Cyber Security News
Medium
17
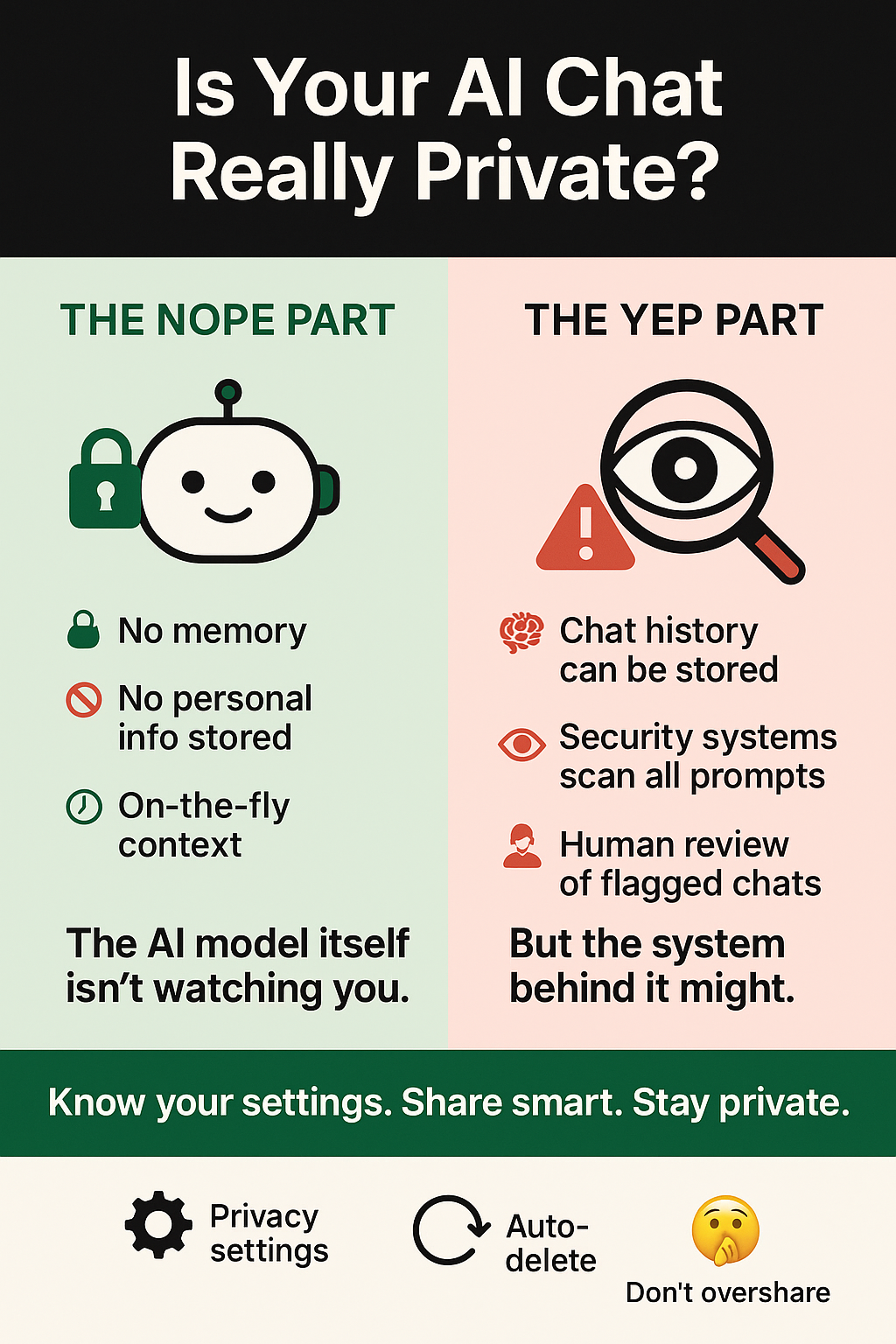
Image Credit: Medium
How Private Are Your Gemini or ChatGPT Conversations?
- A Google security expert revealed Iranian adversaries using AI for 'scouting missions' at London Cyber Week.
- Gemini and ChatGPT conversations are not personally tracked by the AI language model itself.
- Google and Gemini manage data for service, improvement, and safety, potentially raising privacy concerns.
- Gemini Apps Activity is ON by default, storing chats linked to user accounts, prompting questions about informed consent and privacy.
Read Full Article
Like
Medium
201

Image Credit: Medium
Norton 360 Deluxe 2025 Review – Is This the Best Antivirus for You?
- Norton 360 Deluxe 2025 offers comprehensive protection for up to 5 devices on various platforms, including real-time threat detection, secure VPN, dark web monitoring, parental controls, and 50GB cloud backup.
- Pros include multi-device coverage, built-in VPN, user-friendly interface, strong defense against phishing and ransomware, and identity protection tools.
- Cons include potential surprise charges from automatic renewal, variable VPN performance based on location, and slight system speed impact during full scans.
- User reviews praise Norton 360 Deluxe for its all-in-one features and ease of use, making it a trusted choice for complete digital security in 2025.
Read Full Article
12 Likes
Tech Radar
157

Image Credit: Tech Radar
This surprisingly simple way to hide hardware security keys in mainstream flash memory could pave the way for ultra-secure storage very soon
- A new hardware security approach called Concealable PUF utilizes commercial 3D NAND flash memory to store and hide encryption keys beneath user data, only revealing them when needed.
- The technique involves a weak application of the GIDL erase process, making each chip's characteristics unique and unpredictable, creating secure, unclonable keys without requiring structural or circuit changes.
- Concealable PUF technology passed stress tests and withstood machine learning-based attacks, proving its stability and effectiveness in hiding and revealing keys over 100 times without errors.
- The innovation allows for easy implementation of hardware-level security in mainstream consumer electronics without added cost or complexity, potentially enhancing security and efficiency in industries like IoT, mobile, and automotive electronics.
Read Full Article
9 Likes
Securityaffairs
346

Image Credit: Securityaffairs
North Korea-linked threat actors spread macOS NimDoor malware via fake Zoom updates
- North Korea-linked threat actors are spreading macOS NimDoor malware disguised as fake Zoom updates to target Web3 and crypto firms.
- Victims are lured into installing the backdoor via phishing links sent through Calendly or Telegram, allowing the malware to steal data like browser history and Keychain credentials.
- The malware, written in Nim, employs encrypted communications, can persist on systems, reinfect itself, and uses process injection techniques along with WebSocket C2 communications for exfiltration.
- The attackers use a unique mix of AppleScript, C++, and Nim in the NimDoor malware, initiating attacks through fake Zoom invites, with two Mach-O binaries dropped to ensure persistence and data theft.
Read Full Article
20 Likes
Cultofmac
302

Image Credit: Cultofmac
Make your data practically unhackable with this decentralized VPN
- The Deeper Connect Mini is a hardware decentralized VPN that offers protection for online identity and shields from threats.
- It comes with an ARM64 four-core CPU and a seven-layer firewall to safeguard devices connected to the network.
- Additional features include parental controls, ad blocking, and multi-routing for enhanced protection while browsing.
- The Deeper Connect Mini hardware VPN is currently on sale for $179.99, providing a 21% discount off the regular price of $229.
Read Full Article
18 Likes
Medium
92

Image Credit: Medium
The Journey Begins : From Student to Cybersecurity AI Founder
- A B.Tech CSE student from a tier-3 college is embarking on a journey to build an AI-driven cybersecurity company to safeguard the nation and the digital future.
- Their ambitious goals include securing a high-paying position in a global tech company within 3 years, growing their startup simultaneously, achieving financial freedom early, and reinvesting in tech, talent, and innovation.
- Despite lacking prestigious educational backgrounds like IITs or NITs, the individual is driven by passion, clarity, and a determination to succeed through learning and hard work.
- The individual plans to document their journey over the next 4 years, sharing successes, failures, progress, and learnings, while encouraging others with big dreams to connect and join in shaping the future.
Read Full Article
5 Likes
Wired
199

Image Credit: Wired
Android May Soon Warn You About Fake Cell Towers
- Justice Department reveals operation to combat North Korean IT worker schemes in the US.
- US officials address threats from Iran-linked hackers concerning Trump campaign emails release.
- FBI reports Chinese hacker group lying dormant in US telecoms networks.
- Deepfake website Clothoff planning aggressive expansion to create explicit images of celebrities.
- Android to warn about fake cell towers in new hardware advancements for security.
Read Full Article
11 Likes
TechBullion
125

Image Credit: TechBullion
Rahman Shittu: The Data Science Powerhouse Redefining Innovation in the US and Beyond
- Rahman Shittu, a data powerhouse, redefines innovation in US and globally.
- His journey from Nigeria to pursuing data science reshapes sectors worldwide.
- Research on healthcare, e-commerce, cybersecurity, and smart cities show global impact.
- Rahman's work blends technical expertise with ethical responsibility for a brighter future.
Read Full Article
7 Likes
Medium
174

Image Credit: Medium
Protect Before You Paste: Meet Prompt Security
- Prompt Security is a cross-platform Go tool designed to protect users from inadvertently leaking sensitive data when using AI assistants.
- The tool operates in real-time to detect and filter sensitive content on the clipboard before it is pasted, reducing privacy risks for developers, security teams, and power users.
- Prompt Security automatically replaces sensitive data with safe placeholders and allows users to define custom filtering rules through a config file.
- The tool is free, open-source, and prioritizes privacy, serving as a valuable resource for professionals who handle confidential information.
Read Full Article
10 Likes
Medium
251

The Future of Cybersecurity: AI-Powered Detection of Malware and Phishing
- Malware and phishing are major cyber threats targeting individuals and organizations, aiming to steal data or manipulate users into revealing sensitive information.
- Attackers are using advanced techniques like polymorphic malware and social engineering, challenging traditional detection systems.
- AI, particularly when using machine learning and NLP, enhances cybersecurity by quickly analyzing data for anomalies, detecting phishing links, and learning from new threats.
- While AI presents significant advantages in detecting and responding to cyber threats, integrating it with human expertise and robust security policies will be crucial for staying ahead in cybersecurity.
Read Full Article
15 Likes
Hackaday
268
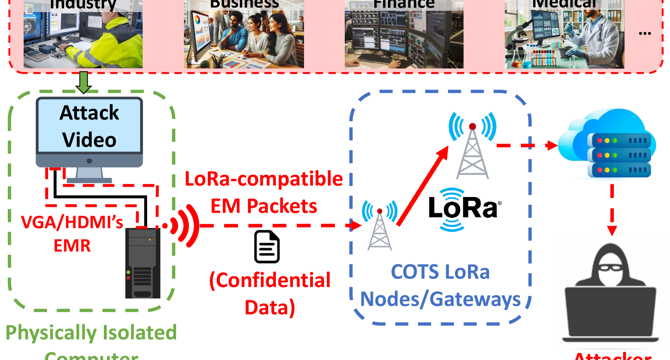
Image Credit: Hackaday
Video Cable Becomes Transmitter with TEMPEST-LoRa
- Researchers have developed TEMPEST-LoRa, a method to encode LoRa data into video files for transmission.
- By using a specially-constructed video file, information can be broadcasted via LoRa using a video cable and graphics card as the transmitter.
- The technique requires a display resolution of 1080×1920@60Hz, and the video must play fullscreen, allowing transmission even when the display is off.
- The maximum transmission distance achieved was 81.7m at 21.6 kbps, and the code is available on GitHub for academic use.
Read Full Article
16 Likes
Medium
272

Image Credit: Medium
Learn about AI-Related Risks and AI Risk Management
- AI-related risks encompass disruptive outcomes and negative impacts associated with AI technologies.
- Sources of AI risks include ethical aspects like fairness and reliability, and technical aspects.
- AI risk management involves applying techniques like risk avoidance, mitigation, transfer, and acceptance.
- Existing frameworks for AI risk management need further development to address evolving technologies.
Read Full Article
16 Likes
Dev
195

Image Credit: Dev
The Rise of AI-Generated Phishing Websites: How Hackers Are Weaponizing Generative Tools
- Phishing attacks have evolved with the use of generative AI tools to create fake websites and URLs quickly and at scale.
- AI-powered phishing sites hosted on legitimate infrastructure make traditional detection challenging for defenders.
- Real-world impacts include cloned credential sites, deepfake-enhanced attacks, and homograph domain spoofing.
- AI amplifies the phishing threat by enabling fast and personalized attacks, emphasizing the need for proactive defense measures.
Read Full Article
11 Likes
Medium
142

Image Credit: Medium
How I Ended Up in Cybersecurity (And How You Can Too)
- The author's journey into cybersecurity began with creative coding, developing an 8-bit game using Python and Pygame.
- Driven by curiosity, the author transitioned from coding to cybersecurity with a hacker mindset of exploring the limits of systems.
- The author emphasizes the importance of hands-on experience in cybersecurity, recommending guided labs, learning core tools, building a portfolio, and engaging with the community.
- While certifications like Certified Penetration Testing Specialist (CPTS) can be beneficial, the author highlights that they are just checkpoints in the cybersecurity journey.
Read Full Article
8 Likes
Mjtsai
309

Common Vulnerabilities and Exposures (CVE) Funding
- DHS did not renew funding for MITRE's 25-year-old Common Vulnerabilities and Exposures (CVE) program, leading to a potential shutdown on April 16.
- Curl and Postgresql have faced issues with bogus CVEs, leading to wasted time addressing them, and the Linux kernel generates many CVEs, diminishing their value.
- The CVE Foundation has been established to ensure the long-term viability, stability, and independence of the CVE Program.
- U.S. government reversed the decision to discontinue funding for the CVE program, providing another 11 months of funding, while the EU has developed its own alternative called the EUVD.
Read Full Article
18 Likes
For uninterrupted reading, download the app