Software News
Tech Radar
373

Image Credit: Tech Radar
Want to be the next Spielberg? Google’s AI-powered Flow could bring your movie ideas to life
- Google has launched a new AI-based filmmaking tool called Flow, allowing filmmakers to generate cinematic scenes and characters from text prompts.
- Flow utilizes Google's AI models to assist in exploring storytelling ideas without the need for filming clips or storyboarding manually.
- Filmmakers can integrate their own assets into Flow, which can be manipulated for camera angles, perspectives, and motion with ease.
- Flow will be available for subscribers of Google AI Pro and Ultra plans in the US initially, potentially revolutionizing the way movies are created by offering powerful creative tools.
Read Full Article
22 Likes
Tech Radar
47

Image Credit: Tech Radar
Gemini Live is now free for everyone on Android and iOS, and you can finally share your screen and camera on iPhone - here's how to try it
- Google's Gemini Live is now available for free on both Android and iOS platforms.
- iOS users can now share their screen and camera using Gemini Live, which was previously limited to Android users.
- Expect more integration of Gemini Live with Google apps in the upcoming weeks, enhancing AI interactions with devices.
- Gemini Live's features were announced at Google I/O event, including free access, iOS rollout, and deeper integration into daily life.
Read Full Article
2 Likes
Tech Radar
264

Image Credit: Tech Radar
Google's Veo 3 marks the end of AI video's 'silent era'
- Google introduced the Veo 3 AI video generation model at Google I/O 2025, marking a significant advancement in AI video technology.
- Veo 3 can combine audio and video seamlessly, a feature not found in other AI video generation tools like Sora and Pika, potentially revolutionizing content creation.
- This innovation represents a move away from the 'silent era' of video generation, as Veo 3 can generate synchronized audio along with high-quality video output.
- Veo 3 is currently available in the US as part of the Ultra tier in the Gemini App, offering a range of new features including dialogue generation and advanced video manipulation abilities.
Read Full Article
15 Likes
Engadget
4

Image Credit: Engadget
Google's Veo 3 AI model can generate videos with sound
- Google has unveiled Veo 3, its latest AI model that can generate videos with sound, making it the first of its kind.
- The Veo 3 model is currently available for Gemini Ultra subscribers in the US and enterprise users on Vertex AI, as well as in Google's AI filmmaking tool, Flow.
- Google introduced Flow, a new tool that combines Veo, Imagen, and Gemini to create cinematic clips and scenes based on users' natural language descriptions.
- Additionally, Google launched Imagen 4 for generating intricate images, and SynthID Detector to help identify AI-generated content by using watermarking and identification tools.
Read Full Article
Like
Discover more
- Programming News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Operating Systems News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Tech Radar
338

Image Credit: Tech Radar
Google finally gave us a closer look at Android XR – here are 4 new things we've learned
- Google showcased Android XR at I/O 2025, featuring AI-driven features like live translation.
- Google Gemini powers Android XR, offering advanced AI capabilities for hands-free assistance.
- Additionally, several glasses brands, including Xreal, Gentle Monster, and Warby Parker, will incorporate Android XR features.
- Project Moohan, an Android XR headset, is expected to launch in 2025 without a confirmed release date.
- Google's competition with Meta and its Quest headset hardware suggests a balanced rivalry in the XR space.
- The Android XR showcase hints at potential challenges for Meta but keeps the competition balanced for consumers' benefit.
- Meta's upcoming Connect 2025 showcase is anticipated to reveal similar glasses tech and features.
- Competition between Google's Android XR and Meta's offerings is set to benefit consumers by pushing innovation and pricing.
- Overall, the showcase suggests an exciting future in the XR space with competing technologies driving advancements.
- Potential release timelines indicate a competitive market as both Google and Meta aim to captivate consumers with their unique offerings.
Read Full Article
20 Likes
Tech Radar
30

Image Credit: Tech Radar
Xreal is making Android XR glasses and this could be the biggest XR announcement since the Meta Quest 2 – here’s why
- Xreal is working on Android XR glasses, codenamed Project Aura, in collaboration with Google and Qualcomm.
- Project Aura by Xreal is the second official Android XR device, showcasing AR elements that create a private movie theatre-like experience.
- The Xreal Project Aura, classified as an optical see-through XR device, aims to compete with other smart glasses with superior technology and Google's Android XR software.
- With Project Aura being tethered and featuring Qualcomm processors, Xreal aims to offer advanced spatial computing capabilities.
- Details about cost and release date of Project Aura are yet to be disclosed, promising further revelations at the Augmented World Expo.
- Xreal's CEO anticipates Project Aura to be a breakthrough moment for real-world XR, potentially offering cost-effective entry into XR glasses.
- The partnership of Google and Xreal in Android XR poses a threat to Meta's dominance in XR, potentially leading to competition and better devices for consumers.
- Android XR may challenge Meta's Horizon OS with a diverse range of XR hardware options backed by Google, Samsung, and Xreal.
- The future of Android XR in terms of app quality and variety could significantly impact Meta's standing in the XR space.
- Google's strong start in the XR market with Android XR could put pressure on Meta to respond and innovate further.
Read Full Article
1 Like
Engadget
381
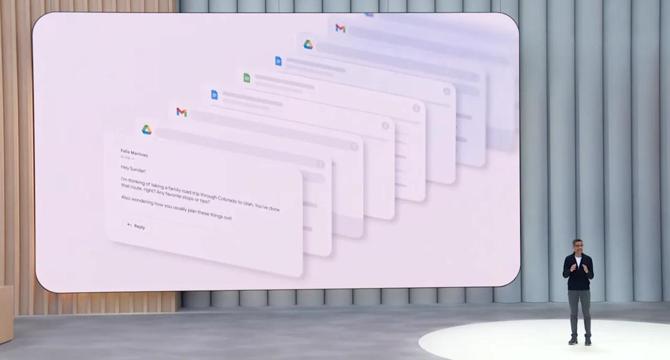
Image Credit: Engadget
Personalized AI-powered Smart Replies are coming to Gmail
- Google's Gemini AI will bring Personalized Smart Replies to the upcoming Gmail app, analyzing past emails and Google Docs to assist in composing responses.
- Gemini can create email drafts based on user's typical tone, style, and words used, as showcased by CEO Sundar Pichai using an example of planning a trip.
- New features like Inbox cleanup and fast appointment scheduling are also introduced to help manage emails efficiently, with a focus on Workspace subscribers.
- While these updates may benefit many users, some find Google's integration of Gemini features intrusive and unwelcome.
Read Full Article
22 Likes
Tech Radar
416

Image Credit: Tech Radar
Google CEO: AI is not a 'zero-sum moment' for search
- Google announced the full rollout of AI Mode for all US Google Search users at Google I/O in California, merging AI with traditional web search paradigms.
- AI Mode offers a fundamental shift in search by using generative models to provide comprehensive results on the Google result page.
- AI Mode is an advanced version that enhances reasoning and can handle longer and more complex queries, indicating a significant change in the Google Search experience.
- Google CEO Sundar Pichai views the integration of AI in search as an exciting development, emphasizing increased engagement and expanding use cases while suggesting that AI adoption in search is a positive advancement.
Read Full Article
25 Likes
Tech Radar
134

Image Credit: Tech Radar
Gemini’s AI images have been updated to Imagen 4 with a ‘huge step forward in quality’ – here’s what you need to know
- Google has announced an upgrade to its AI image generation tool – Imagen 4, which offers higher resolution and improved text handling.
- Imagen 4 provides 2K images with more detail, better typography, and the ability to create larger images for presentations.
- The new version is claimed to excel in fine details like water droplets and animal fur, as well as realistic and abstract styles.
- Imagen 4 is not only available in Gemini but also across various Google apps with a future faster variant in the works.
Read Full Article
8 Likes
Tech Radar
82

Image Credit: Tech Radar
Google Gemini 2.5 just got a new 'Deep Think' mode – and 6 other upgrades
- Google Gemini 2.5 Pro introduces a new 'Deep Think' mode to enhance reasoning capabilities.
- Deep Think enables Gemini to analyze multiple reasoning paths simultaneously before responding.
- The Deep Think mode aims to boost accuracy in handling complex mathematical and coding queries.
- Gemini's AI in Deep Think mode undergoes parallel reasoning before providing responses, akin to cautious decision-making.
- Initial tests show Deep Think excelling in math challenges, programming tests, and reasoning tasks.
- Deep Think is currently available to select testers, with plans to expand its accessibility in the future.
- Gemini 2.5 Pro now supports native audio generation with affective dialogue capabilities for personalized interactions.
- Proactive Audio feature in Gemini filters background noise to enhance interaction accuracy.
- Gemini 2.5 incorporates a 'thinking budget' for developers to control the depth of model reasoning.
- Google emphasizes deeper reasoning over speed, focusing on understanding questions and providing thoughtful responses.
Read Full Article
4 Likes
Tech Radar
242

Image Credit: Tech Radar
Gemini AI Ultra is Google's new ultimate 'VIP' plan for AI obsessives – here's what you get for its staggering price tag
- Google has launched a new ultra premium AI subscription service called Google AI Ultra in the US, priced at $250 a month.
- Google AI Ultra offers the highest usage limits and access to premium features, targeting filmmakers, developers, and creative professionals.
- The subscription includes exclusive features like Gemini app access, advanced video generation tools, 30 TB of storage, and more.
- A special offer of 50% off for the first three months is available for US users, with plans to expand the service to more countries soon.
Read Full Article
14 Likes
Hackernoon
195

Image Credit: Hackernoon
BingX AI Evolution Begins: A $300M Vision To Build The Future Of AI-Powered Crypto
- BingX, a leading cryptocurrency exchange and Web3 AI company, has announced the BingX AI Evolution strategy with a $300 million investment over the next three years.
- The initiative aims to integrate artificial intelligence into every aspect of BingX's platform to redefine crypto with AI and enhance user experience and industry collaboration.
- BingX will deploy AI tools to support users in trading smarter, accelerate investments in AI-native projects, and become an AI-native company in operations and decision-making.
- The long-term vision includes playing a leadership role in building a responsible Web3 AI ecosystem, establishing an AI institute, and shaping the future of crypto with intelligence and inclusivity.
Read Full Article
11 Likes
TechBullion
429

Image Credit: TechBullion
LITRBULL Games Announces First Major CEX Listing of $LITR Token on MEXC
- LITRBULL Games announced the listing of its native $LITR token on the MEXC exchange against Tether USDT on May 20.
- MEXC exchange plans to distribute 50 million $LITR tokens as a prize pool and open withdrawals on May 21, 2025, at 10:00 UTC.
- LITRBULL game, a Telegram-native Gamifi project on TON, has achieved over 300,000 users, with plans for further CEX listings.
- The $LITR token has a total supply of 8,045,311,447, with plans for staking to earn passive income and future game developments in 2025.
Read Full Article
25 Likes
Engadget
173

Image Credit: Engadget
Screen and camera sharing in Gemini Live is heading to all Android and iOS devices
- Gemini Live camera and screen sharing is now available on all compatible Android and iOS devices after being introduced on Pixel phones last month.
- This capability allows users to share their phone's camera or screen content with Google's AI, enabling easier access to information on complex topics through object recognition.
- Google plans to integrate Gemini Live more deeply with apps like Google Maps, Calendar, Tasks, and Keep in the coming weeks for more relevant responses to user queries.
- Users can manage app connections within the Gemini app for data privacy, and Google emphasizes the ease of adjusting settings at any time to address user concerns.
Read Full Article
10 Likes
TechBullion
212

Image Credit: TechBullion
New Scanner Technology at Stock Market Guides Shows the Historical Track Record of Each Trade Setup It Finds
- Stock Market Guides introduces a new improvement to its stock scanner technology that shows the historical performance of each trade setup it identifies through backtest research.
- The updated scanner is beneficial for active stock traders, buy-and-hold investors, and option traders, catering to both technical and fundamental analysis-based trade setups.
- Customers can utilize the scanner for stock trades and stock options, enabling it to suggest trades for them.
- Stock Market Guides, based in Altadena, California, has been offering stock scanning services since 2023 and provides free educational guides to help users make informed financial decisions.
Read Full Article
12 Likes
For uninterrupted reading, download the app