Cyber Security News
Securityaffairs
89
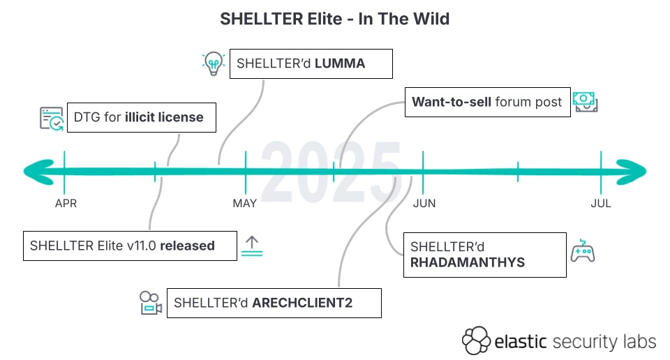
Image Credit: Securityaffairs
Hackers weaponize Shellter red teaming tool to spread infostealers
- Hackers exploit leaked Shellter Elite copy for infostealer attacks, bypassing security measures.
- Elastic Security Labs identifies malware campaigns using Shellter for evasion and malware deployment.
- Dynamic unpacker released by Elastic to detect and analyze SHELLTER-protected malware more effectively.
- Threat actors adopt Shellter for infostealer attacks, prompting efforts to counter abuse.
Read Full Article
5 Likes
Dev
279

Image Credit: Dev
How to Secure a Website and How SafeLine Helps
- Securing your website is essential in today's digital landscape to protect against bots, attackers, and vulnerabilities.
- Key strategies include using HTTPS, hardening HTTP headers, blocking common web attacks, implementing rate limiting, protecting admin panels, monitoring traffic, and self-hosting for maximum privacy.
- SafeLine WAF can assist in enforcing HTTPS, injecting custom security headers, detecting web threats with a semantic analysis engine, and providing rate limiting and abuse protection features.
- It offers real-time notifications, threat intelligence dashboards, and self-hosted solutions for website security without compromising privacy.
- The article qualifies for web story generation.
Read Full Article
16 Likes
Fintechnews
195
Image Credit: Fintechnews
Crypto Hacks Already Cost US$2.1 Billion in 2025 as State Attacks Rise
- In the first six months of 2025, the crypto industry suffered over US$2.1 billion in losses due to hacks and exploits across 75 incidents.
- State-sponsored actors are increasingly targeting critical financial infrastructure in the crypto space, exploiting its borderless and currently unregulated nature.
- The Bybit breach, attributed to North Korean hackers, resulted in over US$1.5 billion in losses, showcasing the intensity and speed of cyberattacks in the crypto realm.
- Crypto crime is evolving into a geopolitical tool, with state-aligned groups like Gonjeshke Darande from Iran using digital asset theft for symbolic or political motives.
Read Full Article
11 Likes
Semiengineering
205

Image Credit: Semiengineering
PUFs In A Post-Quantum World
- Quantum computing is a looming threat to current cryptographic standards, with potential to disrupt existing methods.
- Transitioning to post-quantum cryptography may be necessary to maintain robust security in the quantum era.
- PUF technology is highlighted as a secure option against quantum attacks, offering strong security for systems.
- The white paper offers insights into the impact of quantum computing on security and the role of PUF products in ensuring robust security.
Read Full Article
12 Likes
VentureBeat
159
Image Credit: VentureBeat
Hugging Face just launched a $299 robot that could disrupt the entire robotics industry
- Hugging Face launches $299 Reachy Mini robot democratizing robotics development.
- Robot combines AI with robotics, aiming to challenge industry's closed-source, high-cost model.
- Emphasizes accessibility, packs advanced features like body rotation, multiple microphones, and cameras.
Read Full Article
9 Likes
Nordicapis
320

Critical API Security Failures That Could Break Your Business (And How to Prevent Them)
- APIs play a crucial role in modern software ecosystems, but poorly secured APIs pose significant risks.
- Security gaps like weak authentication, insufficient authorization, injection attacks, and data exposure are common.
- Best practices include strong authentication, encryption, input validation, rate limiting, and security testing.
- Properly configuring CORS, adopting security headers, logging and monitoring, and securing the entire SDLC are vital.
- Addressing these security gaps is essential to protect businesses from costly incidents and reputational damage.
Read Full Article
19 Likes
Medium
10
Image Credit: Medium
Satellites, Cyber Weapons, and AI: The Unseen War That Already Began
- Warfare has evolved with a focus on cyber insertion, satellite data, and AI algorithms to identify targets before physical combat.
- Satellites play a crucial role on the frontline, providing real-time data for strategic purposes, emphasizing the importance of air defense, satellite encryption, and cyber resilience.
- Nuclear weapons are now integrated with AI, satellites, and cyber capabilities, affecting global deterrence strategies.
- The article warns that the next war could already be unfolding, emphasizing the need for nations to adapt to the ever-changing landscape of modern warfare.
Read Full Article
Like
Dev
64

Image Credit: Dev
Critical RCE Vulnerability in Redis HyperLogLog (CVE-2025-32023)
- Redis patched a critical Remote Code Execution (RCE) vulnerability (CVE-2025-32023) in its HyperLogLog implementation.
- The vulnerability allows for remote code execution under specific conditions with a public proof-of-concept exploit available.
- An authenticated attacker can trigger memory corruption in Redis by sending a specially crafted string, leading to arbitrary system command execution.
- Users are strongly advised to upgrade to the latest patched versions to mitigate the vulnerability and prevent potential exploitation.
Read Full Article
3 Likes
Medium
355

Image Credit: Medium
Can AI Be Held Legally Responsible? Exploring Robot Rights & Accountability
- The question of who is legally responsible when AI causes accidents remains a major gap in current legal systems as AI lacks intent and consciousness.
- Some experts suggest granting AI a form of “legal personhood” to hold them accountable in civil cases, while others argue that humans involved in AI design or deployment should bear responsibility.
- The European Union has proposed AI-specific regulations to ensure transparency and accountability, while India is still developing its stance on AI accountability.
- Globally, there is a growing need for laws that balance innovation and public safety as AI continues to advance, requiring legal systems to adapt to keep pace with technological developments.
Read Full Article
19 Likes
Dev
256

Image Credit: Dev
Interview With Author Ahmed Awad ( NullC0d3 )
- Ahmed Awad, also known as NullC0d3, is a veteran cybersecurity threat intelligence analyst with over 20 years of experience. He has written two books in the Hacker Hunter series focusing on real-world cybersecurity strategies and insights.
- His latest book, 'Inside the Hacker Hunter’s Toolkit,' was inspired by the need for practical guidance in cybersecurity beyond certifications. Ahmed writes authentically after completing real-world cases and draws inspiration from authors like Kevin Mitnick and Clifford Stoll.
- He is currently working on his third book, 'Inside the Hacker Hunter’s Ransomware Playbook,' which aims to delve into ransomware operations and how defenders can counter them effectively.
- Ahmed Awad leverages platforms like LinkedIn, Medium, TikTok, and Facebook Groups for book promotion. His advice to new authors includes not waiting for perfection and ensuring their work provides value to readers.
Read Full Article
15 Likes
Dev
135

Image Credit: Dev
What is Dangling DNS? (And How It Can Lead to Domain Takeovers)
- Dangling DNS occurs when a DNS record still points to a cloud service that has been deleted, leaving the record 'dangling.'
- Attackers can exploit dangling DNS by claiming the deleted resource name and hosting malicious content under the subdomain, leading to brand impersonation, data theft, and phishing.
- An example scenario is deleting an Azure App Service but forgetting to remove the CNAME record, allowing an attacker to claim the resource name and redirect traffic.
- To prevent dangling DNS, it is crucial to clean up DNS records when deleting cloud services, audit DNS regularly, use monitoring tools, and enable ownership validation on platforms that support it.
Read Full Article
8 Likes
Medium
88

Image Credit: Medium
Soul Cyber Tech Brief
- Bitchat is a messaging app that operates without servers, the internet, or phone numbers, using Bluetooth technology to create a decentralized network for private and encrypted communication.
- Devices running Bitchat form a mesh network where messages are relayed through nearby devices, enabling communication even in areas with poor internet connectivity or censorship.
- Key features include peer discovery through Bluetooth, self-destructing encrypted messages, and the ability to communicate when some devices are offline.
- Bitchat's use of decentralized mesh networks, Bluetooth Low Energy, encryption, and privacy features offers a resilient and secure communication option in scenarios like protests, disaster zones, or remote areas.
Read Full Article
5 Likes
Medium
332

Mullvad VPN vs ProtonVPN: Who’s the Real Champion of Digital Anonymity
- Mullvad VPN and ProtonVPN are trusted for digital anonymity due to open-source transparency and third-party audits.
- Mullvad prioritizes anonymity, operating out of Sweden without mandatory data retention laws for VPNs.
- ProtonVPN balances privacy with account-based convenience and is more polished, offering better performance and global streaming options.
- Mullvad is simpler, cheaper, more anonymous by design, control-heavy, and maintains a smaller fleet of servers with a focus on privacy over streaming perks.
Read Full Article
20 Likes
Medium
185

Image Credit: Medium
When Kindness Leads, Hearts Heal – A World We All Deserve
- Kindness is a powerful force that often goes unnoticed in today's fast-paced world focused on innovation and wealth.
- It is a silent yet impactful leader that can touch hearts and bring warmth to a future that needs kindness.
- Kindness is portrayed as courage in its gentlest form, capable of saving someone's day, offering support, and listening without judgment.
- The truest achievement lies in choosing to be human and fostering kindness in a world that often prioritizes speed and profits.
Read Full Article
11 Likes
Dev
237

Image Credit: Dev
The Security Checklist I Use for Every Website I Build
- New website builder shares insight on crucial security checklist developed through experience.
- Emphasizes importance of integrating security from project initiation and offers practical tips.
- Covers topics like JWT structure, critical security measures, recent vulnerabilities, implementation lessons, and testing.
- Explains authentication methods, JWT best practices, security hardening, mistakes to avoid, and testing.
- Concludes with key takeaways on security implementation and the ongoing nature of security.
Read Full Article
14 Likes
For uninterrupted reading, download the app