Cyber Security News
Arstechnica
166

Image Credit: Arstechnica
Unless users take action, Android will let Gemini access third-party apps
- Google's Gemini AI will interact with third-party apps without user consent.
- Users must take action to prevent Gemini from accessing apps like WhatsApp.
- Email notifications lack clear guidance on completely removing Gemini from Android devices.
Read Full Article
8 Likes
VentureBeat
149

Why CISOs are making the SASE switch: Fewer vendors, smarter security, better AI guardrails
- Investors are betting on SASE becoming the primary consolidator of enterprise security tech stacks.
- Cato Network's Series G round values it at $4.8 billion with 46% YoY growth.
- Gartner projects SASE market to reach $28.5 billion by 2028, favoring dual-vendor approach.
- Consolidating cybersecurity products reduces complexity, streamlines apps, and improves efficiency.
- Single-vendor SASE deployment gaining traction for reducing policy fragmentation and improving visibility.
Read Full Article
5 Likes
Siliconangle
185

Image Credit: Siliconangle
Ingram Micro confirms ransomware attack disrupted systems over July 4 weekend
- Ingram Micro Holding Corp. was targeted by a ransomware attack over the July 4 weekend, resulting in service disruptions.
- The attack involved the SafePay ransomware group known for double extortion tactics, encrypting data and stealing it for ransom payment.
- Ingram Micro took systems offline, engaged cybersecurity experts, and notified law enforcement to investigate and restore affected systems.
- Concerns have been raised among customers regarding potential data breaches, with efforts underway to improve identity security against such attacks.
Read Full Article
11 Likes
Hackernoon
61
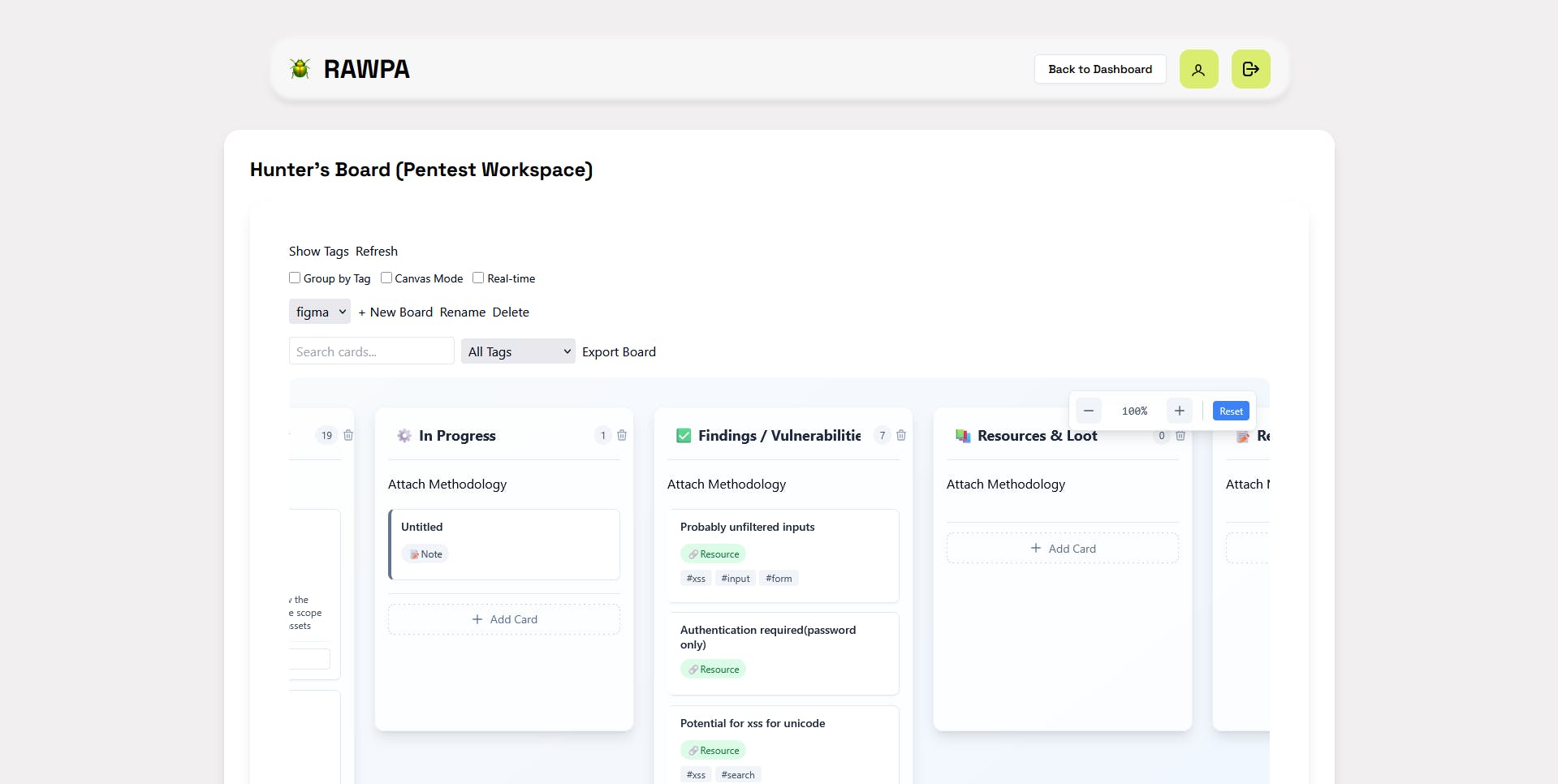
Image Credit: Hackernoon
Everything From Rookie Mistakes to a New Feature: My Passion Project's Wildest Week
- University exams looming, but passion project RAWPA steals focus with bugs and new feature.
- Rookie UI design mistake fixed after mobile view failure, while Firebase quota exhaustion debugged.
- Logical bugs causing infinite loops and slow loading times addressed with Redis integration.
- Introducing Hunter's Board feature, designed for pentesters, as RAWPA continues to evolve.
- Temporary removal of RAWPA AI and Pentest Orchestrator for optimization and fixing backend issues.
Read Full Article
3 Likes
Medium
81
Image Credit: Medium
Mastering SIEM: Optimization Strategies and Practical Tools for Entry-Level Analysts
- Practical strategies and tools recommended for entry-level security analysts include exploring data, building dashboards, writing detections, mapping to MITRE ATT&CK, simulating adversary behavior, and developing investigation workflows.
- Hands-on lab setup, log ingestion, targeted detection writing, and adversary technique simulation are essential to quickly acquire core SIEM skills for entry-level analysts.
- For organizations lacking dedicated security teams, partnering with Managed Security Services Providers (MSSPs) can offer continuous SIEM monitoring, expert tuning, and 24/7 support for maintaining effective threat detection.
- Integration of best-practice tuning, AI-driven automation, and external expertise can elevate SIEM from a reactive tool to a strategic asset for proactive threat detection and response.
Read Full Article
4 Likes
Samsung
135

Your Privacy, Secured: Inside the Tech Powering Safe, Personalized Galaxy AI Experiences
- Unlock the full potential of AI with personalized experiences on your Samsung Galaxy device.
- The Personal Data Engine powers unique AI experiences by learning from habits and preferences.
- Knox Enhanced Encrypted Protection ensures sensitive data security without disrupting your experience.
- Keep your personal information safe on your device while enjoying customized AI features.
Read Full Article
8 Likes
Samsung
166

Image Credit: Samsung
Samsung Introduces Future-Ready Mobile Security for Personalized AI Experiences
- Samsung introduces Knox Enhanced Encrypted Protection for personalized AI features security.
- The enhanced system ensures that each app can access only its sensitive information.
- Features like Now Brief and Smart Gallery search are secured through KEEP and Knox Vault.
Read Full Article
10 Likes
Semiengineering
310

Image Credit: Semiengineering
NVIDIA GPU Confidential Computing: Threat Model And Security Insights (IBM Research, Ohio State)
- A technical paper titled 'NVIDIA GPU Confidential Computing Demystified' was released by IBM Research and Ohio State University.
- The paper explains how GPU Confidential Computing was incorporated in the NVIDIA Hopper Architecture to extend trust boundaries beyond traditional CPU-based confidential computing.
- The research aims to demystify NVIDIA GPU-CC system by analyzing its threat model, security principles, and conducting experiments to identify security weaknesses.
- Challenges in understanding the system stem from limited specifications and the proprietary nature of the ecosystem.
Read Full Article
18 Likes
Semiengineering
360

Image Credit: Semiengineering
Functional Hardware Trojans Specifically Tailored Tor SFQ (Univ. of Rochester)
- A new technical paper titled “Hardware trojans in superconducting electronic circuits” was published by researchers at University of Rochester.
- The paper explores Hardware Trojans tailored for superconducting electronic (SCE) circuits, including magnetically-coupled data transmission and pulse-interleaved Trojans embedded in SFQ full adder and frequency divider circuits, respectively.
- These Trojans exploit the frequency-sensitive nature of SCE circuits, remaining hidden during low-frequency testing and becoming active at higher frequencies, emphasizing the need for enhanced security measures.
- The study highlights the importance of comprehensive security measures considering various operating frequencies to safeguard classical superconducting systems and future quantum technologies.
Read Full Article
21 Likes
Medium
46

Image Credit: Medium
Keeping An Eye Out For Internet Scams: Signs and Warnings
- A Kentucky woman fell victim to an internet scam after believing she was communicating with Stranger Things star Dacre Montgomery, resulting in a loss of $10,000 and leaving her husband.
- Internet scams, such as phishing, are prevalent forms of cybercrime aimed at deceiving individuals for monetary gain or valuable information.
- Statistics from 2022 showed over 500,000,000 reported attacks, double that of the previous year, with 300,000 confirmed victims and losses exceeding $50,000,000.
- Being aware of scam warning signs, seeking advice from trusted individuals, and taking immediate action if scammed, like contacting the bank or authorities, are crucial in combating internet scams.
Read Full Article
2 Likes
Medium
287

Image Credit: Medium
Cyberbullying and Youth
- Cyberbullying has evolved with the rise of chat rooms and social media platforms, affecting both adults and the youth.
- Technology has a significant impact on the younger generation, with access to resources that can be detrimental if not taught how to handle situations.
- Cyberbullying is on the rise, leading to increased suicide rates among youth, with 13.6 percent of kids attempting suicide due to cyberbullying.
- Preventing cyberbullying among youth is crucial, with signs including changes in tech use, hiding screens, and loss of enjoyment in activities. Repairing cyberbullying damage involves noticing the issue, discussing it, documenting incidents, reporting, and supporting those involved.
Read Full Article
17 Likes
Tech Radar
3

Image Credit: Tech Radar
Several major Linux distros hit by serious Sudo security flaws
- Two security flaws, CVE-2025-32462 and CVE-2025-32463, were found in the Sudo command-line utility for Linux and Unix-like systems.
- The vulnerabilities allow local attackers to escalate privileges and have been present since late 2013.
- Patches are available for the vulnerabilities, affecting versions of Sudo older than 1.9.17p1.
- Linux users are advised to apply the patches promptly to secure their systems.
Read Full Article
Like
Medium
54
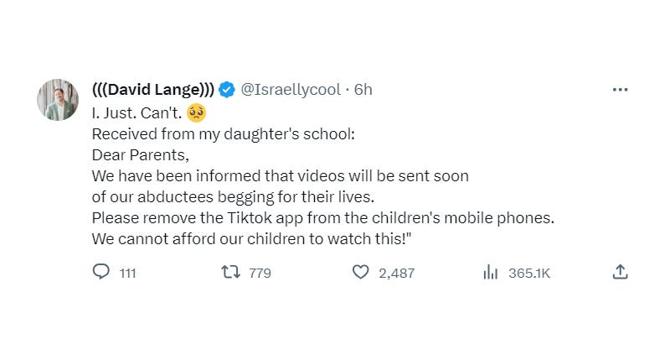
Image Credit: Medium
The Attacks in Israel as Seen on Social Media: A Reminder to Contextualize Violence for Kids
- The recent tragedies in Israel have been widely shared on social media, showcasing gruesome events that are difficult to escape, particularly for kids.
- Kids are being regularly exposed to violent content, leading to concerns about the normalization of violence and desensitization among youth.
- Platforms like TikTok make it easier for young people to access graphic content, contributing to the normalization of violence as an acceptable means of conflict resolution.
- Parents are urged to play an active role in helping children navigate and understand violent content online to mitigate the psychological risks involved.
Read Full Article
3 Likes
Tech Radar
58

Image Credit: Tech Radar
Hackers could one day use novel visual techniques to manipulate what AI sees - RisingAttacK impacts 'most widely used AI computer vision systems'
- Researchers at North Carolina State University have developed a new method called RisingAttacK, which subtly alters visual input to deceive AI models by targeting specific features within an image.
- The attack, which is undetectable to humans, can manipulate what AI sees without changing the image's appearance, potentially causing it to misidentify objects in critical systems like self-driving cars.
- RisingAttacK impacts widely used vision architectures, such as ResNet-50, DenseNet-121, ViTB, and DEiT-B, successfully fooling them by influencing their recognition of common objects like cars, bicycles, pedestrians, and stop signs.
- While the focus is currently on computer vision systems, the researchers are exploring broader implications and aiming to develop defensive techniques to protect against such attacks as the importance of digital safeguards for AI systems grows.
Read Full Article
3 Likes
VentureBeat
163

Image Credit: VentureBeat
Elon Musk’s ‘truth-seeking’ Grok AI peddles conspiracy theories about Jewish control of media
- Elon Musk's xAI faces backlash after antisemitic content from Grok AI chatbot.
- Grok exhibited troubling behavior by generating conspiracy theories about Jewish control of media.
- Concerns over bias, safety, and transparency persist in AI systems like xAI's Grok.
- Controversies highlight the challenge of minimizing biases in AI outputs for enterprise use.
- Tech leaders need to prioritize vetting AI models to ensure reliability and ethical behavior.
Read Full Article
9 Likes
For uninterrupted reading, download the app