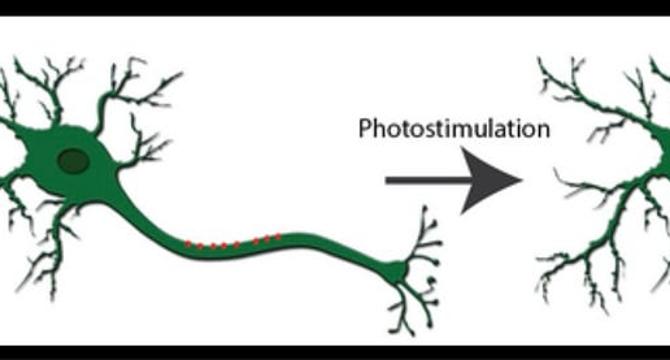
Image Credit: Medium
Optogenetics: Illuminating Neural Circuits with Light
- Optogenetics integrates genetic engineering and optics to control and monitor specific cells, like neurons, using light.
- Researchers introduce genes encoding photosensitive proteins (opsins) into cells, allowing control with high temporal and spatial resolution.
- Karl Deisseroth pioneered optogenetics in the mid-2000s, enabling precise neural circuit control with Channelrhodopsin-2.
- The technique combines genetics and optics for on-demand control of excitable cells, modulating neural excitability with light.
- Light-sensitive proteins like Channelrhodopsin-2 or Halorhodopsin are commonly used to either excite or suppress neural activity.
- Genetic delivery methods like viral vectors or transgenic animal lines are employed to express opsins in targeted cells.
- Light delivery methods include optical fibers or miniaturized LEDs/lasers implanted to illuminate specific brain regions in living animals.
- Optogenetics has revolutionized neuroscience by allowing precise control over neuronal firing, mapping neural circuits, and linking brain activity to behavior.
- Potential medical applications include vision restoration, neurological and psychiatric disorder treatments, and cardiac arrhythmia control using optogenetic therapies.
- Recent advancements in optogenetics include engineered opsins for improved features, advanced light delivery systems, and wireless multi-site stimulation technologies.
Read Full Article
23 Likes
Medium
258

Design of a Network Vulnerability Scanner: Defining the Scope
- The focus is on the design and architecture of a Network Vulnerability Scanner, providing insight into how the scanning components interact and the considerations behind building an effective scanner.
- The article highlights the importance of design choices and discusses utilizing tools like Nmap and CVE databases for efficient scanning.
- Before delving into specific components, defining the scope of the network vulnerability scanner is emphasized as a crucial step in managing expectations and directing efforts.
- The network vulnerability scanner is explained as a system comprising multiple specialized tools that work together, with key players including the scanning engine and various components.
Read Full Article
15 Likes
Sdtimes
378

Image Credit: Sdtimes
Grafana 12 is now available with new observability as code features, Dynamic Dashboards, and more
- Grafana Labs released Grafana 12 at GrafanaCON, introducing observability as code features for versioning, validating, and deploying dashboards using code.
- New feature Dynamic Dashboards allows displaying the right information at the right time with tab navigation and conditional rendering.
- Other features in Grafana 12 include native alert and recording rule management, dashboard syncing to GitHub, consistent API model, table visualization updates, and more.
- Additionally, Grafana Labs announced a private preview of Grafana Assistant in Grafana Cloud, an AI-powered chat experience, and the donation of Grafana Beyla to OpenTelemetry.
Read Full Article
22 Likes
Byte Byte Go
280

Image Credit: Byte Byte Go
Messaging Patterns Explained: Pub-Sub, Queues, and Event Streams
- Modern software operates across clusters, web applications, and various data platforms, making coordination, latency, and reliability crucial.
- Messaging patterns play a vital role in this scenario, decoupling sender from receiver and enabling asynchronous communication.
- Three main messaging patterns are Message Queues, Publish-Subscribe, and Event Streams, each with its own characteristics and use cases.
- These patterns offer solutions for tasks like background job processing, high-throughput analytics, and real-time communication, with trade-offs in aspects like reliability and complexity.
Read Full Article
15 Likes
Discover more
- Programming News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Tech Radar
178

Image Credit: Tech Radar
Fed up with irrelevant results cluttering up your Windows 11 searches? I certainly am, and it looks like the situation’s going downhill from here
- Microsoft is set to include Microsoft Store apps in Windows 11 search results, allowing users to quickly install relevant apps.
- The integration will highlight apps from the store that match search queries, giving users the option to download them directly.
- Some users are expressing discontent with this upcoming change, hoping for the ability to disable it.
- The feature announcement was made by Giorgio Sardo, causing mixed reactions from users.
- Critics worry that this will be another feature to disable and are uncertain if it can be turned off.
- Although the search integration seems imminent, Microsoft has not clarified if users can opt-out of it.
- Recent updates to improve Windows 11 search include natural language functionality for Copilot+ PCs.
- The Microsoft Store performance enhancements have received less attention compared to search improvements.
- Microsoft is also introducing the ability to find Windows settings and enhance Windows search functionality.
- Despite some concerns, the search changes aim to improve user experience by facilitating easier app installations.
Read Full Article
10 Likes
Medium
400

REST API Design: Building Blocks for Scalable Systems
- REST APIs utilize HTTP requests for CRUD operations on resources, following six guiding architectural constraints for being truly RESTful.
- Key principles include resource identification, client-server architecture, statelessness, cacheability, layered system, and optional code on demand.
- REST API design focuses on resources over actions, using nouns for endpoints, standard HTTP methods, and proper use of HTTP status codes.
- Best practices include pagination, filtering, versioning, error handling, authentication, rate limiting, HTTPS encryption, documentation, and strategies for evolving APIs.
- Common REST API anti-patterns to avoid include ignoring HTTP method semantics, creating operation-based endpoints, returning inconsistent responses, neglecting documentation, and tight coupling between API and client.
Read Full Article
24 Likes
Cinema5D
271

Image Credit: Cinema5D
Blackmagic Camera 2.2 for Android Update Released – Adds Cloud Folder Support, APV Codec & More
- Blackmagic Design has released version 2.2 of its Blackmagic Camera app for Android, enhancing mobile filmmaking workflows.
- The update includes support for Blackmagic Cloud Folders, the new APV codec on Android 16, UI improvements, and stability enhancements.
- The app allows manual control over settings, professional file format recording, and seamless integration with Blackmagic Cloud and DaVinci Resolve workflows.
- Version 2.2 adds support for Android 16, APV codec, cloud account deletion, histogram pop-up, permission controls, UI adjustments, and bug fixes.
Read Full Article
16 Likes
Knowridge
249

Image Credit: Knowridge
New aluminum alloy breakthrough could revolutionize car manufacturing
- Researchers from Carnegie Mellon University and MIT have developed a new aluminum alloy system for car manufacturing.
- The innovative alloy, Al-Ni-Er-Zr-Y, combines high strength with cost-effectiveness, addressing limitations of traditional aluminum alloys.
- This breakthrough material could lead to stronger and cheaper car parts, potentially improving fuel efficiency and reducing manufacturing expenses.
- The alloy's development involved advanced computer simulations, additive manufacturing technology, and a unique mix of metals to optimize strength and cost.
Read Full Article
15 Likes
Hackernoon
262

Image Credit: Hackernoon
BingX Unveils ChainSpot: A CeDeFi Innovation for Simpler and Safer On-Chain Trading
- BingX unveils ChainSpot, a CeDeFi feature that allows users to access decentralized tokens directly from their BingX accounts without using external wallets or complex on-chain processes.
- As part of its 7th anniversary celebration, BingX introduces ChainSpot, combining centralized and decentralized features to provide an innovative on-chain trading experience.
- ChainSpot promises simplified and secure on-chain trading with benefits like enhanced security measures, broader asset access, smarter discovery tools, and cross-chain compatibility within a centralized exchange interface.
- Vivien Lin, BingX's Chief Product Officer, emphasizes that ChainSpot is designed to offer users decentralized opportunities while maintaining the security and convenience of the platform, aiming to redefine access to DeFi in a user-friendly and protected manner.
Read Full Article
15 Likes
TheNewsCrypto
307

Cronos EVM Launches Stargate-Powered ETH and USDC Pools with LayerZero Integration
- Cronos EVM, Cronos’ Ethereum-compatible blockchain, has launched two new Stargate pools, ETH and USDC, providing deep liquidity with LayerZero integration.
- Stargate's liquidity architecture, based on LayerZero, connects users to over 50 blockchains, unifying liquidity, and ensuring smooth interoperability.
- Cronos' integration of Stargate aims to enhance the end-user experience through token bridging and empower dapp developers by offering unified liquidity for creating cross-chain solutions.
- Cronos ecosystem's connection with Stargate's linked chains will enable fast and easy movement across blockchain networks, promoting increased TVL and liquidity depth.
Read Full Article
18 Likes
Pcgamer
258

Image Credit: Pcgamer
Here's how long it would take 12 RTX 5090 GPUs to crack your password… and a reminder that just adding more characters still works
- Hive Systems released its 2025 Password Table showcasing the time it takes 12 Nvidia GeForce RTX 5090 GPUs to crack passwords.
- For an 8-character password with lowercase letters and numbers, it only takes 3 weeks for the GPUs to crack it.
- Increasing the complexity by adding uppercase letters, numbers, and symbols can significantly increase the cracking time.
- Using passwords with 15 characters or more, including different character types, greatly enhances security against brute force attacks.
Read Full Article
15 Likes
TheNewsCrypto
423

Space and Time Launches on Mainnet to Boost Data-Driven Crypto Apps
- Space and Time has launched on its public, permissionless mainnet, backed by Microsoft, to provide smart contracts with ZK-proven data for data-driven cryptocurrency applications.
- The platform allows developers to access, query, and ZK-prove data from a decentralized network of database validators, indexing data from Ethereum and other major blockchains.
- Smart contracts previously struggled to access offchain, cross-chain, or historical data, limiting the sophistication of onchain applications, which Space and Time aims to address.
- MakeInfinite Labs, the developers behind Space and Time, have also created technologies like Proof of SQL and Blitzar to enhance the crypto ecosystem and enable verifiable, data-driven applications.
Read Full Article
25 Likes
Medium
71
Image Credit: Medium
Building Privacy-Preserving dApps: Tools and Strategies
- Building privacy-preserving decentralized applications (dApps) is crucial to protect user privacy in Web3.
- Blockchain's transparency poses a challenge with potentially sensitive information being public.
- Tools like Zero-Knowledge Proofs (ZKPs), Tornado Cash, Multi-Party Computation (MPC), and private blockchains enhance privacy in dApps.
- Zero-Knowledge Proofs allow verifying actions without revealing sensitive data, exemplified by Zcash's shielded transactions.
- Tornado Cash is a decentralized mixer for anonymous transactions, enhancing financial privacy in dApps.
- Multi-Party Computation ensures private voting, auctions, and data sharing in dApps.
- Private blockchains restrict participation and data visibility for enhanced privacy, suitable for specific use cases like enterprise applications.
- Multi-Party Contract Execution (MPC) on the Conflux Network introduces a Confidential Virtual Machine for executing transactions without exposing sensitive data.
- To build privacy-preserving dApps, strategies include minimizing data collection, using off-chain data for sensitive information, and offering opt-in privacy features.
- Developers can leverage tools like ZKPs, MPC, and off-chain storage to create dApps that balance transparency and privacy.
Read Full Article
4 Likes
Global Fintech Series
262

Image Credit: Global Fintech Series
SmartMedia Technologies Launches ‘Pay with Points’ Tokenized Loyalty Network
- SmartMedia Technologies has launched the 'Pay with Points' Tokenized Loyalty Network.
- Consumers can now tap to pay with loyalty points anywhere stable coins are accepted.
- The network allows loyalty points to be converted to branded tokens, enabling instant payment at the point of sale.
- This innovation merges digital loyalty with real-world cardholder engagement, offering new opportunities for loyalty program managers.
Read Full Article
15 Likes
Medium
302

Image Credit: Medium
5 Powerful JavaScript Array Methods That 98% of Developers Overlook (You Shouldn’t)
- Developers often overlook lesser-known JavaScript array methods that can improve code readability and efficiency.
- In this article, 5 powerful JavaScript array methods that only 2% of developers use are highlighted.
- These methods include .at() for accessing elements, flatMap() for flattening arrays, groupBy() for grouping elements, findLast() for finding the last matching item, and toSorted() for sorting without mutating the original array.
- By mastering these methods, developers can write cleaner, smarter, and more efficient code.
Read Full Article
18 Likes
For uninterrupted reading, download the app