Cyber Security News
Securityaffairs
143
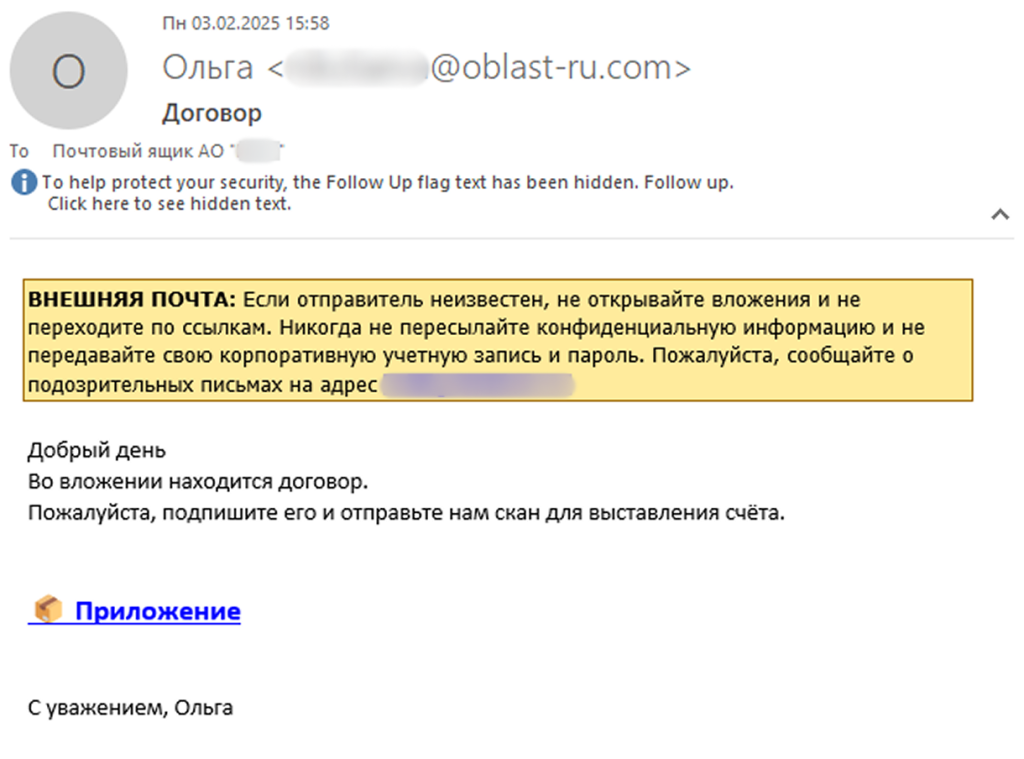
Image Credit: Securityaffairs
New Batavia spyware targets Russian industrial enterprises
- A new spyware named Batavia is being spread through fake contract-themed emails targeting Russian organizations since March 2025.
- The spyware includes a VBA script and two executables, detected by Kaspersky as Trojan.Batavia variants, designed to steal internal documents.
- The attack involves multiple stages where the malware collects system info, spies on the system by capturing screenshots and exfiltrating data to a command-and-control server.
- The victims of the Batavia spyware campaign are Russian industrial enterprises, with over 100 users across multiple organizations falling prey to the phishing messages.
Read Full Article
8 Likes
Ars Technica
241

Image Credit: Ars Technica
“No honor among thieves”: M&S hacking group starts turf war
- A ransomware group responsible for recent cyberattacks on UK retailers has entered a turf war with a competitor, leading to potential fallout for corporate victims.
- The conflict between DragonForce and RansomHub in the ransomware-as-a-service market may increase risks for companies, including the possibility of being extorted twice.
- The rivalry escalated after DragonForce rebranded itself as a 'cartel,' widening its services and attracting more affiliate partners, causing friction with RansomHub.
- Experts warn that the conflict between these hacking groups could lead to increased cyberattacks and double extortion of victims, highlighting the lawless and volatile nature of the cybercrime landscape.
Read Full Article
14 Likes
Ubergizmo
27

Image Credit: Ubergizmo
AI-Powered Browser Agents Pose Major Security Risks, Experts Warn
- Cybersecurity experts warn of significant risks posed by AI-powered browser agents, especially for users of Chrome and Microsoft Edge.
- Browser AI agents lack the ability to recognize malicious websites or phishing attempts, making them vulnerable to attacks that traditional security measures may not prevent.
- These agents operate with the same privileges as human users, leading to potential unauthorized access to sensitive information.
- Recommendations include enabling Chrome’s 'Enhanced Protection' mode and implementing browser-native security controls to govern AI agent behavior.
Read Full Article
1 Like
Tech Radar
303

Image Credit: Tech Radar
The EU could be scanning your chats by October 2025 – here's everything we know
- Denmark has reintroduced the controversial child sexual abuse (CSAM) scanning bill, known as Chat Control, at the start of its EU Presidency on July 1, 2025.
- The Chat Control proposal aims to require messaging services in Europe to scan users' chats for CSAM, even if they are encrypted, and could potentially be adopted by October 14, 2025.
- Since May 2022, the proposal has struggled to secure the necessary majority support, with Poland being the latest Presidency to abandon such plans.
- Privacy advocates and experts have raised concerns over the potential impact of Chat Control on encryption protections, with past versions facing backlash and the industry pushing back against coercive measures to weaken encryption.
Read Full Article
18 Likes
Pymnts
89

Image Credit: Pymnts
Understanding Fraud Patterns Key to Trust in Crypto’s Growth Narrative
- Crypto-related fraud has become a multibillion-dollar global phenomenon, with recent cases involving impersonating the Trump-Vance Inaugural Committee and seizing nearly $400 million in crypto assets.
- The history of crypto scams, ranging from amateur phishing campaigns to coordinated fraud rings, offers valuable lessons in trust, transparency, and consumer protection for mainstream businesses.
- Scams in the crypto world have evolved from unsophisticated schemes in the early days to elaborate frauds like the BitConnect Ponzi scheme and the recent collapse of FTX, highlighting human failures and systemic risks.
- Understanding the patterns of fraud in crypto can provide insights for enterprises and financial institutions integrating digital assets, emphasizing the importance of employee training in cybersecurity and recognizing the role of psychology in scams.
Read Full Article
5 Likes
Dev
307

Image Credit: Dev
How I Hack a Hacker
- A cybersecurity analyst in Lagos recounts a phishing scam encounter via dubious email.
- Despite suspicion, curiosity leads to inspecting the phishing structure to analyze tactics.
- Investigation reveals a silent redirect technique used to gain access without passwords.
- The analyst shares how these covert attacks exploit session handling vulnerabilities for access.
- The account of hacking back the hacker unfolds in a detailed digital pursuit.
Read Full Article
16 Likes
Dev
81

Image Credit: Dev
Day 21: Backend Security – The Last Line of Defense
- The importance of backend security as the last line of defense is emphasized in a developer's internship journey.
- Initially, RBAC checks were done on the frontend for a system called Lura, but vulnerabilities arose if malicious requests were sent directly to the backend.
- To enhance security, the focus shifted to securing NestJS backend endpoints through the implementation of custom guards, decorators, and workspace validation logic.
- Testing was conducted using Jest to ensure the effectiveness of the implemented security measures, highlighting the significance of robust backend checks in protecting users.
Read Full Article
4 Likes
Tech Radar
239

Image Credit: Tech Radar
Over 26 million resumes exposed in top CV maker data breach - here's what we know
- Security researchers discovered a large unprotected database containing almost 26 million resumes and CVs belonging to US citizens.
- The exposed data, found in a misconfigured Azure Blob storage container, included individuals' personal information like full names, email addresses, phone numbers, education and professional details.
- The database was later identified as belonging to TalentHook, a cloud-based applicant tracking system, exposing job seekers to potential phishing attacks and malware threats.
- While the researchers informed TalentHook about the issue, there is uncertainty regarding whether access to the database has been restricted, leaving it vulnerable to cybercriminals.
Read Full Article
12 Likes
Dev
206

Image Credit: Dev
Secure Note Manager in React - Part 2. Client-Side Login with Web Crypto and Redux
- Build a browser-based secure login page without backend using Redux and Web Crypto.
- Utilize in-memory storage with Redux for CryptoKey ensuring data disappears on reload.
- Implement secure login form authorizing users via master password and browser-based cryptography.
- Technique to trigger UI reactivity with Redux, ensuring secured, offline login experience.
- Vault access granted only upon presence of CryptoKey, ensuring secure data handling.
Read Full Article
12 Likes
Tech Radar
7

Image Credit: Tech Radar
US government cracks down on bulletproof hosting provider helping to prop up cybercrime gangs
- The US government has sanctioned a Russia-linked bulletproof hosting provider, Aeza Group, for supporting ransomware and cybercrime.
- Aeza Group provided infrastructure to ransomware group BianLian and infostealer operations like Meduza and Lumma.
- Britain's National Crime Agency helped identify Aeza Group's UK affiliate and individuals associated with the group, leading to sanctions.
- While US sanctions prohibit engagement with Aeza Group, their impact on Russian attackers using the bulletproof host is expected to be minimal.
Read Full Article
Like
Tech Radar
179

Image Credit: Tech Radar
Ingram Micro confirms ransomware attack, internal systems affected and shut down
- Ingram Micro, a global IT distributor, confirms ransomware attack impacting internal systems and forcing some employees to work from home.
- Reports suggest the attack may be the work of the SafePay ransomware group, known for double-extortion tactics and breaching over 200 organizations.
- No information regarding stolen data has been provided yet, but the breach affected systems like the Xvantage distribution platform.
- Ingram Micro is actively working to restore affected systems, with third-party cybersecurity experts involved in the investigation.
Read Full Article
10 Likes
TechCrunch
432

Image Credit: TechCrunch
Ingram Micro says ongoing outage caused by ransomware attack
- Ingram Micro, a U.S. technology distributing giant and managed services provider, confirms that a ransomware attack caused an ongoing outage at the company.
- The hack started on Thursday, leading to the company's website and network going down, impacting its ability to process orders.
- The outage at Ingram Micro is affecting software licensing, hindering customers from using or provisioning certain products reliant on the company's systems.
- Although no specific ransomware group has claimed responsibility, reports suggest the SafePay ransomware gang may be behind the attack, aiming to extort victims into paying ransoms.
Read Full Article
15 Likes
Securityaffairs
74

Image Credit: Securityaffairs
Taiwan flags security risks in popular Chinese apps after official probe
- Taiwan's National Security Bureau (NSB) warns that Chinese apps like TikTok and WeChat pose security risks due to excessive data collection and data transfers to China.
- NSB coordinated with other agencies to inspect popular Chinese apps and found violations of security standards, advising caution when using such apps.
- Five China-made apps were found to violate key security standards, collecting personal data without consent and transferring it to servers in China.
- Taiwanese authorities emphasize the risks of data misuse and privacy infringement posed by Chinese apps, similar to concerns expressed by other countries like the US and the EU.
Read Full Article
4 Likes
Tech Radar
323

Image Credit: Tech Radar
Hacker threatens to leak a rumoured huge cache of stolen Telefónica data
- A cybercriminal threatens to release over 100GB of sensitive data allegedly stolen from Telefnica, a Spanish telecommunications giant.
- The hacker, known as Rey, claims to have stolen 106GB of files, including internal communications, purchase orders, logs, customer records, and employee data during a data breach in May 2025.
- Telefnica downplays the incident, stating the data is old and there was no new breach, despite Rey sharing a sample of the stolen data with the media.
- Rey has threatened to release the full batch of data unless a payment is made, with evidence of files containing email addresses for employees and invoices for business partners from various countries.
Read Full Article
18 Likes
Silicon
141
Image Credit: Silicon
Hackers Steal Data From Louis Vuitton Korea
- Hackers compromised Louis Vuitton Korea's IT systems in June, accessing some data, including customer information.
- No financial data such as payment card or bank account details were included in the breach, and the incident has been contained.
- Louis Vuitton Korea is investigating the attack, has notified authorities, and is enhancing system security along with working with third-party experts.
- Considering recent breaches affecting luxury brands like Louis Vuitton and airlines like Qantas, cybersecurity threats continue to evolve, with hackers targeting sensitive data for ransom purposes.
Read Full Article
8 Likes
For uninterrupted reading, download the app